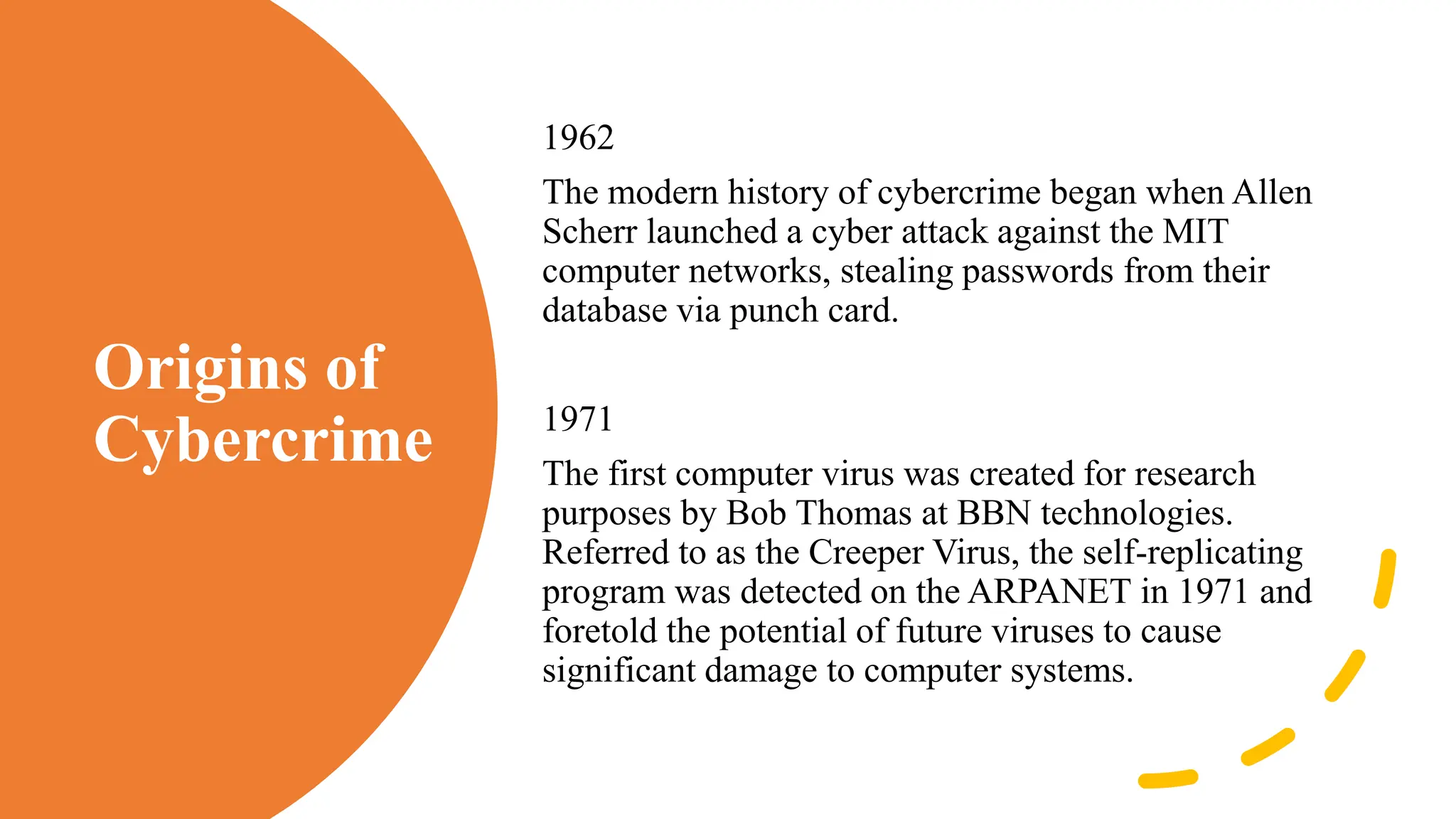
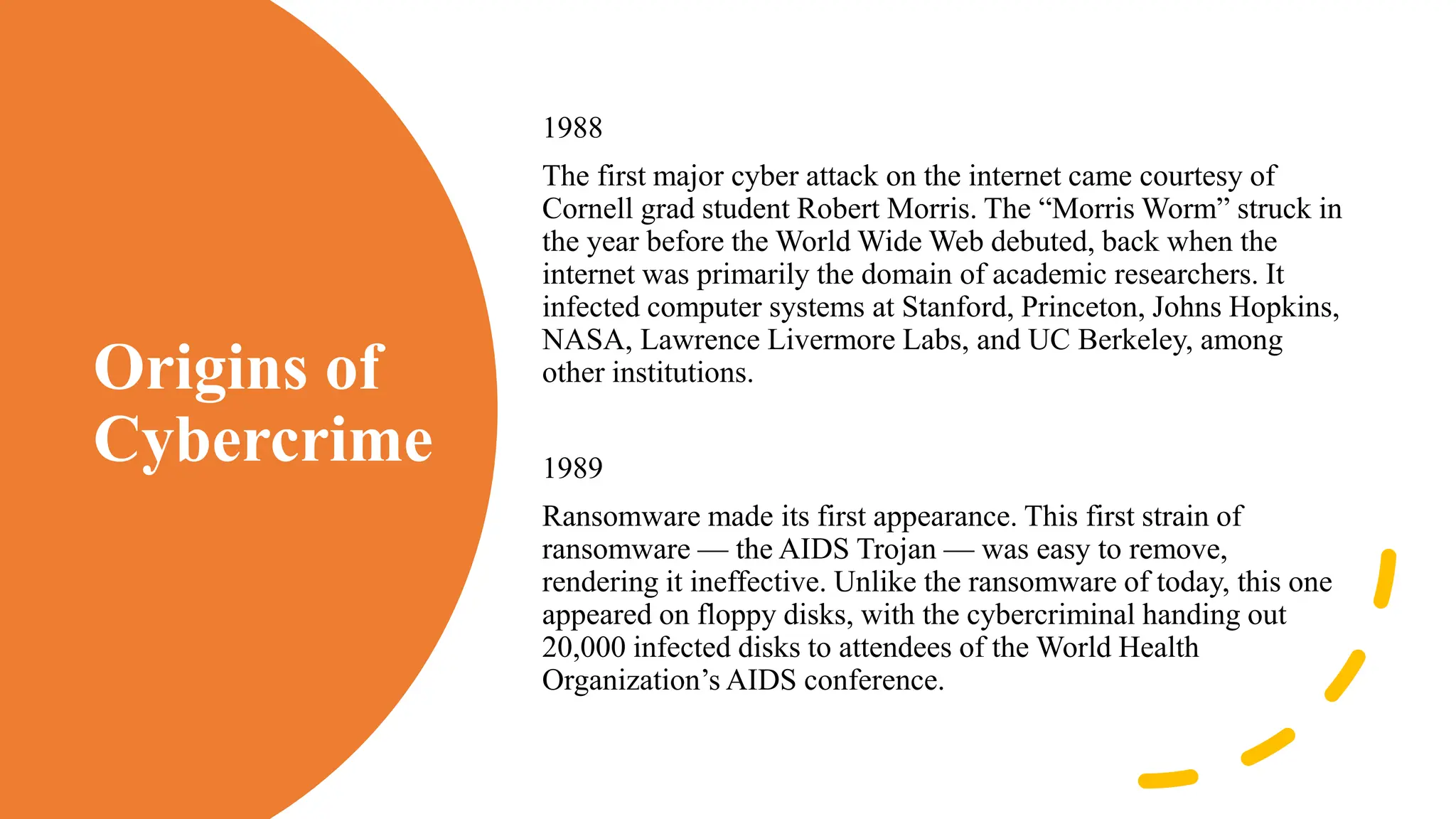
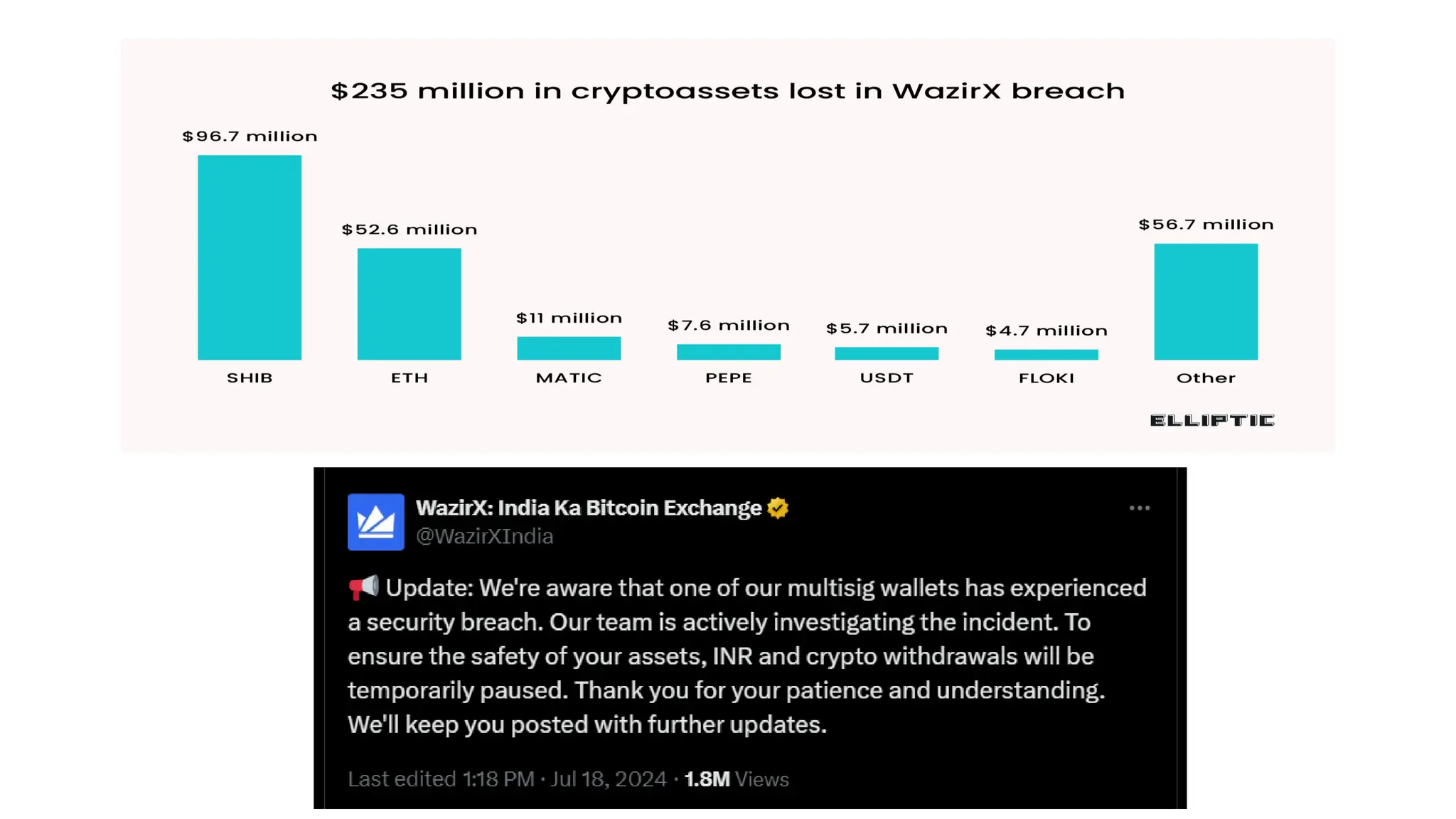
