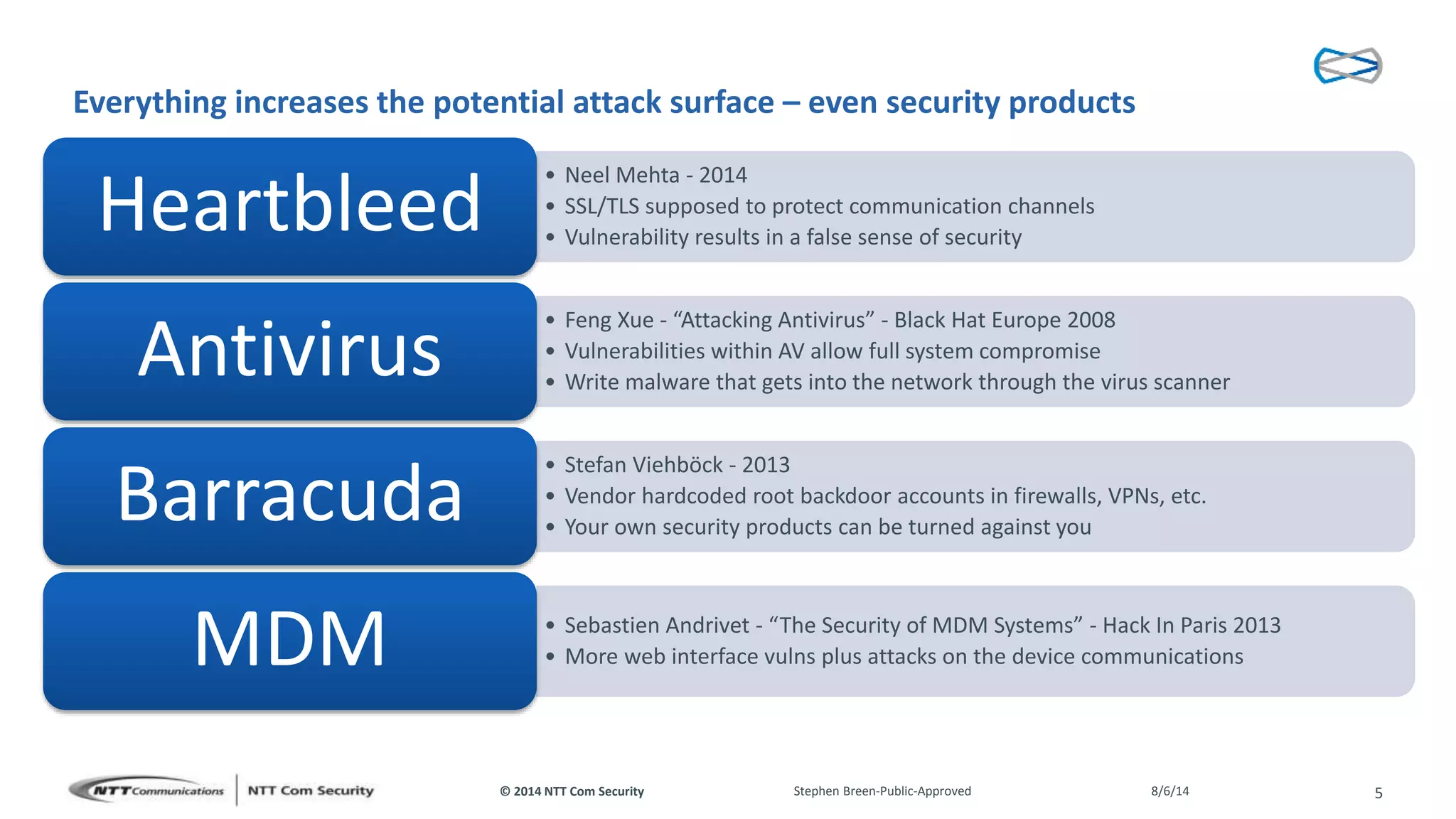
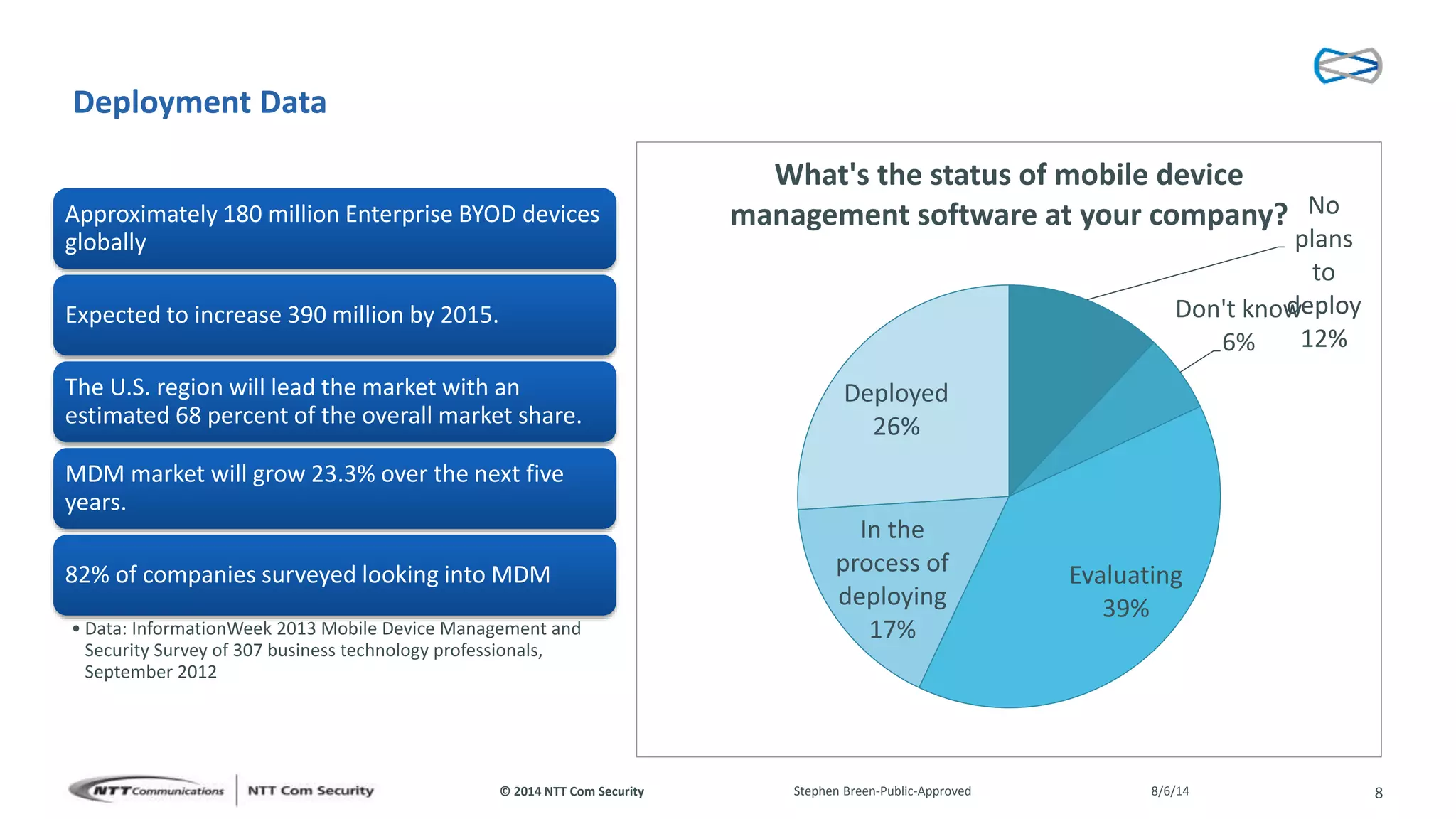
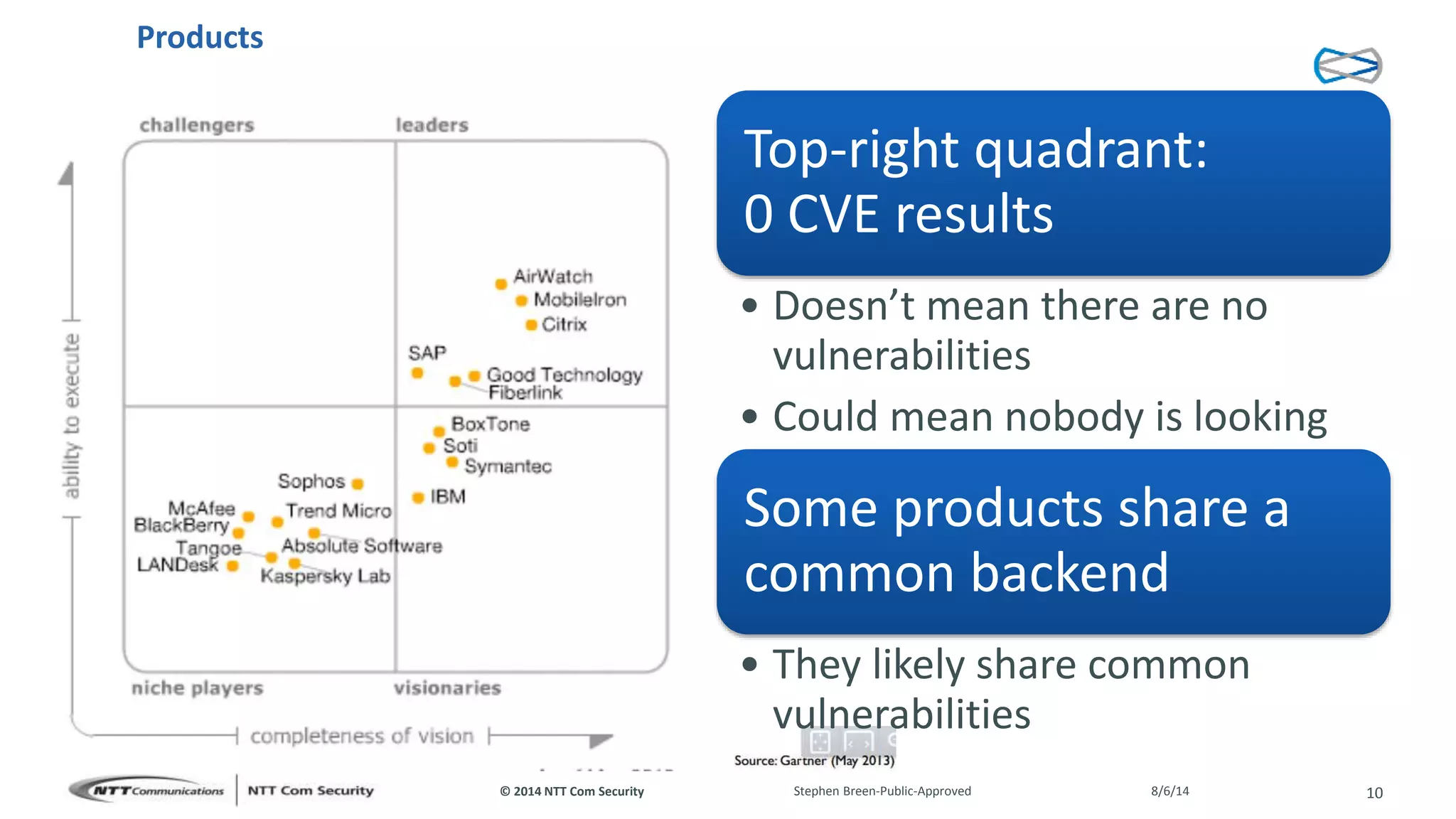
