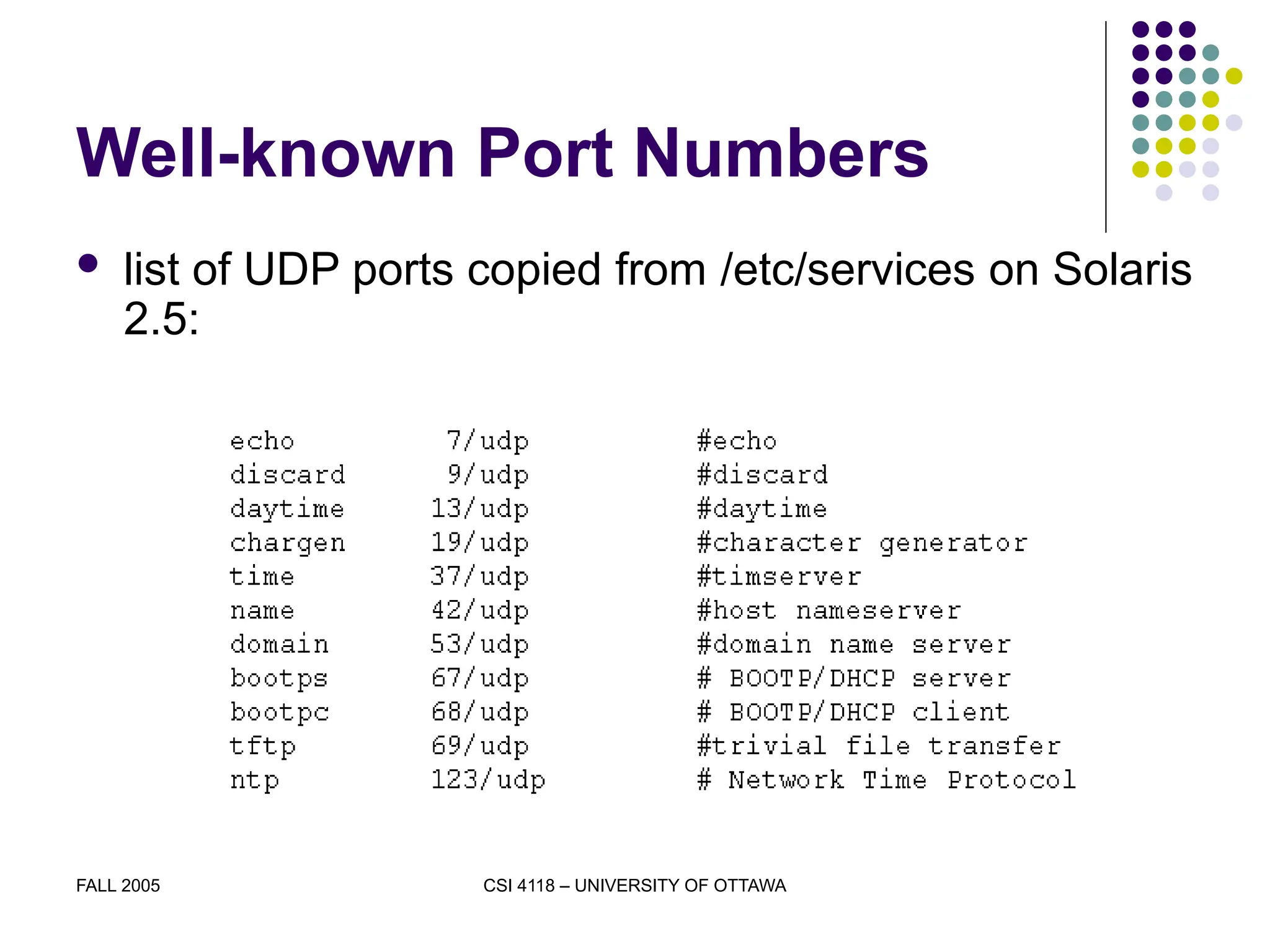
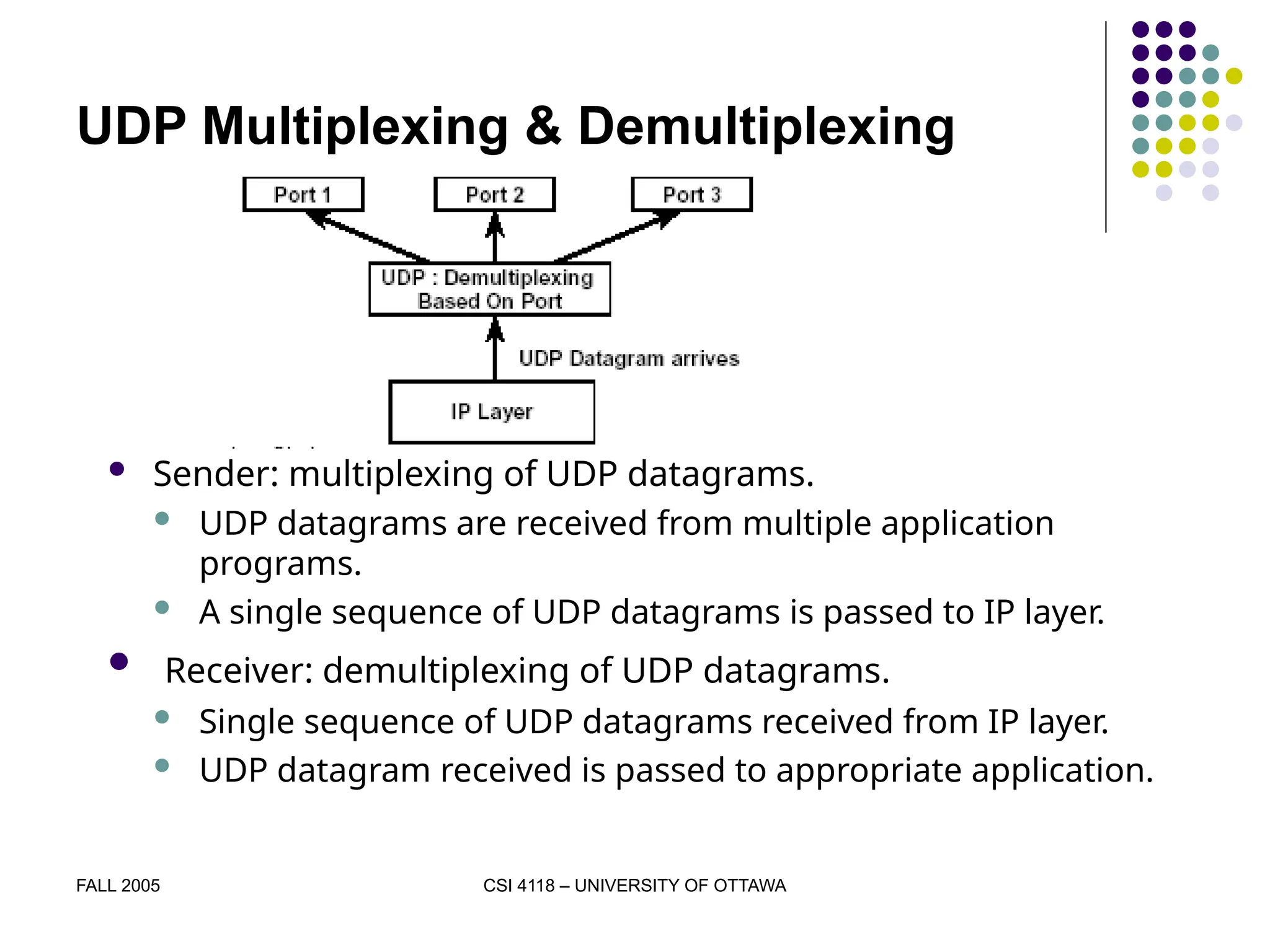
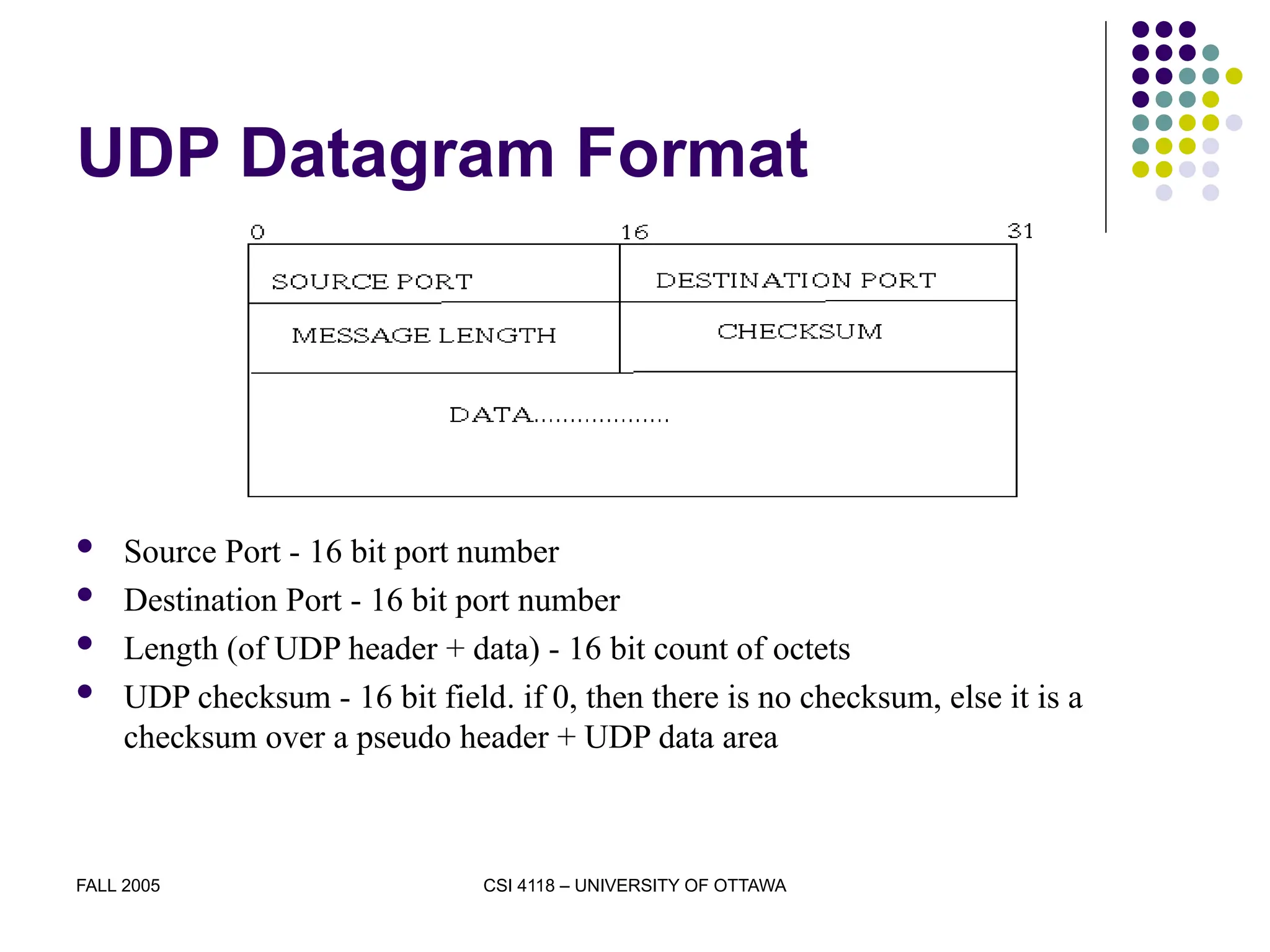
