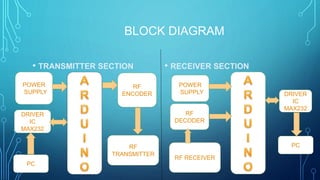
This document describes a wireless data encryption and decryption system for security in army applications. It contains an introduction, description, block diagram, power supply, advantages, applications, and conclusion. The system encrypts data on an Arduino board at the transmitter side before sending it via RF transmitter. At the receiver side, an Arduino board decrypts the received data from the RF receiver. The system provides secure wireless communication for military applications.