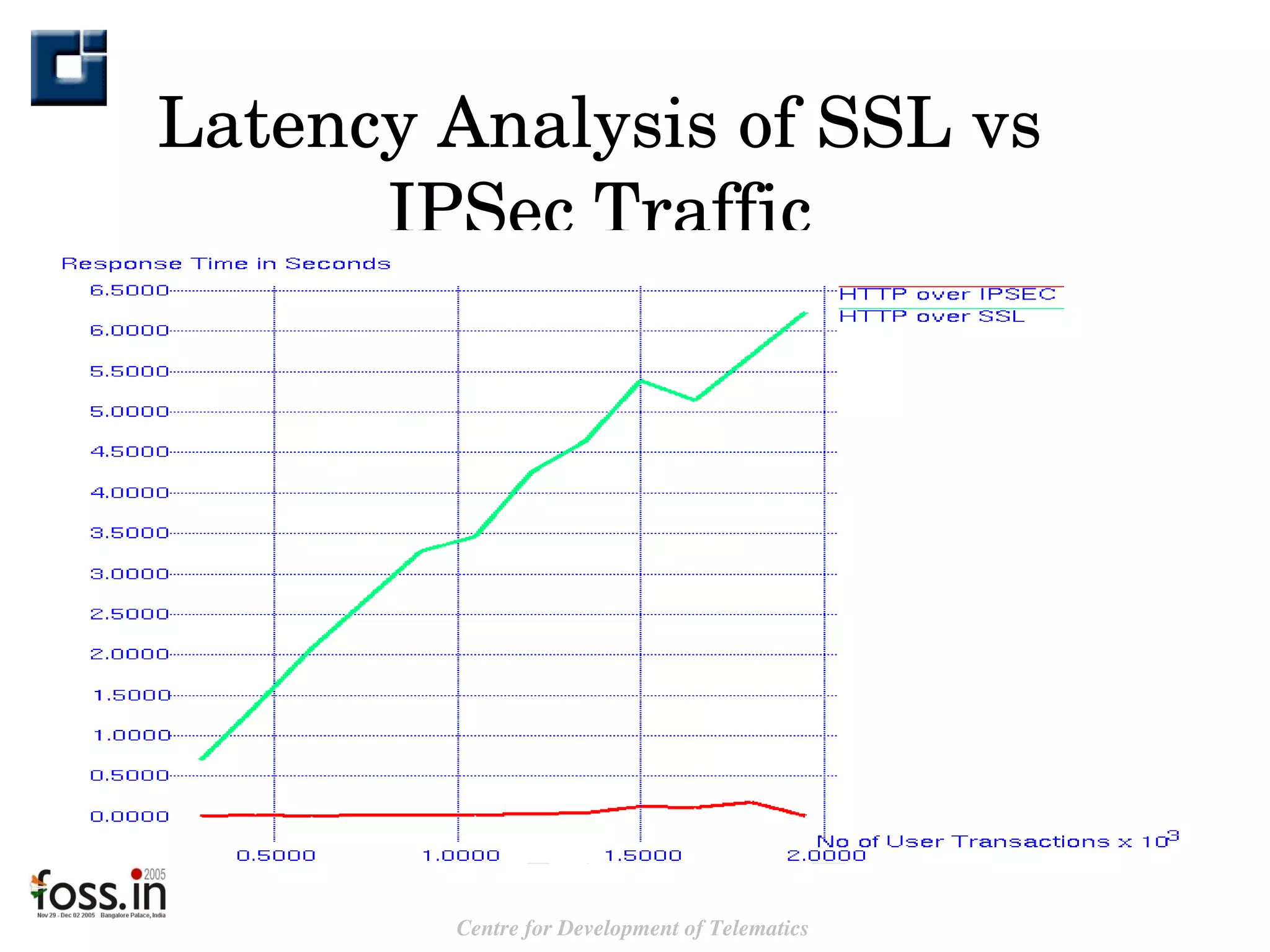
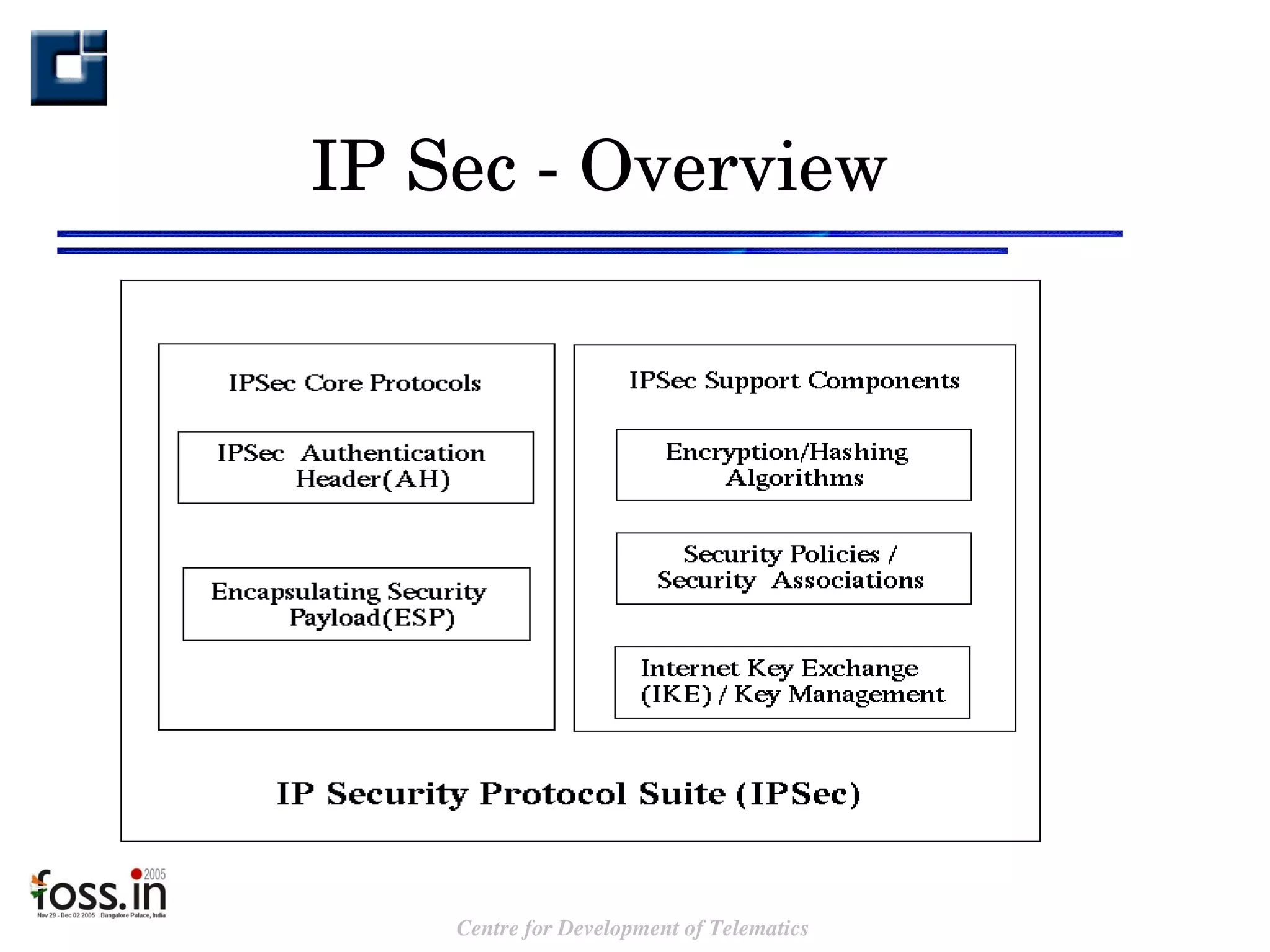
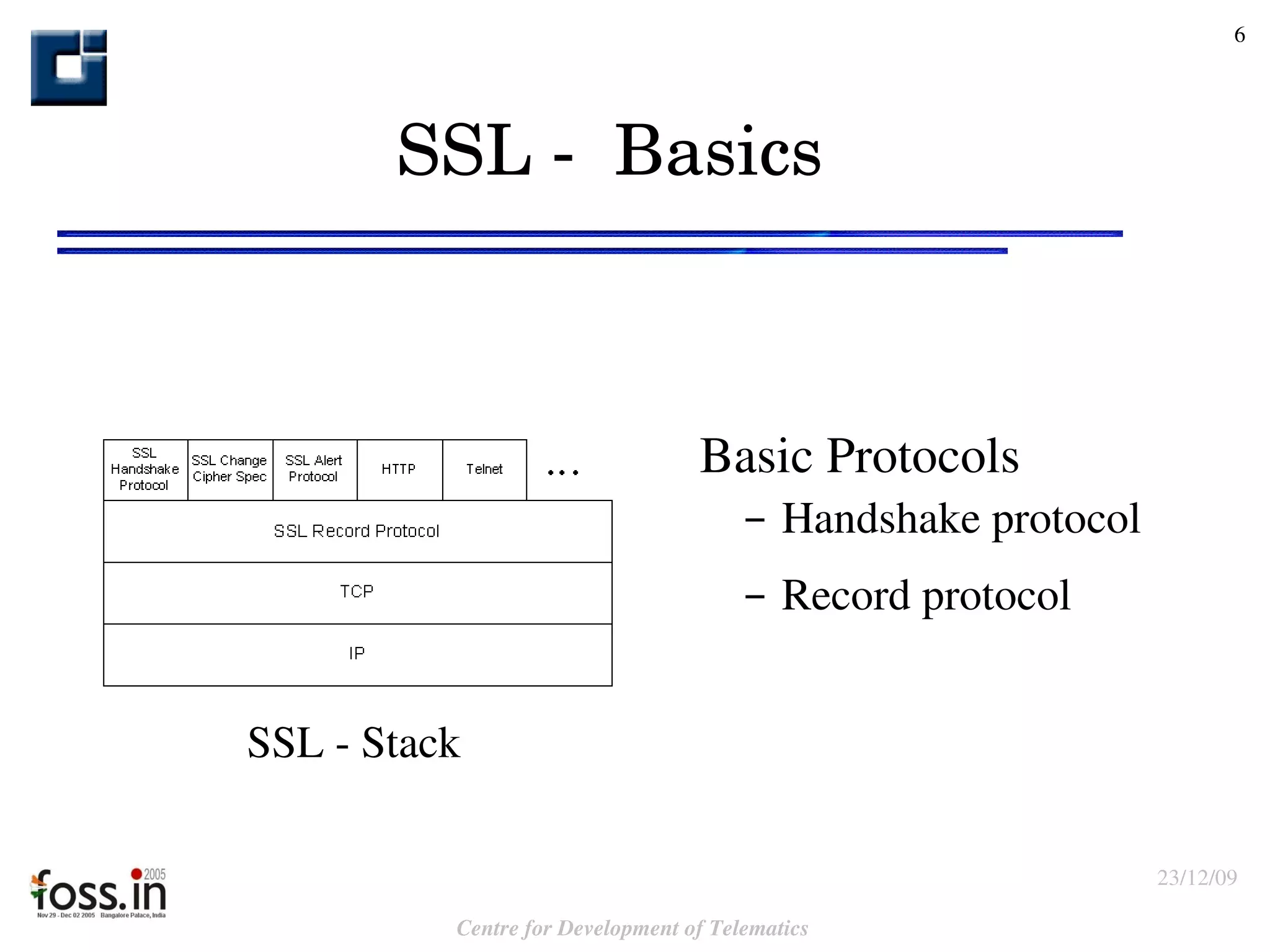
