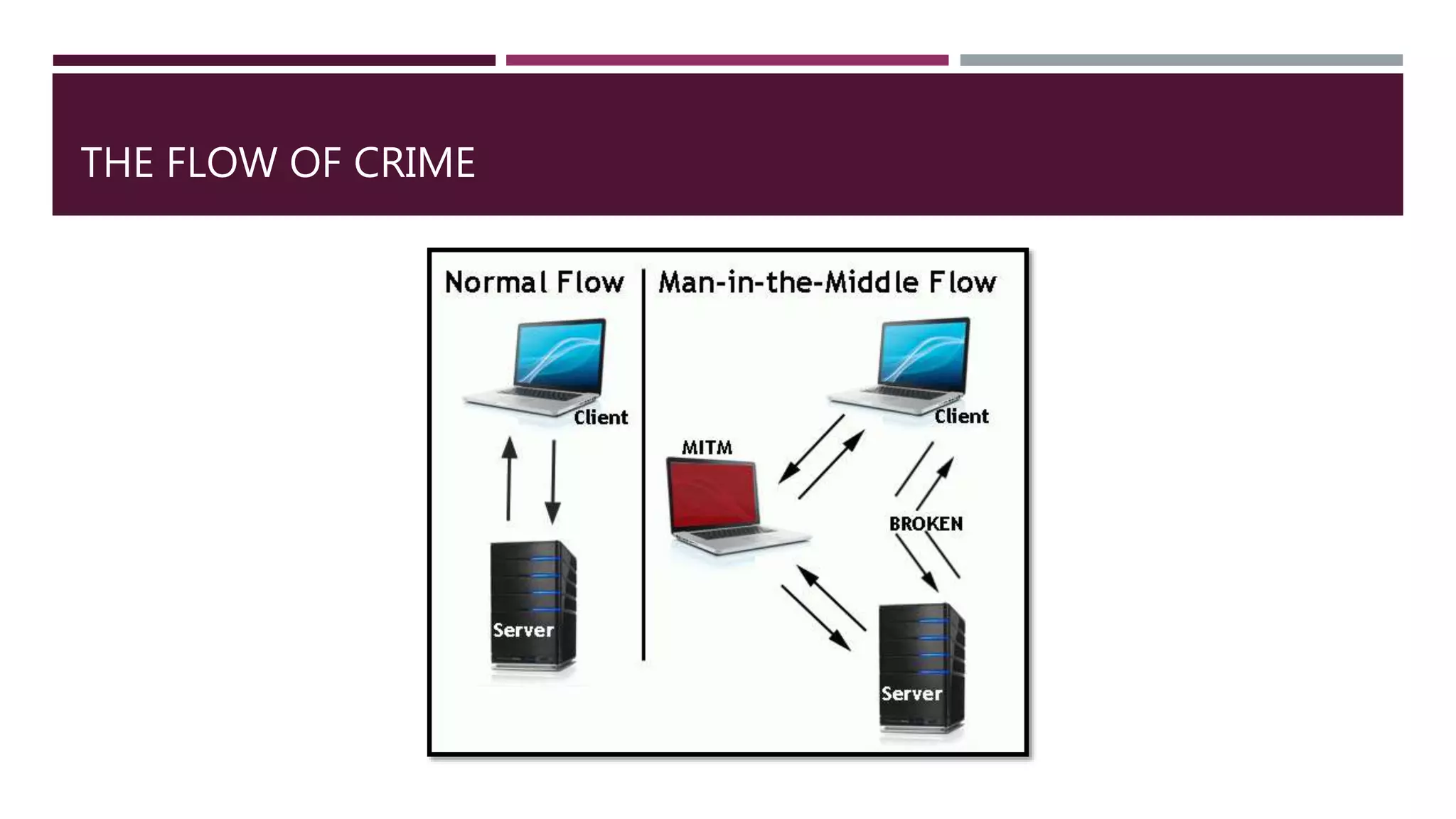
A man-in-the-middle attack is where an attacker secretly relays communications between two parties who believe they are directly communicating, allowing the attacker to intercept and potentially alter these communications. There are two main types - one using physical proximity to intercept wireless communications, and one using malware to intercept communications. Some common man-in-the-middle attack techniques aim to spoof IP addresses, DNS information, HTTPS secure connections, SSL encryption, email sender addresses, or eavesdrop on Wi-Fi networks to intercept user communications and credentials.