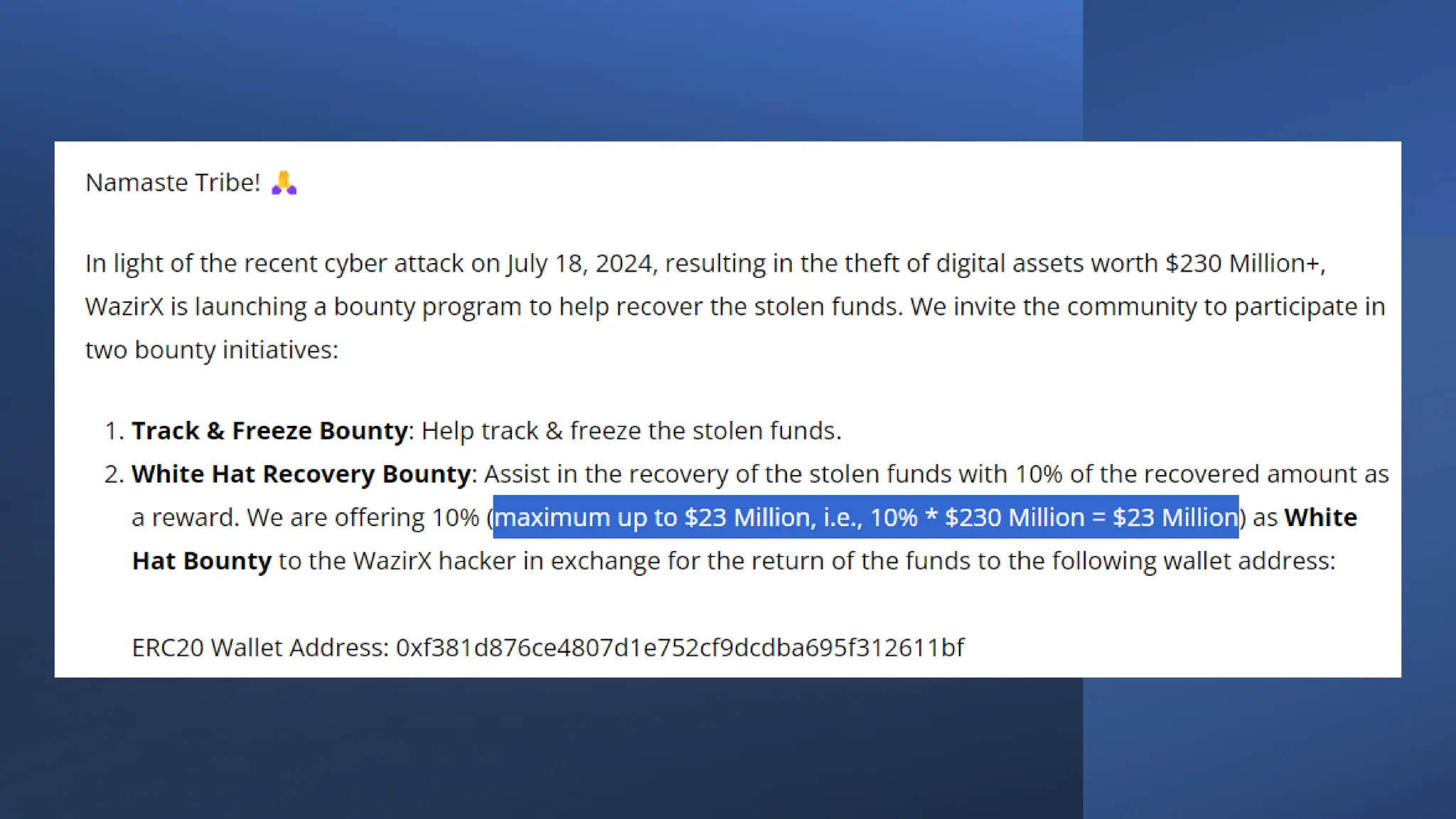
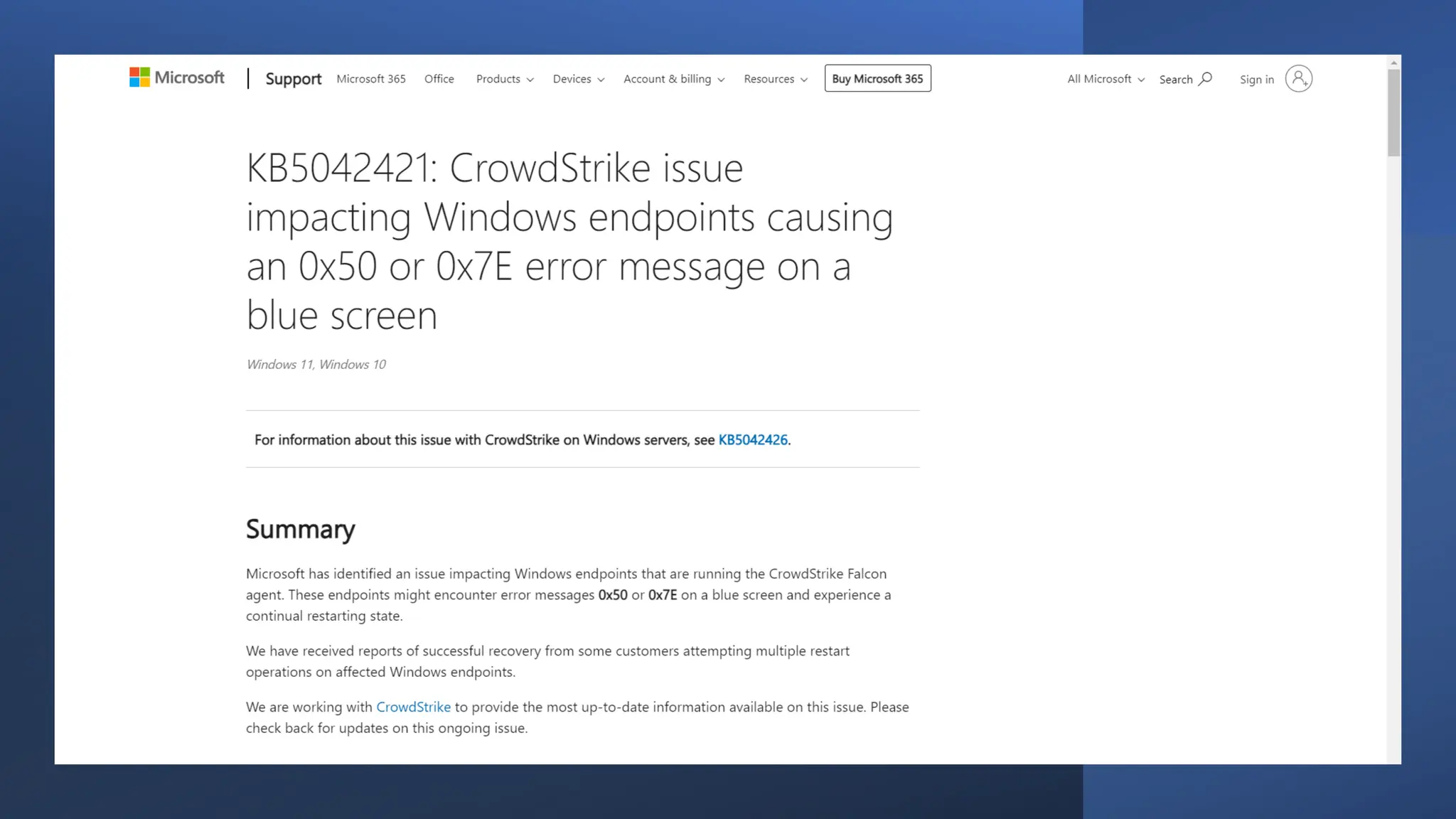
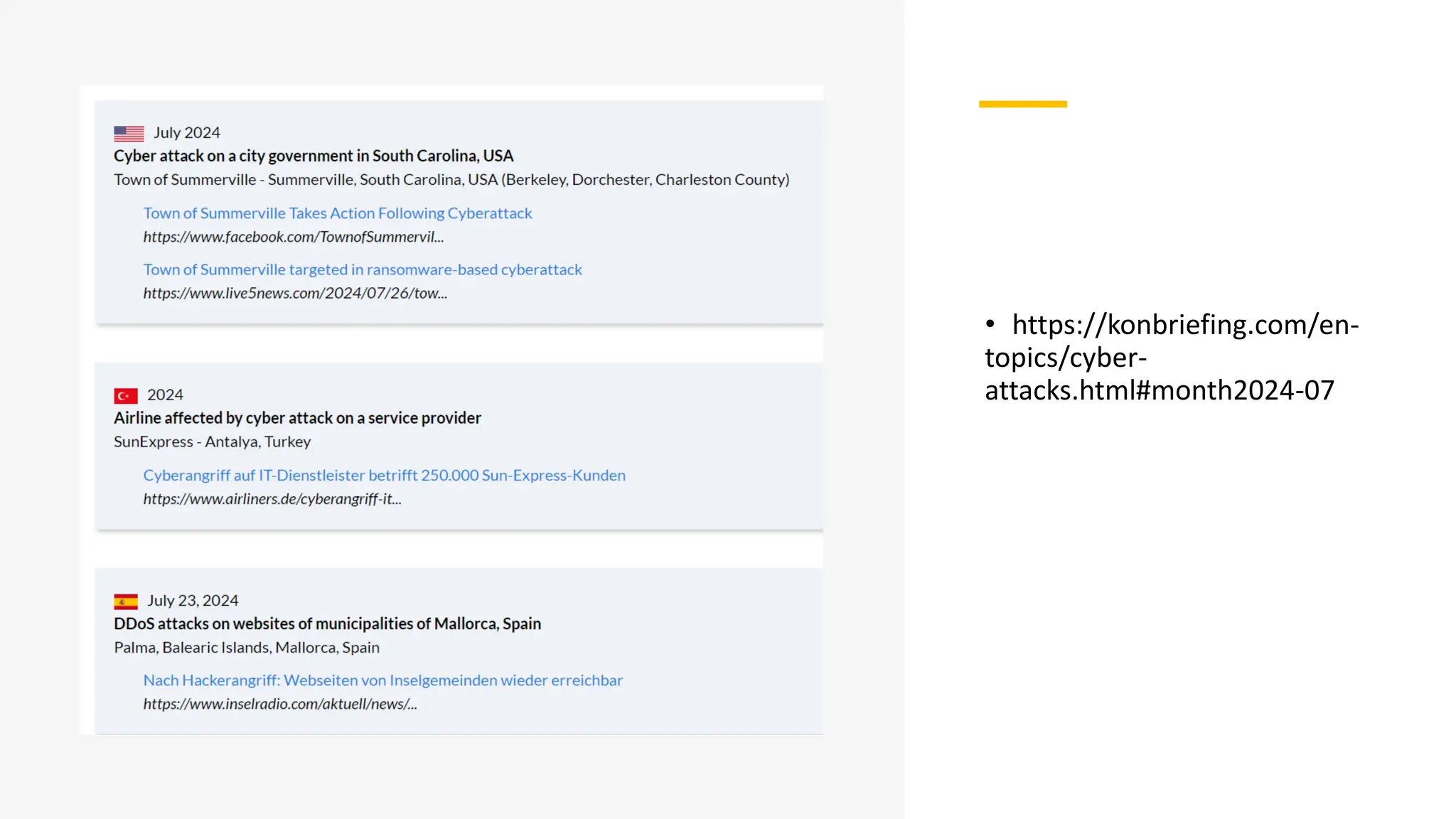