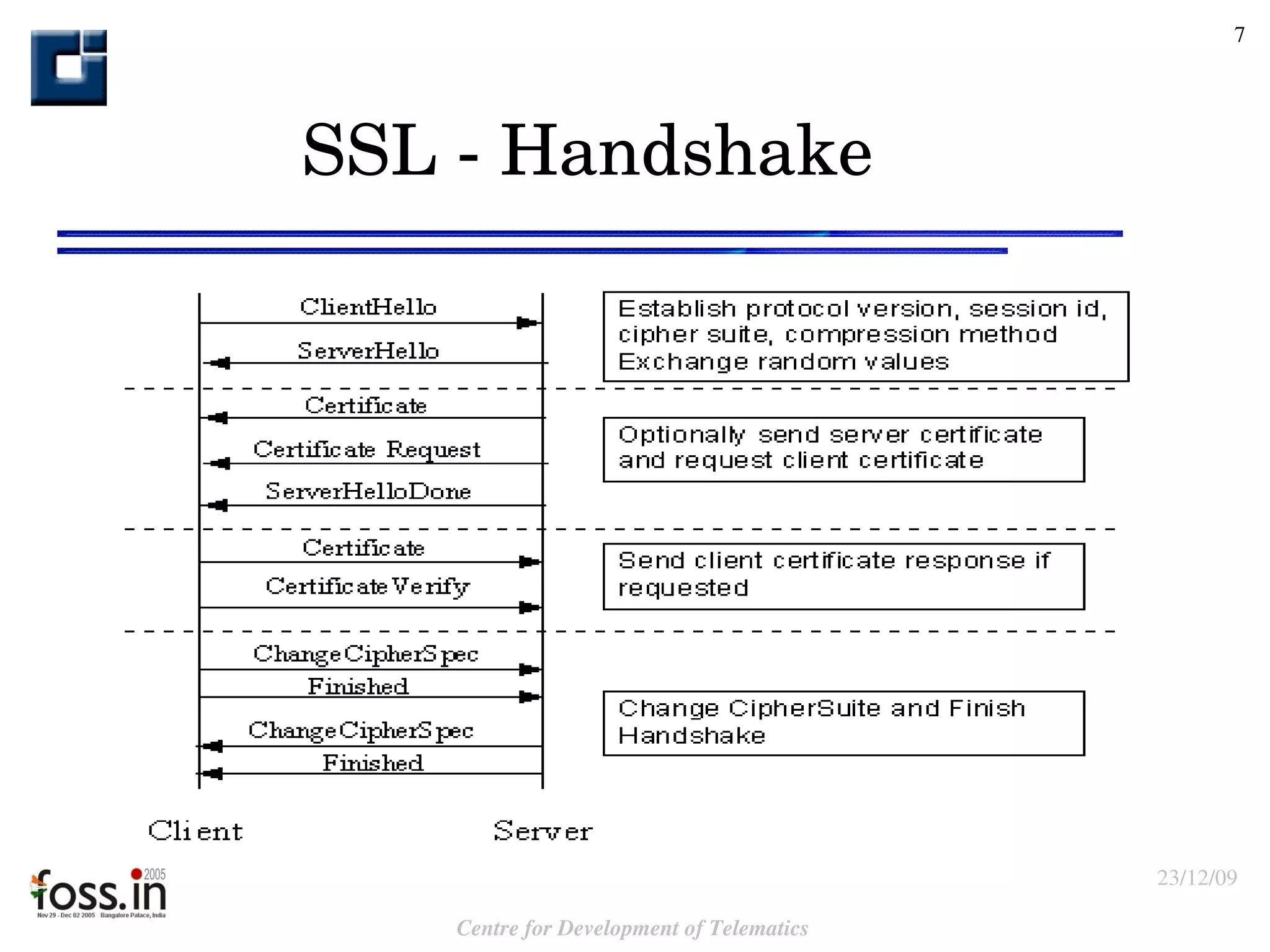
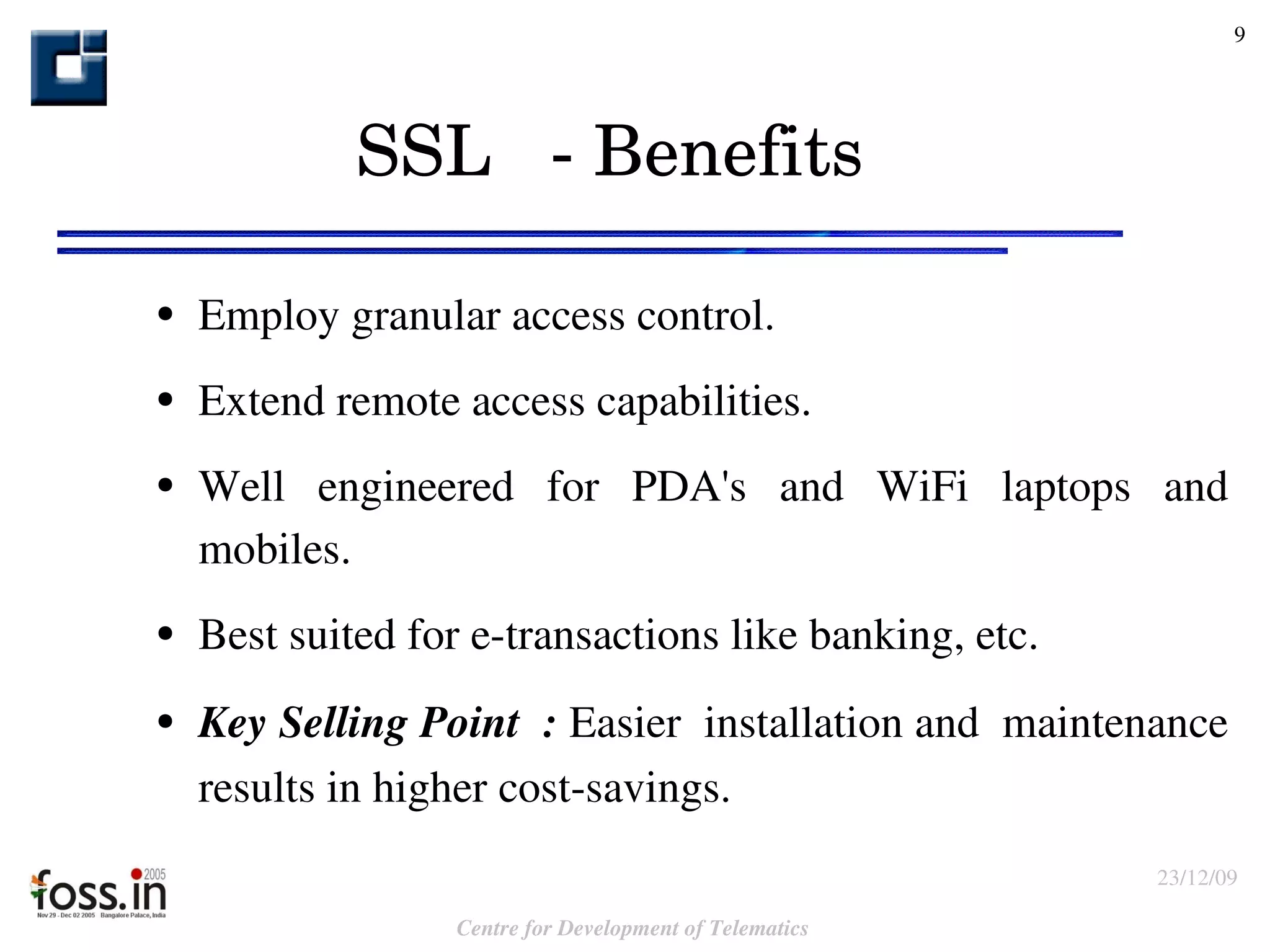
