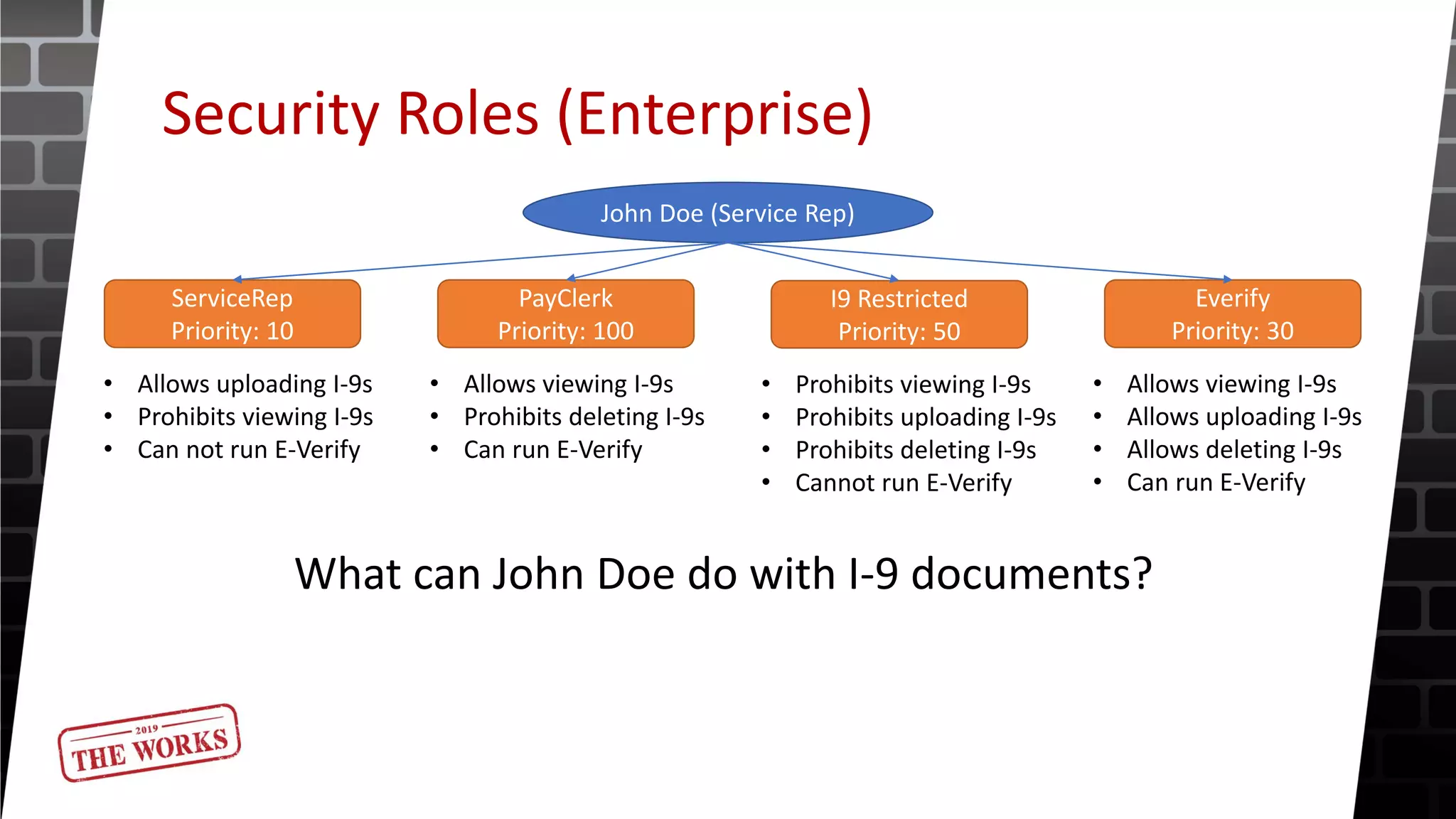
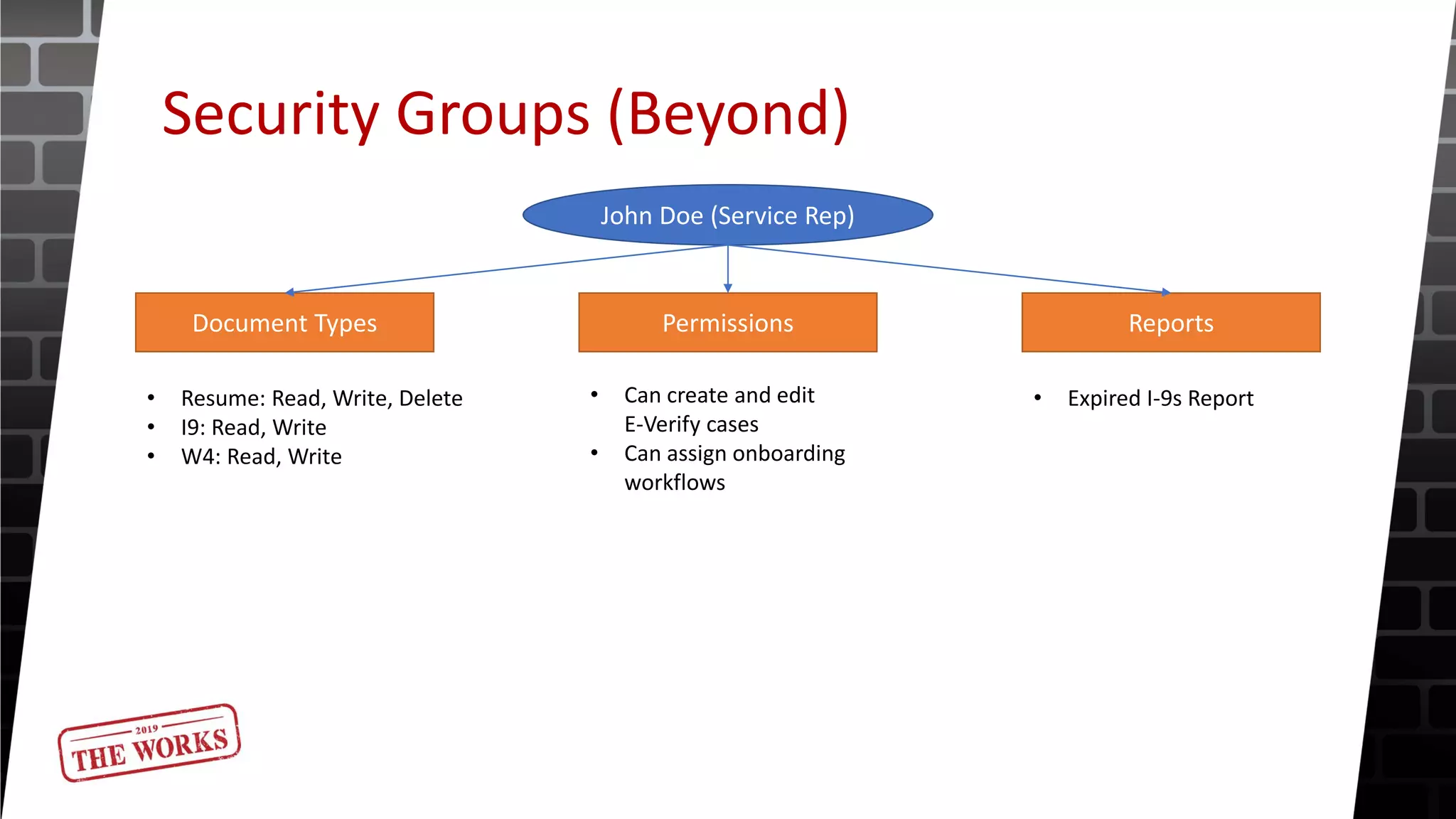
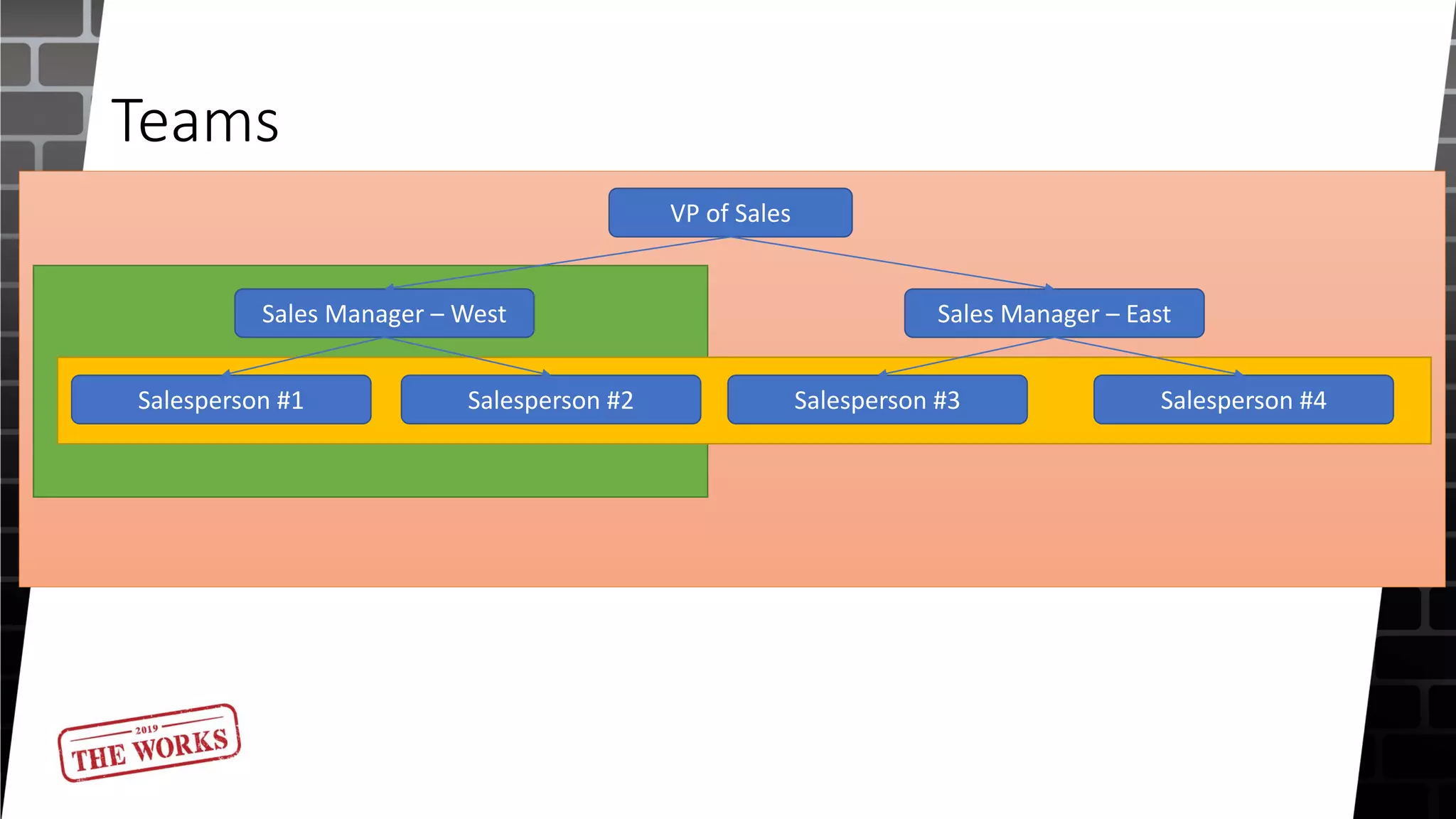
