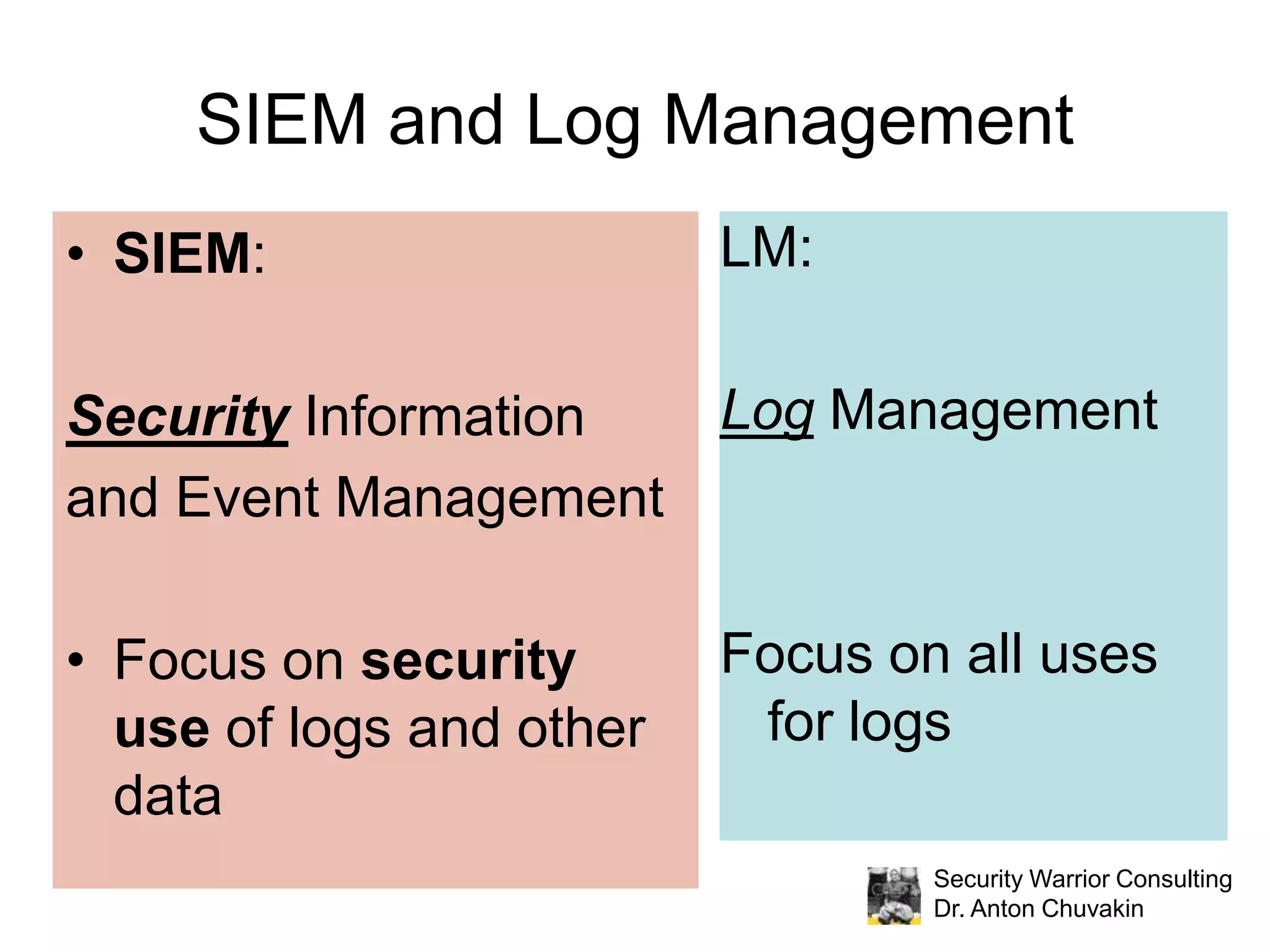
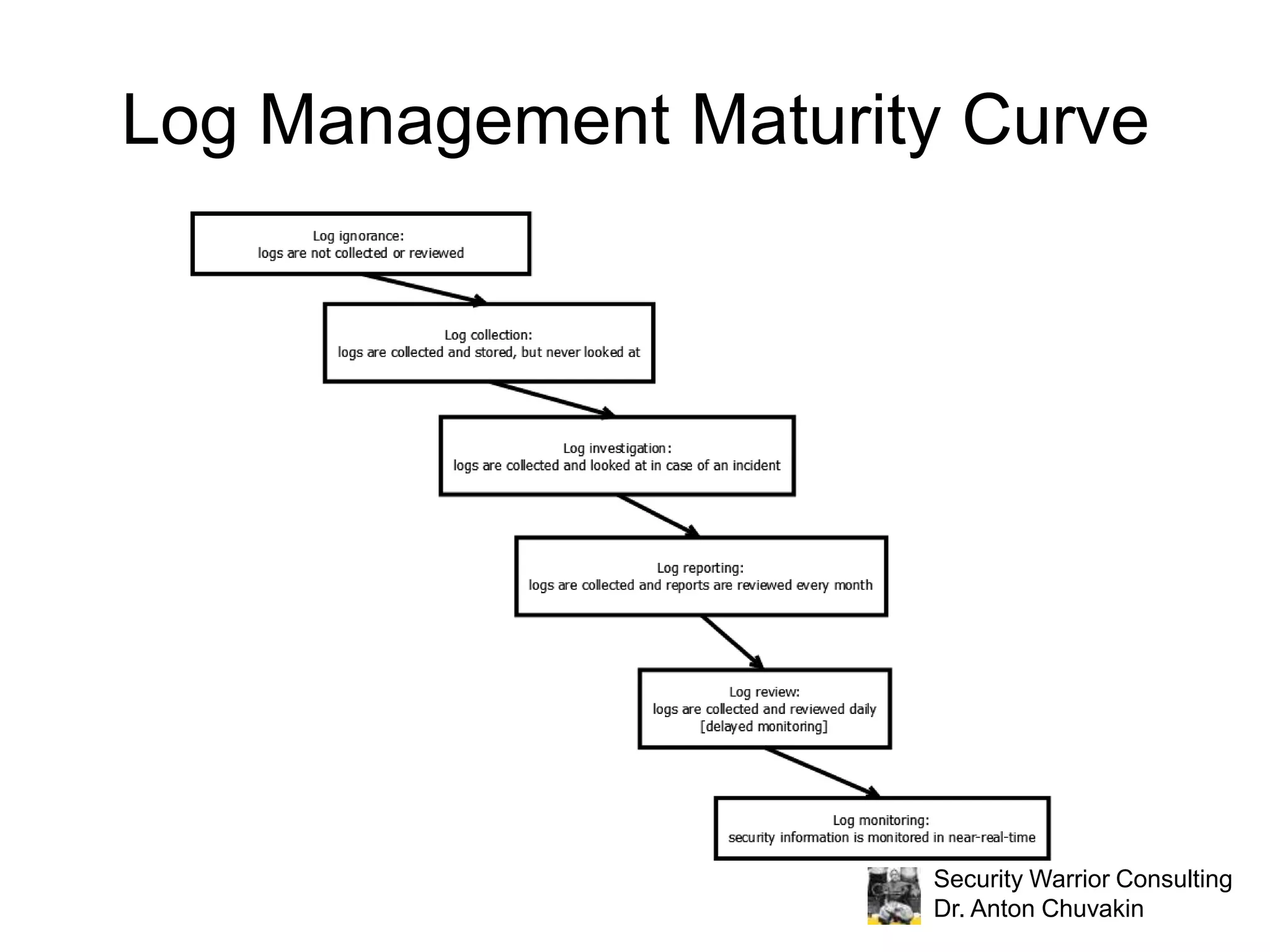
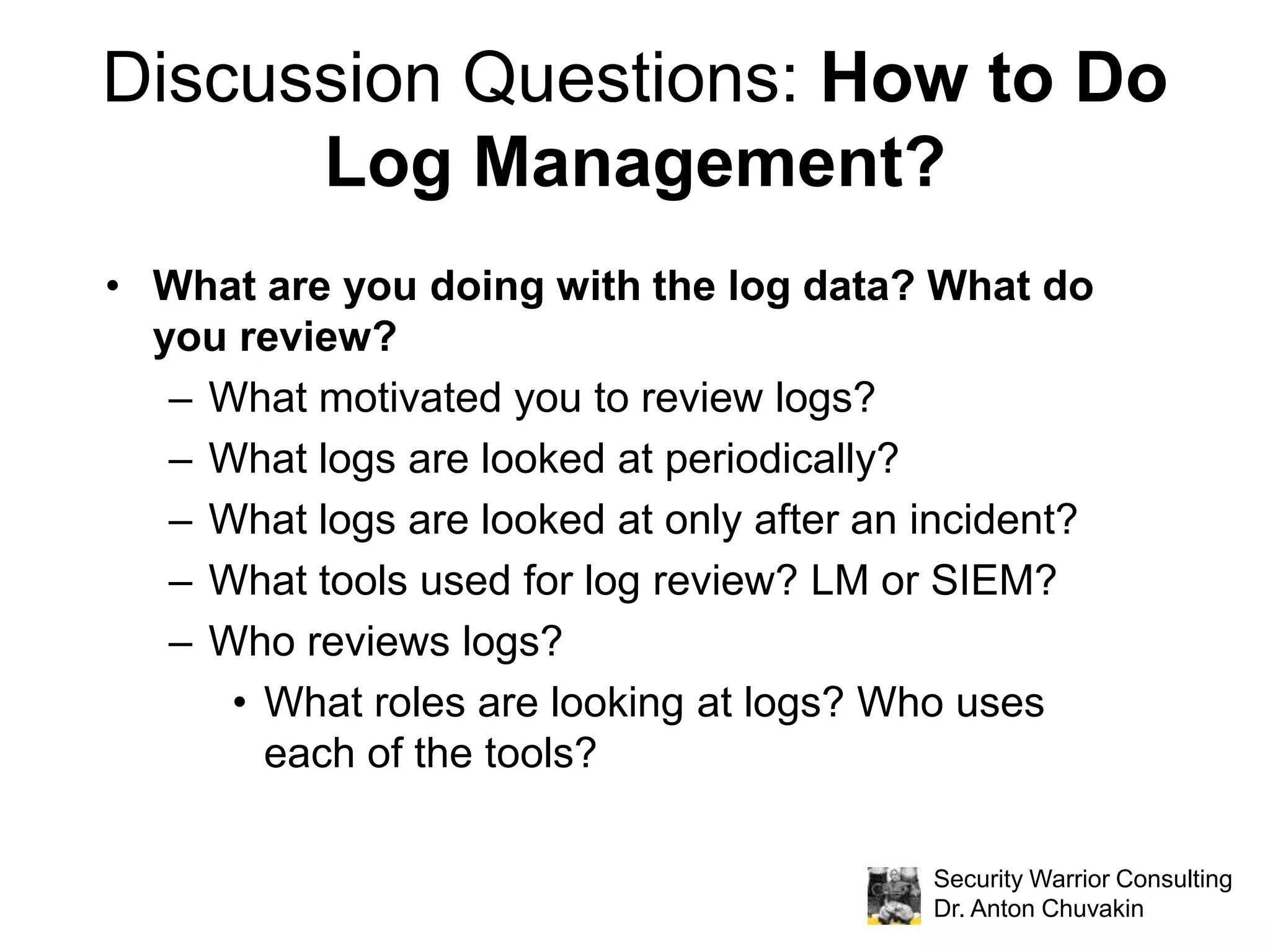
The document discusses effective log management and shared insights from case studies involving SIEM (Security Information and Event Management) tools. It highlights common pitfalls in log management, outlines essential practices for logging, and poses discussion questions about logging strategies and tools. Dr. Anton Chuvakin, an expert in the field, also emphasizes the importance of understanding what to log, how to manage logs, and the relevance of compliance in log practices.
![Navigating the Data Stream without Boiling the Ocean: Case Studies in Effective Log ManagementDr. Anton Chuvakin: IANS FacultyPanel members from large organizations using log management/SIEM tools [names removed due to not having permission to post themSee IANS site http://www.iansresearch.com for full details]](https://image.slidesharecdn.com/iansipccombinedacrel-100419153630-phpapp01/75/IANS-Navigating-the-Data-Stream-without-Boiling-the-Ocean-Case-Studies-in-Effective-Log-Management-by-Dr-Anton-Chuvakin-1-2048.jpg)