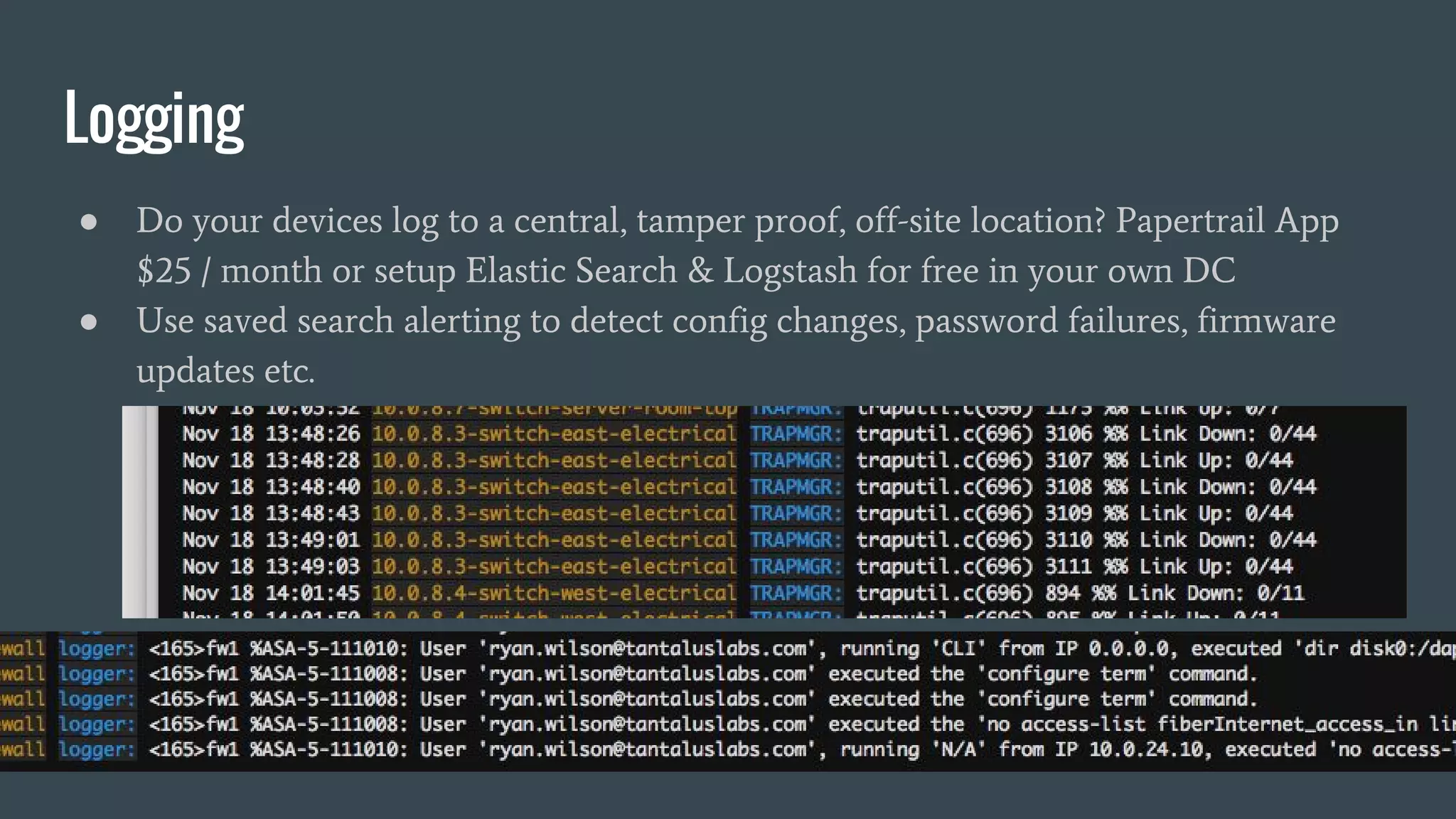
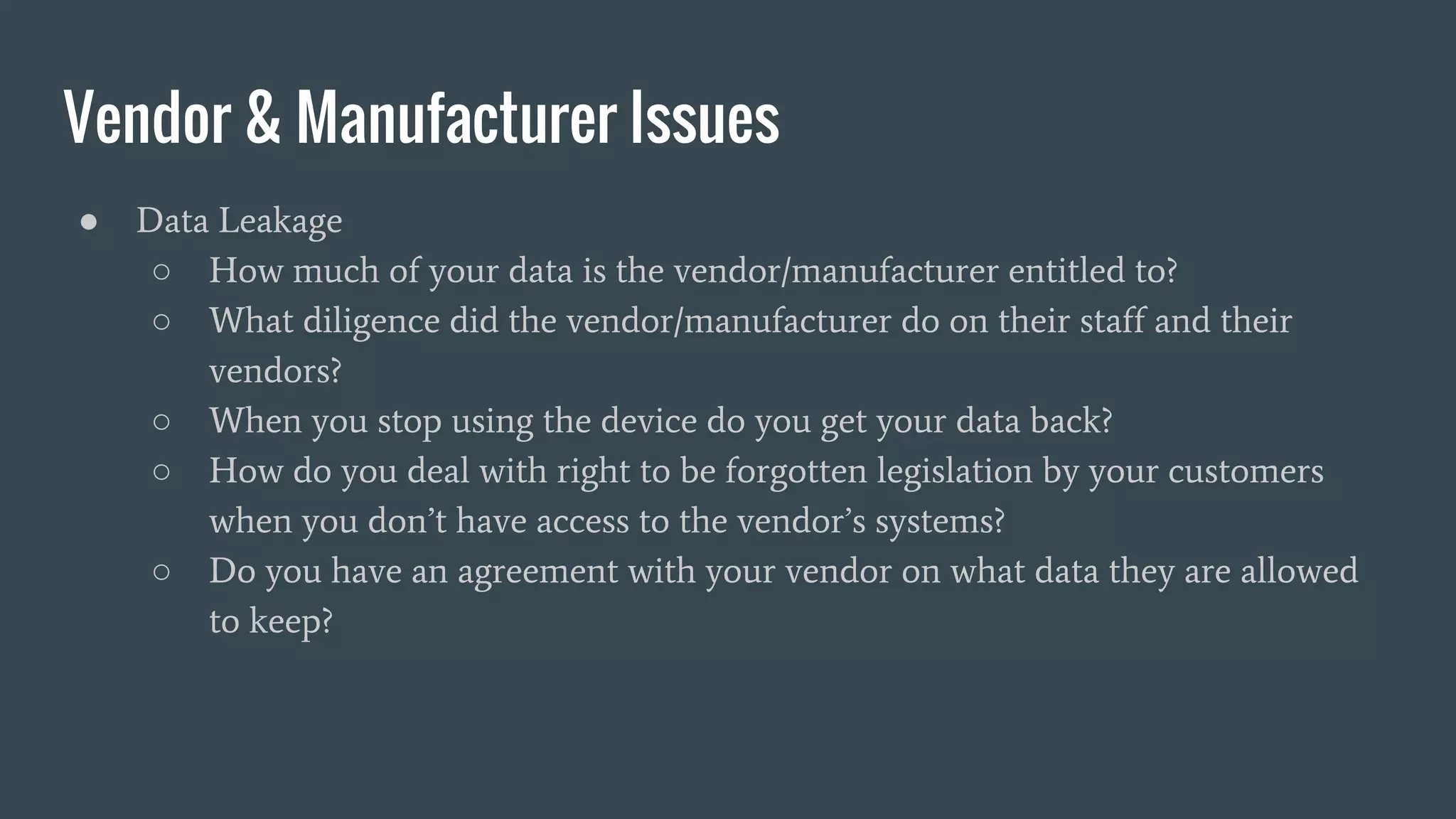
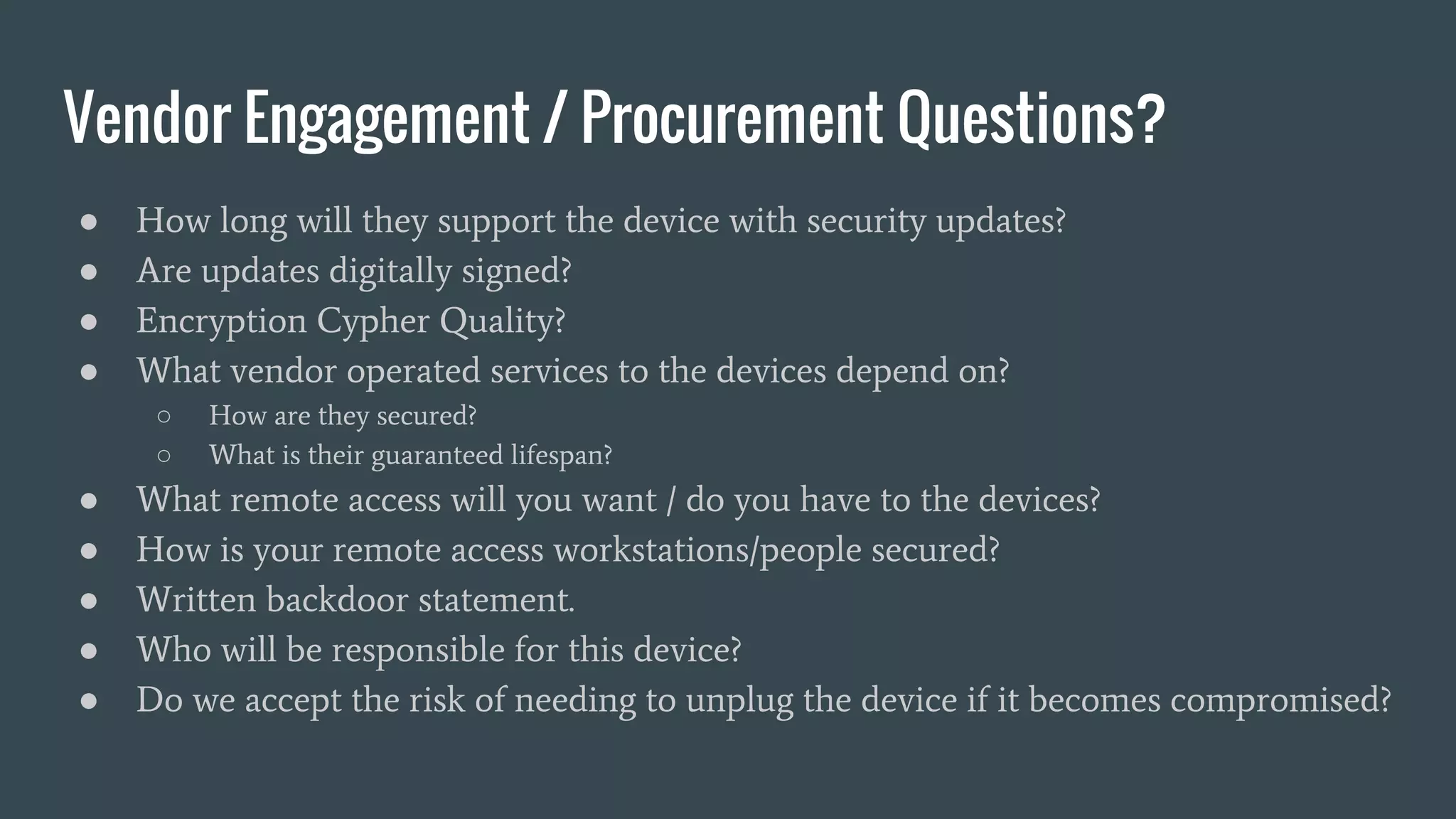
This document provides a summary of an IoT security presentation. It discusses what IoT devices are, why they pose security risks, and how others have been affected by IoT compromises. The presentation then outlines a basic IoT security checklist and covers common attack vectors like weak passwords, lack of encryption and patching, and physical security issues. It emphasizes the importance of inventory, segmentation, strong unique passwords, logging, and engagement with device vendors on security responsibilities and practices.




