Cyber security career development paths
•
0 likes•3,748 views
Here is your guide on how to progress through the cyber security career ladder. This resource shows you all the different cyber security roles and the qualifications needed for each!
Report
Share
Report
Share
Download to read offline
Recommended
This session is for organizational executive managers and security teams who want to know the effectiveness and performance of their organization’s application security initiatives.
Introductory performance KPI metrics covered for:
1. Product Security Quality & Business Financial Risk Exposure
2. SSDLC Maturity Organizational Performance
3. AppSec QA Testing
4. AppSec Consulting
5. AppSec Training
6. DevSecOps
AppSec & DevSecOps Metrics: Key Performance Indicators (KPIs) to Measure Success

AppSec & DevSecOps Metrics: Key Performance Indicators (KPIs) to Measure SuccessRobert Grupe, CSSLP CISSP PE PMP
Recommended
This session is for organizational executive managers and security teams who want to know the effectiveness and performance of their organization’s application security initiatives.
Introductory performance KPI metrics covered for:
1. Product Security Quality & Business Financial Risk Exposure
2. SSDLC Maturity Organizational Performance
3. AppSec QA Testing
4. AppSec Consulting
5. AppSec Training
6. DevSecOps
AppSec & DevSecOps Metrics: Key Performance Indicators (KPIs) to Measure Success

AppSec & DevSecOps Metrics: Key Performance Indicators (KPIs) to Measure SuccessRobert Grupe, CSSLP CISSP PE PMP
Cyber Security Career PathChandu cyber security career path

Chandu cyber security career pathUniversity College of Engineering Kakinada, JNTUK - Kakinada, India
More Related Content
What's hot
What's hot (20)
How To Present Cyber Security To Senior Management Complete Deck

How To Present Cyber Security To Senior Management Complete Deck
SOC presentation- Building a Security Operations Center

SOC presentation- Building a Security Operations Center
Security Operations Center (SOC) Essentials for the SME

Security Operations Center (SOC) Essentials for the SME
Security operations center-SOC Presentation-مرکز عملیات امنیت

Security operations center-SOC Presentation-مرکز عملیات امنیت
An introduction to SOC (Security Operation Center)

An introduction to SOC (Security Operation Center)
SABSA: Key features, advantages & benefits summary

SABSA: Key features, advantages & benefits summary
Information Security Architecture: Building Security Into Your Organziation

Information Security Architecture: Building Security Into Your Organziation
Dragos S4x20: How to Build an OT Security Operations Center

Dragos S4x20: How to Build an OT Security Operations Center
Cybersecurity roadmap : Global healthcare security architecture

Cybersecurity roadmap : Global healthcare security architecture
Evaluating System-Level Cyber Security vs. ANSI/ISA-62443-3-3

Evaluating System-Level Cyber Security vs. ANSI/ISA-62443-3-3
Cybersecurity Career Paths | Skills Required in Cybersecurity Career | Learn ...

Cybersecurity Career Paths | Skills Required in Cybersecurity Career | Learn ...
From SIEM to SOC: Crossing the Cybersecurity Chasm

From SIEM to SOC: Crossing the Cybersecurity Chasm
DTS Solution - Building a SOC (Security Operations Center)

DTS Solution - Building a SOC (Security Operations Center)
Similar to Cyber security career development paths
Cyber Security Career PathChandu cyber security career path

Chandu cyber security career pathUniversity College of Engineering Kakinada, JNTUK - Kakinada, India
Similar to Cyber security career development paths (20)
Best Cybersecurity Certification Courses [2022]-vinsys![Best Cybersecurity Certification Courses [2022]-vinsys](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Best Cybersecurity Certification Courses [2022]-vinsys](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Best Cybersecurity Certification Courses [2022]-vinsys
Level up your SOC - Guide for a Resilient Education Program.pdf

Level up your SOC - Guide for a Resilient Education Program.pdf
What Cybersecurity Certifications Make You The Most Money Today.pptx

What Cybersecurity Certifications Make You The Most Money Today.pptx
TIC-TOC: Ransomware: Help your Customers be Prepared with Dominique Singer an...

TIC-TOC: Ransomware: Help your Customers be Prepared with Dominique Singer an...
Runecast: Simplified Security with Unparalleled Transparency (March 2022)

Runecast: Simplified Security with Unparalleled Transparency (March 2022)
Today's Cyber Challenges: Methodology to Secure Your Business

Today's Cyber Challenges: Methodology to Secure Your Business
Best Professional Courses After Graduation - Get Started Now

Best Professional Courses After Graduation - Get Started Now
What's Next : A Trillion Event Logs, A Million Security Threat

What's Next : A Trillion Event Logs, A Million Security Threat
Recently uploaded
Recently uploaded (20)
WSO2's API Vision: Unifying Control, Empowering Developers

WSO2's API Vision: Unifying Control, Empowering Developers
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
Navigating Identity and Access Management in the Modern Enterprise

Navigating Identity and Access Management in the Modern Enterprise
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Design and Development of a Provenance Capture Platform for Data Science

Design and Development of a Provenance Capture Platform for Data Science
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
Less Is More: Utilizing Ballerina to Architect a Cloud Data Platform

Less Is More: Utilizing Ballerina to Architect a Cloud Data Platform
TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...

TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Decarbonising Commercial Real Estate: The Role of Operational Performance

Decarbonising Commercial Real Estate: The Role of Operational Performance
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Cyber security career development paths
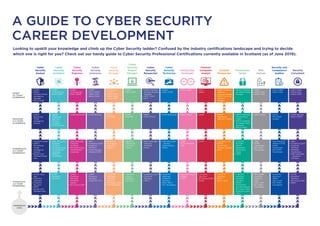
- 1. Looking to upskill your knowledge and climb up the Cyber Security ladder? Confused by the industry certifications landscape and trying to decide which one is right for you? Check out our handy guide to Cyber Security Professional Certifications currently available in Scotland (as of June 2019). A GUIDE TO CYBER SECURITY CAREER DEVELOPMENT Cyber Security Analyst Cyber Security Architect Cyber Security Engineer Cyber Security Instructor Cyber Security Manager Cyber Security Project Manager Cyber Security Researcher Cyber Security Technician DevSecOps Developer Forensic Computer Analyst Incident Responder Penetration Tester Risk Adviser Security and Compliance Auditor Security Consultant EXPERT (5+ YEARS’ EXPERIENCE) • CASP+ • CREST Certified Threat Intelligence Manager • (ISC)2 CISSP • CASP+ • CCIE Security • (ISC)2 CISSP • CASP+ • CCIE Security • (ISC)2 CISSP • CASP+ • (ISC)2 CISSP • ISACA CISA • ISACA CISM • EC-Council CCISO • (ISC)2 CISSP • ISACA CGEIT • ISACA CISM • CASP+ • (ISC)2 CISSP • CREST Certified Malware Reverse Engineer • (ISC)2 CISSP • GCTI • CASP+ • (ISC)2 CISSP • (ISC)2 CISSP • GCTI • GNFA • CREST Certified Network Intrusion Analyst • CREST Certified Incident Manager • CREST Certified Simulated Attack Manager • CASP+ • ISACA CISA • ISACA CISM • (ISC)2 CISSP • ISACA CISA • (ISC)2 CISSP • ISACA CISA • ISACA CISM ADVANCED (3-5 YEARS’ EX-PERIENCE) • CREST Registered Threat Intelligence Analyst • CREST Registered Technical Security Architect • CCNP Security • CCNP Enterprise • CCNP Security • GSLC • PMI PMP • GCPM • PMI PMP • GREM • (ISC)2 CSSLP • CCNP Enterprise • (ISC)2 CSSLP • GASF • CREST Registered Intrusion Analyst • CREST Certified Infrastructure Tester • CREST Certified Simulated Attack Specialist • ISACA CRISC • ISACA CRISC • GCCC • ISO 27001 Auditor • CCNP Security • ISACA CRISC INTERMEDIATE (2-3 YEARS’ EXPERIENCE) • CompTIA CySA+ • CREST Practitioner Threat Intelligence Analyst • Splunk Core Certified Power User • AWS Associate – Solutions Architect • Microsoft Azure Administrator Associate • PRINCE2 Practitioner • AWS Associate – Solutions Architect • Microsoft Azure Administrator Associate • CBCI • CompTIA CySA+ • CompTIA PenTest+ • Cloud Security Alliance CCSK • PRINCE2 Practitioner • CompTIA Cloud+ • PRINCE2 Practitioner • CompTIA Cloud+ • AWS Associate – Solutions Architect • MCSA • AWS Associate – SysOps Administrator • MCSA • GSSP • Scrum Alliance CSM • GCFA • CertNexus CFR • CREST Practitioner Intrusion Analyst • GCIA • CompTIA PenTest+ • CREST Registered Penetration Tester • OSCP • CBCI • GDPR Practitioner • ISO 27001 Practitioner • Cloud Security Alliance CCSK • GDPR Practitioner • ISO 27001 Practitioner • CBCI • CompTIA CySA+ • CompTIA PenTest+ • PRINCE2 Practitioner • AWS Associate – Solutions Architect FOUNDATION (1-2 YEARS’ EXPERIENCE) • CCNA Cyber Ops • CompTIA Network+ • CompTIA Security+ • GSEC • Splunk Core Certified User • CCNA • CompTIA Security+ • CCNA • CompTIA Security+ • CompTIA Server+ • EC-Council CND • CCNA • CompTIA Security+ • CompTIA CTT+ • CompTIA Network+ • CompTIA Security+ • EC-Council CEH • ITIL Foundation • CompTIA Project+ • CompTIA Security+ • CompTIA Linux+ • CompTIA Security+ • LPIC-1 • CompTIA Network+ • CompTIA Security+ • (ISC)2 SSCP • ITIL Foundation • CompTIA Linux+ • GWEB • LPIC-1 • CompTIA Security+ • EC-Council CHFI • GCFE • CompTIA Security+ • GCIH • (ISC)2 SSCP • CompTIA Network+ • CompTIA Security+ • CREST Practitioner Security Analyst • EC-Council CEH • CompTIA Linux+ • LPIC-1 • BCS CISMP • CompTIA Security+ • GSEC • (ISC)2 CAP • ISO 27001 Foundation • CompTIA Security+ • GSNA • (ISC)2 CAP • ISO 27001 Foundation • CCNA • CompTIA Security+ • EC-Council CEH • GSEC EXPERIENCE LEVEL
