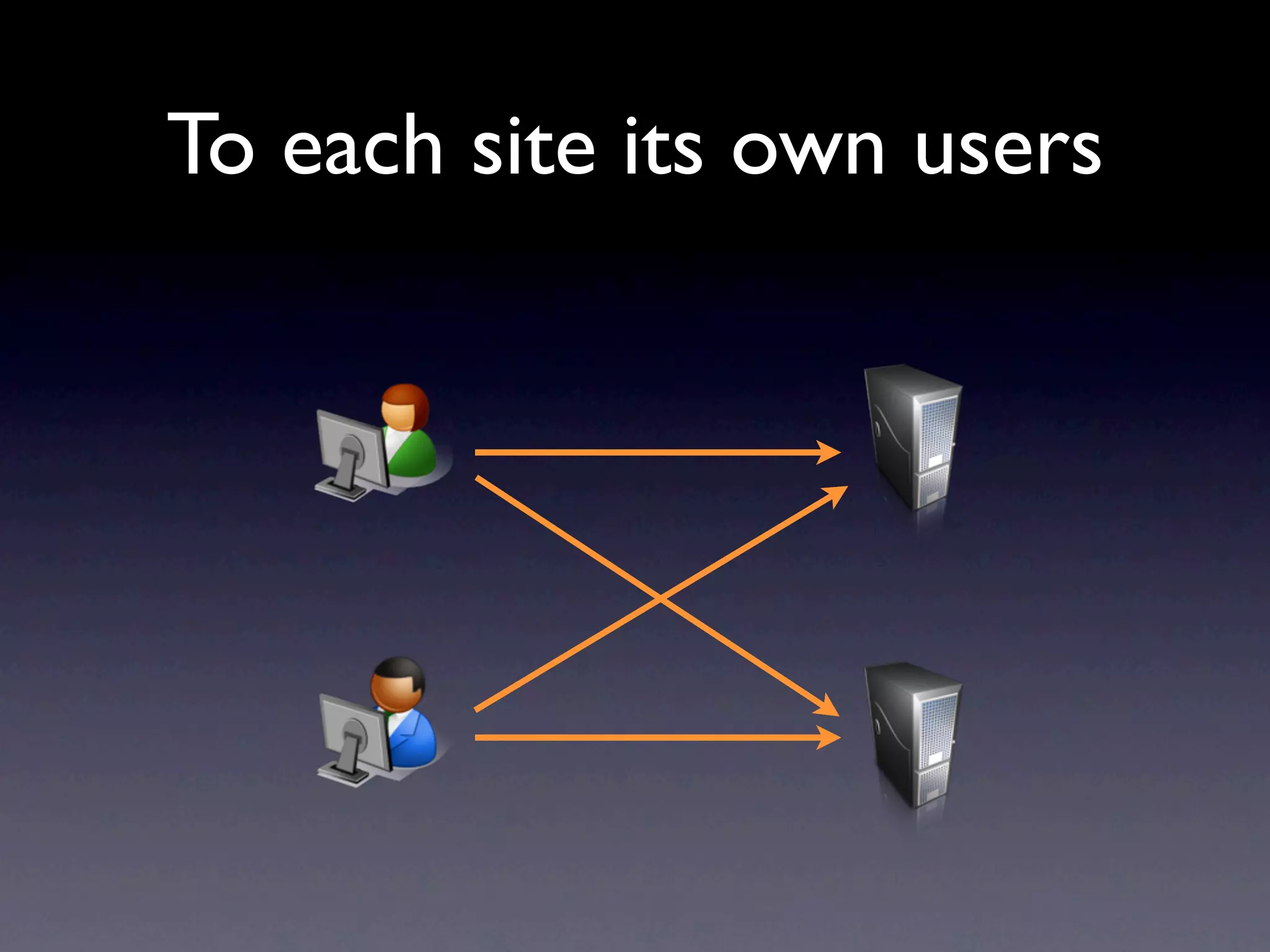
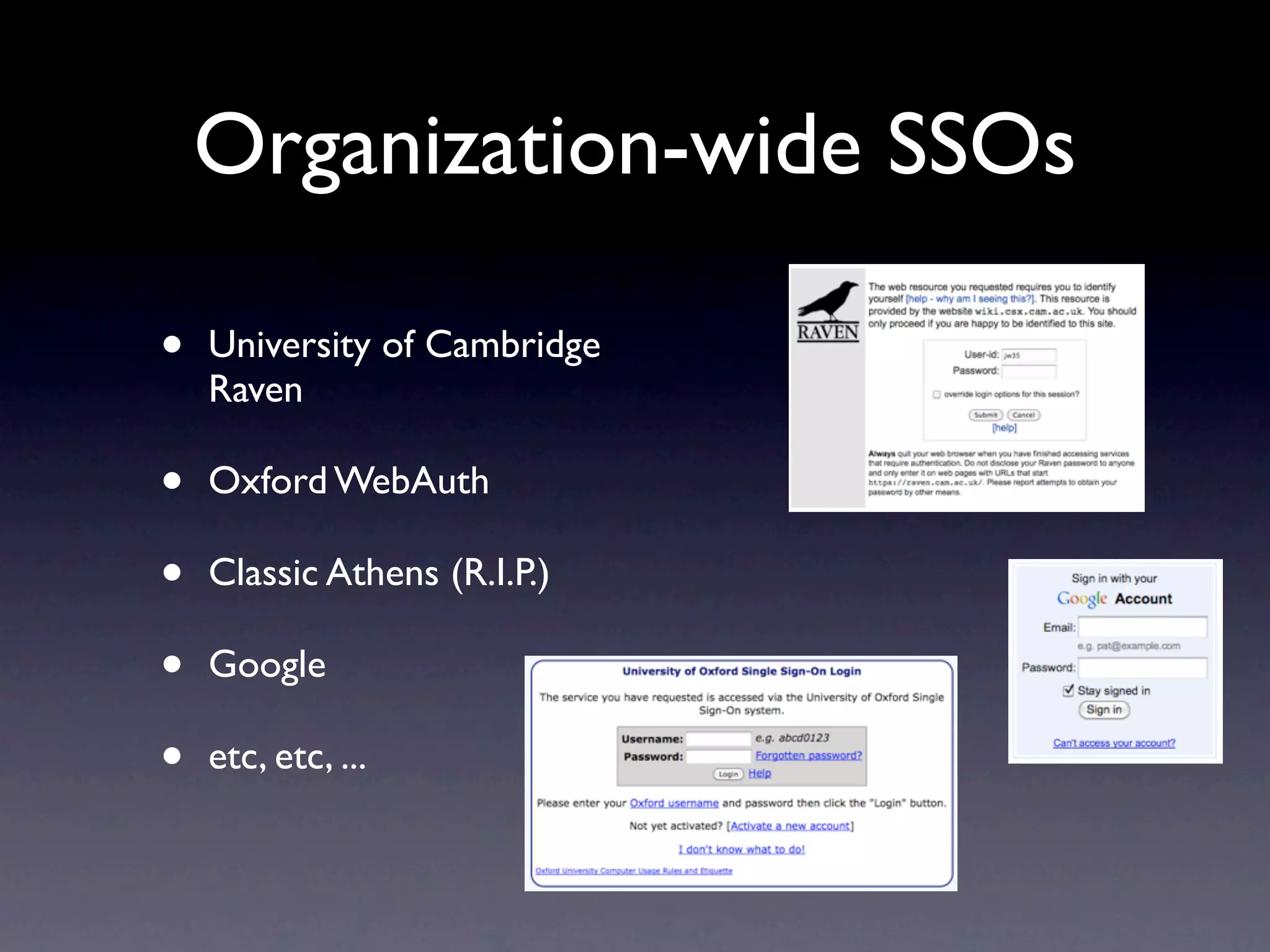
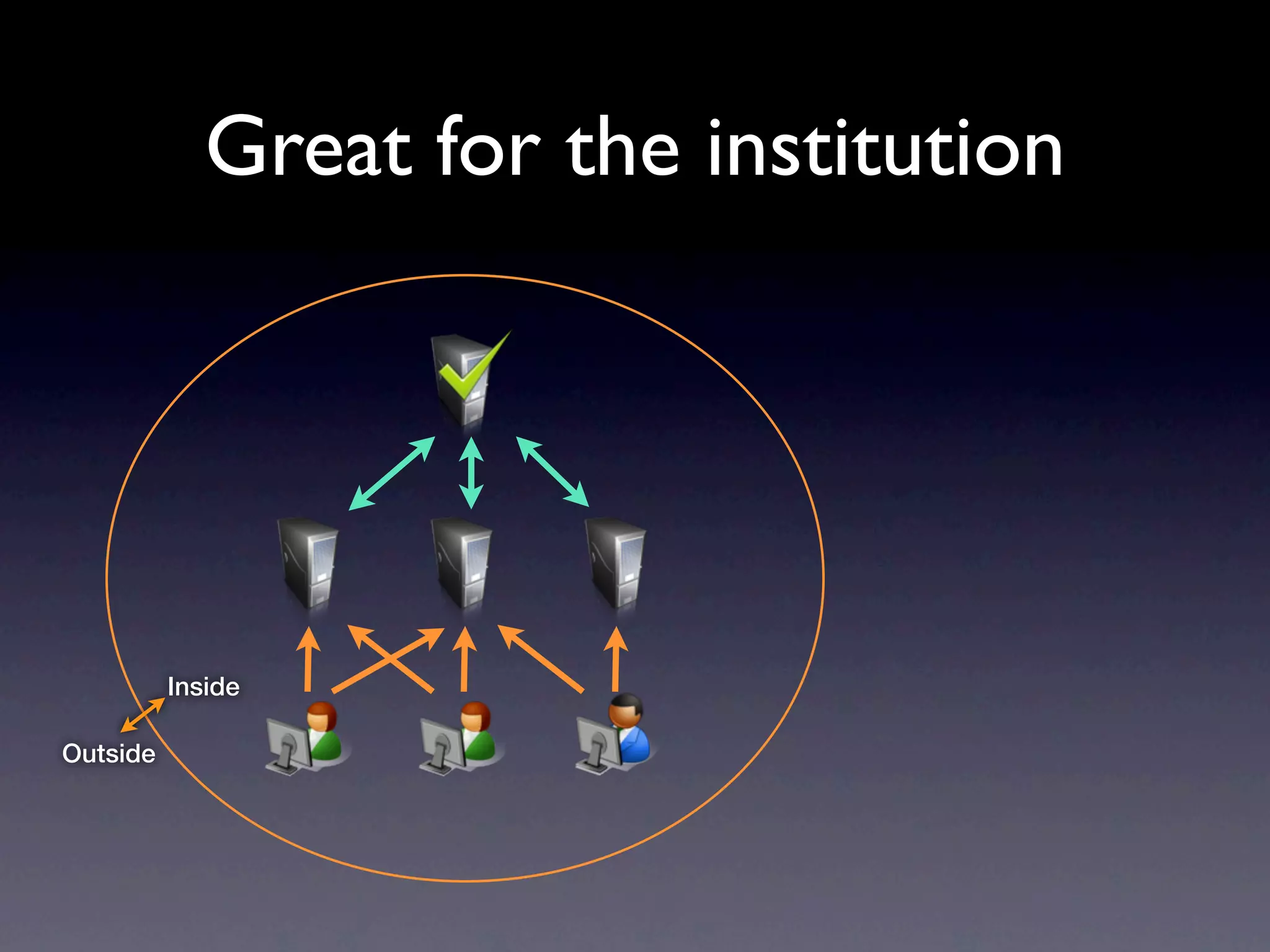
