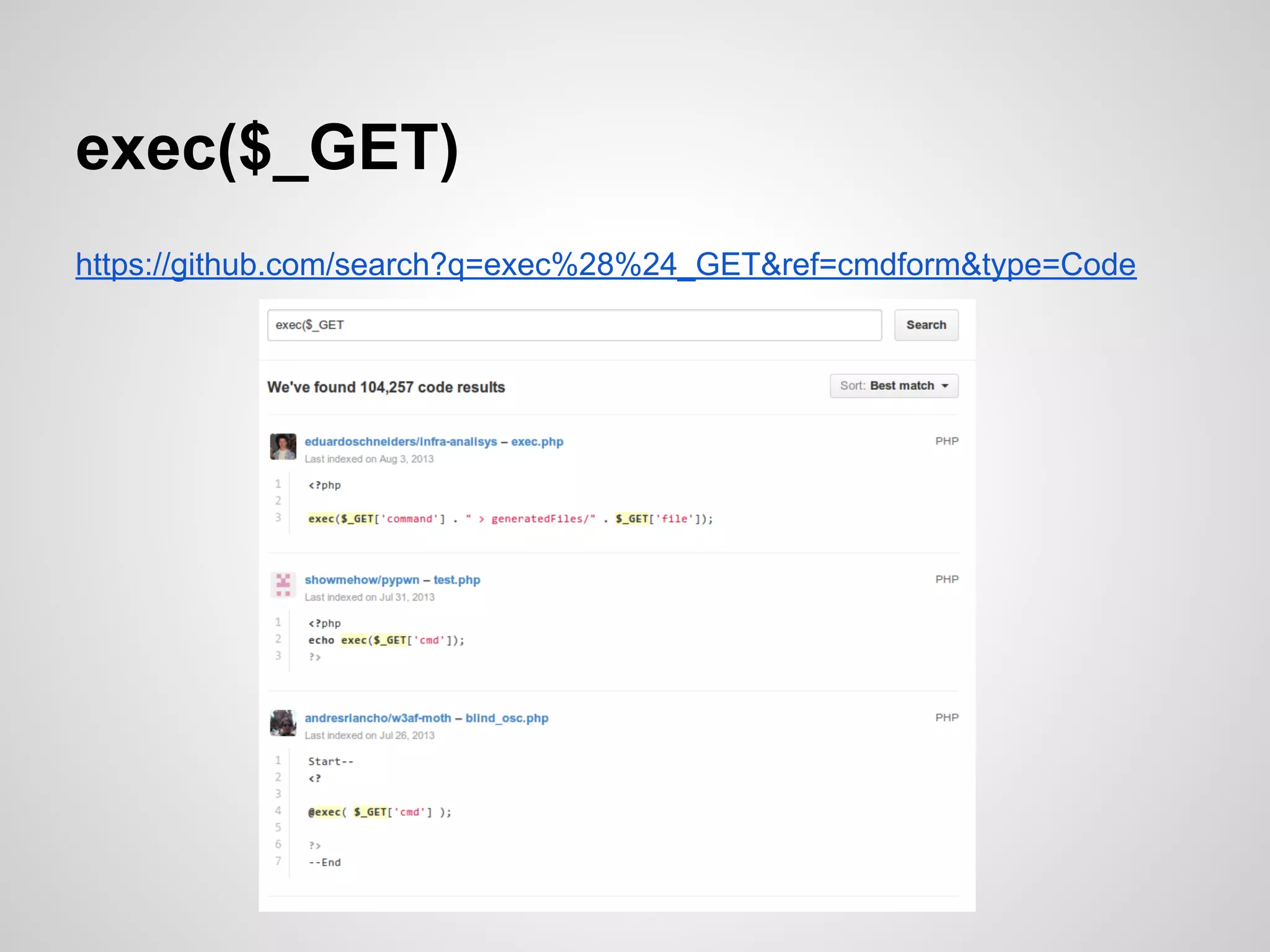
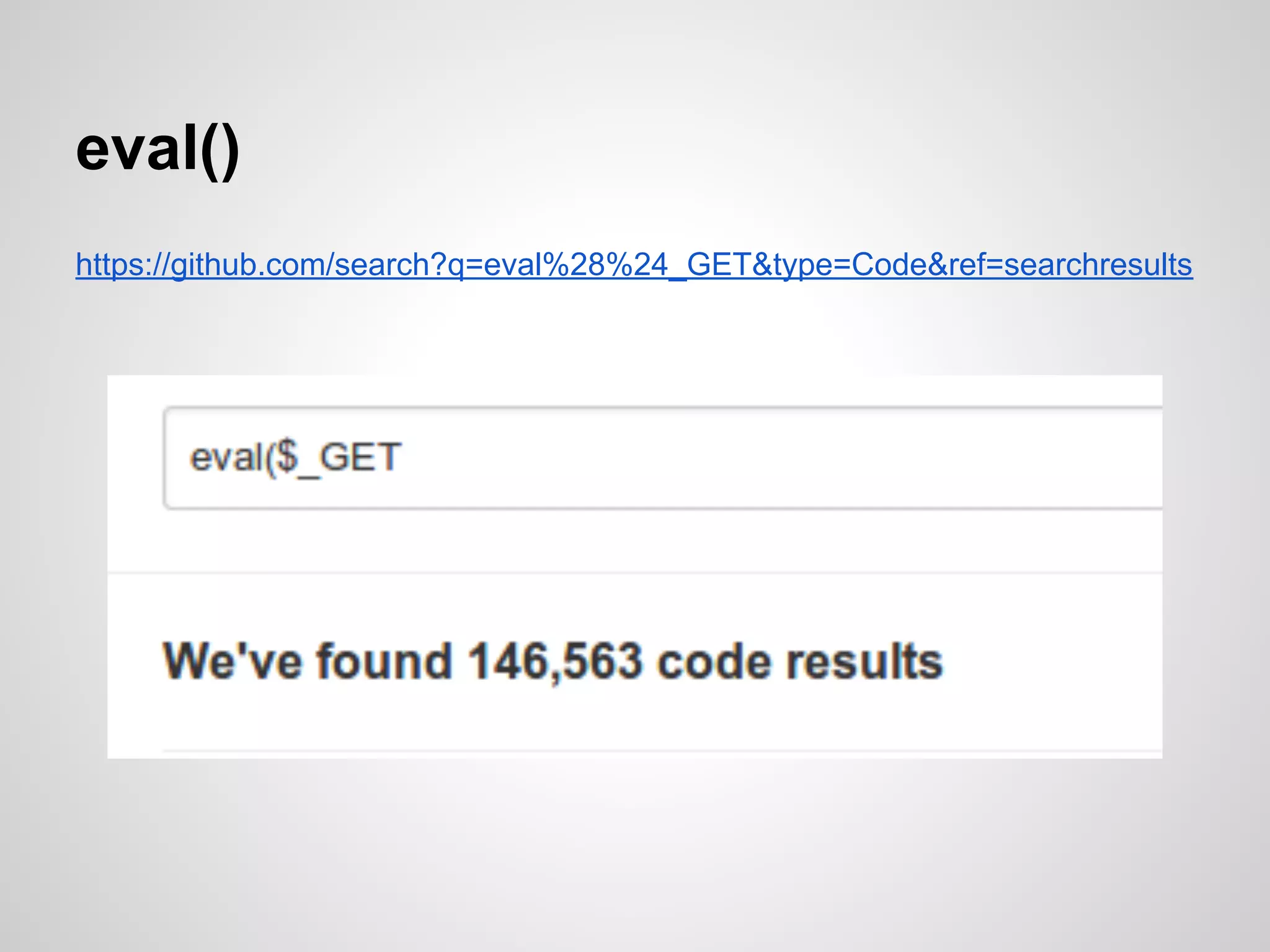
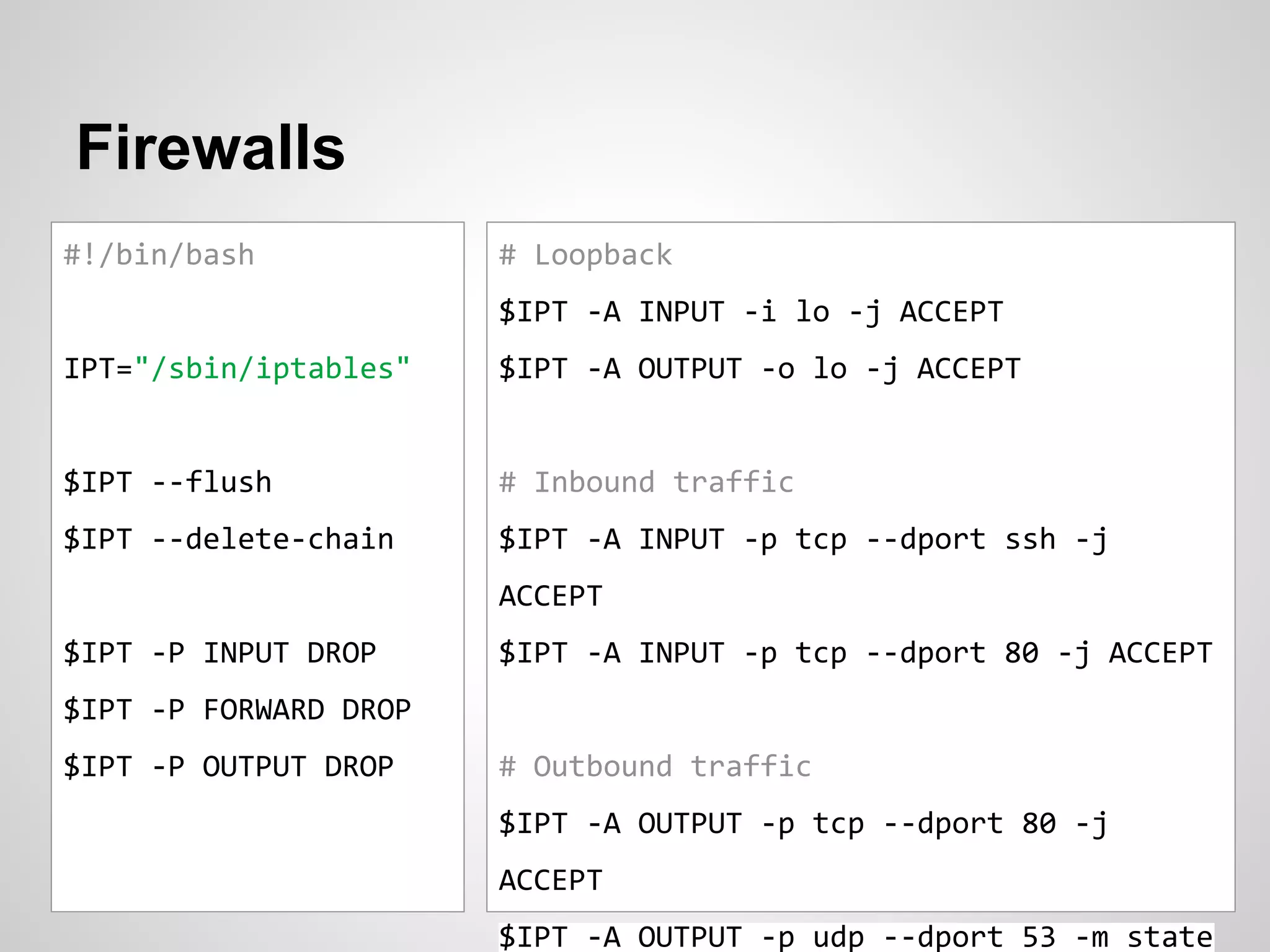
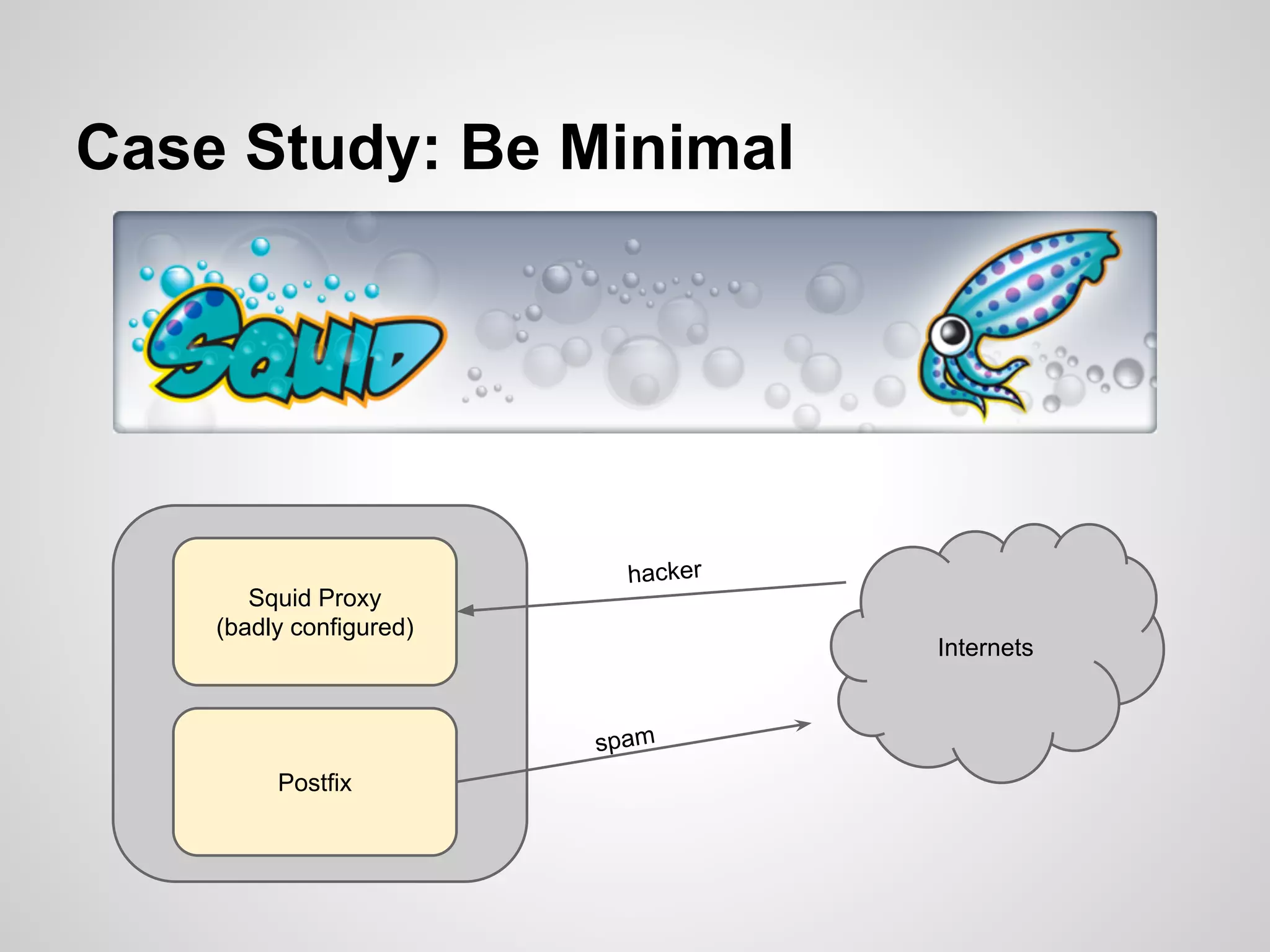
The document is a presentation by James Titcumb on security best practices, particularly for PHP applications, emphasizing the importance of simplicity, risk awareness, and secure coding. Key points include protecting against SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and proper authentication methods. It advocates for learning about vulnerabilities, threat modeling, and maintaining minimal configurations while providing resources for further learning.



![Some simple code...
<?php
$a = (int)$_GET['a'];
$b = (int)$_GET['b'];
$result = $a + $b;
printf('The answer is %d', $result);](https://image.slidesharecdn.com/140602-dipyourtoesintheseaofsecurityphpdorset-140603031551-phpapp02/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-Dorset-2nd-June-2014-4-2048.jpg)











![SQL Injection (#1)
<?php
$user_id = $_GET['user_id'];
$sql = "
SELECT * FROM users
WHERE user_id = {$user_id}";
$db->execute($sql);
✘](https://image.slidesharecdn.com/140602-dipyourtoesintheseaofsecurityphpdorset-140603031551-phpapp02/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-Dorset-2nd-June-2014-16-2048.jpg)
![SQL Injection (#1)
<?php
$user_id = $_GET['user_id'];
$sql = "
SELECT * FROM users
WHERE user_id = :userid";
$stmt = $db->prepare($sql);
$stmt->bind('userid', $user_id);
$stmt->execute();
✔](https://image.slidesharecdn.com/140602-dipyourtoesintheseaofsecurityphpdorset-140603031551-phpapp02/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-Dorset-2nd-June-2014-17-2048.jpg)