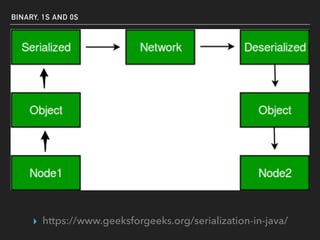
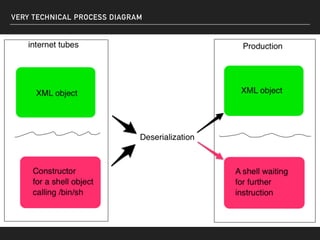
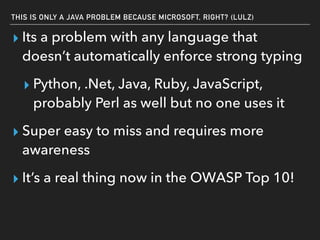
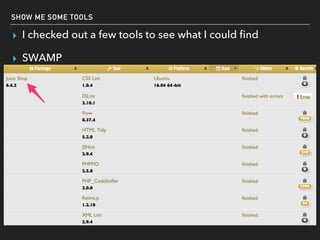
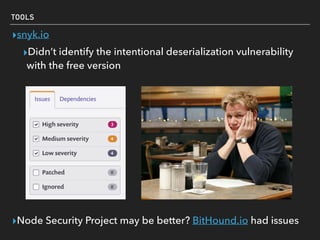
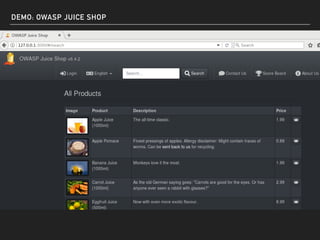
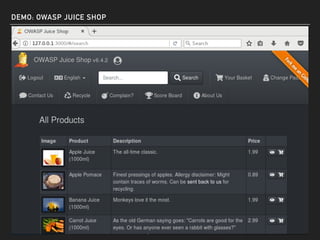
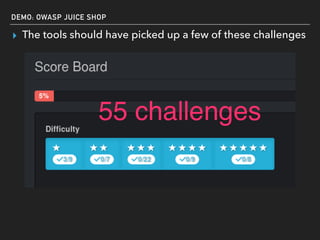
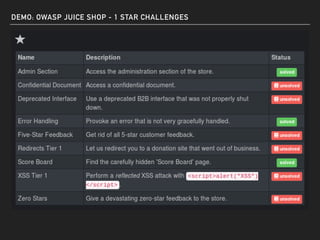
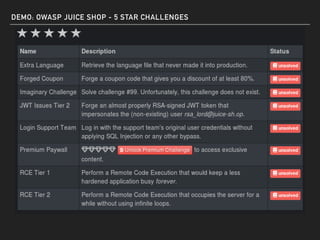
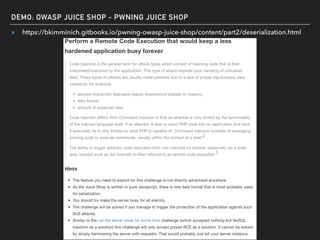
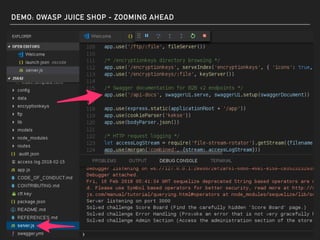
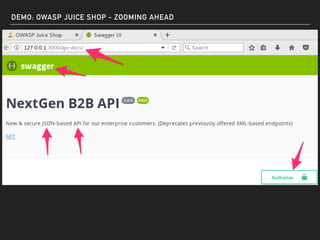
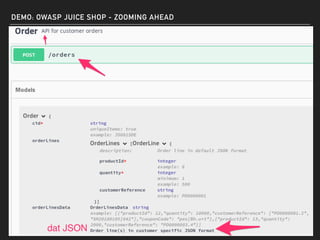
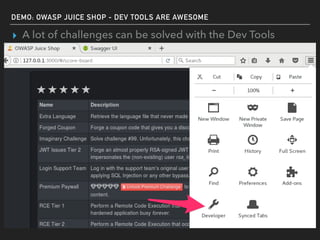
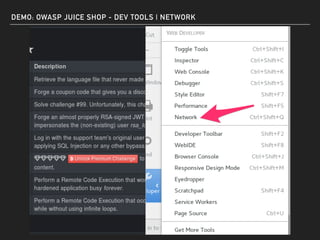
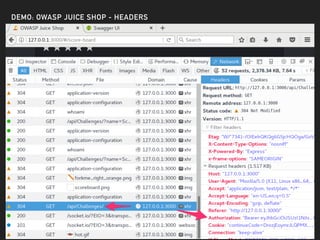
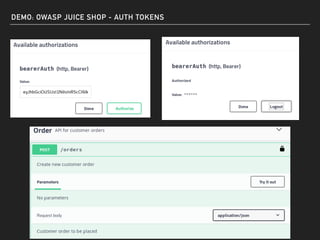
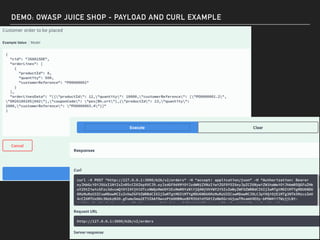
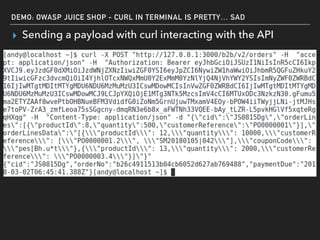