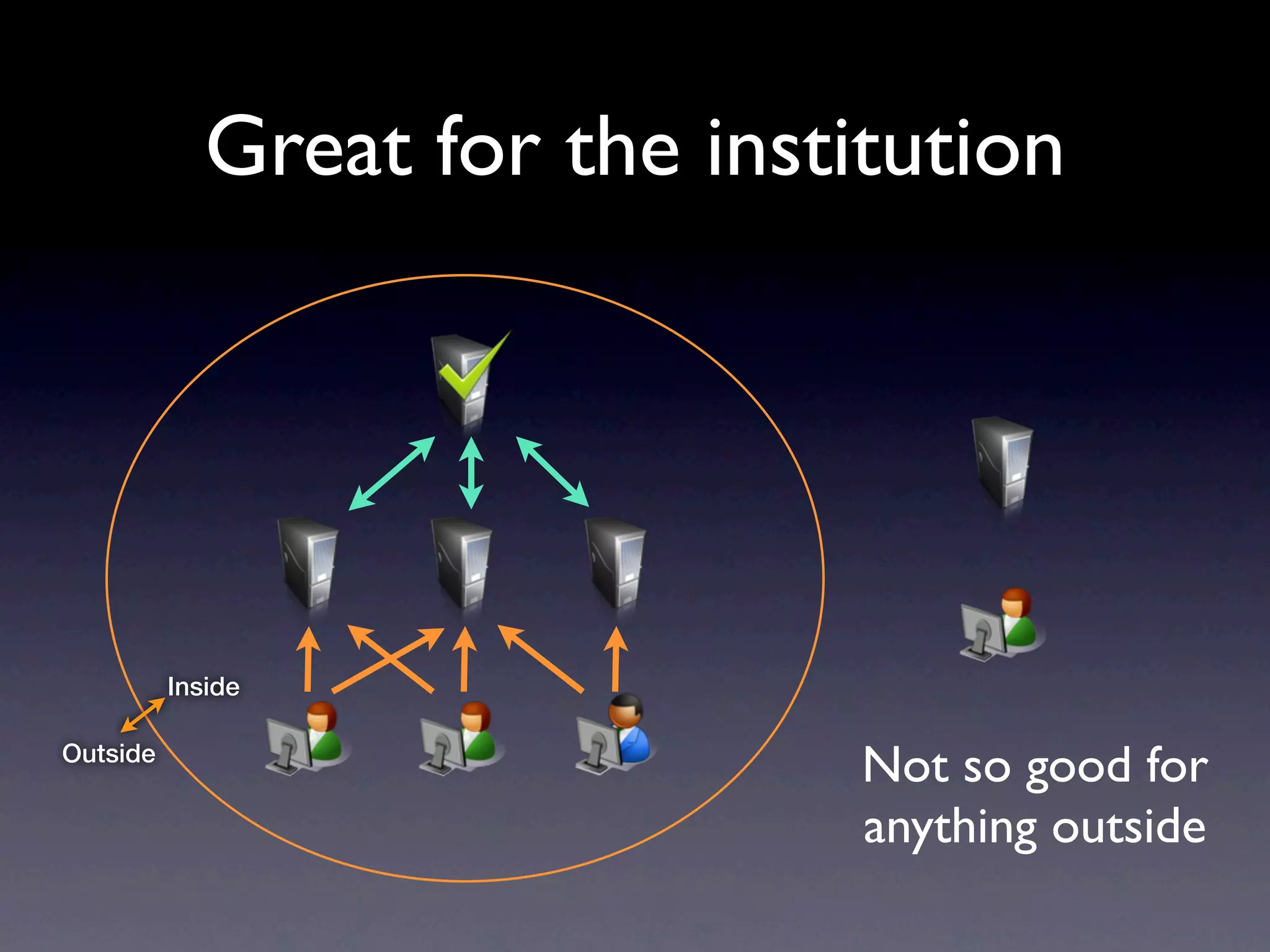
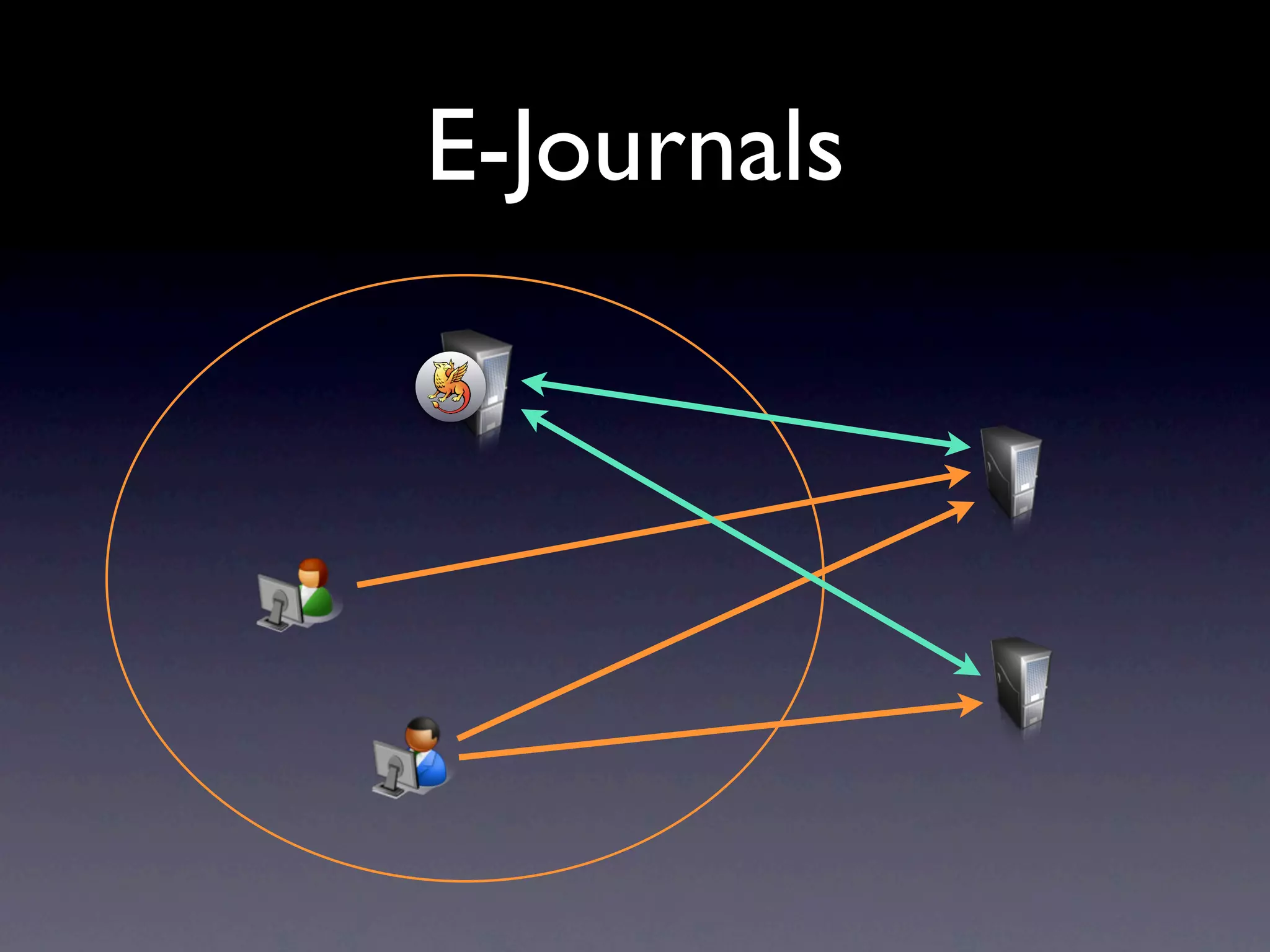
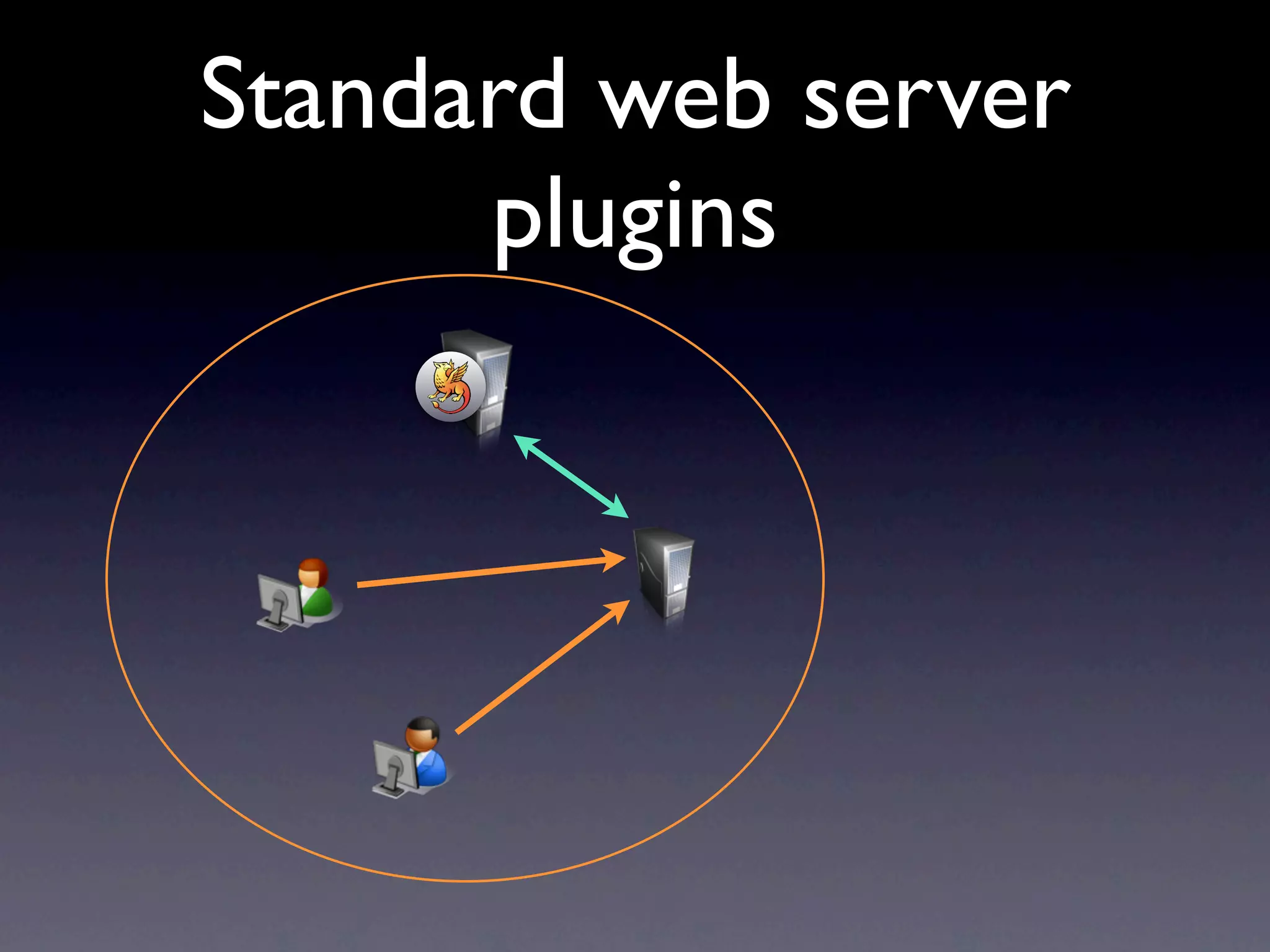
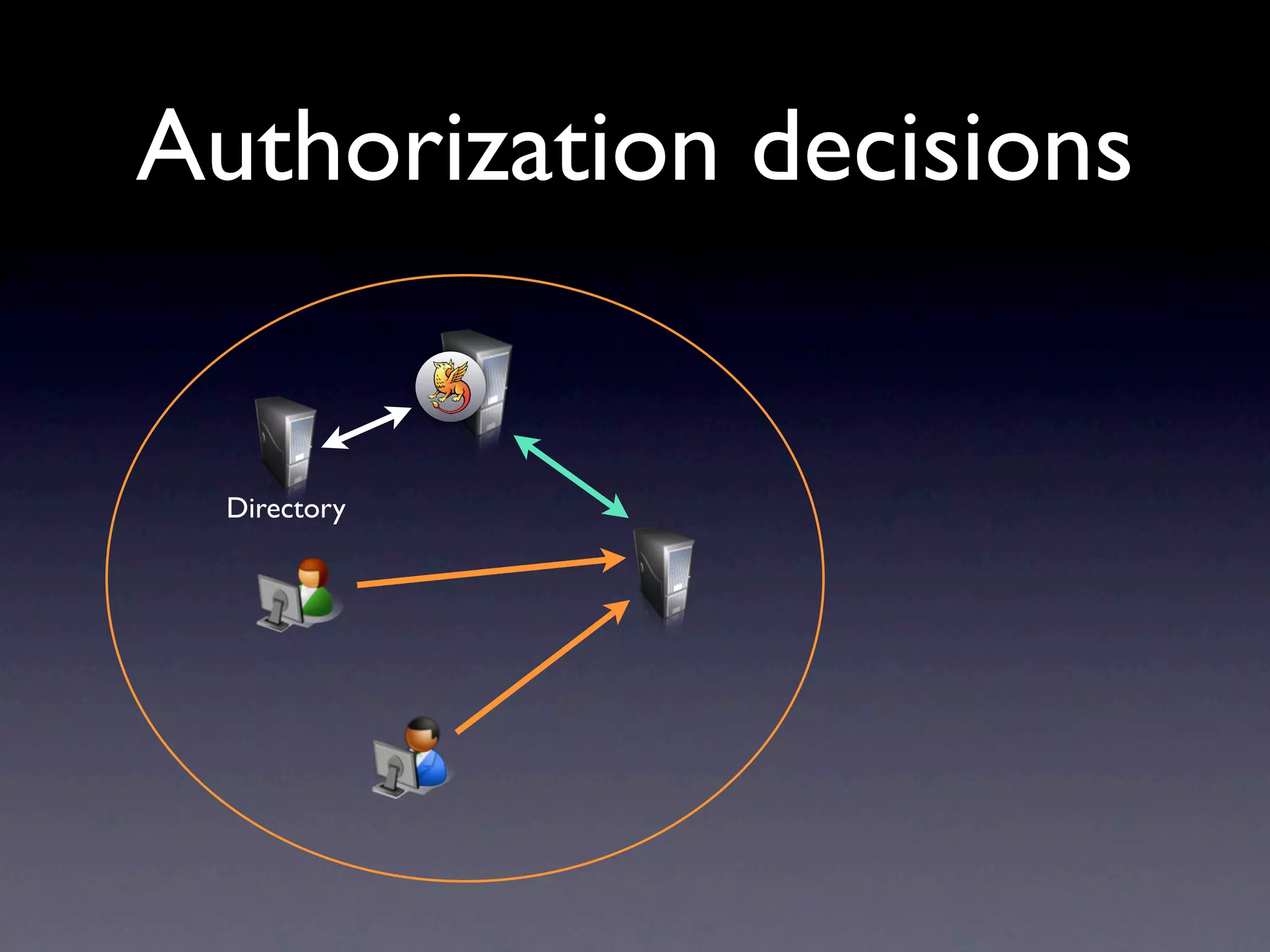