![Examples ● Building & Plant Automation (HVAC,
PLC, SCADA, Thermostats)
● Sensors
● Print Servers / Printers / Scanners
● IP Surveillance Cameras
● Physical Access Control Systems &
Intrusion Alarms, Intercoms
● Televisions/Displays, Audio Equipment,
● Video Game Consoles
● NAS - Storage Appliance
● Credit Card Payment Terminals
● [Routers, Firewalls, Switches, Wireless APs,
Wireless Point to Point (Trango)]
● Facility Backup Generator
● WIFI enabled…..](https://image.slidesharecdn.com/ryanwilson-apracticalapproachtomanagingthesecurityofiotdevicesinyourorganization-170201031131/75/Ryan-Wilson-ryanwilson-com-IoT-Security-5-2048.jpg)







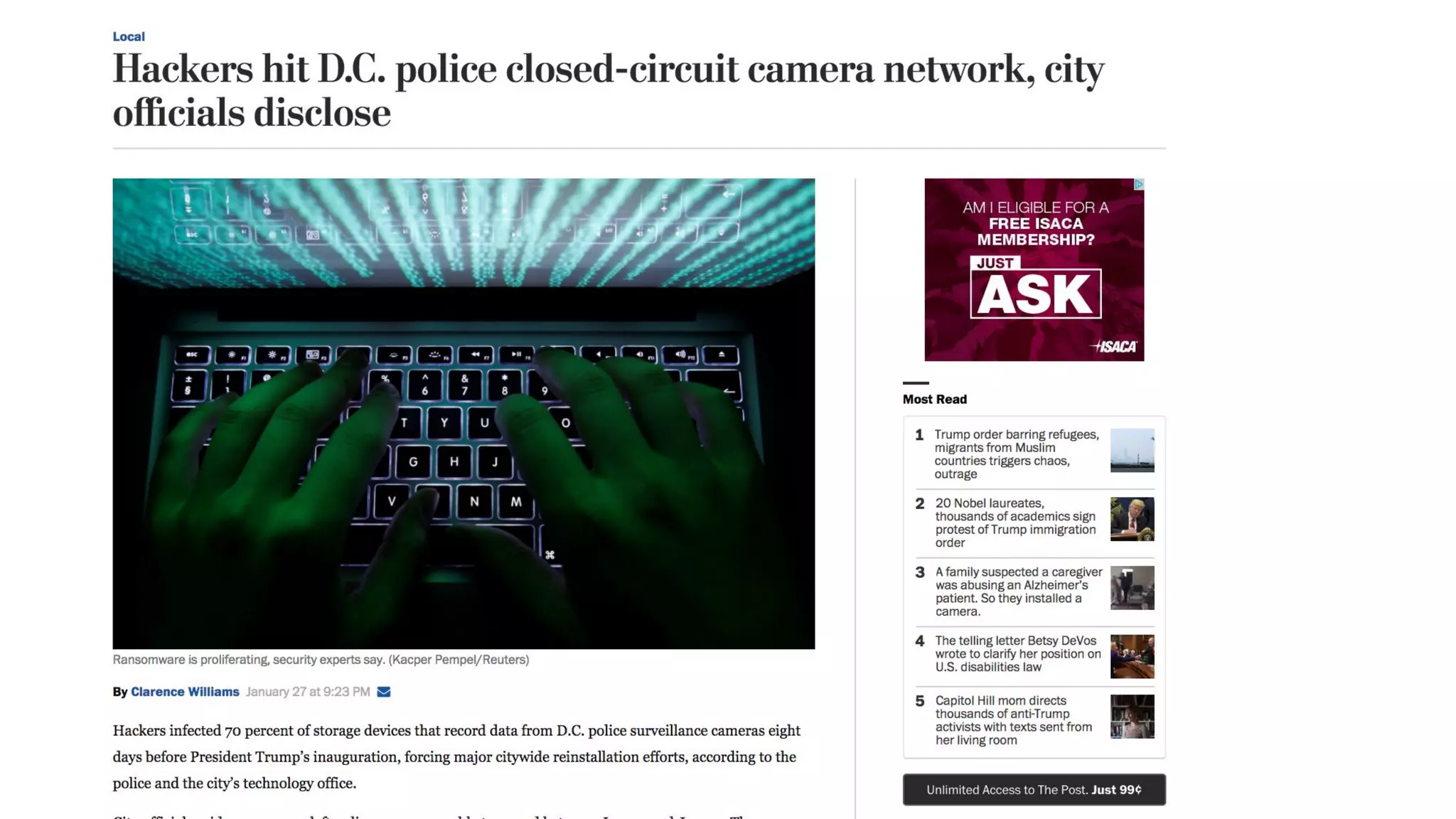
