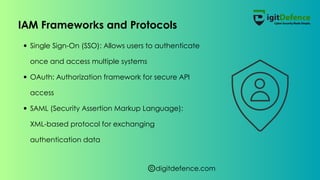
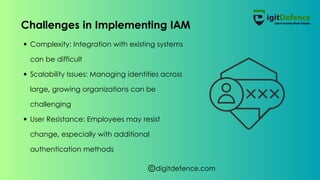
Identity and access management (IAM) is a crucial cybersecurity framework that helps organizations manage digital identities and control access to systems and data. It encompasses components like user identity management, authentication, and authorization, offering solutions both on-premises and cloud-based. Implementing IAM enhances security, ensures regulatory compliance, and improves operational efficiency, although challenges such as system integration complexity and user resistance may arise.