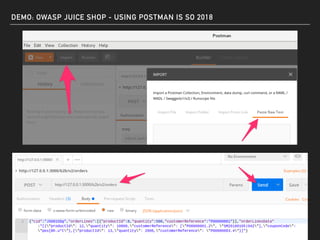
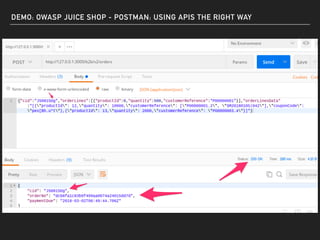
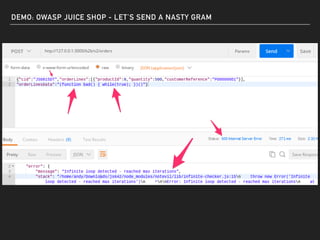
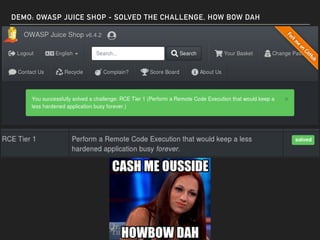
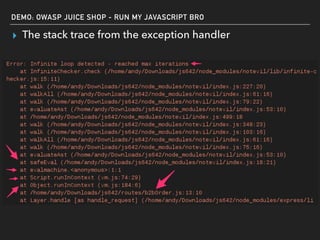
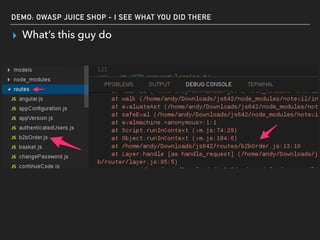
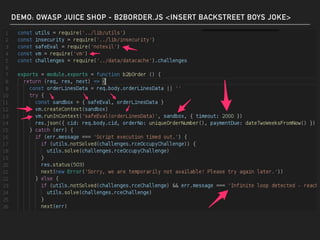
The document discusses deserialization vulnerabilities, notably in programming languages like Java, Python, and .NET, emphasizing the risks associated with weak typing and serialization techniques. It highlights various tools available for detecting these issues and demonstrates the OWASP Juice Shop as a target for testing deserialization exploits. Finally, it encourages developers to understand their applications and actively seek vulnerabilities through practical testing and exploration.