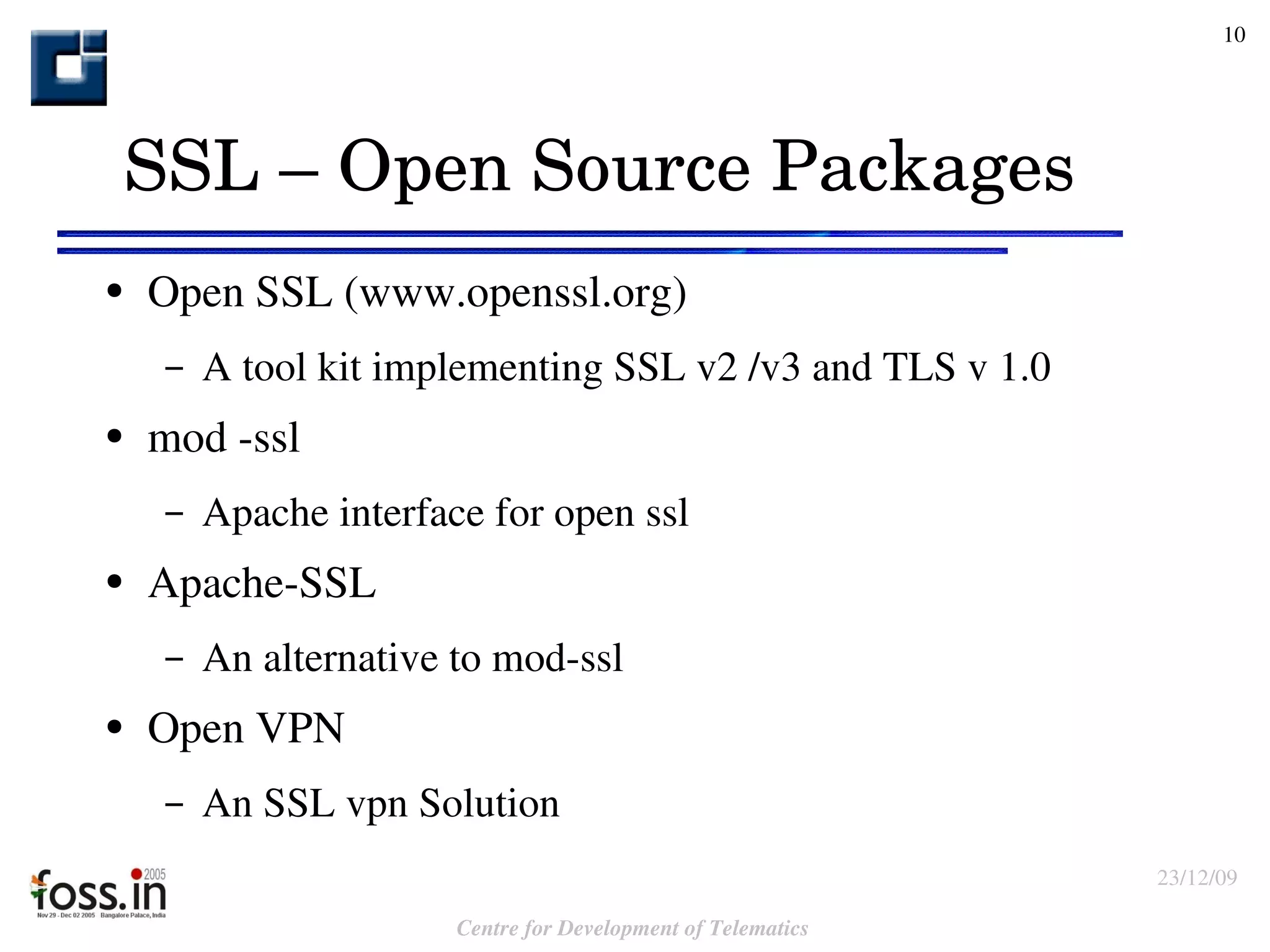
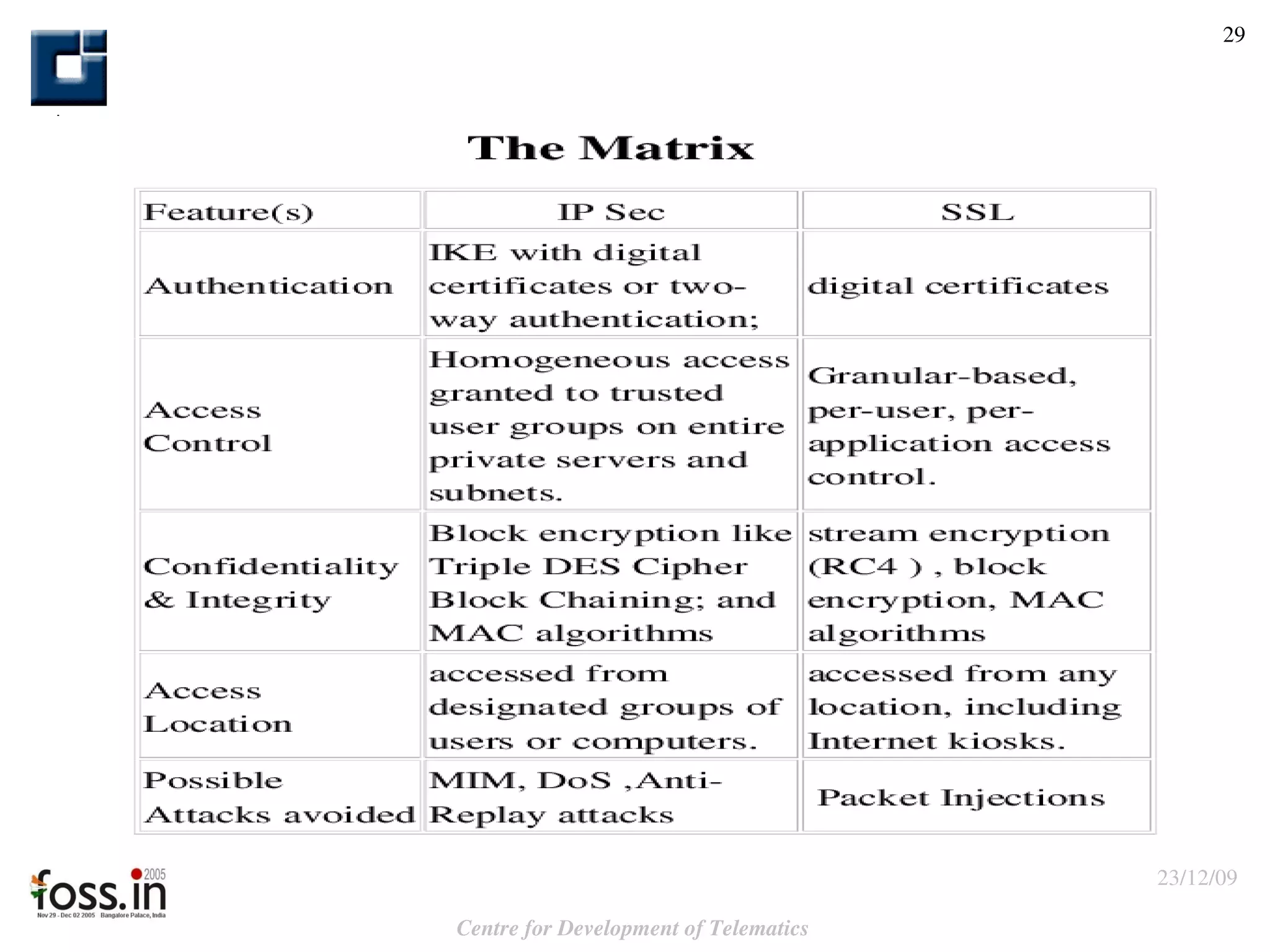
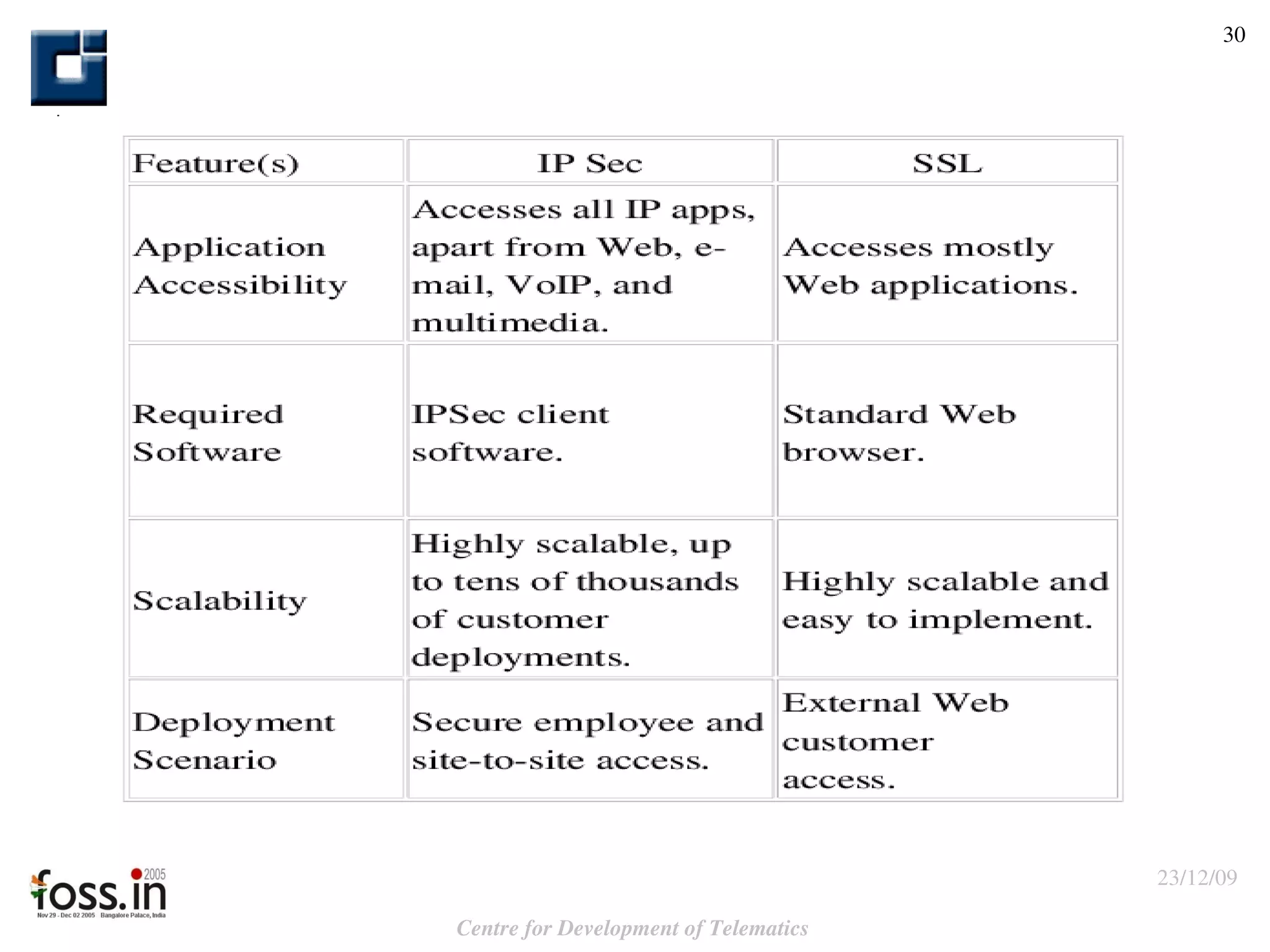
