The document provides guidelines for hardening Apache Cassandra systems to meet compliance standards and improve security. It covers key areas such as encryption at rest, securing inter-node and client-server communication, and authentication best practices tailored to various industry requirements. The content emphasizes the importance of implementing good security practices to protect data and maintains functionality without introducing single points of failure.






























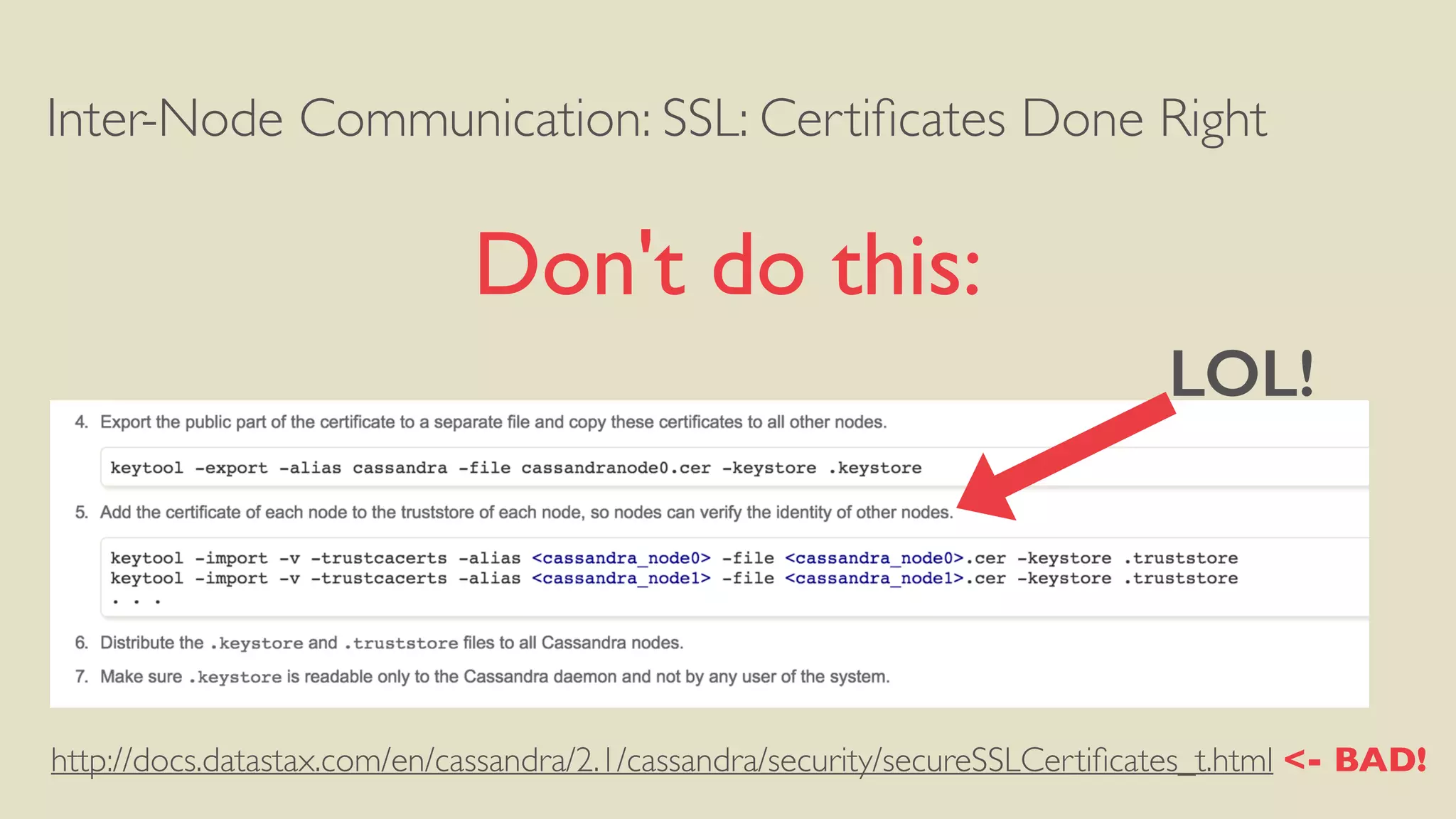



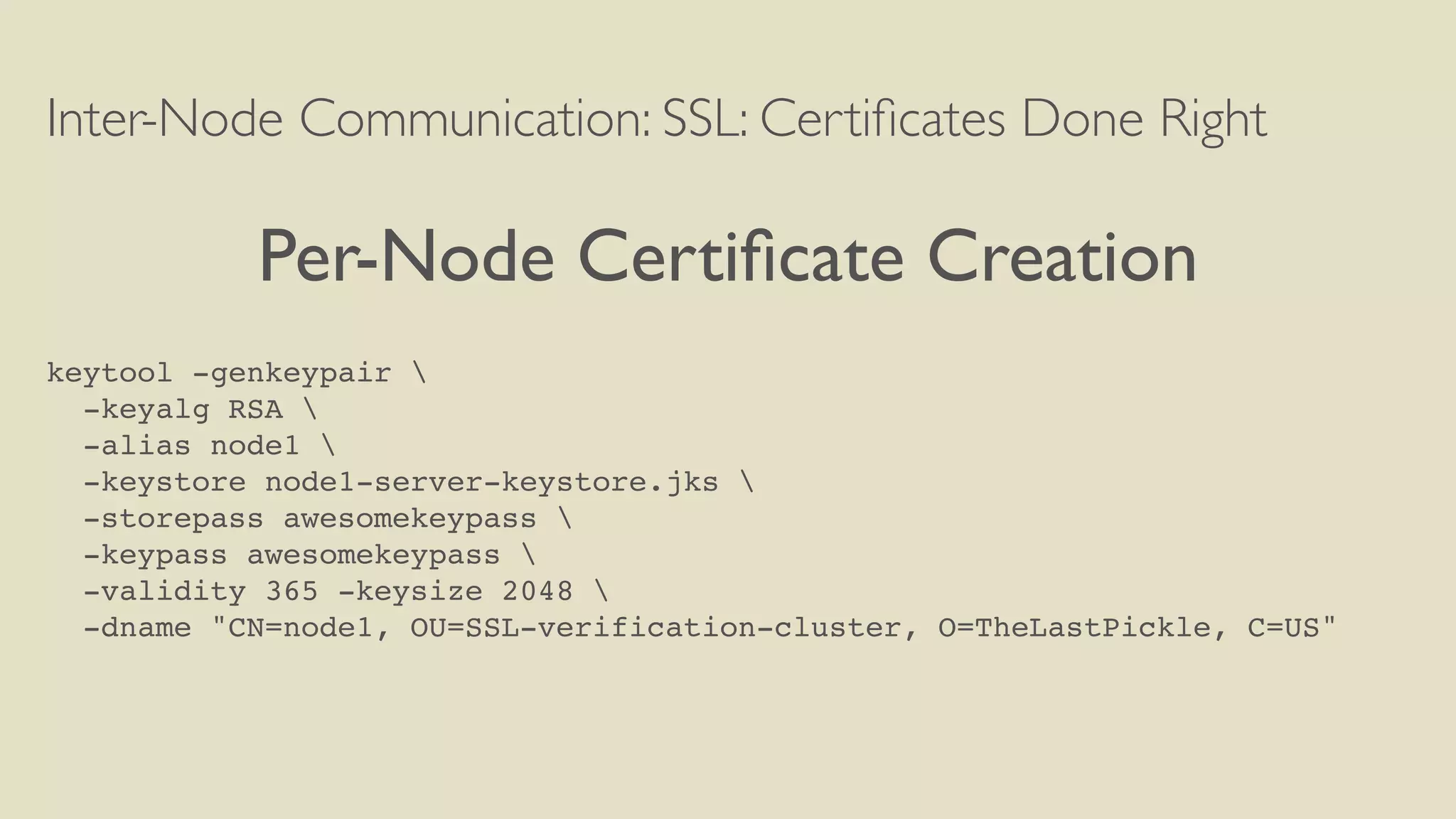
![Inter-Node Communication: SSL: Certificates Done Right
'gen_ca_cert.conf'
[ req ]
distinguished_name = req_distinguished_name
prompt = no
output_password = mypass
default_bits = 2048
[ req_distinguished_name ]
C = US
ST = TX
L = Austin
O = TLP
OU = TestCluster
CN = TestClusterMasterCA