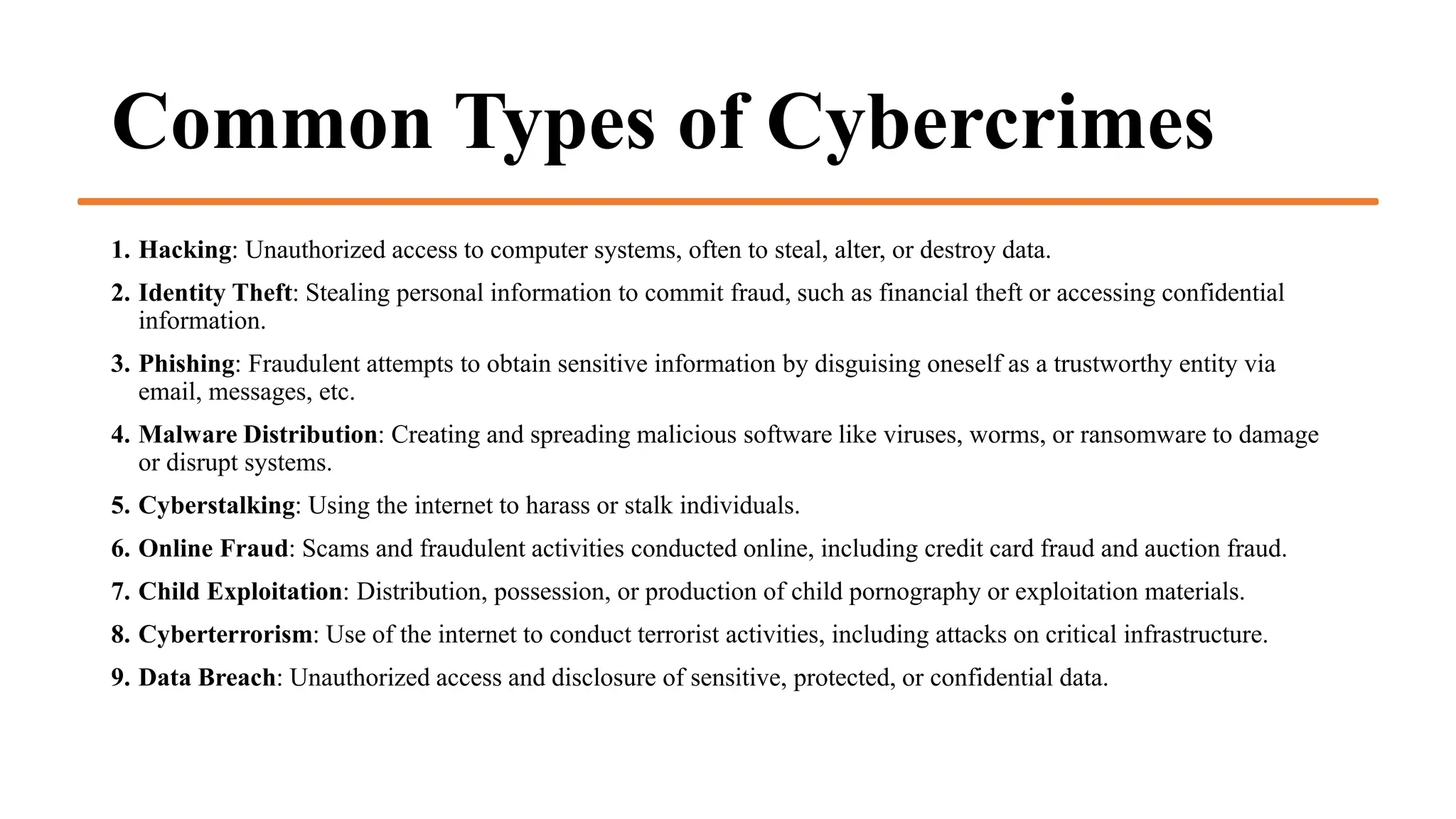
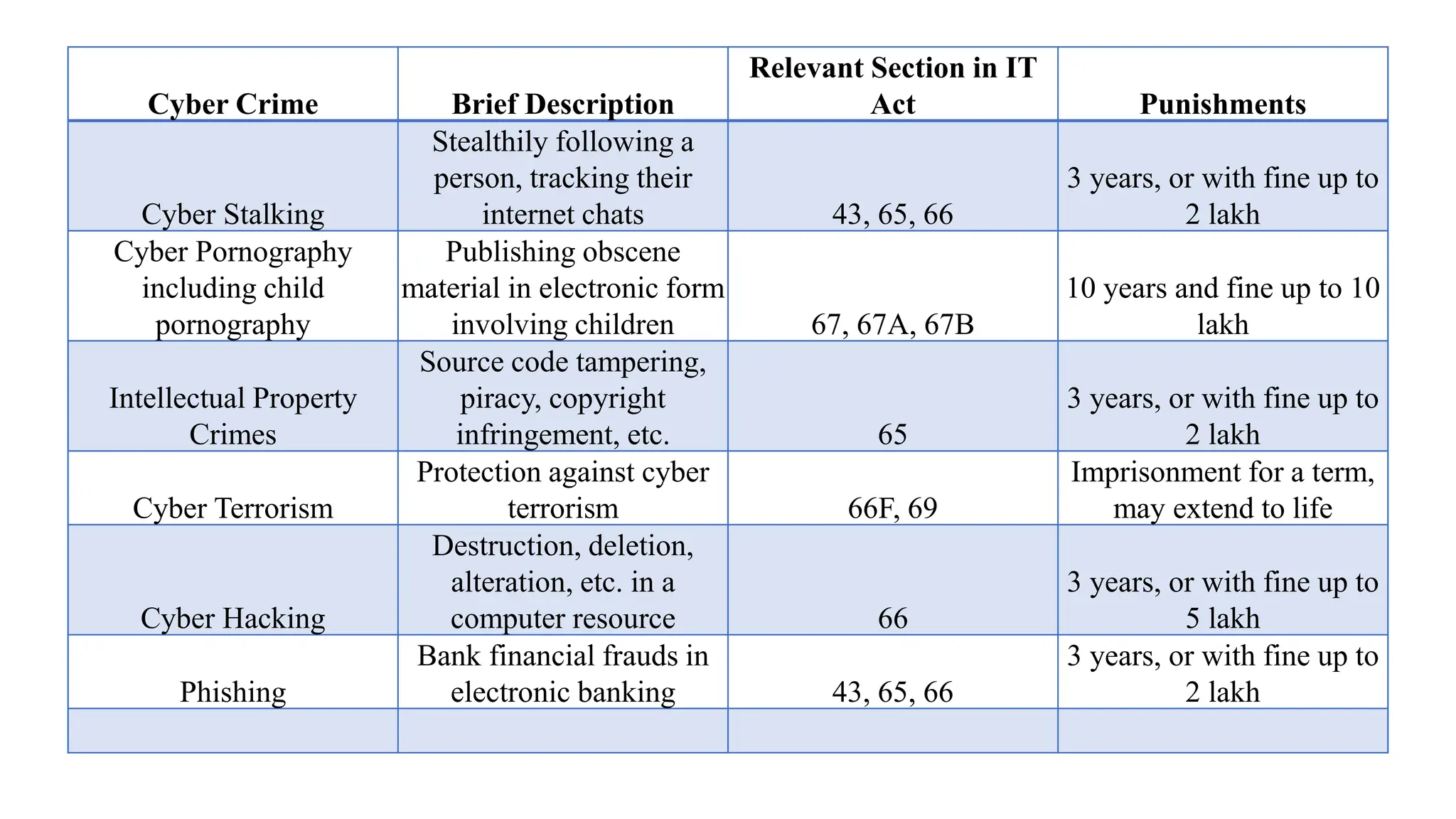
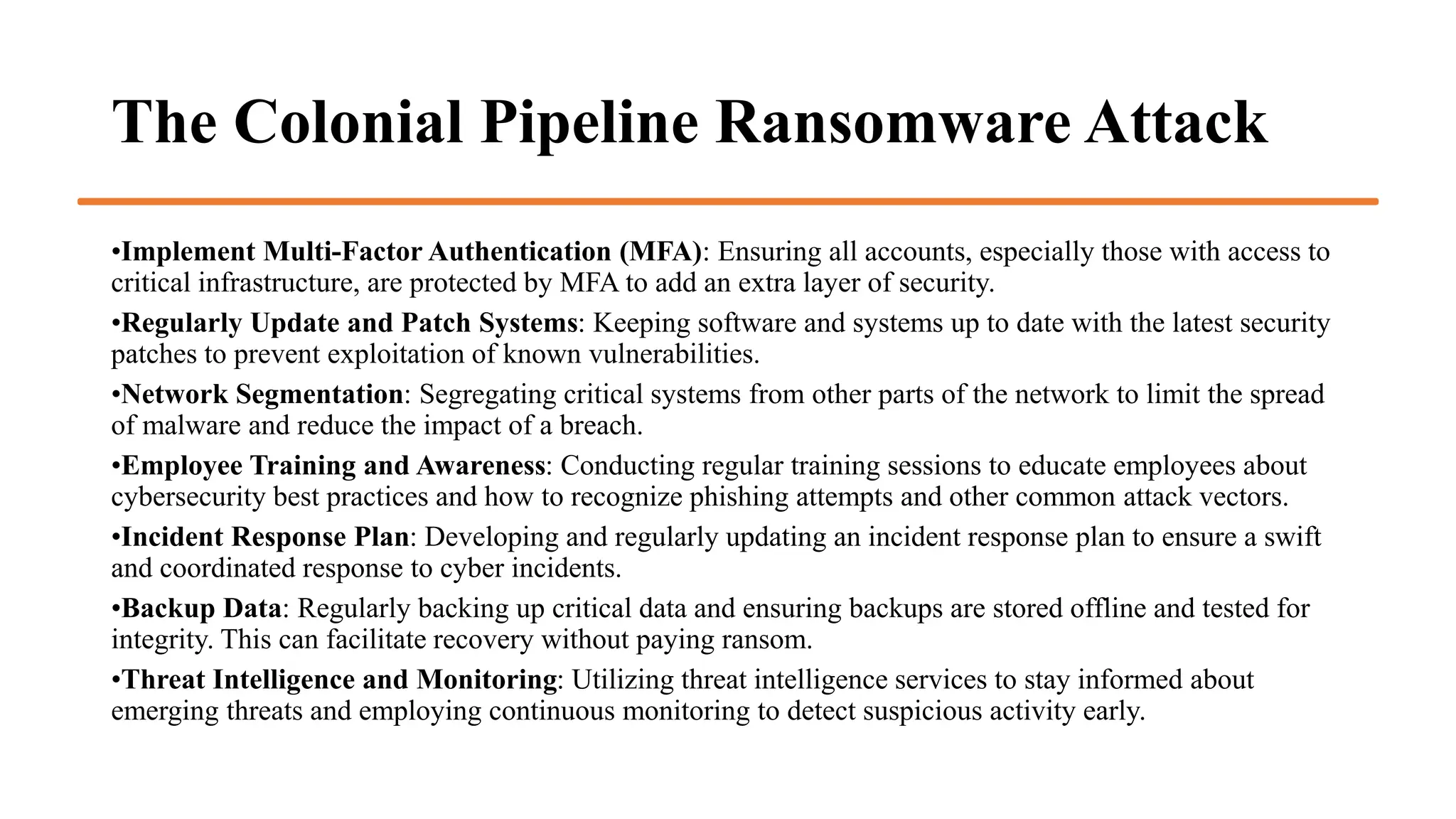
