Embed presentation
Downloaded 220 times



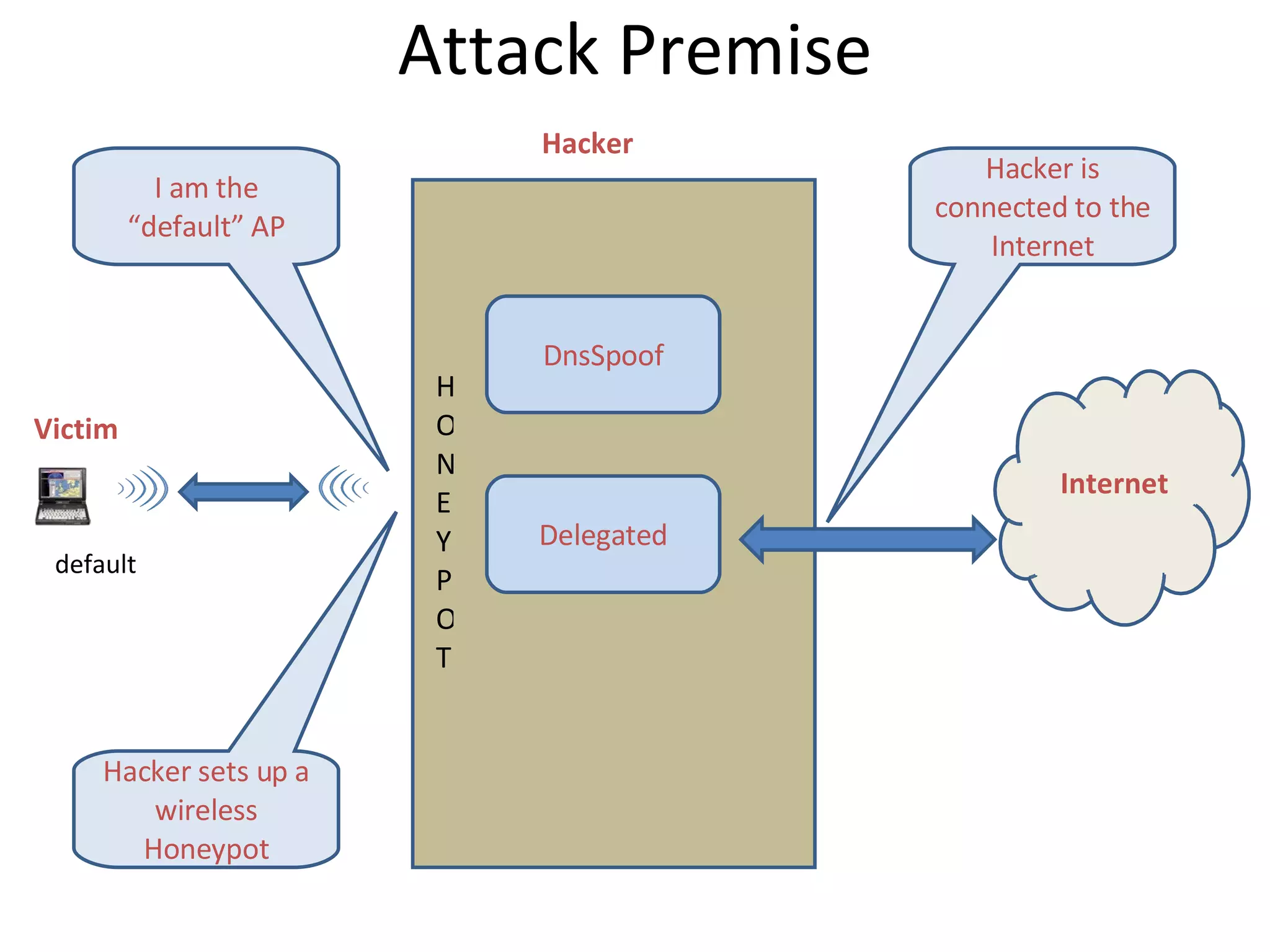
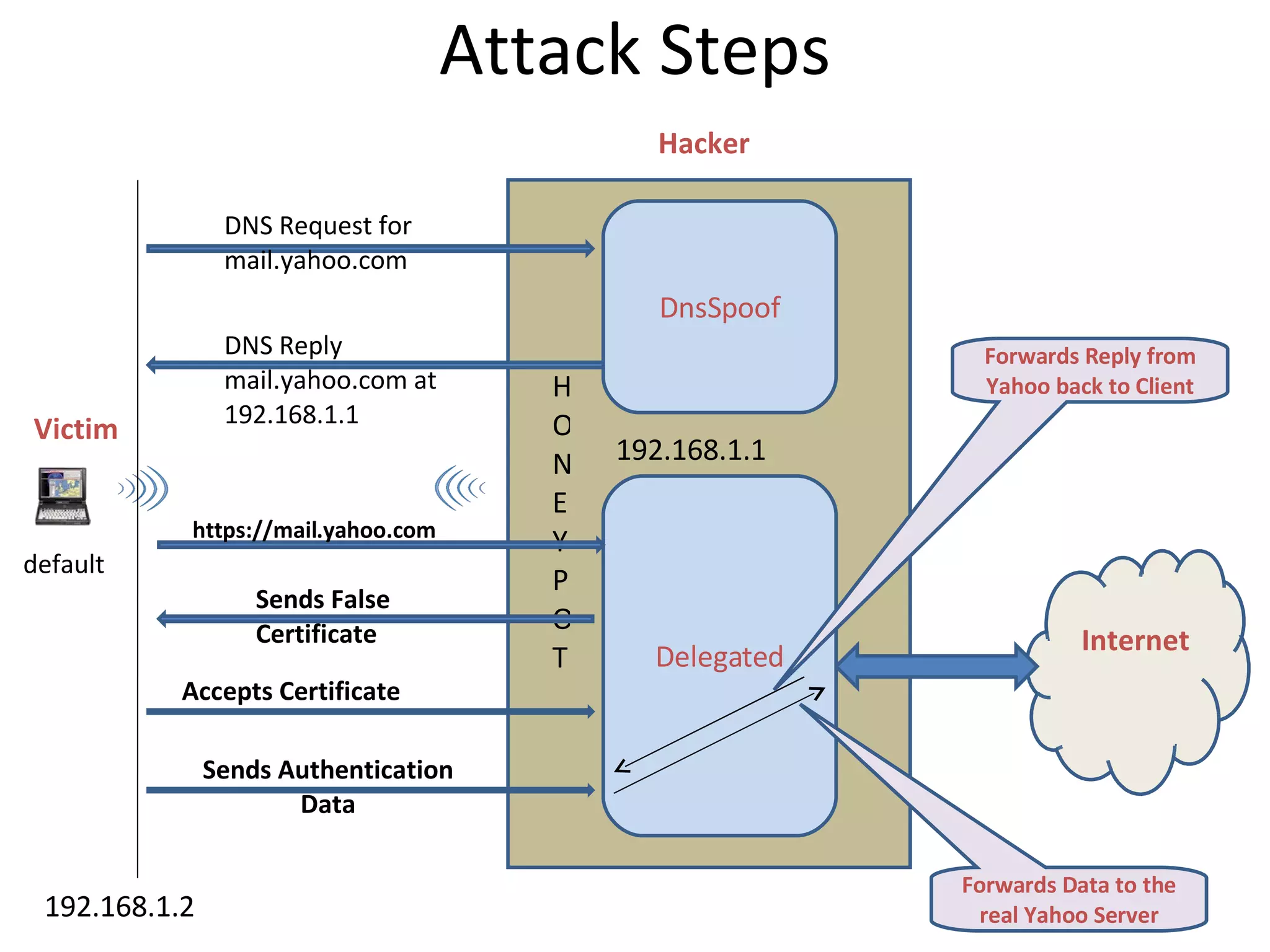
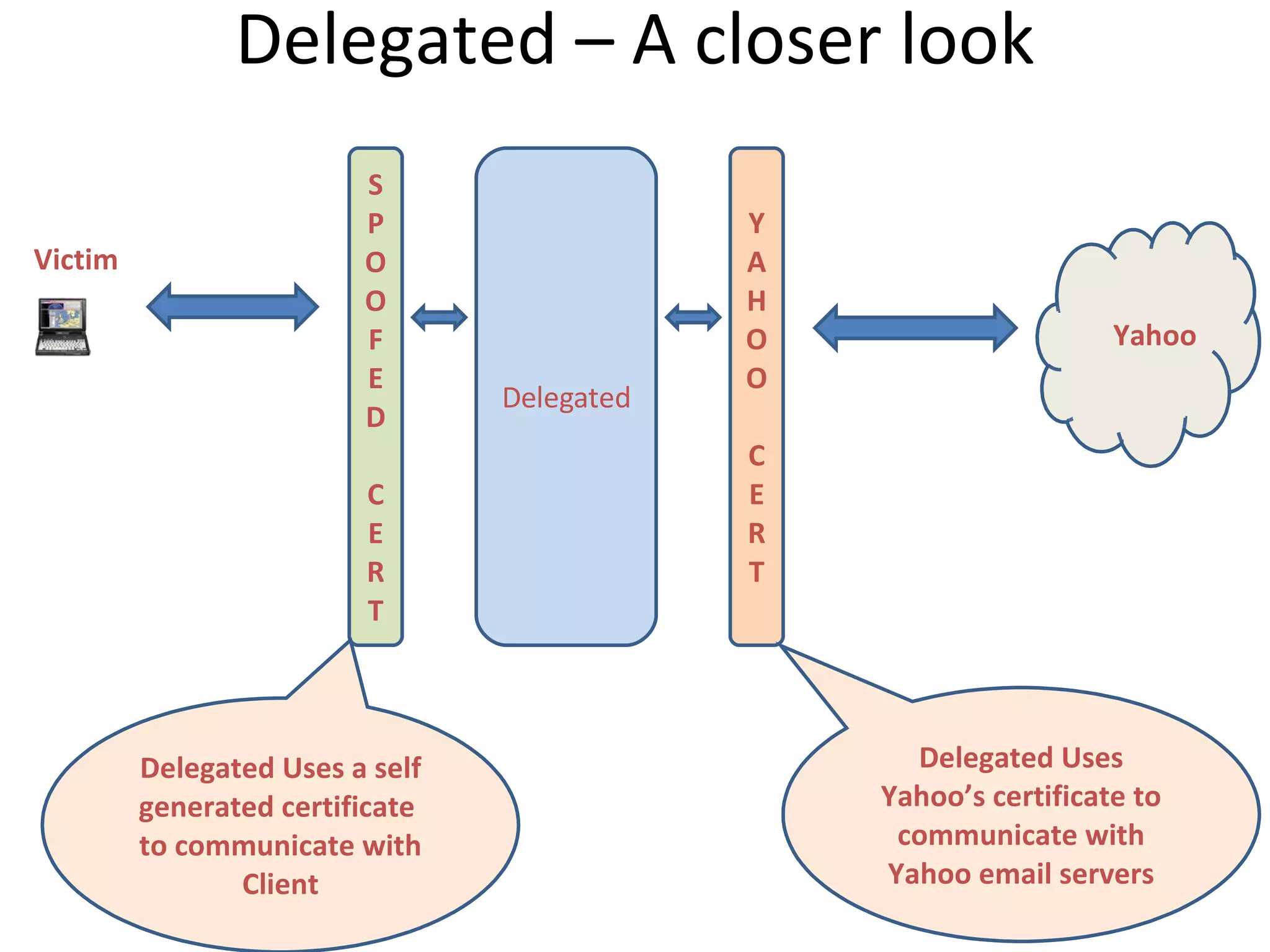

The document discusses a man-in-the-middle attack over a wireless network. It describes how a hacker can intercept traffic between a victim and the host they are communicating with by placing themselves in the middle. The hacker sets up a rogue wireless access point and uses tools like DNS spoofing and a delegated proxy server to redirect traffic and perform an SSL man-in-the-middle attack by presenting a fake certificate to the victim. A demonstration of this attack will be shown from the victim's perspective in the next video.