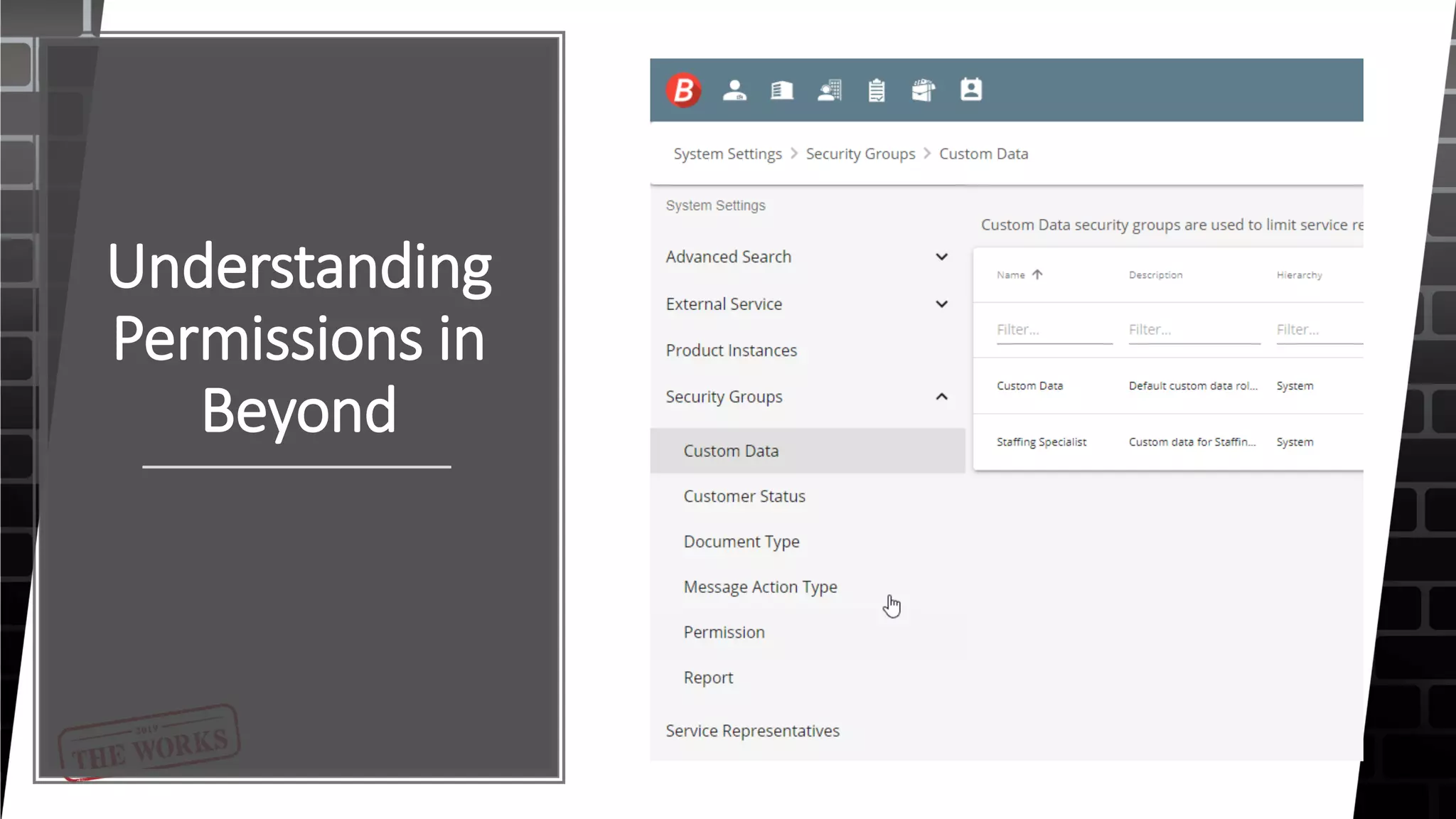
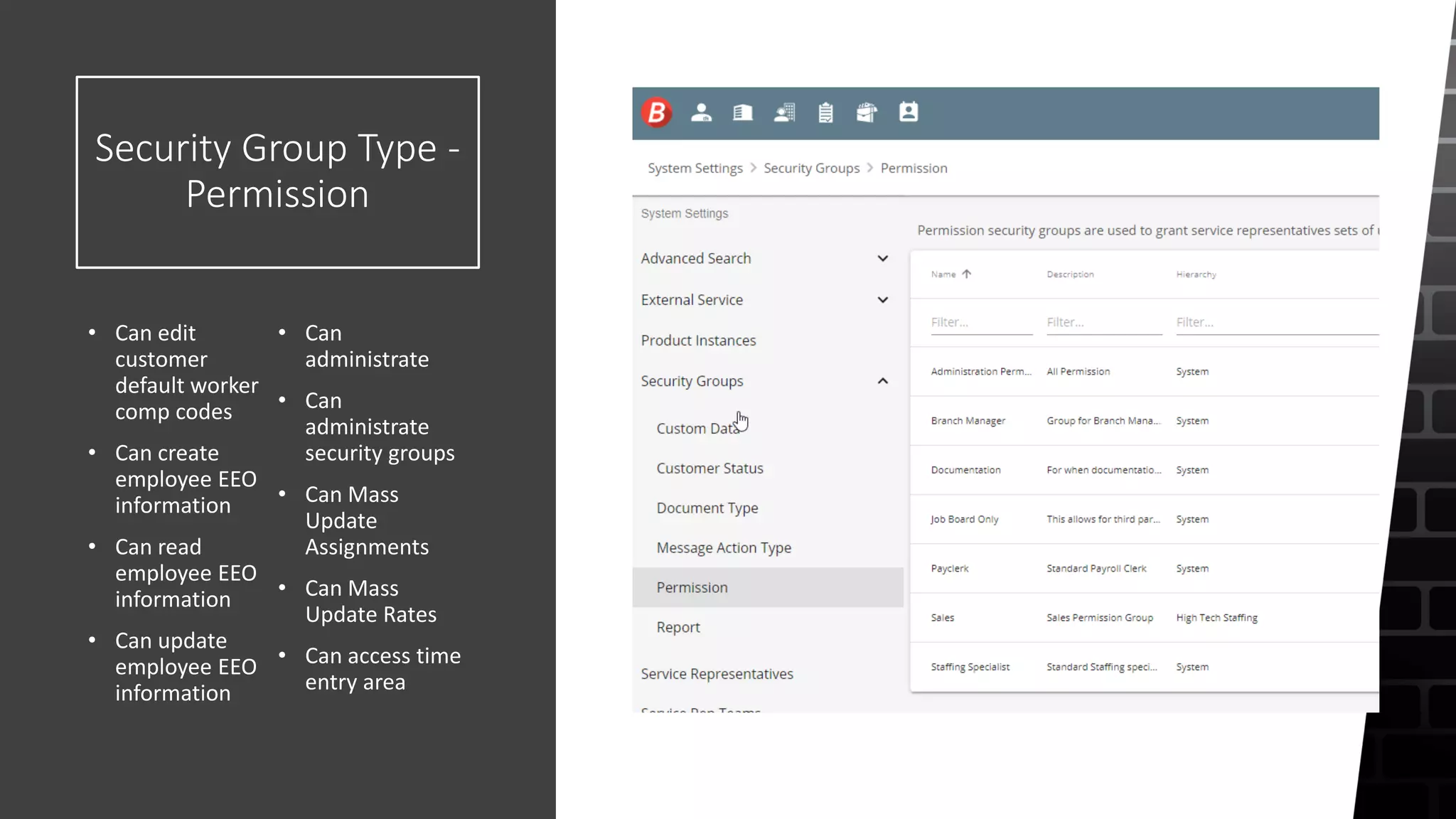