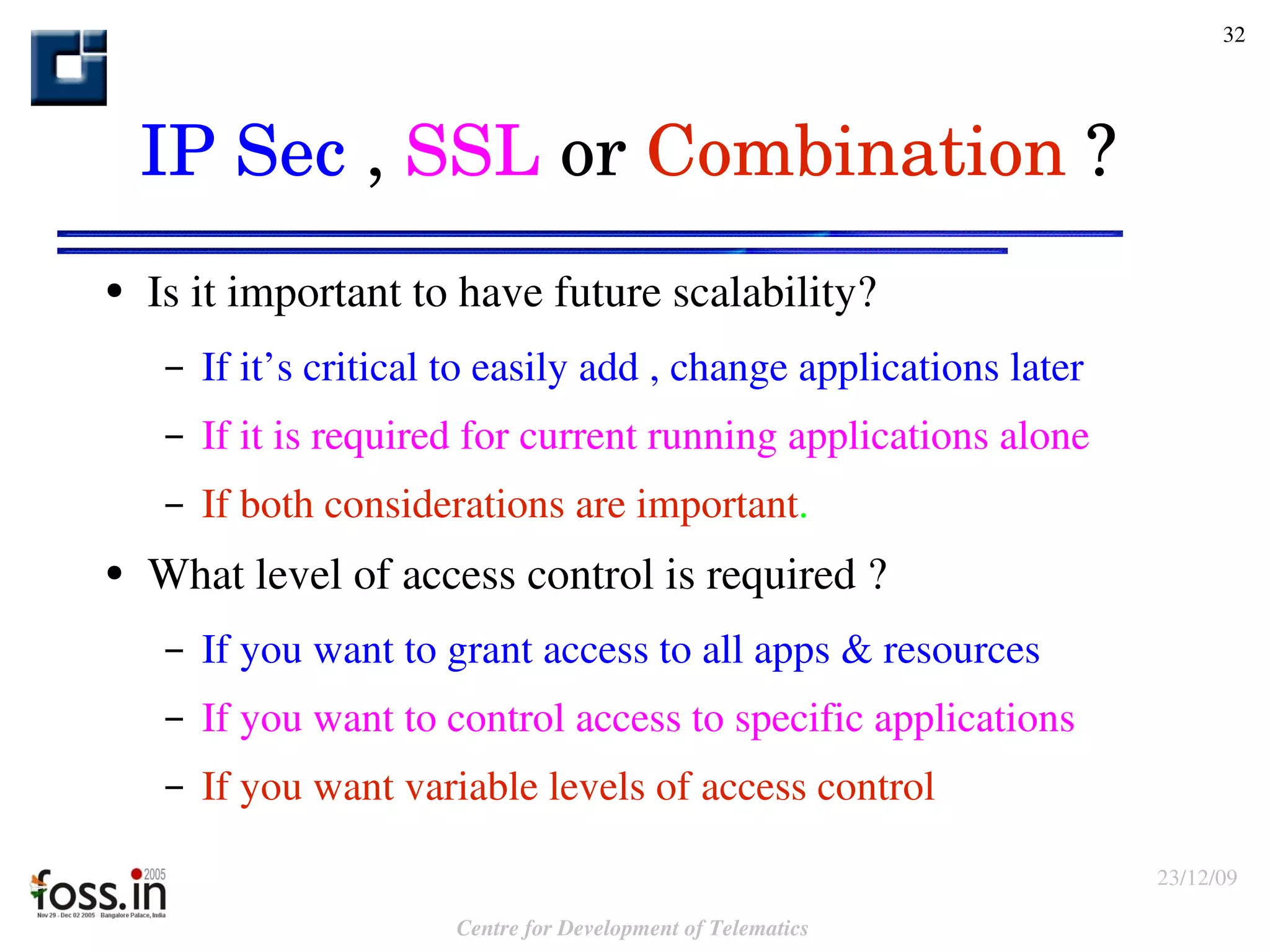
The document compares the security features of SSL and IPsec. It discusses how each protocol provides authentication, confidentiality, integrity and other security services. It also outlines some of the benefits and limitations of each, such as SSL being best for web applications while IPsec provides broader security. Sample use cases are presented to illustrate when each protocol may be best to use.



