Why Host-Based Scanning is Critical for Managing Vulnerabilities [Infographic]
•
0 likes•102 views
Check out this infographic to grasp why host-based scanning is a critical capability for managing vulnerabilities. Learn more: https://www.beyondtrust.com/resources/data-sheet/retina-host-security-scanner/ https://www.beyondtrust.com/products/retina/
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Viewers also liked
Viewers also liked (14)
Entity provider selection confusion attacks in JAX-RS applications

Entity provider selection confusion attacks in JAX-RS applications
PBISE : Installation and Administration Guide v7.5

PBISE : Installation and Administration Guide v7.5
Linux host orchestration with Foreman, Puppet and Gitlab

Linux host orchestration with Foreman, Puppet and Gitlab
Eyes Wide Shut: What Do Your Passwords Do When No One is Watching?

Eyes Wide Shut: What Do Your Passwords Do When No One is Watching?
Puppet Camp DC 2014: Managing Puppet with MCollective

Puppet Camp DC 2014: Managing Puppet with MCollective
CfgMgmtCamp 2015 - Managing the Content Lifecycle with Katello

CfgMgmtCamp 2015 - Managing the Content Lifecycle with Katello
More from BeyondTrust
More from BeyondTrust (20)
The 5 Crazy Mistakes IoT Administrators Make with System Credentials

The 5 Crazy Mistakes IoT Administrators Make with System Credentials
10 Steps to Better Windows Privileged Access Management

10 Steps to Better Windows Privileged Access Management
Tips to Remediate your Vulnerability Management Program

Tips to Remediate your Vulnerability Management Program
Sudo Mode (part 2): How Privilege Mistakes could Dismantle your Entire Enterp...

Sudo Mode (part 2): How Privilege Mistakes could Dismantle your Entire Enterp...
Unearth Active Directory Threats Before They Bury Your Enterprise

Unearth Active Directory Threats Before They Bury Your Enterprise
8-step Guide to Administering Windows without Domain Admin Privileges

8-step Guide to Administering Windows without Domain Admin Privileges
Securing DevOps through Privileged Access Management

Securing DevOps through Privileged Access Management
Crush Common Cybersecurity Threats with Privilege Access Management

Crush Common Cybersecurity Threats with Privilege Access Management
Active Directory Auditing Tools: Building Blocks or just a Handful of Dust?

Active Directory Auditing Tools: Building Blocks or just a Handful of Dust?
Avoiding the 10 Deadliest and Most Common Sins for Securing Windows

Avoiding the 10 Deadliest and Most Common Sins for Securing Windows
Unix / Linux Privilege Management: What a Financial Services CISO Cares About

Unix / Linux Privilege Management: What a Financial Services CISO Cares About
Why Federal Systems are Immune from Ransomware...& other Grim Fairy Tales)

Why Federal Systems are Immune from Ransomware...& other Grim Fairy Tales)
The Hacker Playbook: How to Think like a Cybercriminal to Reduce Risk

The Hacker Playbook: How to Think like a Cybercriminal to Reduce Risk
Hacker techniques for bypassing existing antivirus solutions & how to build a...

Hacker techniques for bypassing existing antivirus solutions & how to build a...
How Federal Agencies Can Build a Layered Defense for Privileged Accounts

How Federal Agencies Can Build a Layered Defense for Privileged Accounts
Using Advanced Threat Analytics to Prevent Privilege Escalation Attacks

Using Advanced Threat Analytics to Prevent Privilege Escalation Attacks
Prevent Data Leakage Using Windows Information Protection (WIP)

Prevent Data Leakage Using Windows Information Protection (WIP)
Enemy from Within: Managing and Controlling Access

