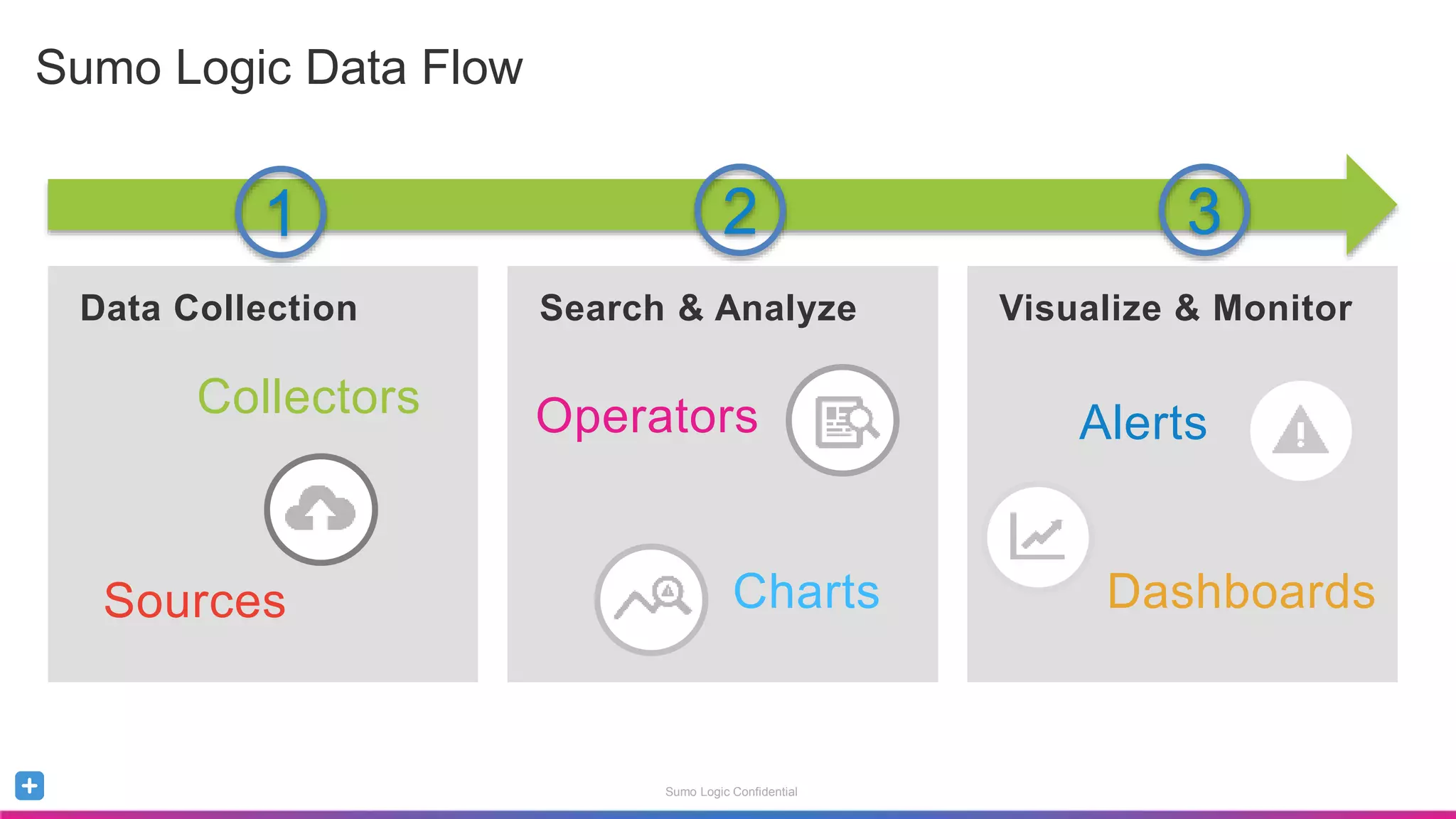
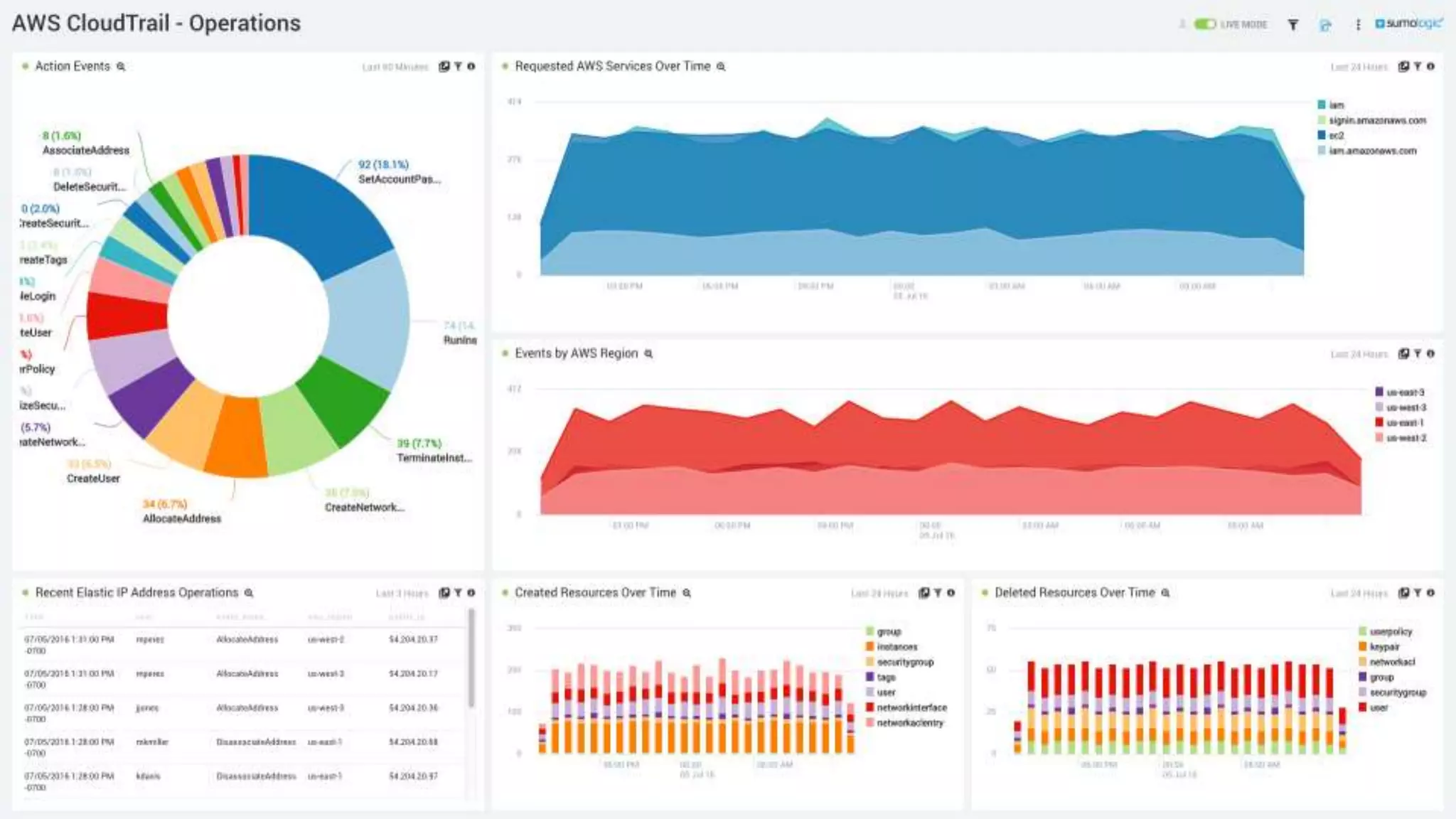
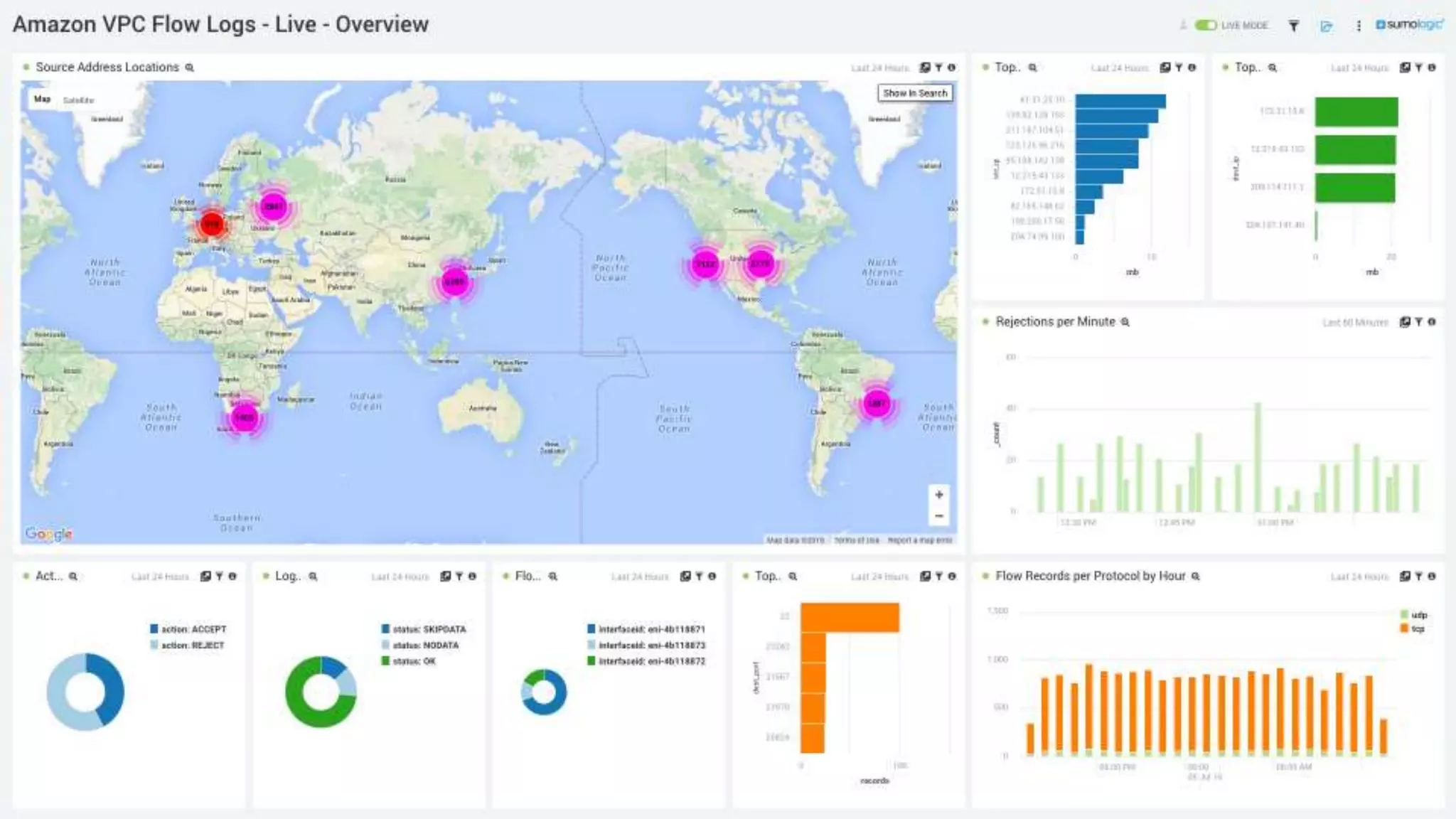
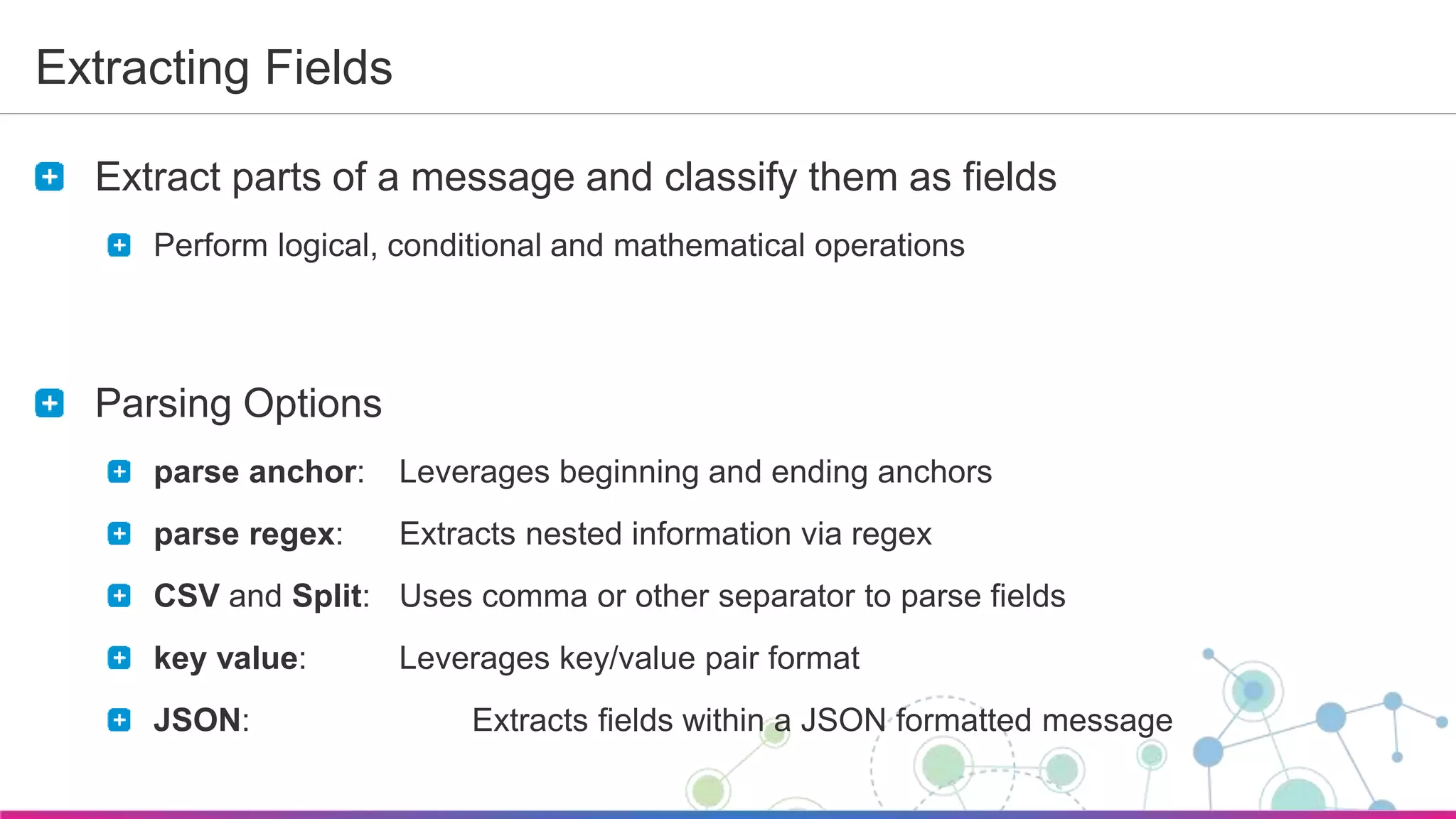
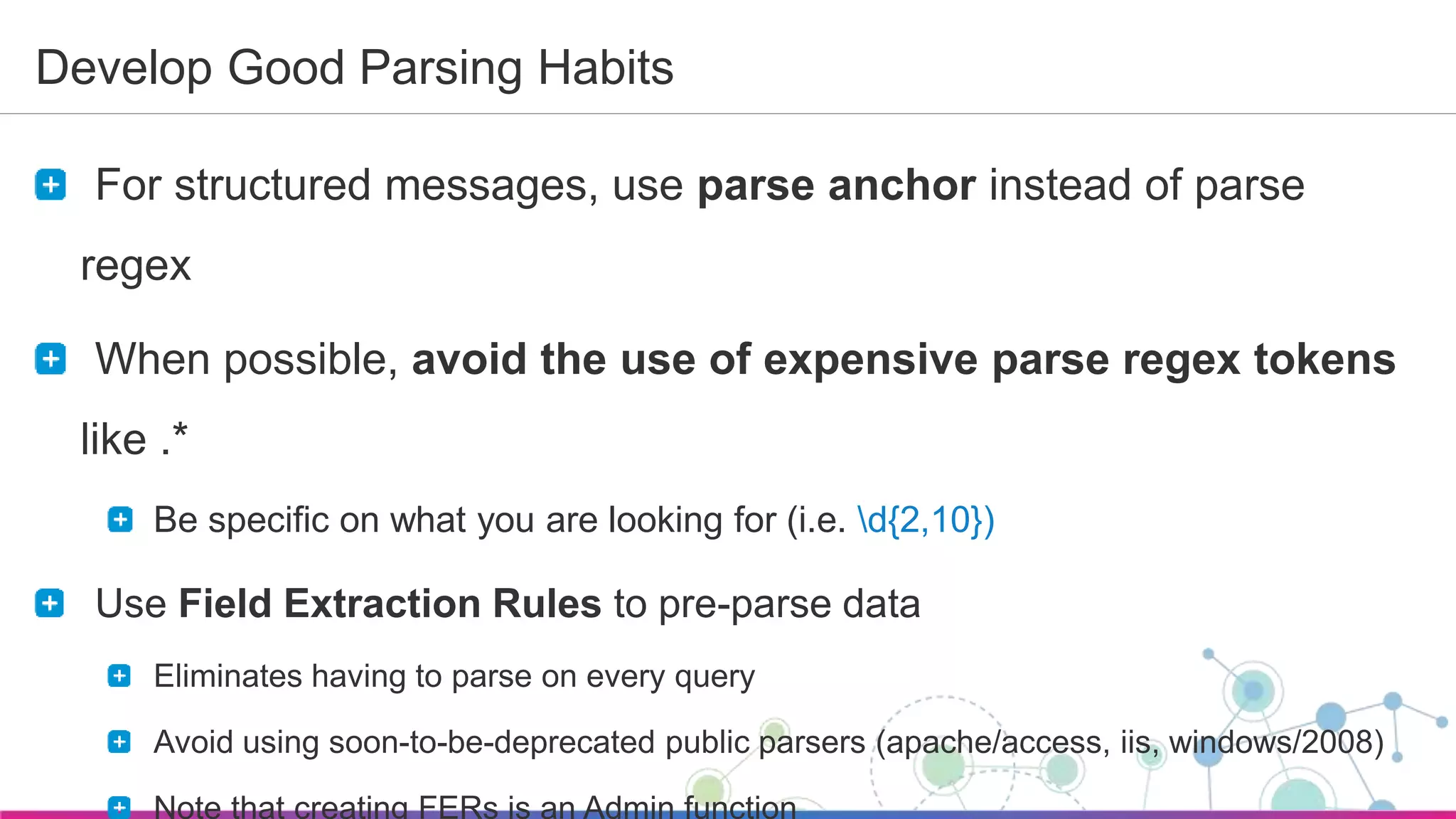