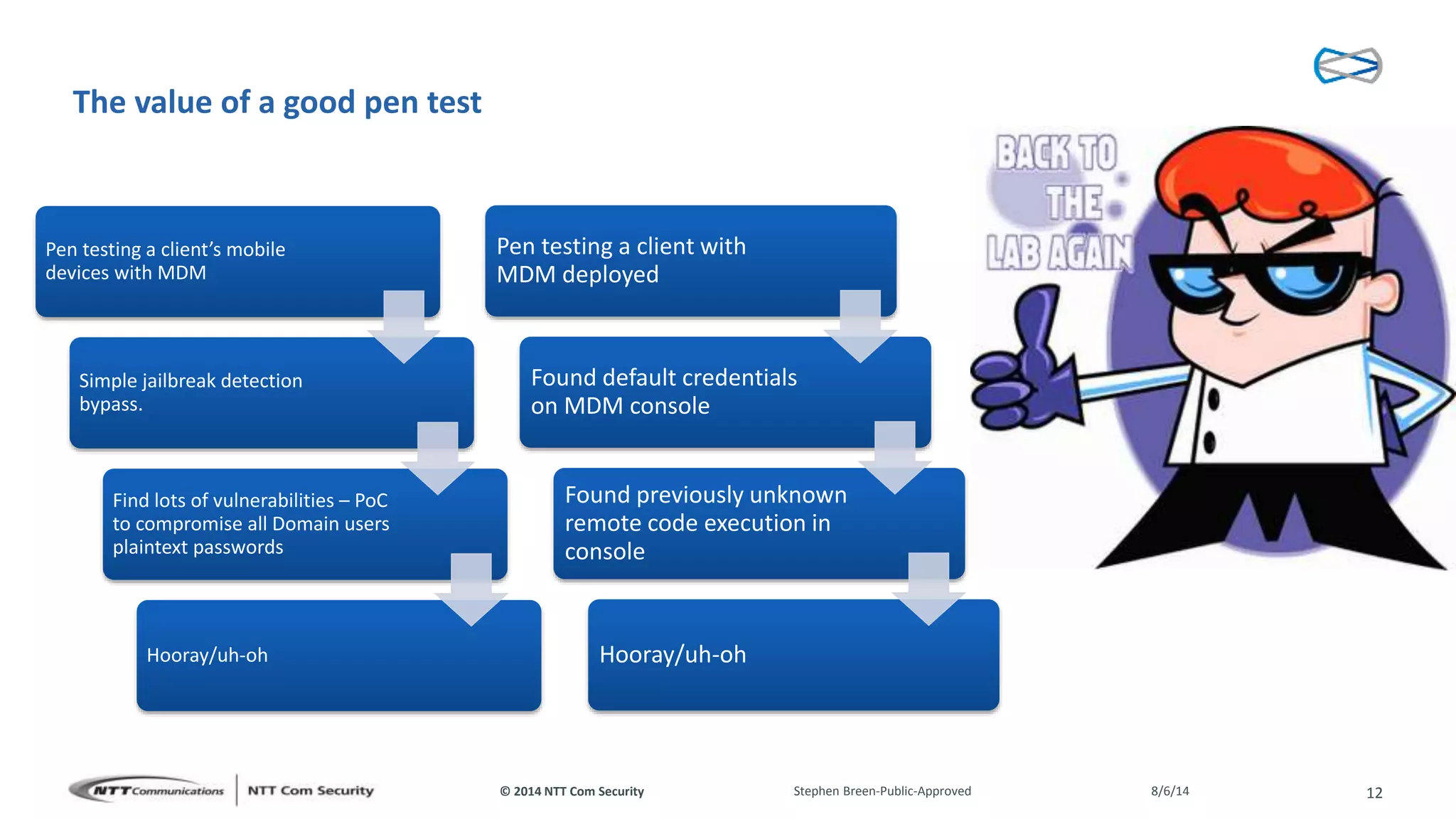
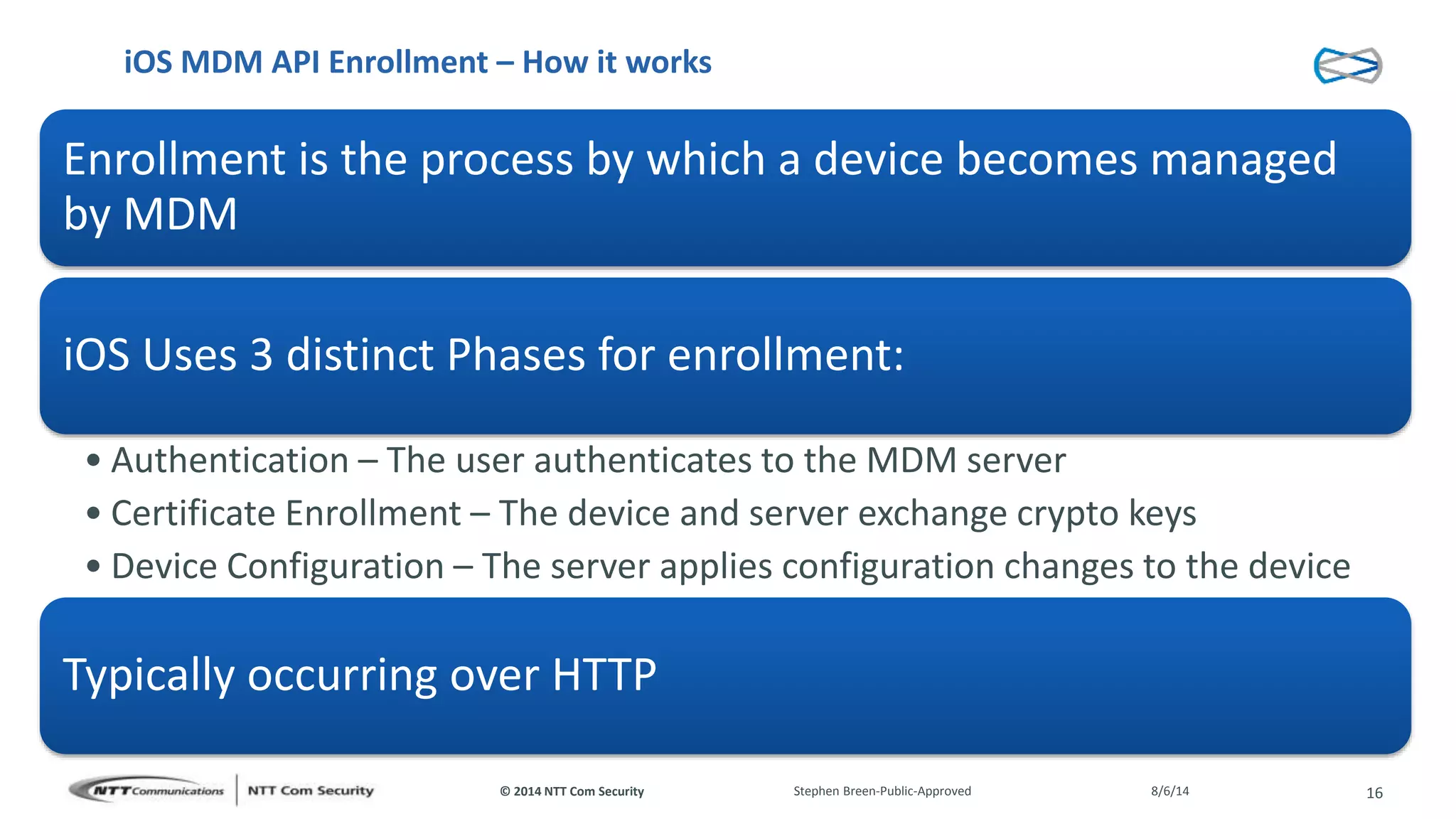
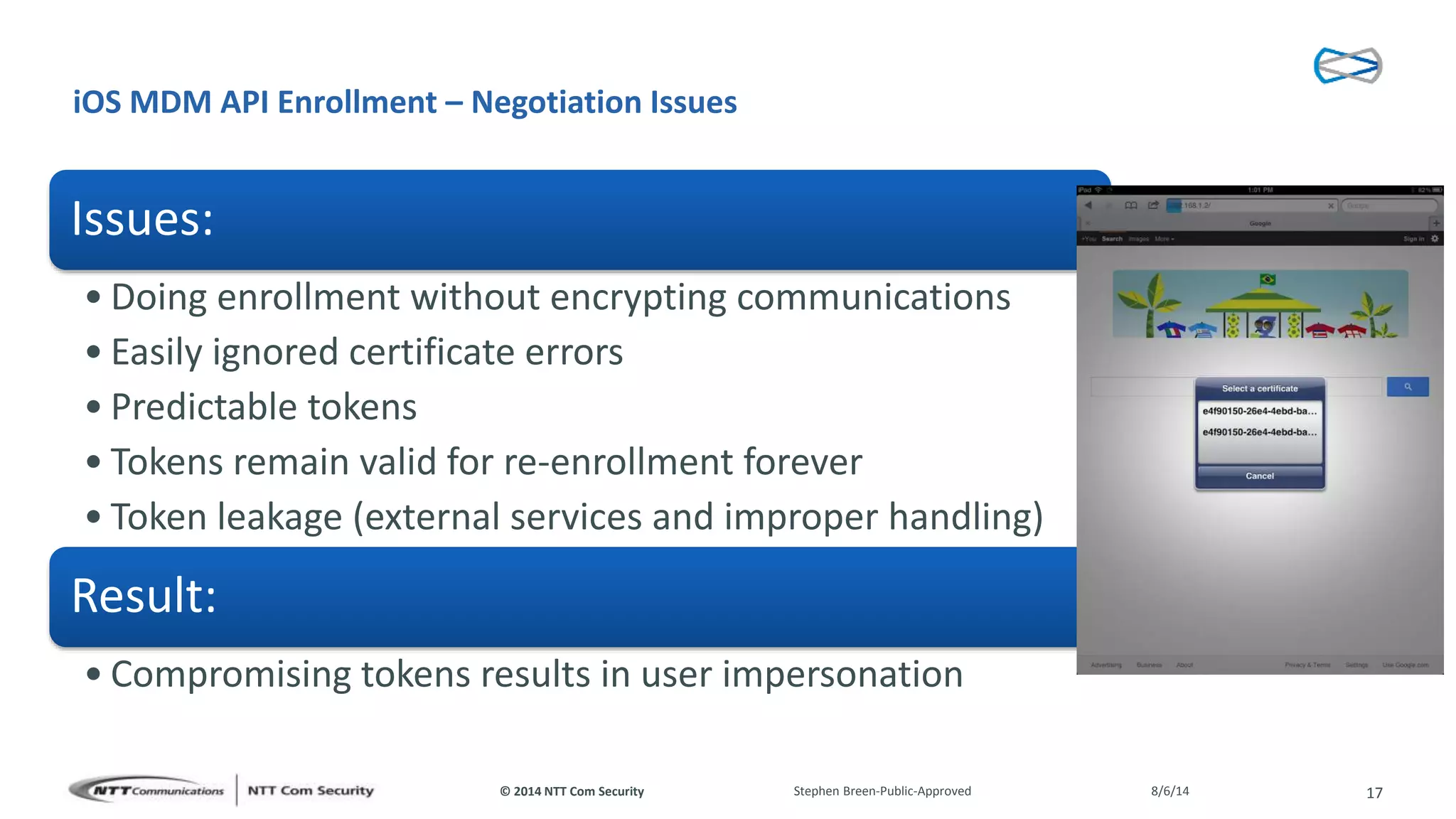
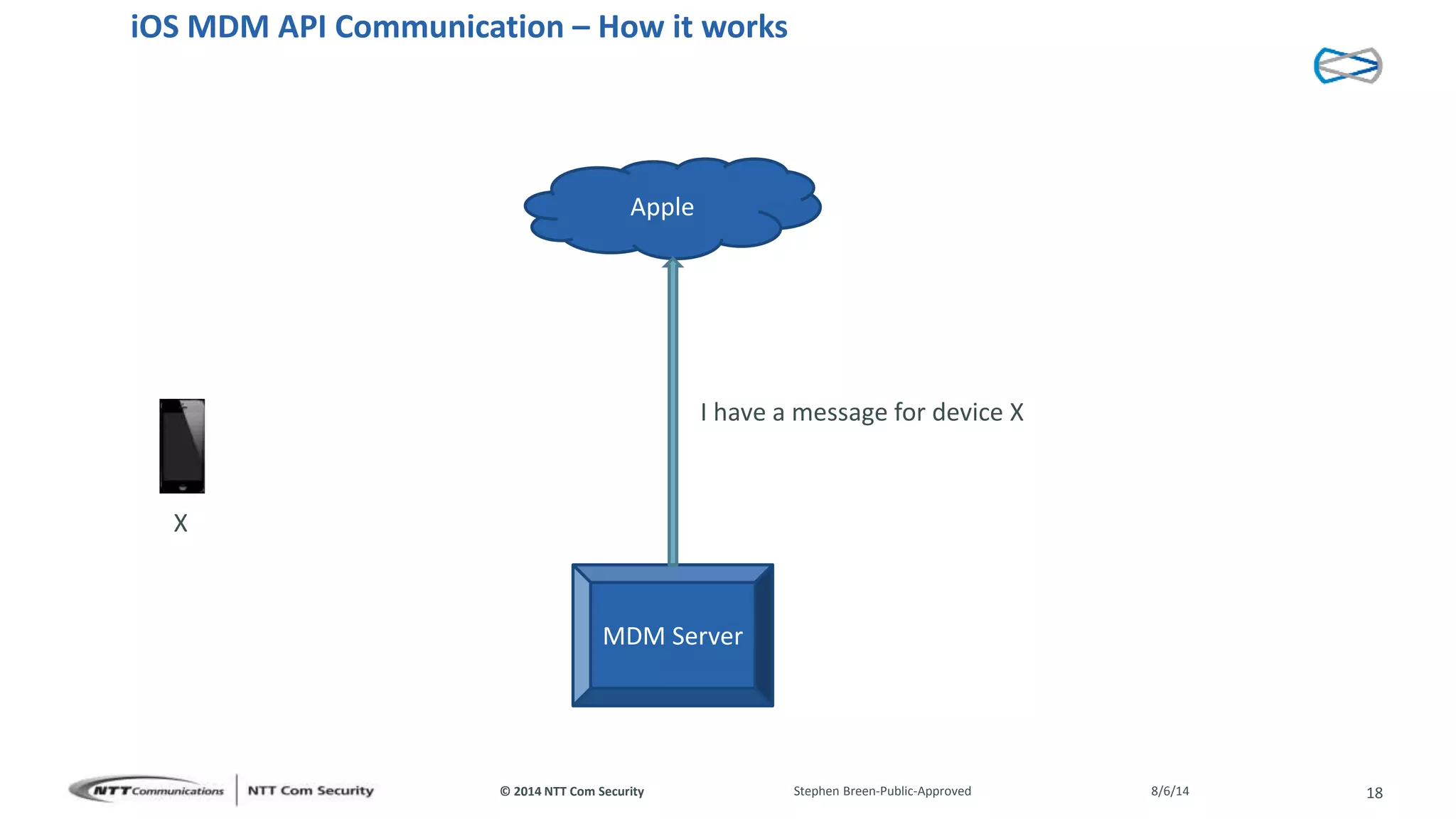