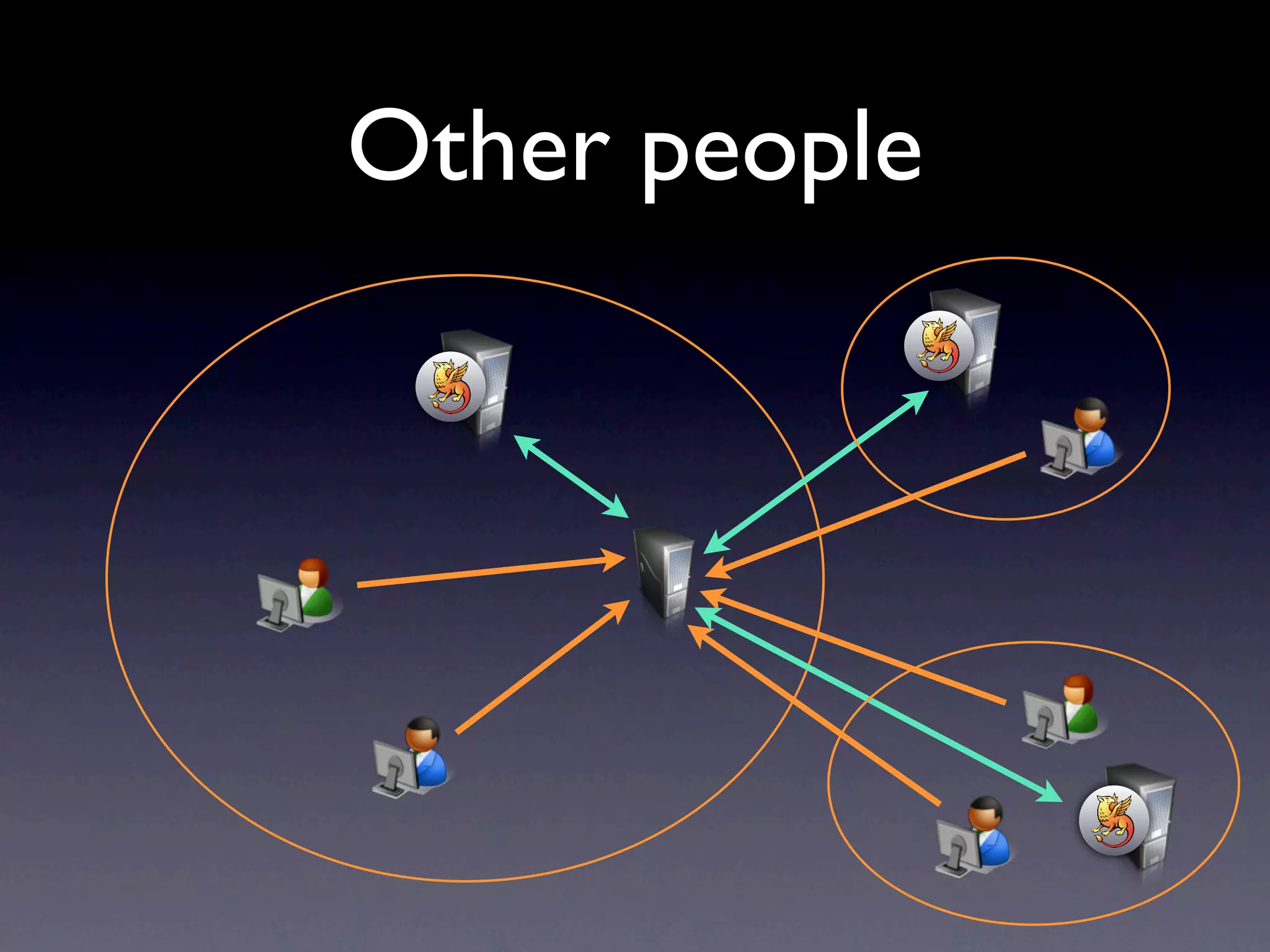
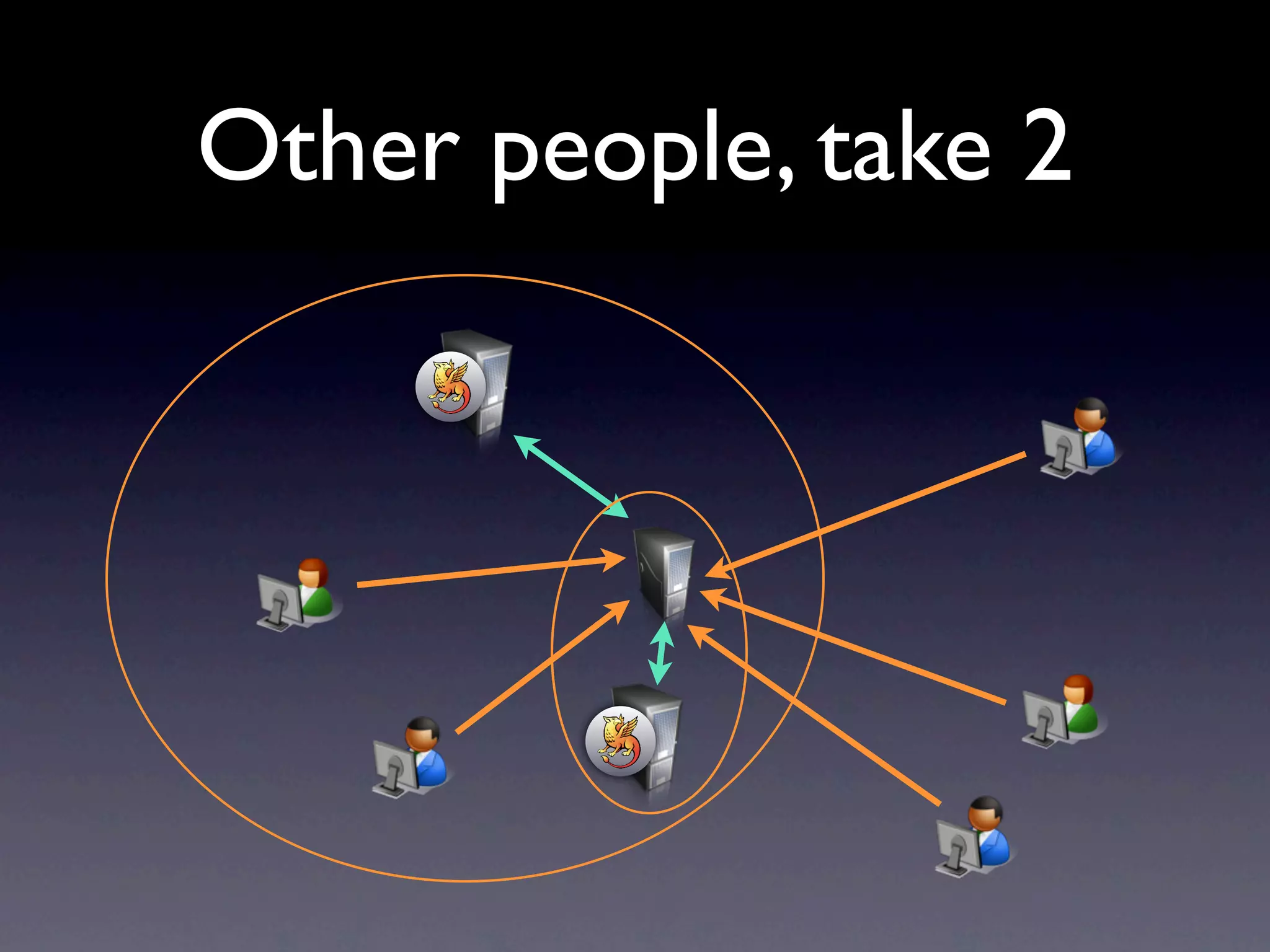
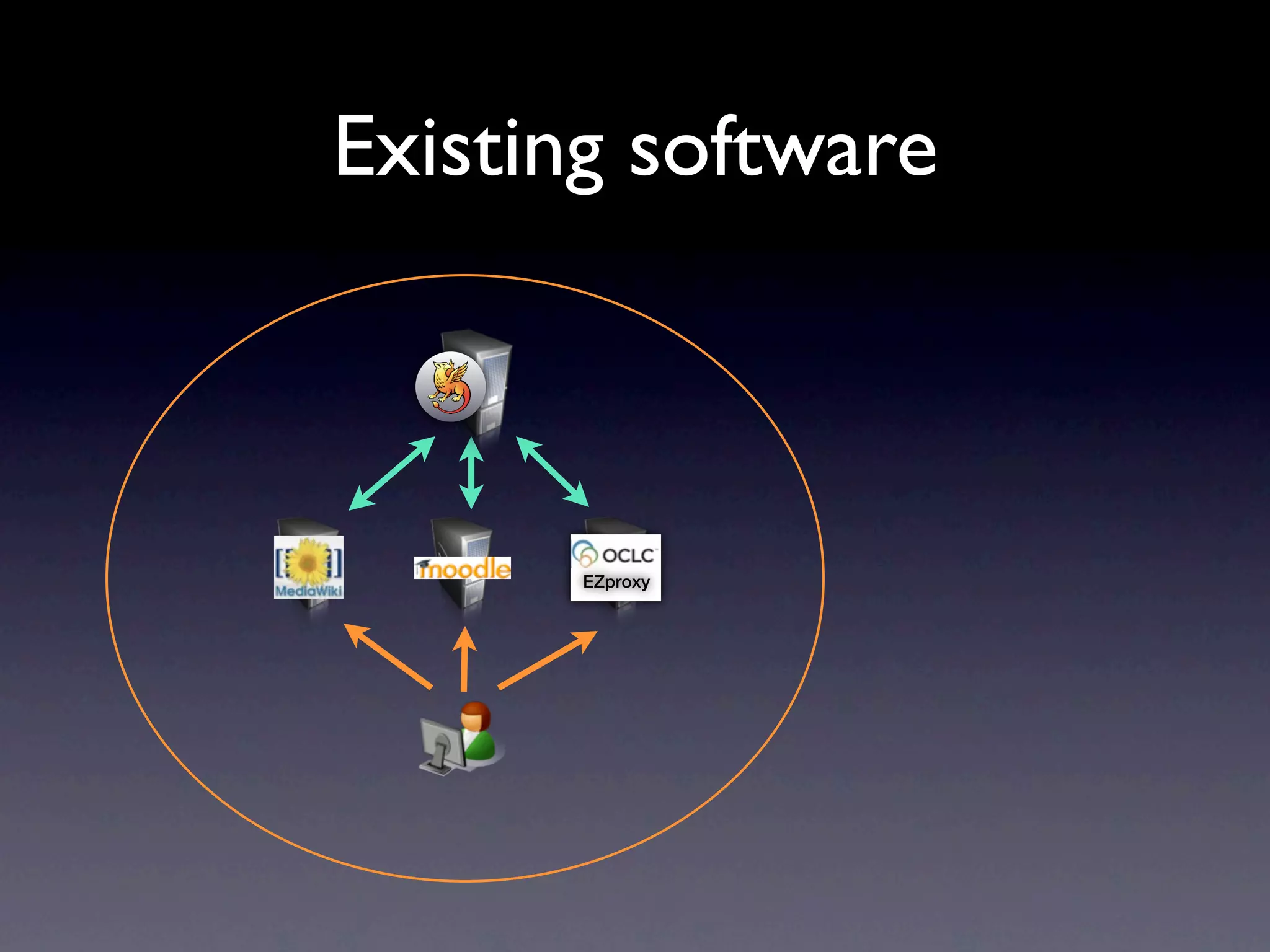
