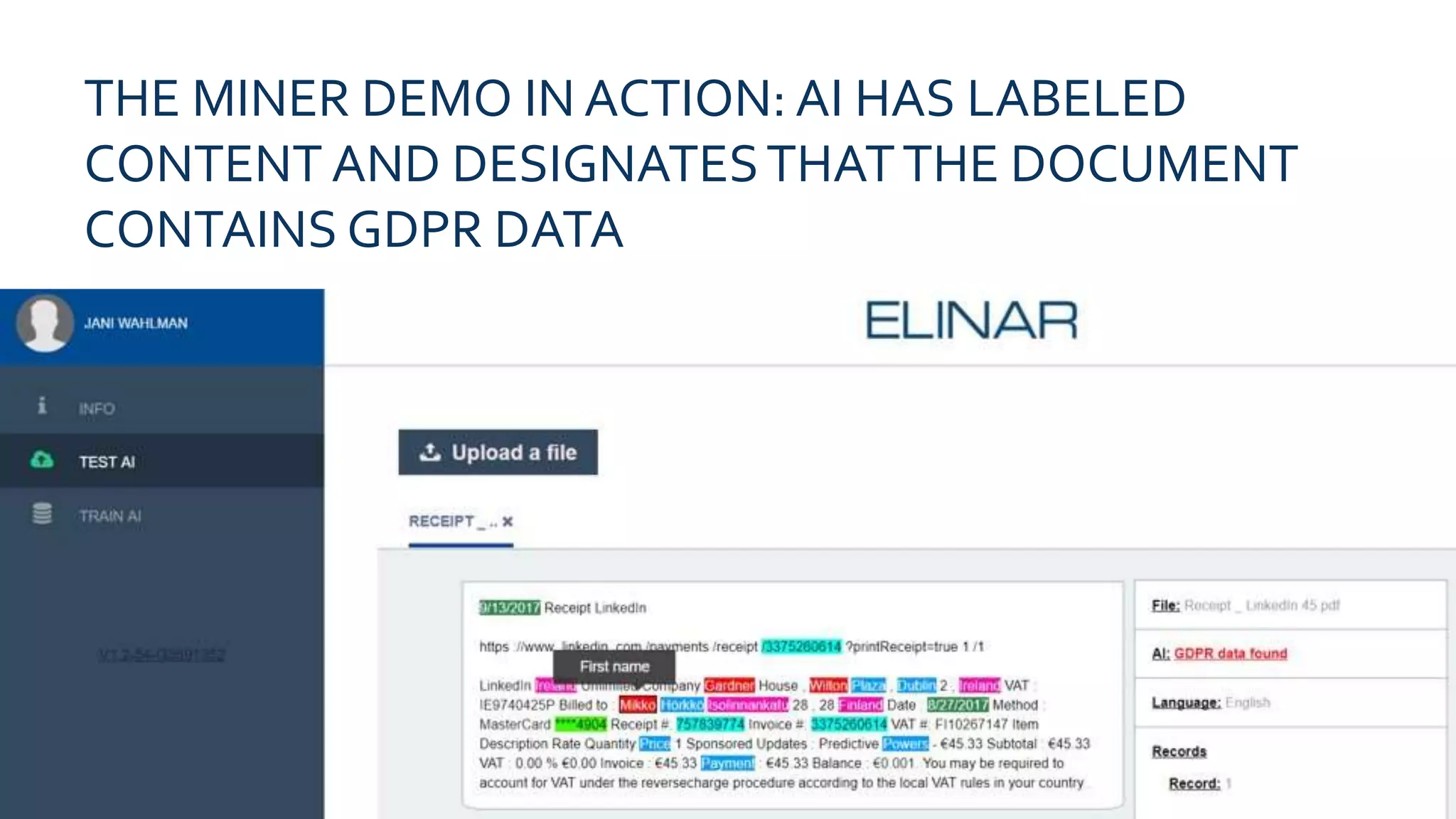
Privacy data regulations, particularly GDPR, will challenge businesses by creating a divide between those who manage data correctly and those who do not. To address the complexity of identifying privacy data, the GDPR and privacy data AI miner offers a scalable solution that helps organizations achieve regulatory compliance while leveraging their privacy data for competitive advantage. Available as on-demand or on-premise, the AI miner can train on a company's specific data to enhance its detection capabilities.