emailAddress = info@thelastpickl.com](https://image.slidesharecdn.com/sea-hardeningcassandraforcomplianceorparanoia-160120215917/75/Seattle-C-Meetup-Hardening-cassandra-for-compliance-or-paranoia-35-2048.jpg)










![Inter-Node Communication: SSL Done Right
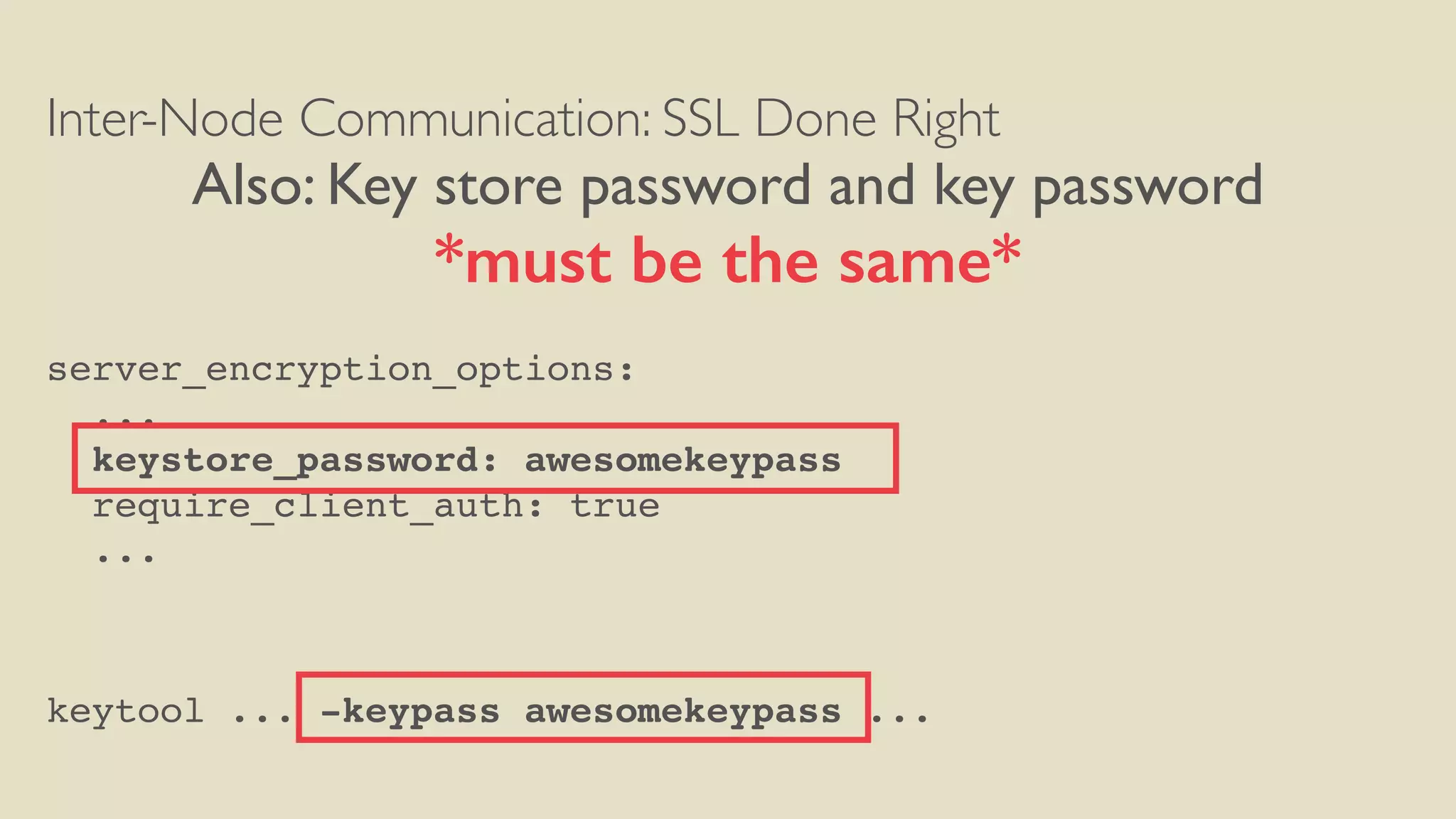
server_encryption_options:
internode_encryption: all
keystore: conf/server-keystore.jks
keystore_password: awesomekeypass
truststore: conf/server-truststore.jks
truststore_password: truststorepass
protocol: TLS
algorithm: SunX509
store_type: JKS
cipher_suites: [TLS_RSA_WITH_AES_256_CBC_SHA]
require_client_auth: true](https://image.slidesharecdn.com/sea-hardeningcassandraforcomplianceorparanoia-160120215917/75/Seattle-C-Meetup-Hardening-cassandra-for-compliance-or-paranoia-47-2048.jpg)
![Inter-Node Communication: SSL Done Right
server_encryption_options:
internode_encryption: all
keystore: conf/server-keystore.jks
keystore_password: awesomekeypass
truststore: conf/server-truststore.jks
truststore_password: truststorepass