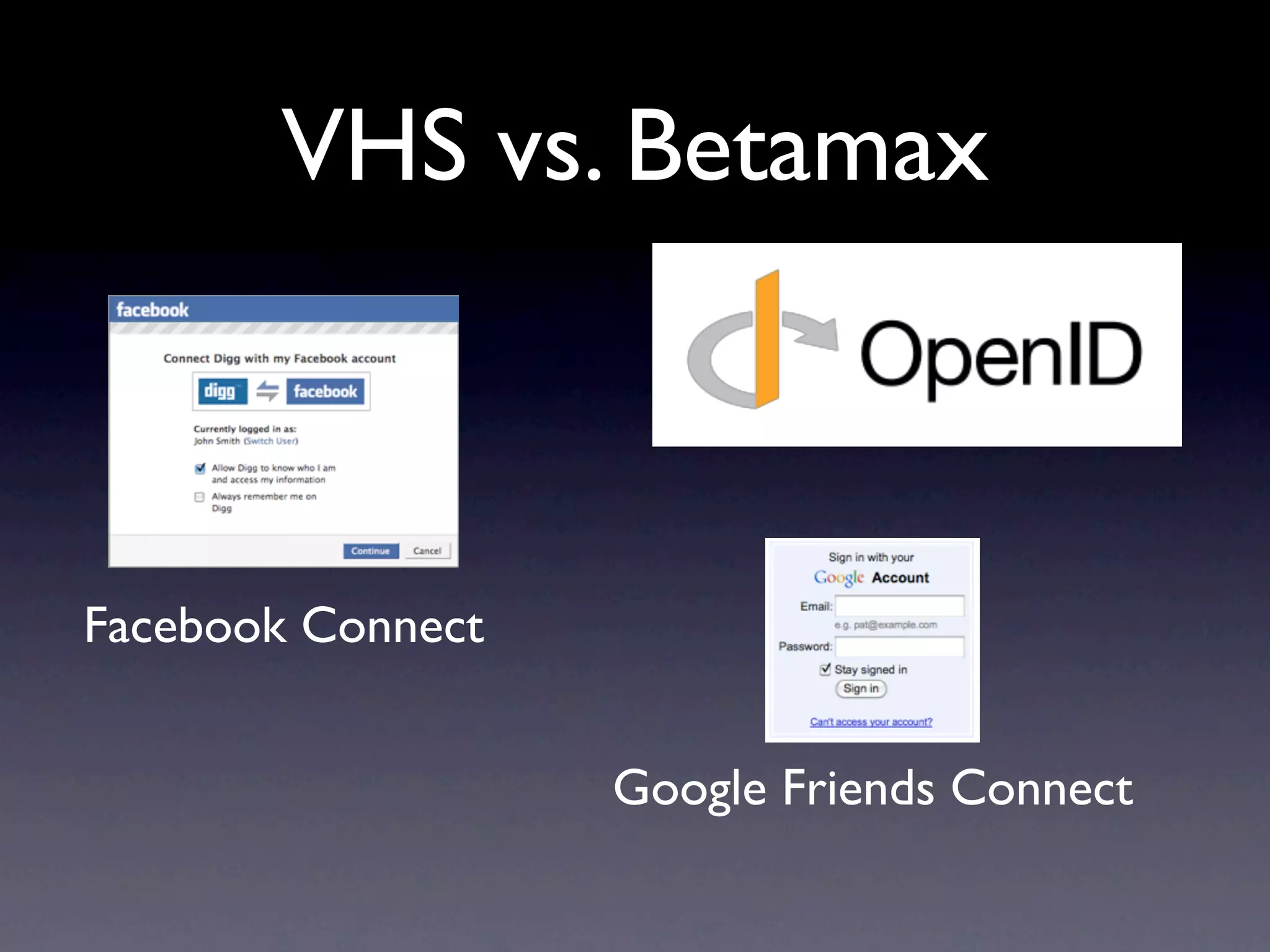
This document provides an overview of web authentication with Shibboleth. It discusses how traditionally each website had its own user authentication, but organization-wide single sign-on systems like university portals provided a solution. However, these were not suitable for accessing resources outside the organization. Shibboleth was designed as an open standard web authentication system that supports multiple identity providers, inter-organization use, privacy, anonymity, and multiple attributes. The document outlines some common misconceptions about Shibboleth and provides examples of how it can be used for e-journals, standard web plugins, and authorization decisions.