Enemy from Within: Managing and Controlling Access
Recently uploaded
API Development involves designing, building, and implementing Application Programming Interfaces (APIs) that enable seamless communication and data exchange between different software systems. There are various types of APIs, including RESTful APIs, SOAP APIs, GraphQL, and WebSocket APIs, each serving specific purposes. API specifications, such as OpenAPI Specification (OAS) and GraphQL Schema Definition Language (SDL), define the structure and behavior of APIs. Documentation plays a crucial role in API development, providing clear instructions, examples, and troubleshooting guidance for developers who want to integrate with the API.
Click Here For More Details: https://www.connectinfosoft.com/rest-api-development-service/What is an API Development- Definition, Types, Specifications, Documentation.pdf

What is an API Development- Definition, Types, Specifications, Documentation.pdfConnect Infosoft Technologies Private Limited
Recently uploaded (20)
The Strategic Impact of Buying vs Building in Test Automation

The Strategic Impact of Buying vs Building in Test Automation
Jax, FL Admin Community Group 05.14.2024 Combined Deck

Jax, FL Admin Community Group 05.14.2024 Combined Deck
how-to-download-files-safely-from-the-internet.pdf

how-to-download-files-safely-from-the-internet.pdf
StrimziCon 2024 - Transition to Apache Kafka on Kubernetes with Strimzi.pdf

StrimziCon 2024 - Transition to Apache Kafka on Kubernetes with Strimzi.pdf
Microsoft 365 Copilot; An AI tool changing the world of work _PDF.pdf

Microsoft 365 Copilot; An AI tool changing the world of work _PDF.pdf
Lessons Learned from Building a Serverless Notifications System.pdf

Lessons Learned from Building a Serverless Notifications System.pdf
OpenChain @ LF Japan Executive Briefing - May 2024

OpenChain @ LF Japan Executive Briefing - May 2024
Odoo vs Shopify: Why Odoo is Best for Ecommerce Website Builder in 2024

Odoo vs Shopify: Why Odoo is Best for Ecommerce Website Builder in 2024
Entropy, Software Quality, and Innovation (presented at Princeton Plasma Phys...

Entropy, Software Quality, and Innovation (presented at Princeton Plasma Phys...
5 Reasons Driving Warehouse Management Systems Demand

5 Reasons Driving Warehouse Management Systems Demand
Tree in the Forest - Managing Details in BDD Scenarios (live2test 2024)

Tree in the Forest - Managing Details in BDD Scenarios (live2test 2024)
GraphSummit Stockholm - Neo4j - Knowledge Graphs and Product Updates

GraphSummit Stockholm - Neo4j - Knowledge Graphs and Product Updates
What is an API Development- Definition, Types, Specifications, Documentation.pdf

What is an API Development- Definition, Types, Specifications, Documentation.pdf
Workforce Efficiency with Employee Time Tracking Software.pdf

Workforce Efficiency with Employee Time Tracking Software.pdf
Automate your OpenSIPS config tests - OpenSIPS Summit 2024

Automate your OpenSIPS config tests - OpenSIPS Summit 2024
Why Host-Based Scanning is Critical for Managing Vulnerabilities [Infographic]
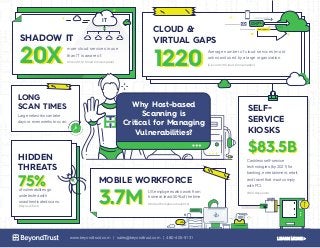
- 1. SELF- SERVICE KIOSKS $83.5B$83.5B Cashless self-service technologies (by 2021) for banking, entertainment, retail, and travel that must comply with PCI. (BCC Research) CLOUD & VIRTUAL GAPS 12201220 Average number of cloud services (most unknown) used by a large organization. (Cisco 2016 Cloud Consumption) Large networks can take days or even weeks to scan. LONG SCAN TIMES US employees who work from home at least 50% of the time MOBILE WORKFORCE 3.7M3.7M (Global Workplace Analytics) of vulnerabilites go undetected with unauthenticated scans. HIDDEN THREATS 75%75% (BeyondTrust) IT SHADOW IT 20X20X more cloud services in use than IT is aware of. (Cisco 2016 Cloud Consumption) Why Host-based Scanning is Critical for Managing Vulnerabilities? www.beyondtrust.com | sales@beyondtrust.com | 480-405-9131 LEARN MORE >
