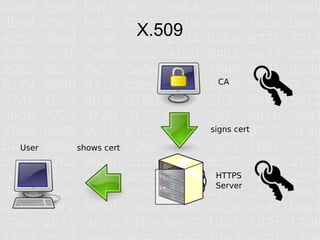
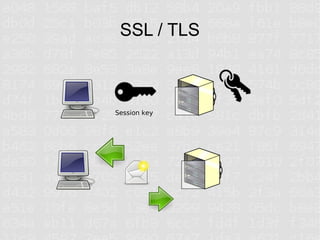
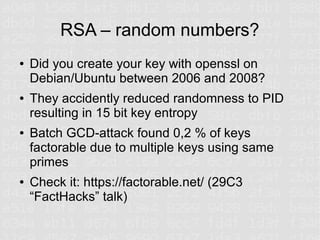
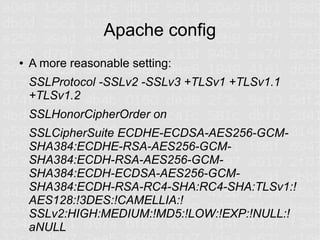
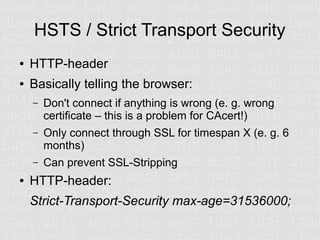
SSL and HTTPS configuration can be complex due to the involvement of multiple cryptographic protocols and standards. Many things can go wrong requiring updates to server configurations to support the latest protocols and address vulnerabilities. Proper configuration of certificates, encryption standards, hashes, and protocols is required to ensure a secure connection.