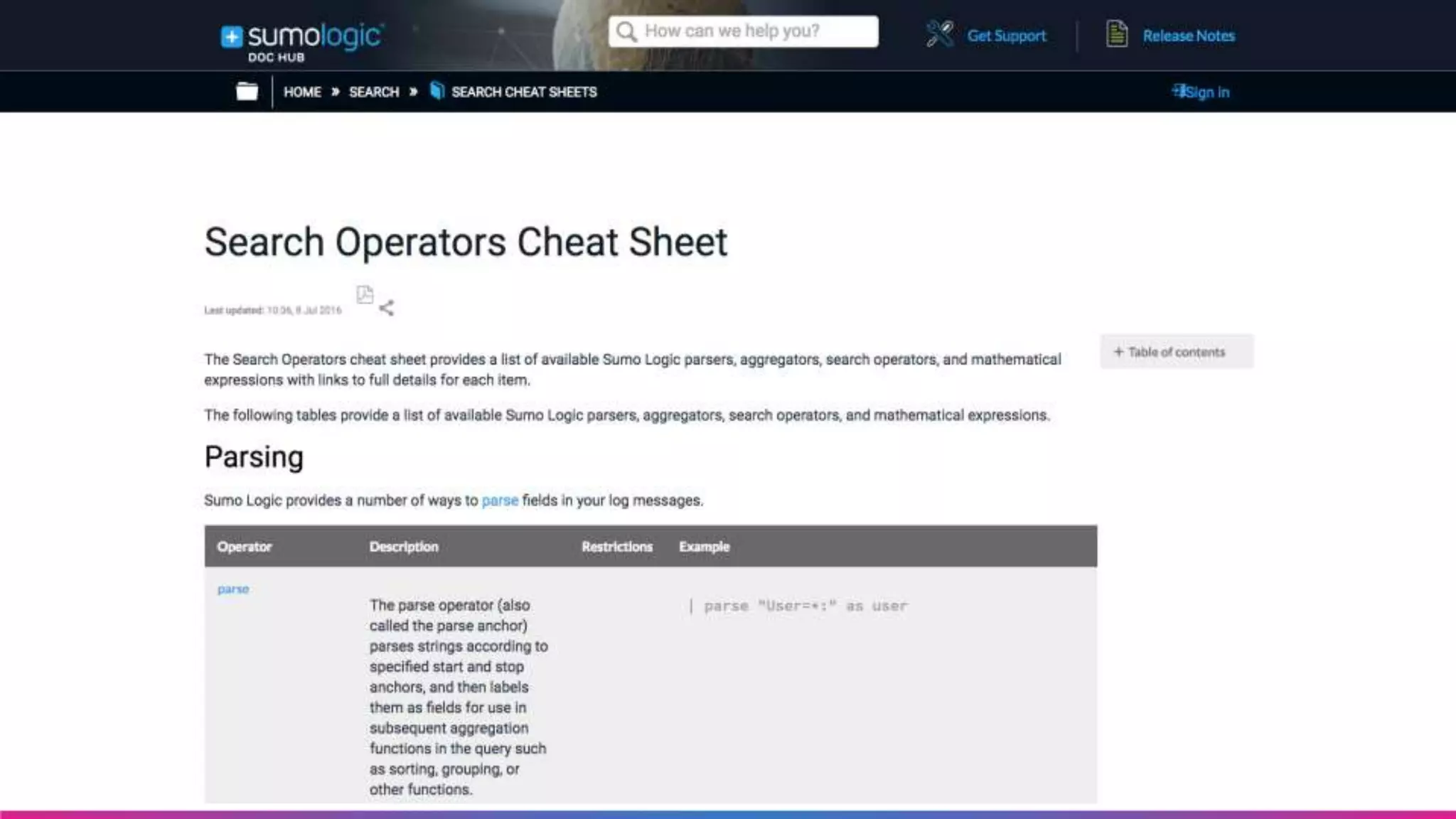
The document is a guide for a Sumo Logic webinar focused on advanced analytics and query usage. It covers key topics such as constructing queries, data collection, and visualization techniques, while also providing tips for parsing data and utilizing operators efficiently. The content emphasizes the importance of utilizing existing resources like query templates and metadata to enhance the analysis and monitoring of log data.




![Sumo Logic Confidential
JOIN Operator Example
_sourceCategory=prod/api/webhooks and "webhook-worker"
| join
(parse regex "INFO (?<id>.*) Send HTTP request with (?<bytes>.*) byte message body to (?<url>.*)") as
info,
(parse regex "INFO (?<id>.*) [FAILURE] (?<message>.*)") as failure
on info.id = failure.id
| fields info_id, info_url, failure_message, info__messagetime
| where info_url = "<insert_webhook_url_here>"
| formatDate(fromMillis(info__messagetime), "MM-dd-yyyy HH:mm:ss") as myDate](https://image.slidesharecdn.com/howtowebinaradvanalytics-160725203948/75/Sumo-Logic-How-to-Webinar-Advanced-Analytics-22-2048.jpg)