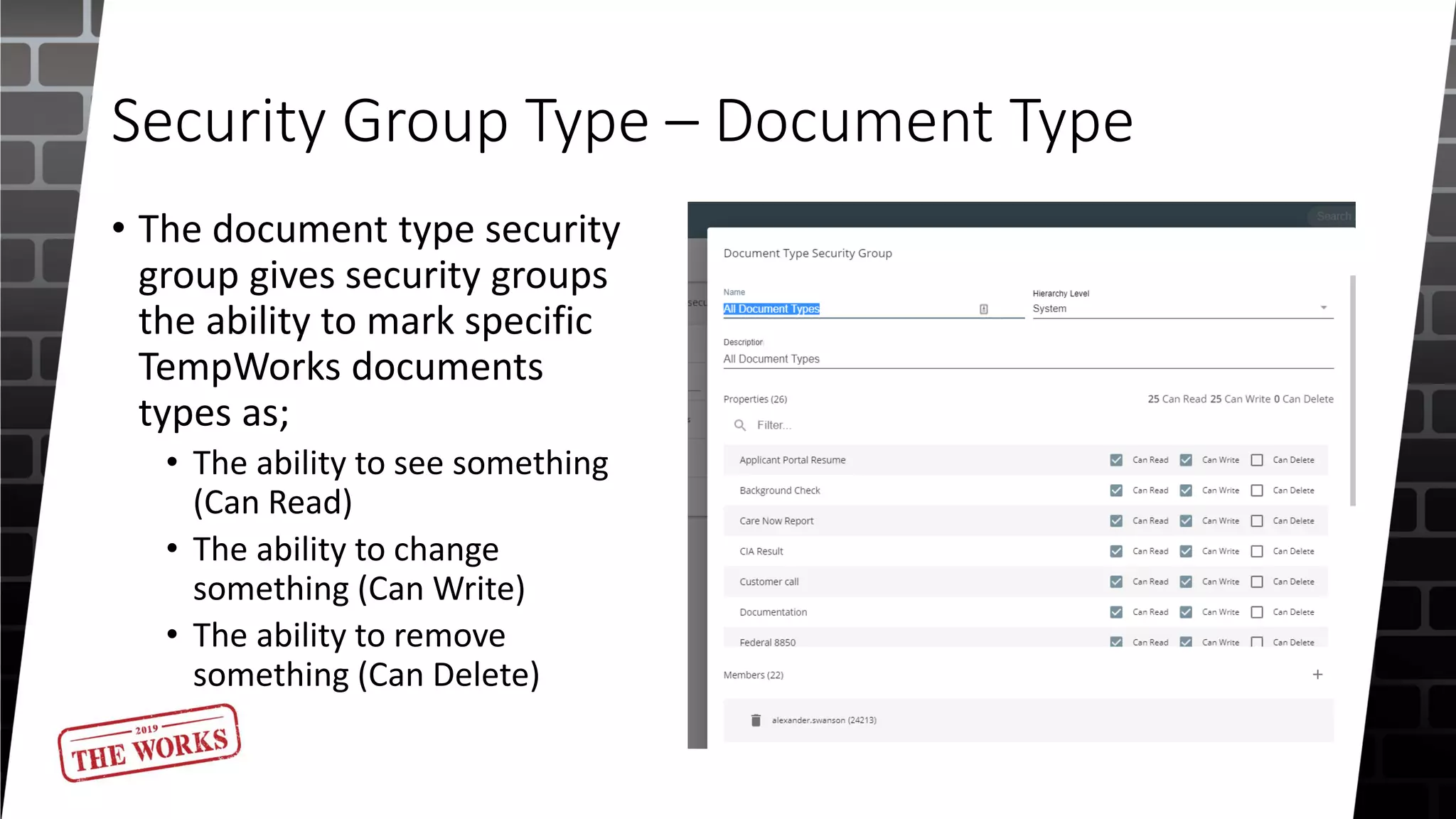
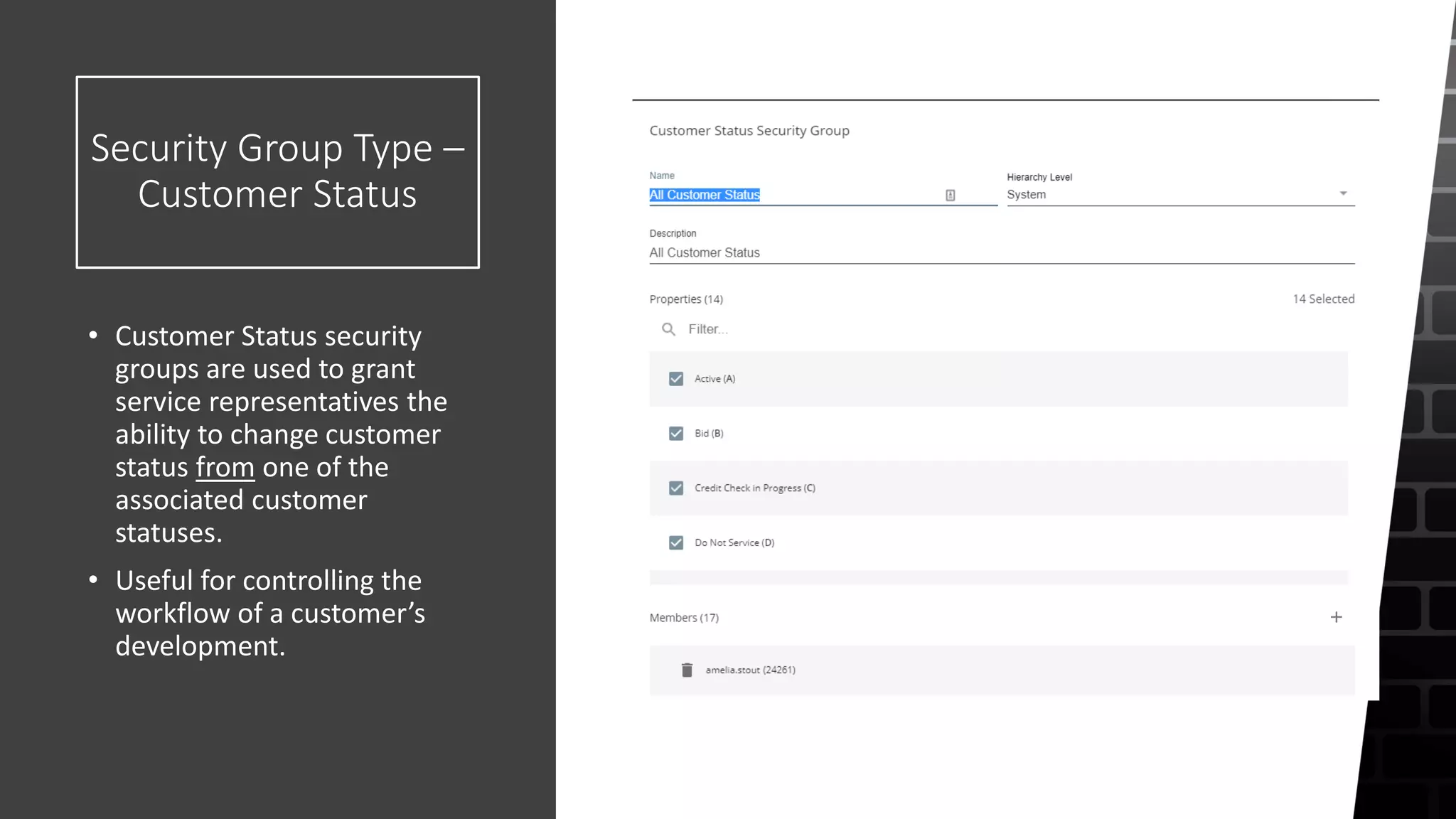
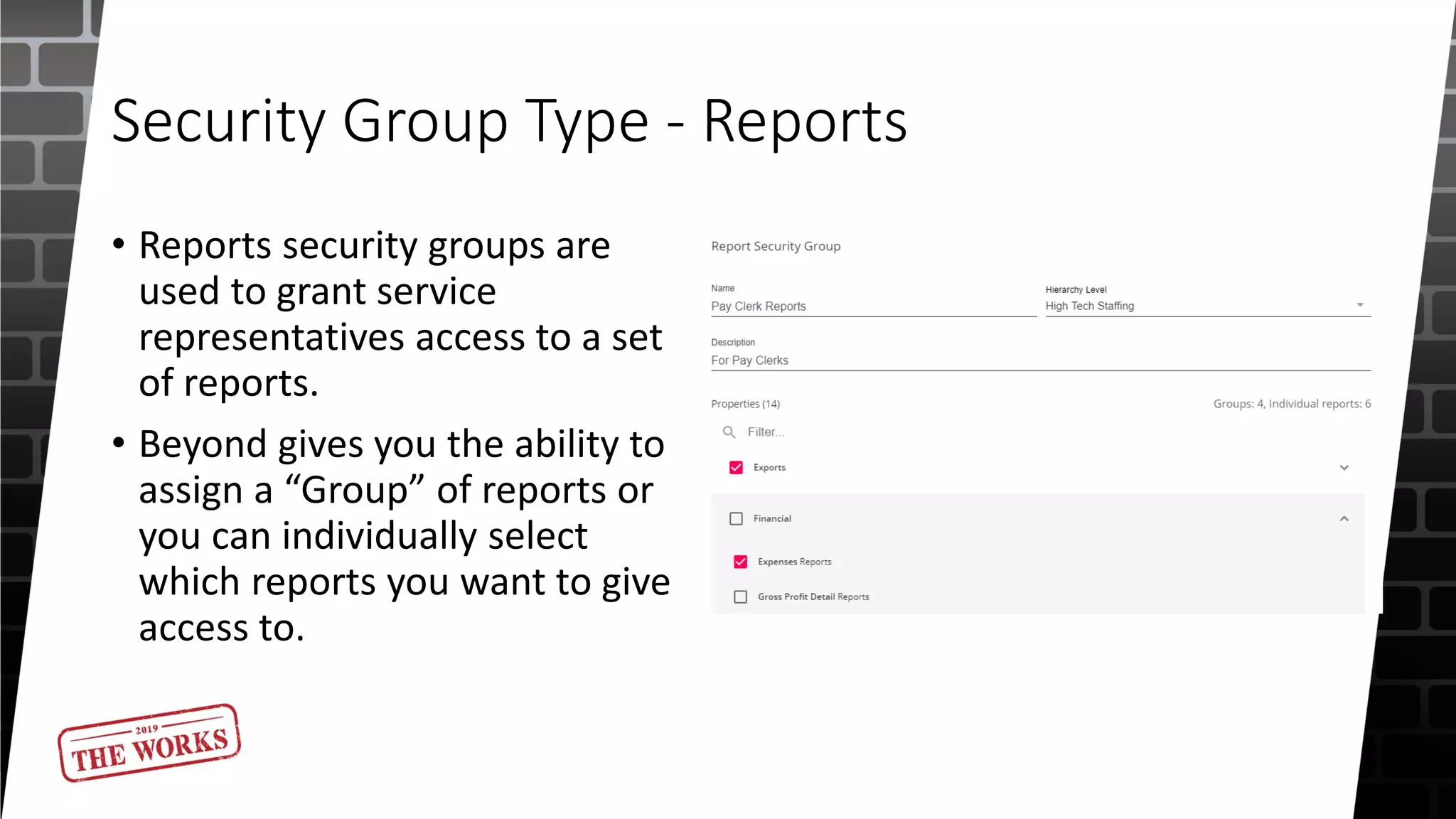
