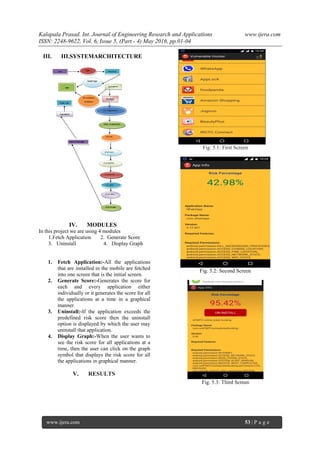
The document outlines the 'Vulnerable Hunter' application, designed to identify risks associated with mobile applications by generating risk scores and allowing users to uninstall potentially harmful apps. It addresses the increasing usage of smartphones and the vulnerabilities of many applications, promoting user convenience without needing an internet connection. The application consists of modules that fetch installed apps, generate scores, allow uninstallation, and display risk scores graphically.

![Kalapala Prasad. Int. Journal of Engineering Research and Applications www.ijera.com
ISSN: 2248-9622, Vol. 6, Issue 5, (Part - 4) May 2016, pp.01-04
www.ijera.com 54 | P a g e
Fig. 5.4: List of Permissions
Fig. 5.5: Permission Information
VI. CONCLUSION
“VULNERABLE HUNTER” effectively
finds the risk in mobile applications and generates
score for each application. It is very useful to all the
smart phone users who are crazy about all new
applications. So by this application one can avoid
the risky applications that causes the decrease in
mobile performance.
REFERENCES
[1]. Java How To Program, Ninth Edition,
Deitel&Deitel.
[2]. Android Programming :The Big Nerd
Ranch Guide By Bill Philips & Brain
Hardy.
[3]. Programming Android
ByG.BlakeMeike& Masumi
Nakamura.
[4]. Website references used:
[5]. www.android.developer.com
[6]. www.wikipedia.com
[7]. www.stackoverflow.com
[8]. www.google.com](https://image.slidesharecdn.com/j060505052054-160811042106/85/Vulnerable-Hunter-3-320.jpg)