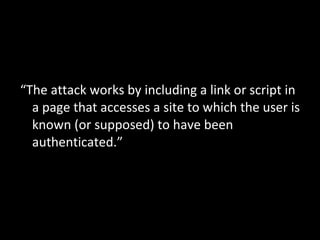
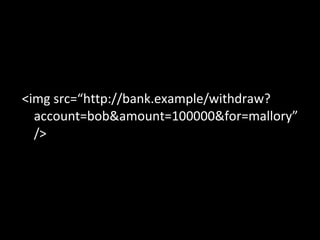
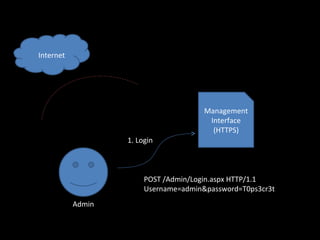
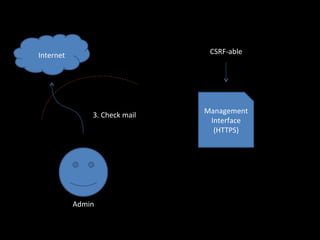
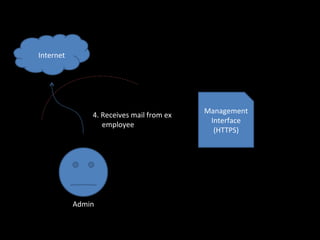
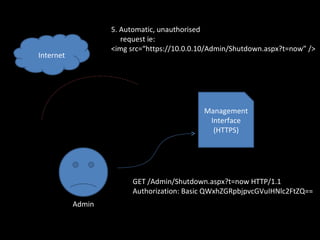
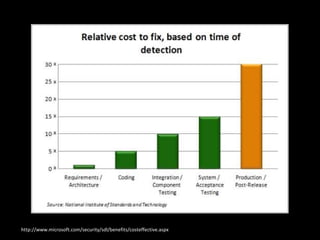
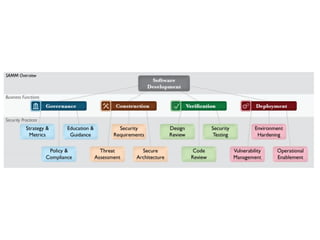
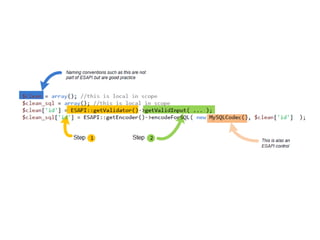
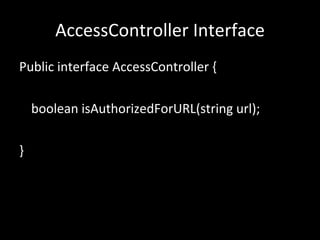
The document discusses several topics including security controls for web applications, common security vulnerabilities like CSRF, and quotes about power and responsibility. It provides recommendations for implementing security controls through interfaces and reference implementations to avoid reinventing the wheel and introduces common security control types like authentication, authorization, input validation and output encoding.