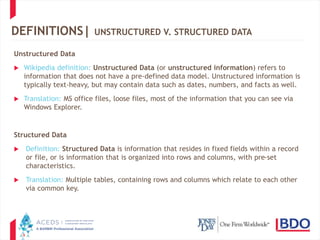
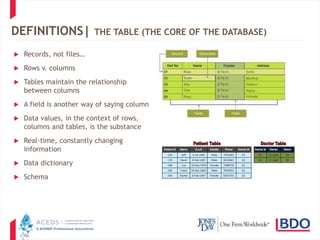
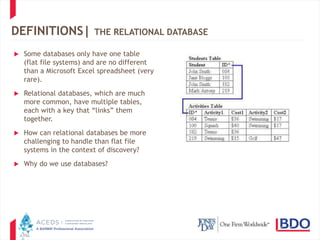
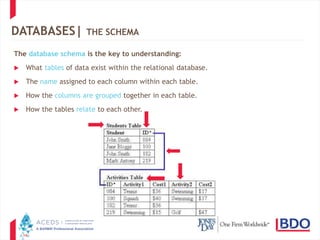
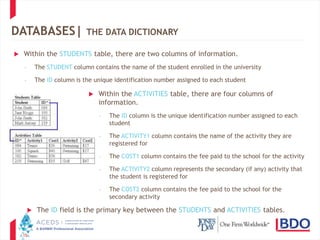
The document discusses database discovery and provides an overview of key concepts. It begins with definitions of structured and unstructured data as well as relational databases. It then outlines two common approaches to database discovery - obtaining the raw data through a "brute force" method or focusing on existing reports. The document cautions that both approaches have pros and cons and advocates balancing needs through meet and confer discussions to determine the appropriate scope. It concludes with several practice pointers regarding assessing database versus report production and addressing challenges that can arise.