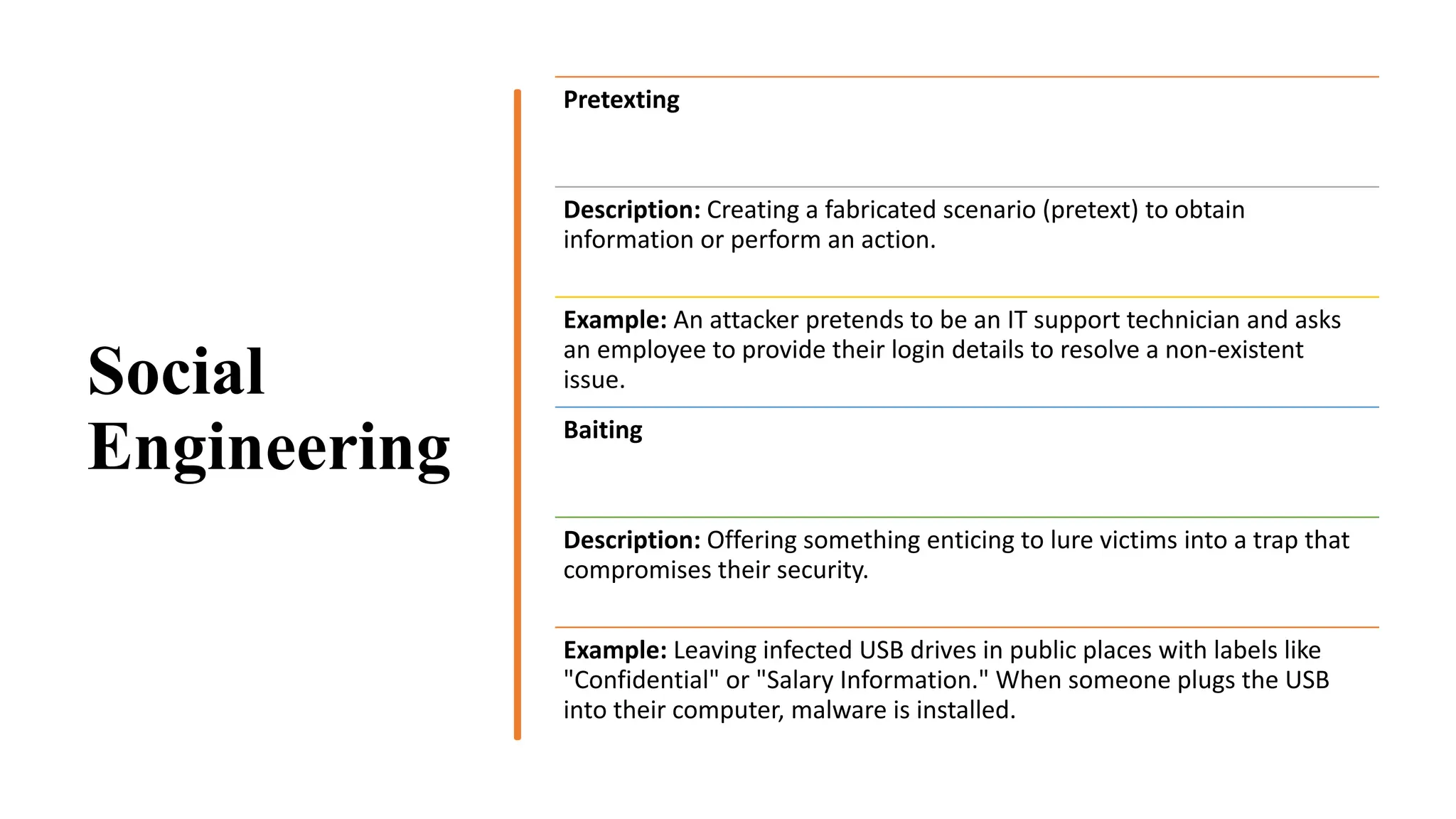
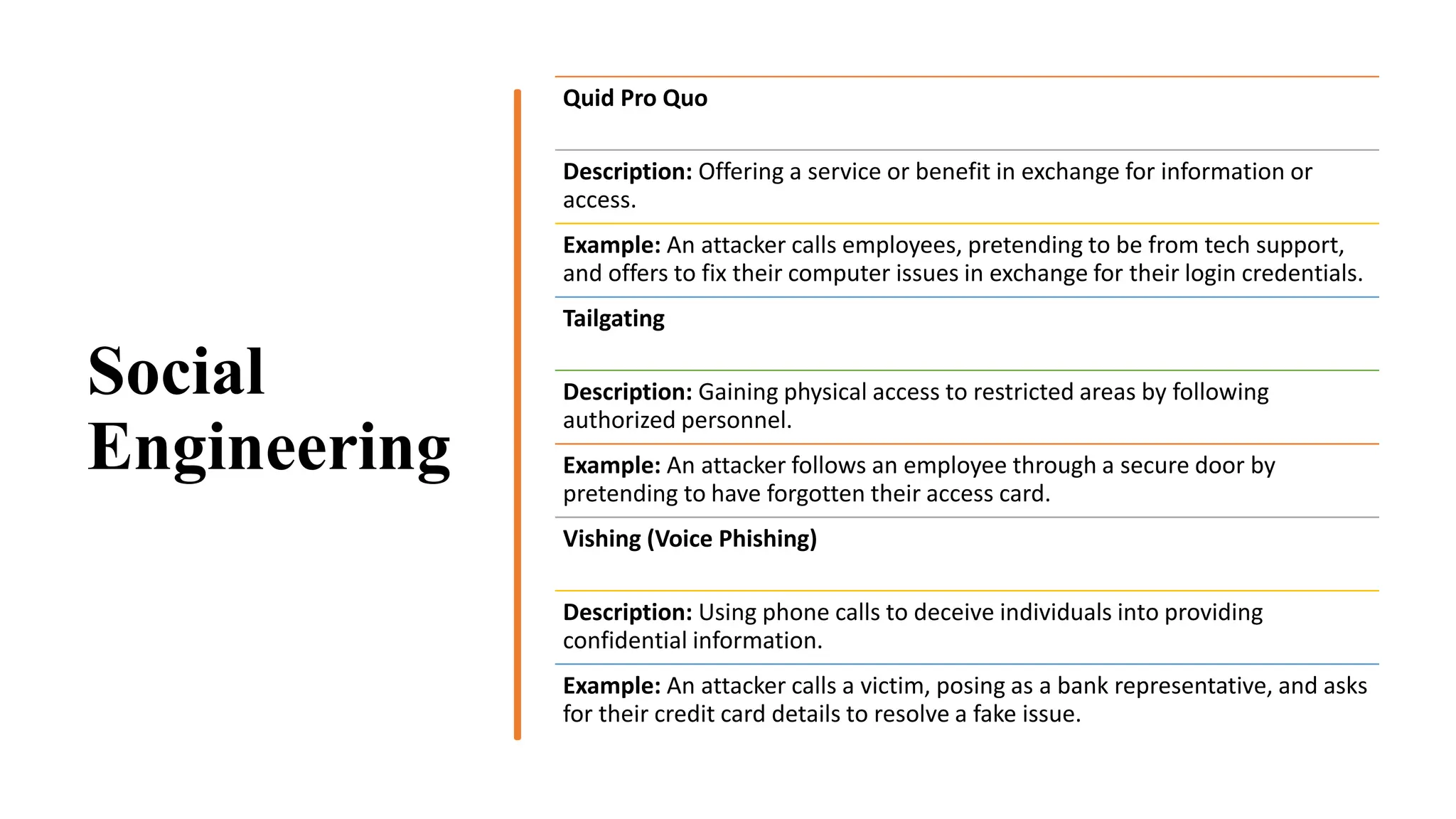
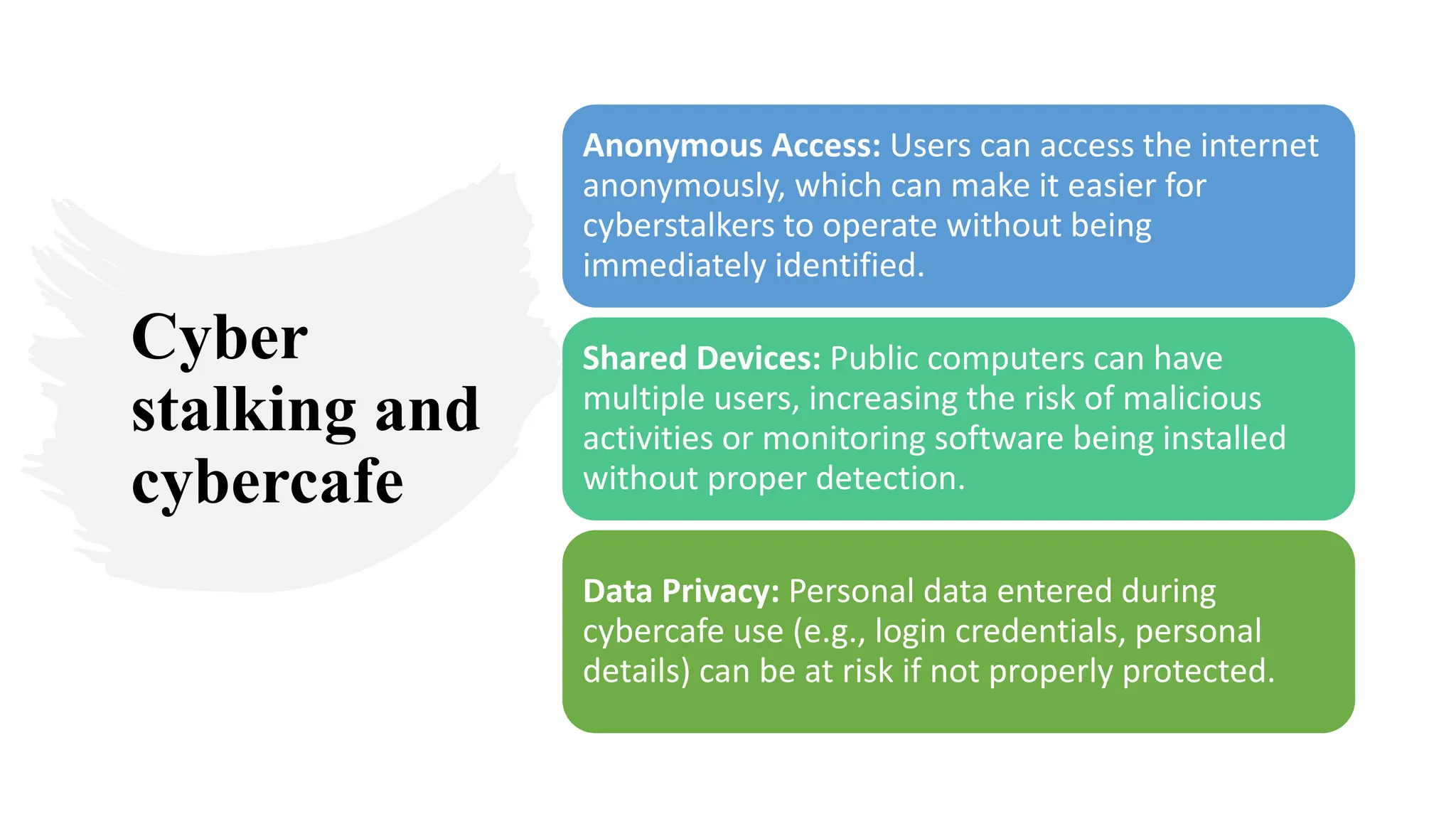
The document provides an extensive overview of cybercrime, exploring its definitions, origins, types, and preventive measures. It details various cyber offenses, including hacking, identity theft, and cyber terrorism, and highlights notable historical events such as the Colonial Pipeline ransomware attack. Additionally, it outlines laws, classifications of crimes, and methods used by cybercriminals, along with strategies for prevention and protection against cyber threats.