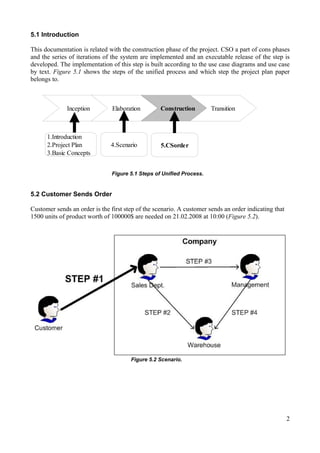
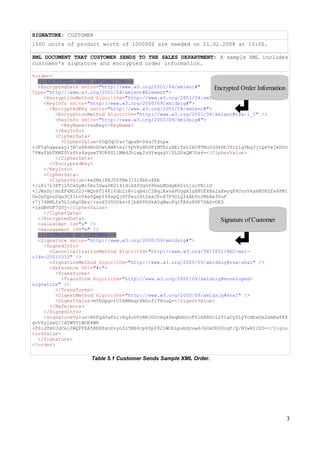
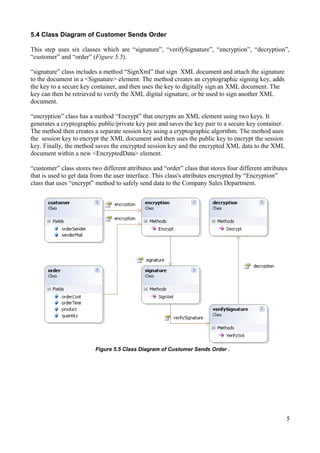
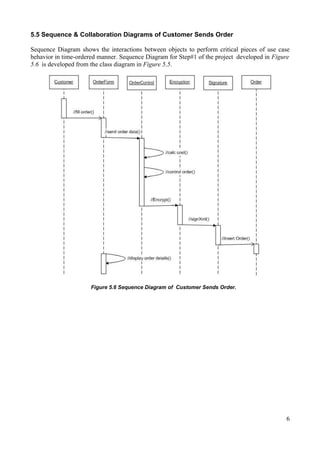
This document summarizes the first step of an e-commerce project which involves a customer sending an order. It includes:
1) Developing an application that allows a customer to send an XML order document to a company's sales department. The order information is encrypted and the document is digitally signed.
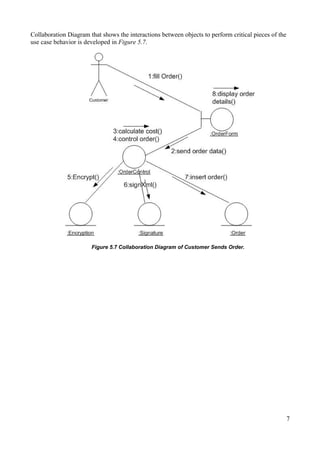
2) Class, sequence, and collaboration diagrams illustrate the interactions between classes like "Customer", "Order", "Encryption" and "Signature" to encrypt order data and sign the XML document before sending.
3) A sample XML order document with encrypted order information and the customer's digital signature.
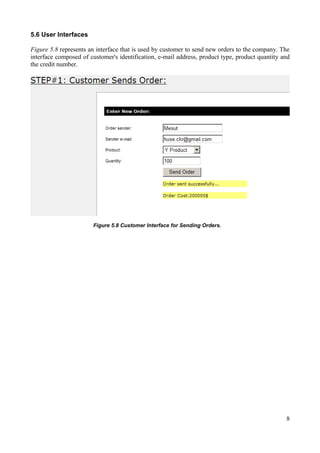
4) User interface screenshots of the web form a customer would use to enter order details.