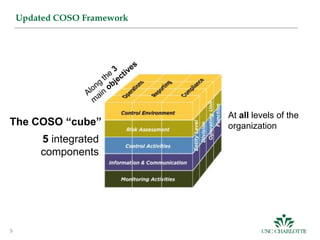
This document outlines the fundamentals of internal controls, their objectives, and the COSO framework, which provides a structured approach to implementing internal controls across an organization. It emphasizes the importance of identifying risks and establishing a control environment alongside risk assessment, control activities, information communication, and monitoring. Additionally, it stresses the need for continuous evaluation and adaptation of internal controls to ensure effectiveness and compliance with regulations.