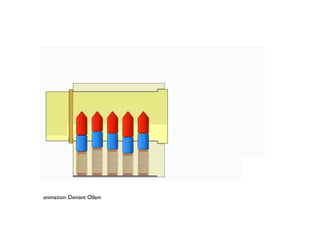
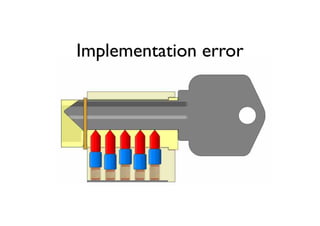
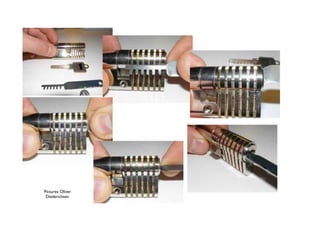
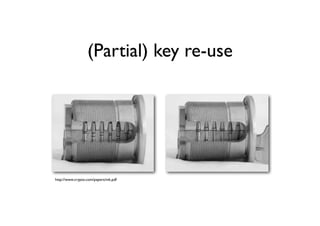
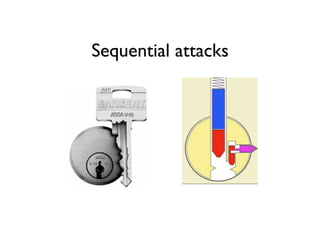
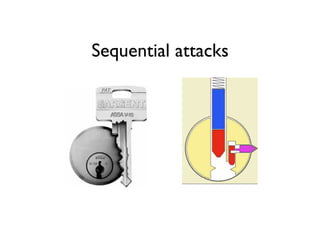
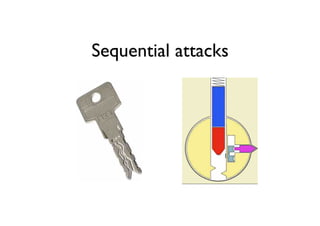
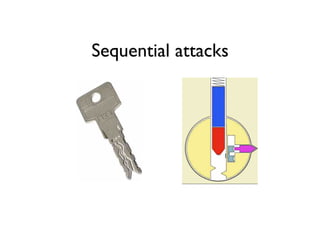
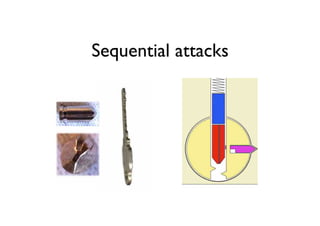
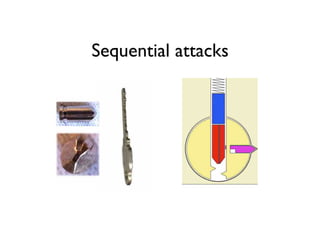
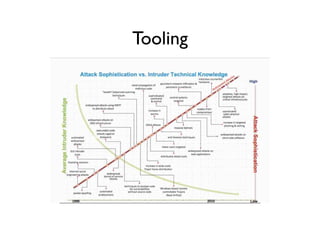
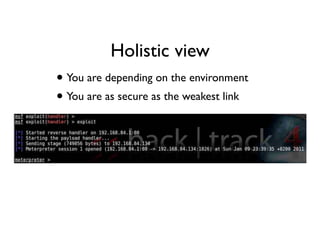
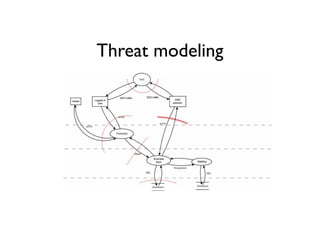
The document discusses security in software and locks, emphasizing the importance of integrating security during the design phase rather than treating it as an afterthought. Walter Belgers, a lockpicker and security expert, highlights various methods of attacks, including social engineering and brute force, and stresses the need for awareness and robust security measures. Additionally, it touches on the significance of certification and threat modeling in maintaining security.