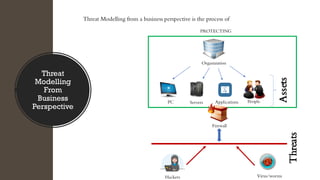
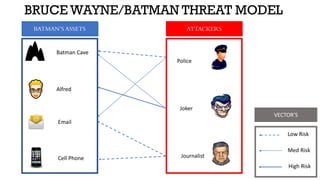
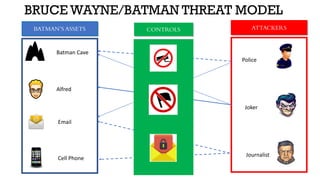
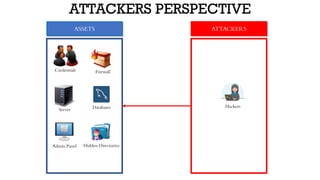
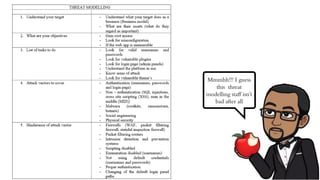
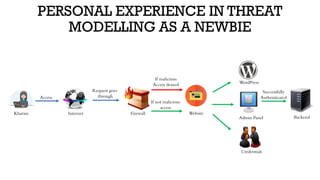
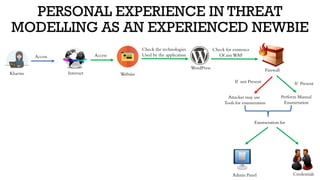
The document discusses threat modeling in penetration testing from both business and attackers' perspectives, emphasizing the importance of identifying and mitigating potential threats to systems and assets. It provides insights into creating attacker profiles, threat catalogs, and determining where to focus security efforts. The author, Kharim Mchatta, shares personal experiences and methods used in threat modeling within the cybersecurity field.