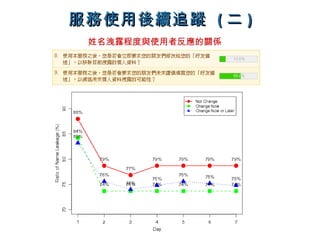
The document discusses social network services (SNS) and some of the privacy and security issues that can arise from them. It notes that personal information like real names, education histories, and other details can sometimes be involuntarily leaked through users' profiles and interactions on SNS sites, even if that information is not directly shared, through factors like contact descriptions, images, and relationships. It also discusses how data posted on SNS sites can never be fully deleted from the internet over time.