The top 5 IT security skills SMBS need in 2017
•Download as PPTX, PDF•
0 likes•14 views
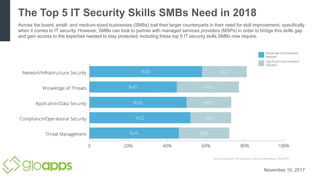
Small and medium-sized businesses lag larger companies in information technology security skills. However, SMBs can work with managed service providers to close this skills gap and obtain expertise in the top 5 IT security skills now needed, including partnering with outside experts.
Report
Share
Report
Share
Recommended
Case study: Managed Services for Network and Security Devices - Happiest Minds

Case study: Managed Services for Network and Security Devices - Happiest MindsHappiest Minds Technologies
Case Study: Risk Assessment & Security Strategy Definition - Happiest Minds

Case Study: Risk Assessment & Security Strategy Definition - Happiest MindsHappiest Minds Technologies
More Related Content
What's hot
Case study: Managed Services for Network and Security Devices - Happiest Minds

Case study: Managed Services for Network and Security Devices - Happiest MindsHappiest Minds Technologies
Case Study: Risk Assessment & Security Strategy Definition - Happiest Minds

Case Study: Risk Assessment & Security Strategy Definition - Happiest MindsHappiest Minds Technologies
What's hot (20)
2016 Scalar Security Study: The Cyber Security Readiness of Canadian Organiza...

2016 Scalar Security Study: The Cyber Security Readiness of Canadian Organiza...
Proactive Risk Management and Compliance in a World of Digital Disruption

Proactive Risk Management and Compliance in a World of Digital Disruption
"Show Me the Value: Enhancing the Perceived Value of Analytics Inside Your Or...

"Show Me the Value: Enhancing the Perceived Value of Analytics Inside Your Or...
Signs It's Time to Modernize Your Identity Management Software

Signs It's Time to Modernize Your Identity Management Software
Case study: Managed Services for Network and Security Devices - Happiest Minds

Case study: Managed Services for Network and Security Devices - Happiest Minds
Case Study: Risk Assessment & Security Strategy Definition - Happiest Minds

Case Study: Risk Assessment & Security Strategy Definition - Happiest Minds
Case study: Role Based Provisioning - Happiest Minds

Case study: Role Based Provisioning - Happiest Minds
More from Globizzcon
More from Globizzcon (10)
What is the financial impact of a ransomware attack?

What is the financial impact of a ransomware attack?
Are SMBS prepared to mitigate cybersecurity risks?

Are SMBS prepared to mitigate cybersecurity risks?
Are cybercriminals phishing for your sensitive business information

Are cybercriminals phishing for your sensitive business information
Information security SMBS need it, MSPS can provide it

Information security SMBS need it, MSPS can provide it
Recently uploaded
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...MyIntelliSource, Inc.
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...MyIntelliSource, Inc.
Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service

Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...

Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Recently uploaded (20)
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...
Automate your Kamailio Test Calls - Kamailio World 2024

Automate your Kamailio Test Calls - Kamailio World 2024
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...
Dealing with Cultural Dispersion — Stefano Lambiase — ICSE-SEIS 2024

Dealing with Cultural Dispersion — Stefano Lambiase — ICSE-SEIS 2024
BATTLEFIELD ORM: TIPS, TACTICS AND STRATEGIES FOR CONQUERING YOUR DATABASE

BATTLEFIELD ORM: TIPS, TACTICS AND STRATEGIES FOR CONQUERING YOUR DATABASE
Adobe Marketo Engage Deep Dives: Using Webhooks to Transfer Data

Adobe Marketo Engage Deep Dives: Using Webhooks to Transfer Data
Unveiling Design Patterns: A Visual Guide with UML Diagrams

Unveiling Design Patterns: A Visual Guide with UML Diagrams
Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide

Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide
Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service

Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service
Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...

Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...
software engineering Chapter 5 System modeling.pptx

software engineering Chapter 5 System modeling.pptx
The top 5 IT security skills SMBS need in 2017
- 1. The Top 5 IT Security Skills SMBs Need in 2018 Across the board, small- and medium-sized businesses (SMBs) trail their larger counterparts in their need for skill improvement, specifically when it comes to IT security. However, SMBs can look to partner with managed services providers (MSPs) in order to bridge this skills gap and gain access to the expertise needed to stay protected, including these top 5 IT security skills SMBs now require. November 10, 2017