protocol: TLS
algorithm: SunX509
store_type: JKS
cipher_suites: [TLS_RSA_WITH_AES_256_CBC_SHA]
require_client_auth: true
If you don't set this to
true, you might as well
turn encryption off](https://image.slidesharecdn.com/sea-hardeningcassandraforcomplianceorparanoia-160120215917/75/Seattle-C-Meetup-Hardening-cassandra-for-compliance-or-paranoia-48-2048.jpg)
![Inter-Node Communication: SSL Done Right
Export restrictions?
Use128 bit keys
cipher_suites: [TLS_RSA_WITH_AES_128_CBC_SHA]
http://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html
http://docs.oracle.com/javase/8/docs/technotes/guides/security/SunProviders.html#importlimits](https://image.slidesharecdn.com/sea-hardeningcassandraforcomplianceorparanoia-160120215917/75/Seattle-C-Meetup-Hardening-cassandra-for-compliance-or-paranoia-50-2048.jpg)










![Client-Server Communication
client_encryption_options:
enabled: true
keystore: conf/client-keystore.jks
keystore_password: clientkeypass
truststore: conf/client-truststore.jks
truststore_password: clienttrustpass
protocol: TLS
algorithm: SunX509
store_type: JKS
cipher_suites: [TLS_RSA_WITH_AES_256_CBC_SHA]
require_client_auth: true](https://image.slidesharecdn.com/sea-hardeningcassandraforcomplianceorparanoia-160120215917/75/Seattle-C-Meetup-Hardening-cassandra-for-compliance-or-paranoia-61-2048.jpg)
![Client-Server Communication
client_encryption_options:
enabled: false
keystore: conf/client-keystore.jks
keystore_password: clientkeypass
truststore: conf/client-truststore.jks
truststore_password: clienttrustpass
protocol: TLS
algorithm: SunX509
store_type: JKS
cipher_suites: [TLS_RSA_WITH_AES_256_CBC_SHA]
require_client_auth: true
If you don't set this to
true, you might as well
turn encryption off](https://image.slidesharecdn.com/sea-hardeningcassandraforcomplianceorparanoia-160120215917/75/Seattle-C-Meetup-Hardening-cassandra-for-compliance-or-paranoia-62-2048.jpg)