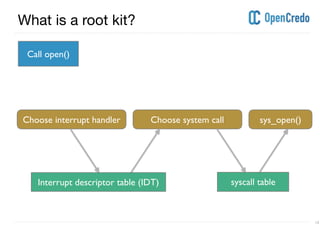
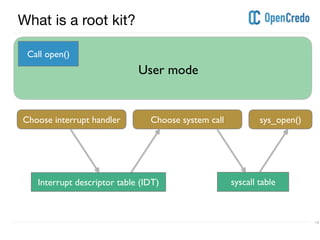
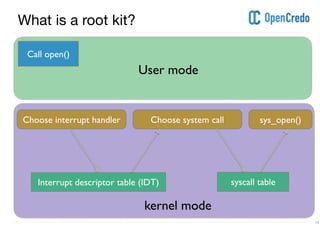
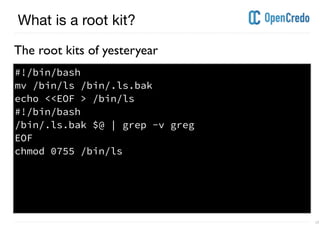
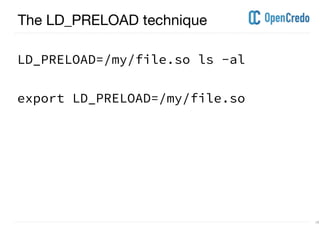
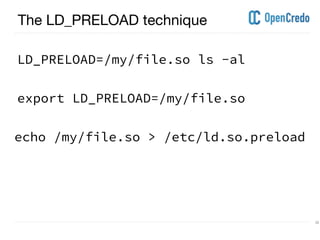
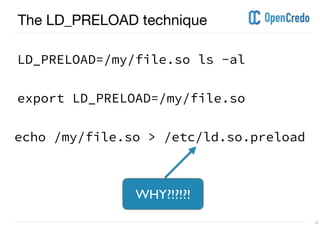
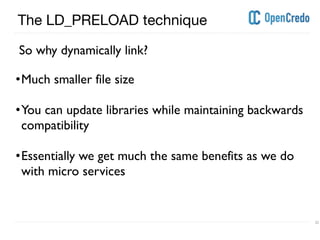
The document discusses userland rootkits, focusing on their functionality, detection, and removal. It explains the concept of rootkits as malicious software that hides the presence of users and processes while maintaining unauthorized access. Additionally, it covers techniques such as ld_preload for exploitation and tools like rkhunter for rootkit detection and removal.