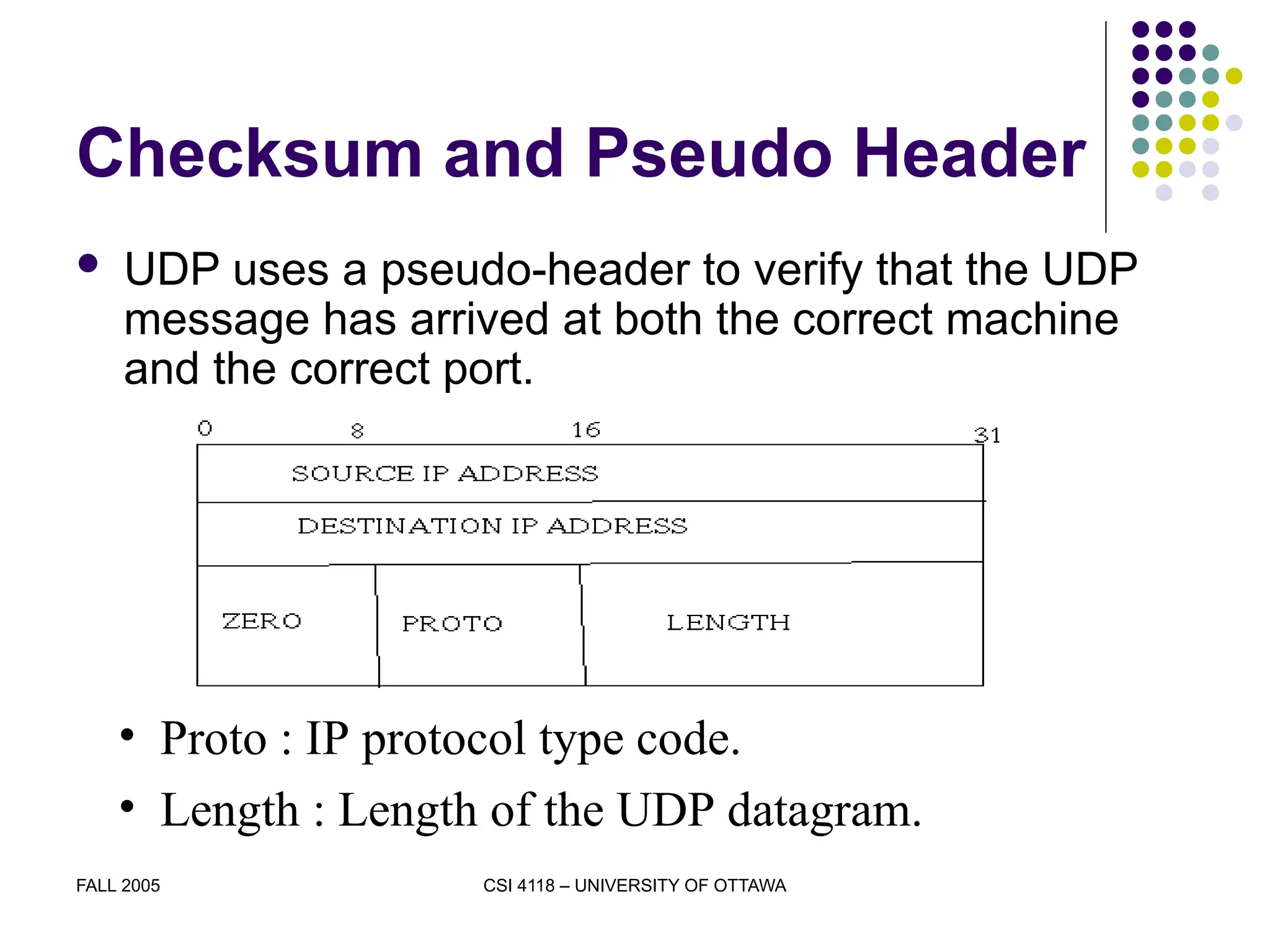
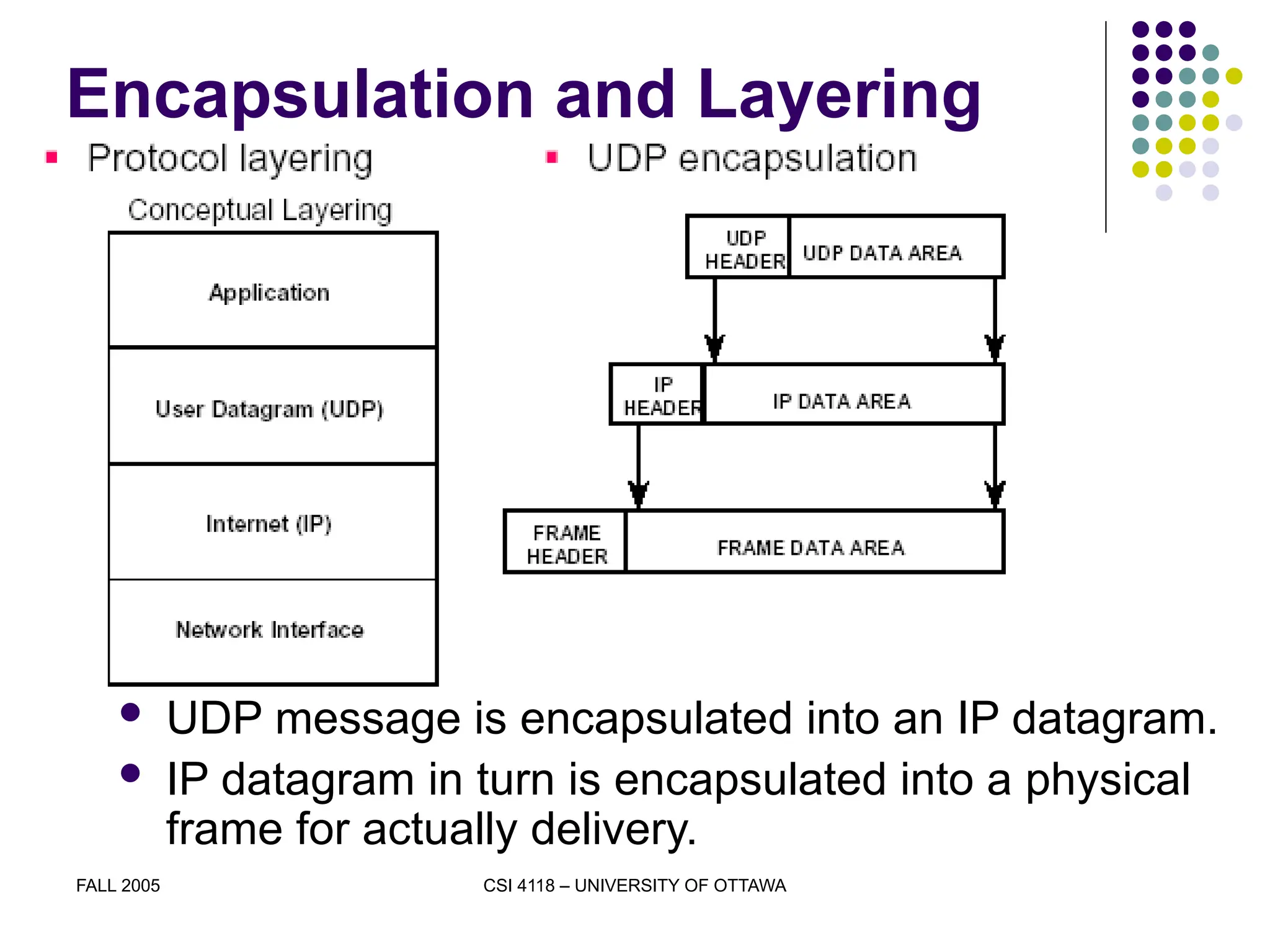
The document discusses the User Datagram Protocol (UDP) as part of the TCP/IP protocol suite, highlighting its characteristics, such as being connectionless, message-oriented, and best-effort in data delivery. It explains how UDP identifies applications using port numbers and details the format of UDP datagrams, including source and destination ports, length, and checksum. Additionally, it covers the concepts of multiplexing and demultiplexing in relation to UDP communication between applications.