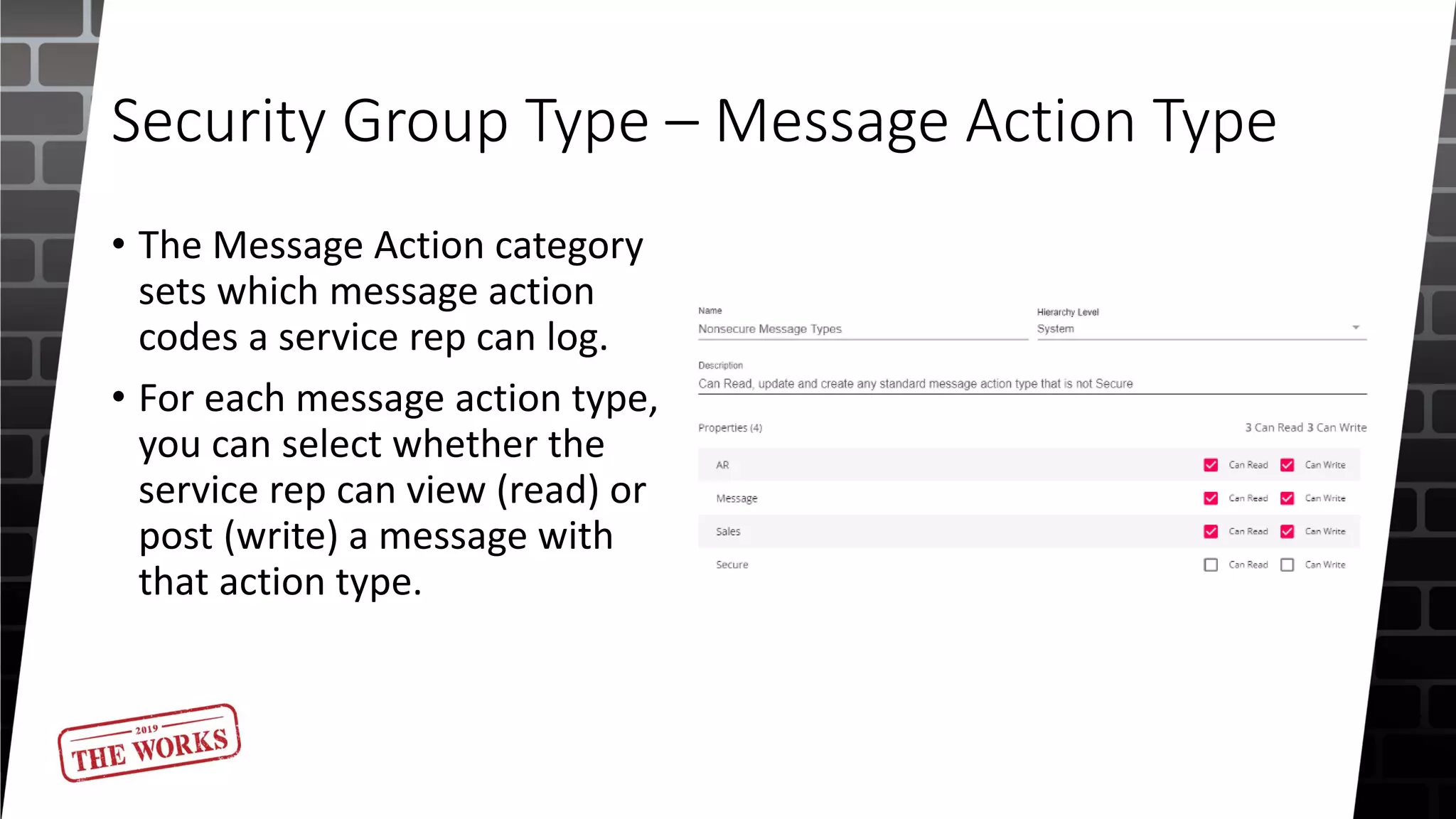
The document outlines the security roles and permissions within the Tempworks system, detailing specific access rights for various user roles regarding document types, reports, and customer statuses. It discusses challenges related to permissions administration and contrasts security groups with teams in terms of their functionality and reporting use. Additionally, it provides guidance for bridge admins and resources for better understanding and navigating security issues in the system.