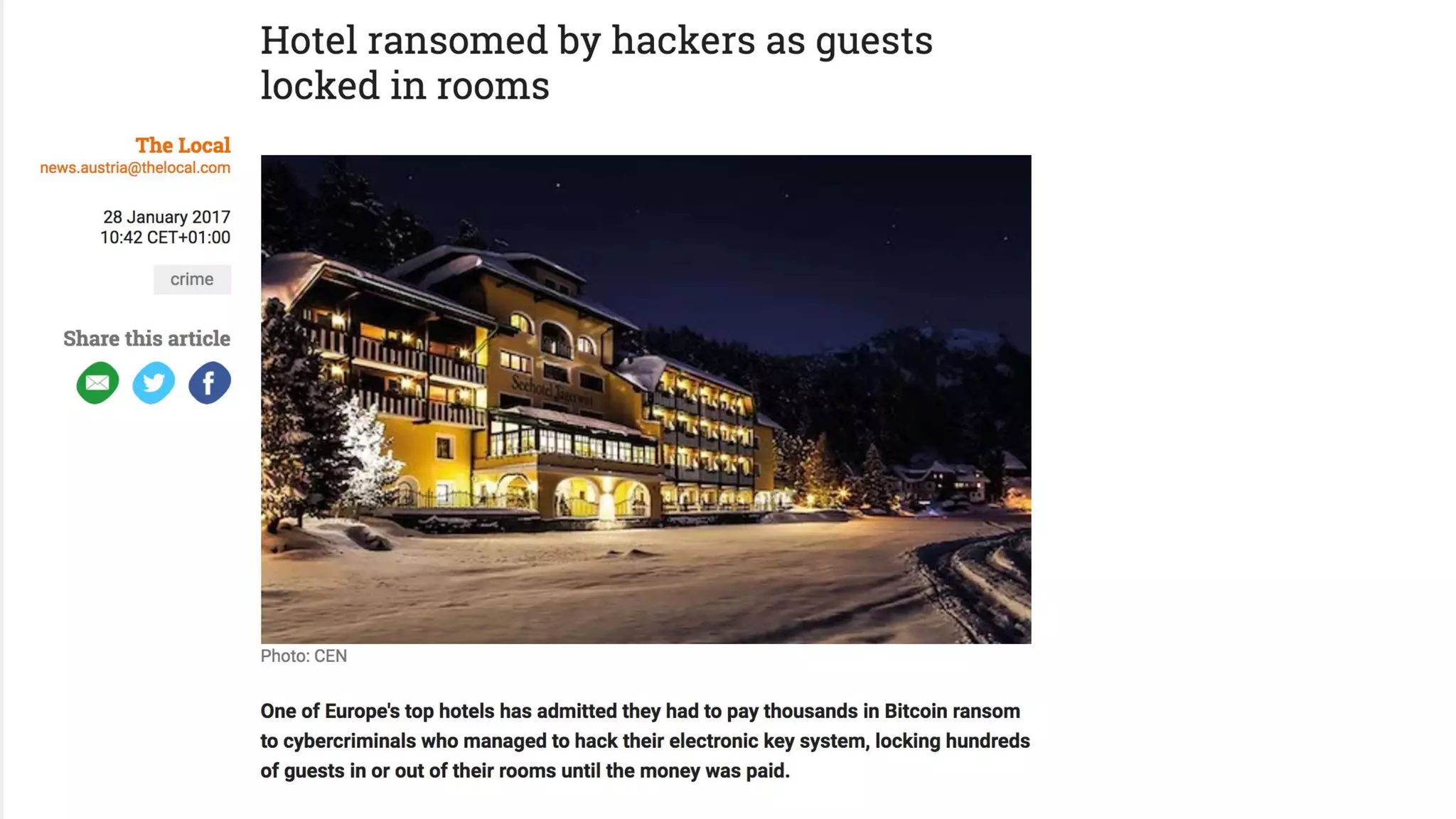
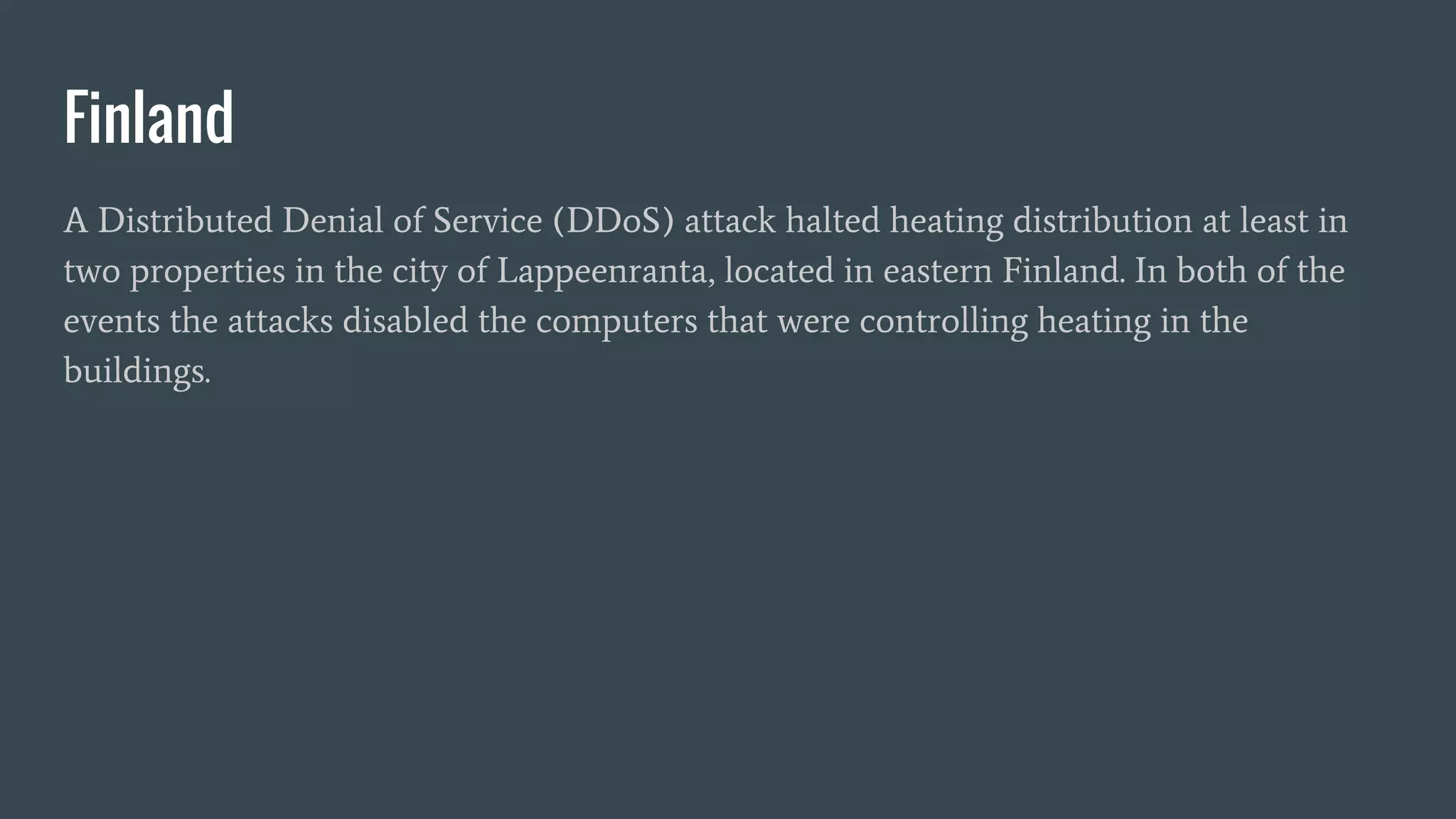
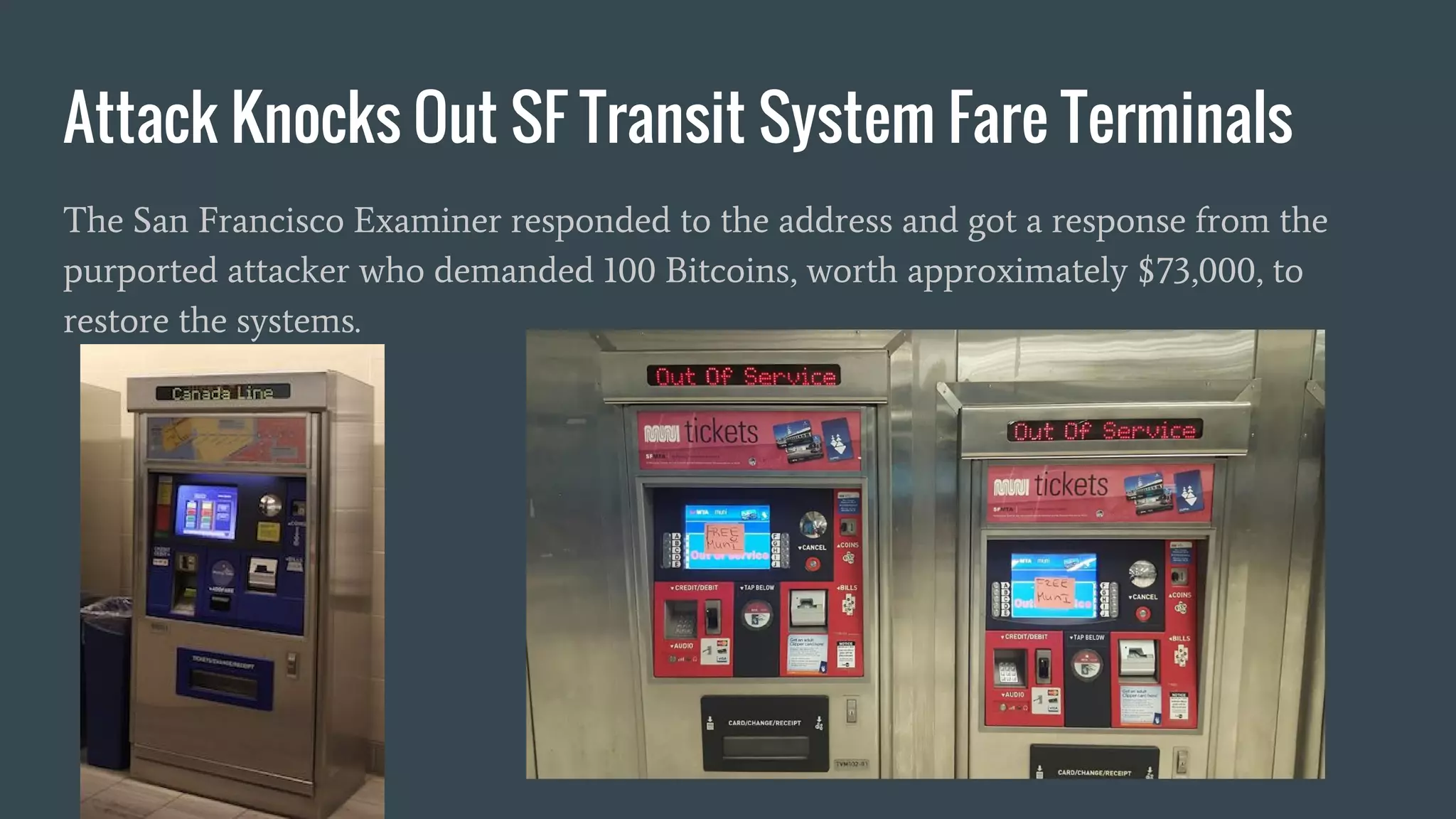














![Discovery / Inventory
● Not even being aware it is there...
● Have a method to discover new devices on your network [alienvault, SIEM, dhcp
etc]
● Establish a policy and inventory of non compute network connected devices in
your organization
● Inventory should outline who is responsible for the device, patches, passwords
and business justification for level of network access](https://image.slidesharecdn.com/ryanwilson-apracticalapproachtomanagingthesecurityofiotdevicesinyourorganization-170201031131/75/Ryan-Wilson-ryanwilson-com-IoT-Security-42-2048.jpg)