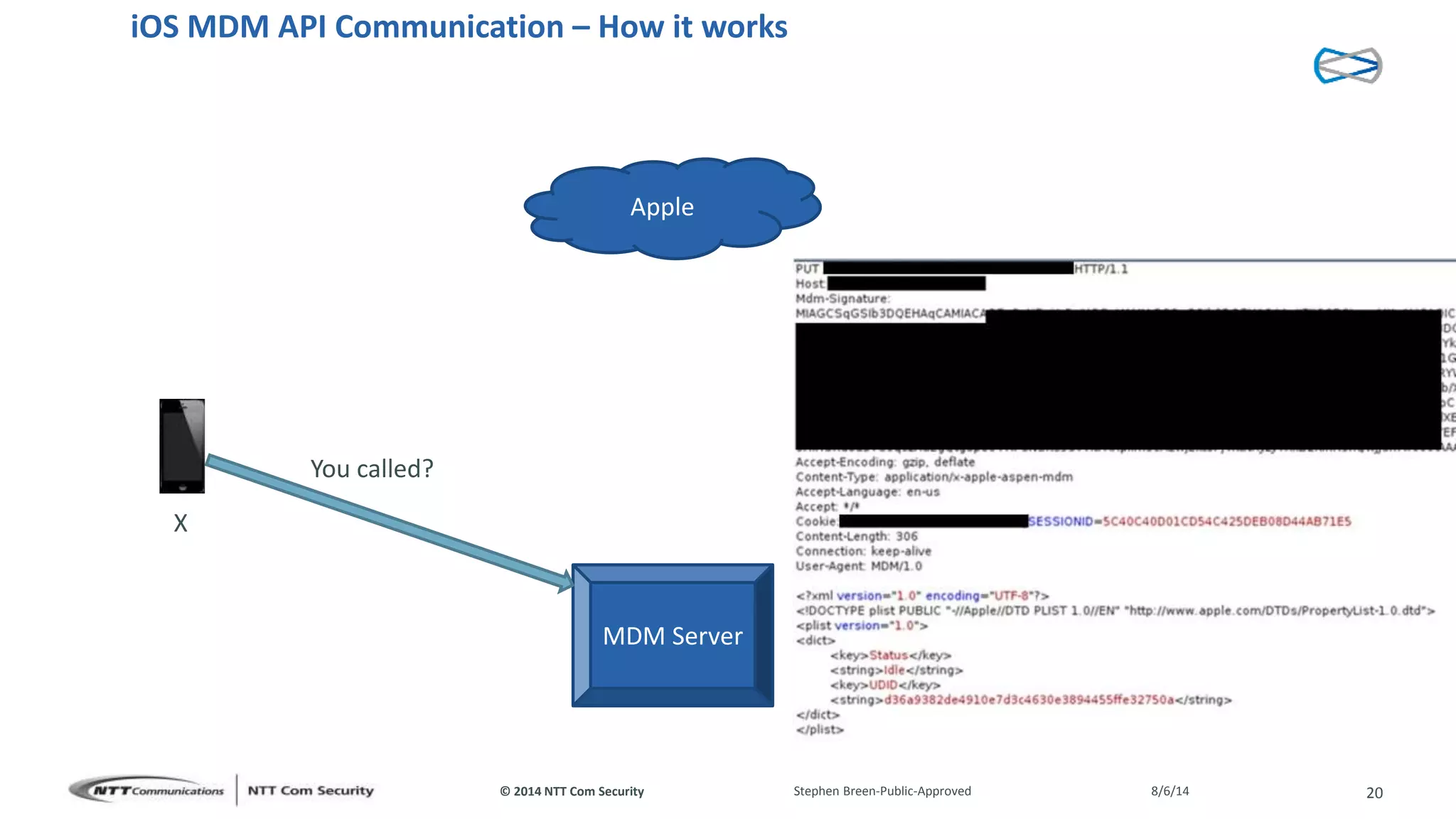
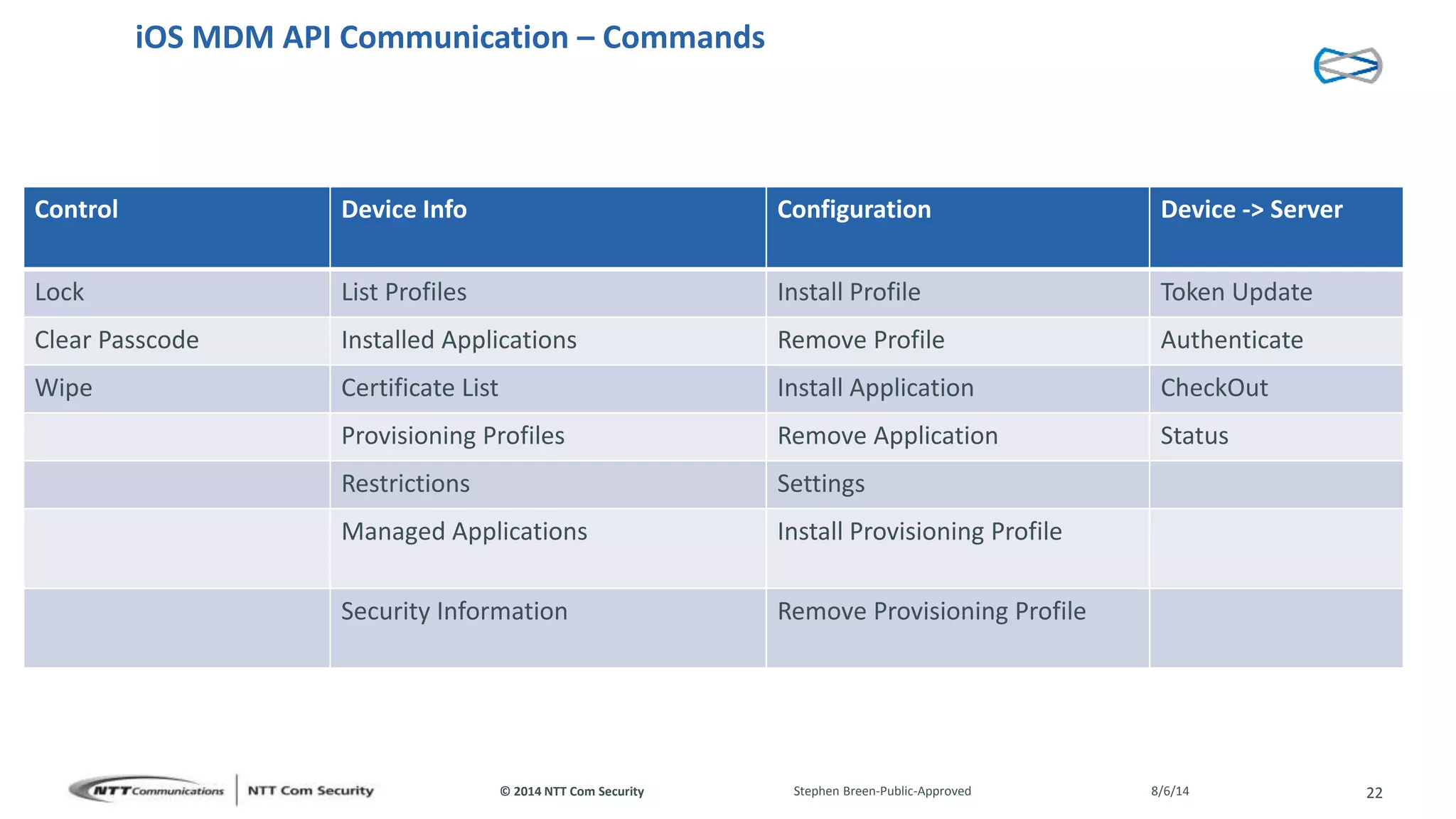
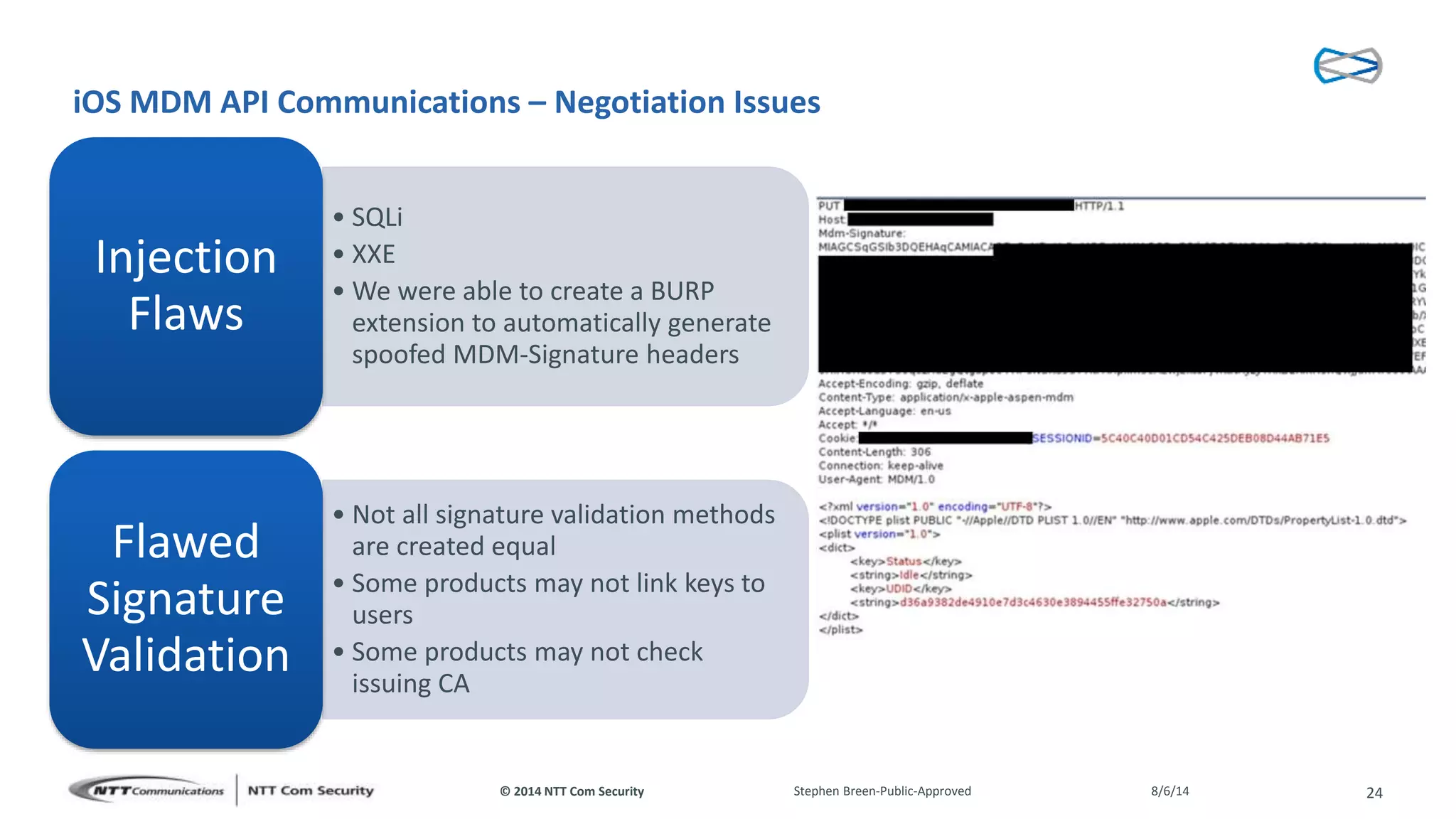
This document discusses vulnerabilities found in mobile device management (MDM) solutions. It begins with background on the growing MDM market and how the research started from vulnerabilities discovered during a penetration test. The research found issues in how MDM solutions implemented the iOS MDM API, including lack of encryption, token issues, and flaws in signature validation. This could allow impersonation of users, denial of service attacks, intercepting sensitive data, and more. The document warns that MDM solutions can increase security risks if not implemented carefully, and that vendors and users must prioritize security practices like penetration testing, secure development, and monitoring.