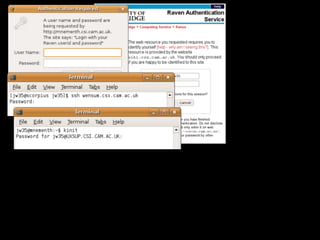
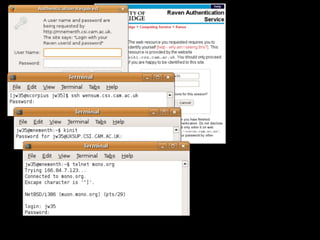
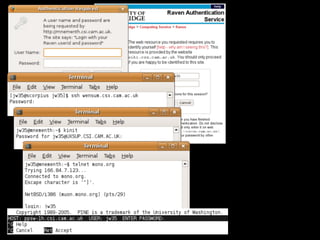
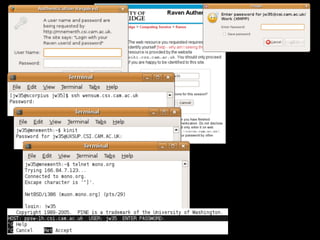
The document discusses various security measures to protect sensitive information from potential threats, including students, journalists, organized criminals, and government agencies. It presents multiple options for password management, such as eliminating passwords or implementing centralized verification systems. The document also highlights ongoing security challenges and questions future directions for improving password security.