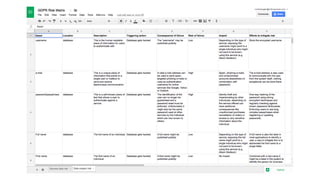
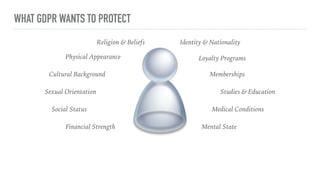
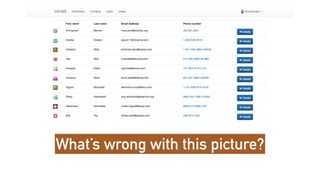
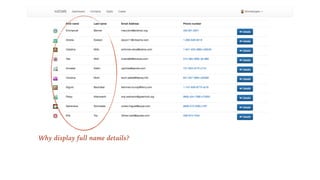
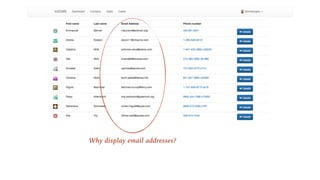
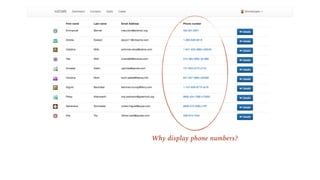
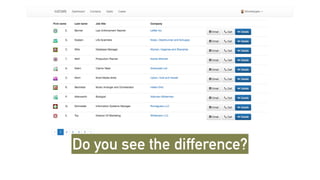
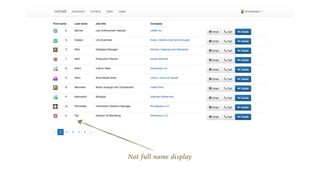
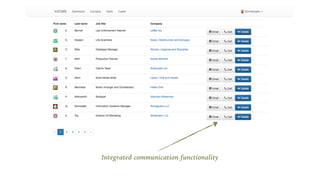
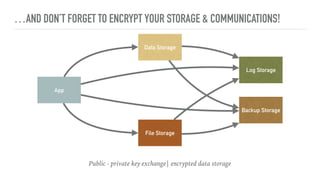
The document outlines the General Data Protection Regulation (GDPR), which enforces strict rules on how businesses must handle personal data of EU data subjects, effective from May 25, 2018. It emphasizes the need for compliance to avoid substantial fines and highlights a risk-based approach to data protection that involves assessing, designing, transforming, operating, and conforming to GDPR standards. Additionally, it provides practical tips for implementing security measures and protecting privacy data.