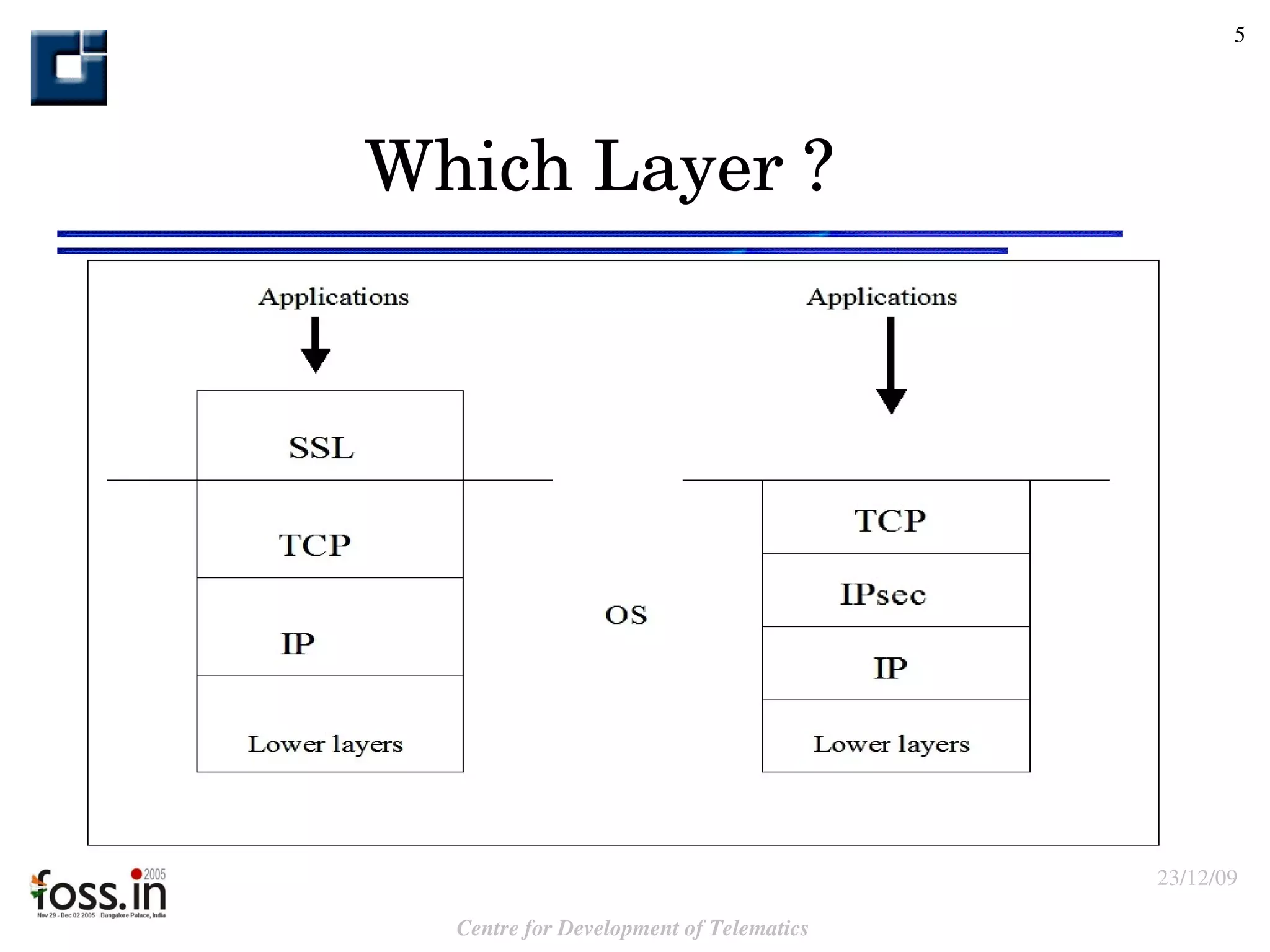











![Contact email : [email_address] [email_address]](https://image.slidesharecdn.com/matrix-091223010609-phpapp02/75/Matrix-37-2048.jpg)