- 2. APM Group FOUNDATION • ISO 27001 Foundation INTERMEDIATE • GDPR Practitioner • ISO 27001 Practitioner ADVANCED • ISO 27001 Auditor Amazon Web Services INTERMEDIATE • AWS Associate – Solutions Architect • AWS Associate – SysOps Administrator Axelos FOUNDATION • ITIL Foundation INTERMEDIATE • PRINCE2 Practitioner Business Continuity Institute (BCI) INTERMEDIATE • CBCI: Certificate of the Business Continuity Institute British Computer Society (BCS) FOUNDATION • CISMP: Certificate of Information Security Management Principles Cisco Systems FOUNDATION • CCNA: Cisco Certified Network Associate • CCNA Cyber Ops: Cisco Certified Network Associate Cyber Operations ADVANCED • CCNP Enterprise: Cisco Certified Network Professional Enterprise • CCNP Security: Cisco Certified Network Professional Security EXPERT • CCIE Security: Cisco Certified Internetwork Expert Security CertNexus INTERMEDIATE • CFR: CyberSec First Responder CompTIA FOUNDATION • CTT+: Certified Technical Trainer • Linux+ • Network+ • Project+ • Security+ • Server+ INTERMEDIATE • Cloud+ • CySA+: Cyber Security Analyst • PenTest+: Penetration Tester EXPERT • CASP+: CompTIA Advanced Security Practitioner Cloud Security Alliance INTERMEDIATE • CCSK: Certificate of Cloud Security Knowledge CREST FOUNDATION • Practitioner Security Analyst INTERMEDIATE • Practitioner Threat Intelligence Analyst • Practitioner Intrusion Analyst • Registered Penetration Tester ADVANCED • Registered Threat Intelligence Analyst • Registered Technical Security Architect • Registered Intrusion Analyst • Certified Infrastructure Tester • Certified Simulated Attack Specialist EXPERT • Certified Threat Intelligence Manager • Certified Malware Reverse Engineer • Certified Network Intrusion Analyst • Certified Incident Manager • Certified Simulated Attack Manager EC-Council FOUNDATION • CEH: Certified Ethical Hacker • CHFI: Computer Hacking Forensics Investigator • CND: Certified Network Defender EXPERT • CCISO: Certified Chief Information Security Officer GIAC FOUNDATION • GCFE: GIAC Certified Forensics Examiner • GCIH: GIAC Certified Incident Handler • GSNA: GIAC Systems and Network Auditors • GSEC: GIAC Security Essentials Certification • GWEB: GIAC Certified Web Application Defender INTERMEDIATE • GCFA: GIAC Certified Forensic Analyst • GCIA: GIAC Certified Intrusion Analyst • GSSP: GIAC Secure Software Programmer ADVANCED • GASF: GIAC Advanced Smartphone Forensics • GCCC: GIAC Critical Controls Certification • GCPM: GIAC Certified Project Manager Certification • GSLC: GIAC Security Leadership • GREM: GIAC Reverse Engineering Malware EXPERT • GCTI: GIAC Cyber Threat Intelligence • GNFA: GIAC Network Forensic Analyst ISACA ADVANCED • CRISC: Certified in Risk and Information Systems Control EXPERT • CGEIT: Certified in the Governance of Enterprise IT • CISA: Certified Information Systems Auditor • CISM: Certified Information Security Manager (ISC)2 FOUNDATION • CAP: Security Assessment and Authorisation Certification • SSCP: Systems Security Certified Practitioner ADVANCED • CSSLP: Certified Secure Software Lifecycle Professional EXPERT • CISSP: Certified Information Systems Security Professional Linux Professional Institute FOUNDATION • LPIC-1: Systems Administrator Microsoft INTERMEDIATE • Microsoft Azure Administrator Associate • MCSA: Microsoft Certified Solutions Associate Offensive Security INTERMEDIATE • OSCP: Offensive Security Certified Professional PMI ADVANCED • PMP: Project Management Professional Scrum Alliance INTERMEDIATE • CSM: Certified ScrumMaster Splunk FOUNDATION • Splunk Core Certified User INTERMEDIATE • Splunk Core Certified Power User