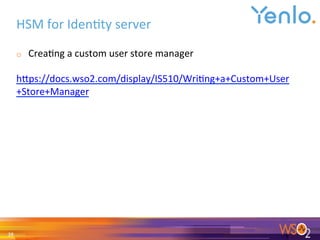
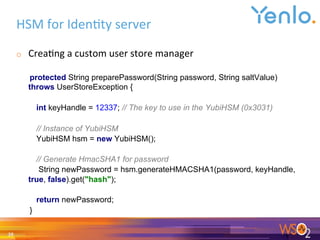
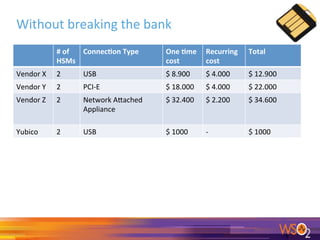
The document presents a webinar on integrating hardware security modules (HSM) with WSO2 Identity Server, highlighting the benefits of increased security without significant financial burden. It introduces speakers from Yubico and Yenlo, discusses various security aspects, and compares costs of different HSM vendors, emphasizing Yubico's affordability. Key takeaways include the advantages of using HSMs for secure cryptographic processing, illustrating their use cases in various industries such as government and healthcare.