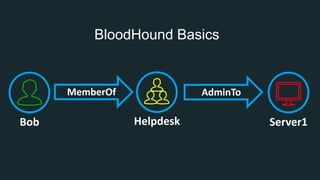
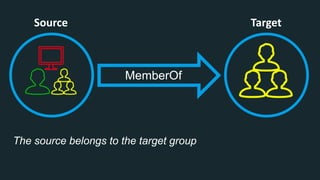
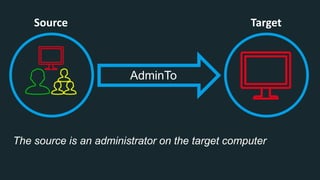
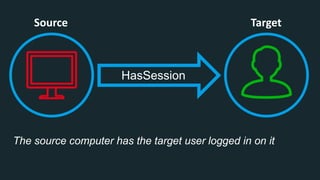
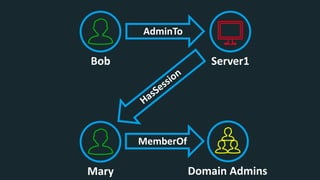
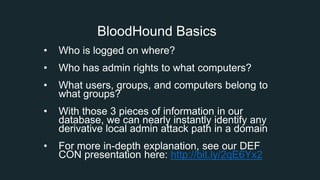
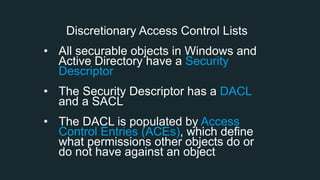
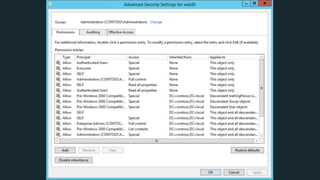
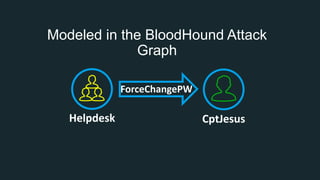
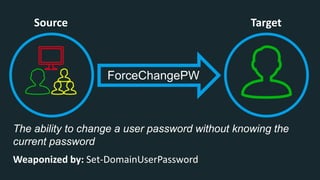
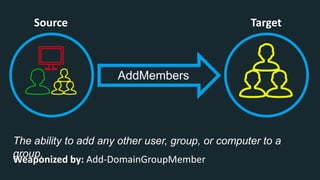
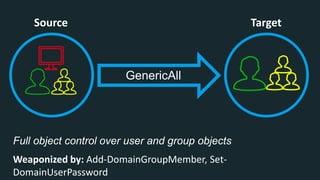
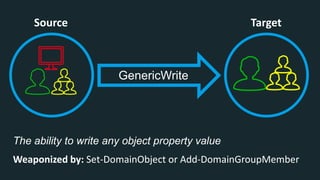
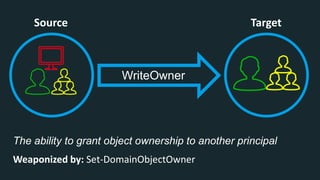
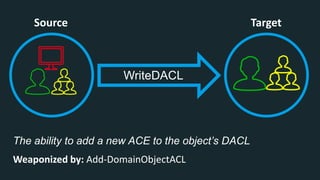
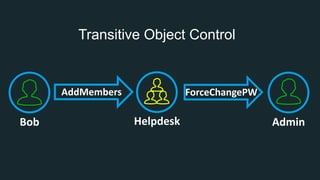
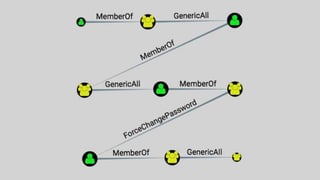
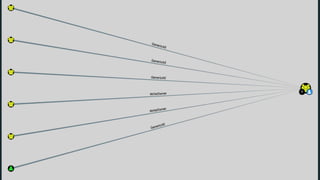
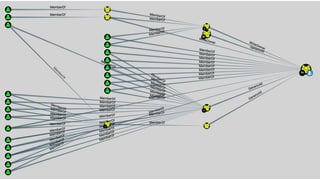
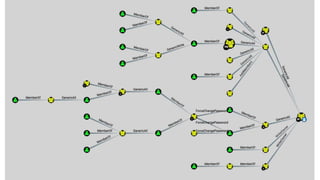
The document discusses BloodHound, a tool created by experts at Specter Ops, for identifying domain attack paths using graph theory and easy data collection methods. It outlines various features and functionalities such as tracking admin rights, user logins, and permissions within Active Directory, while highlighting notable contributors and presentations at cybersecurity conferences. The latest updates in BloodHound 1.3 include analysis of discretionary access control lists and various attack pathways through which privileges can be exploited.