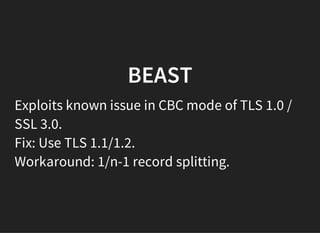
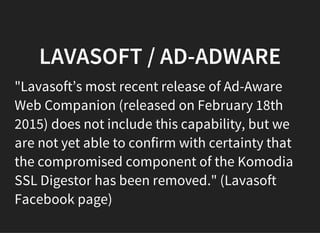
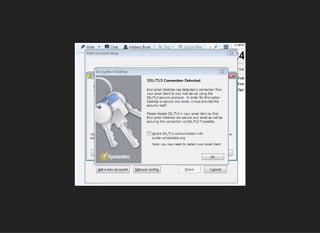
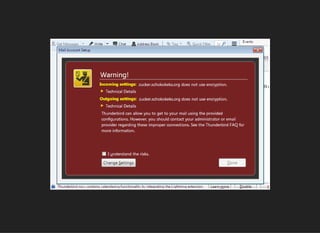
The document discusses the vulnerabilities and issues associated with TLS interception and the role of certificate authorities in web security. It emphasizes that TLS 1.2 with forward secrecy is the safest option, while many security products and browsers mishandle TLS connections, exposing users to significant risks. The conclusion warns against TLS interception practices and highlights the need for better user consent and security measures.