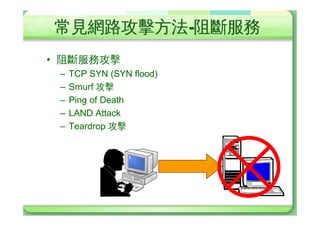
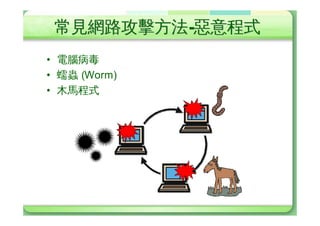
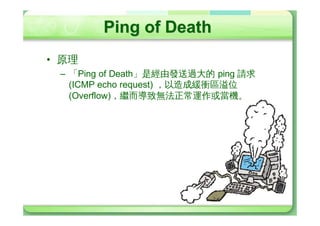
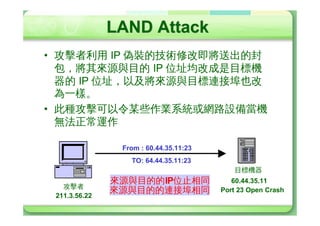
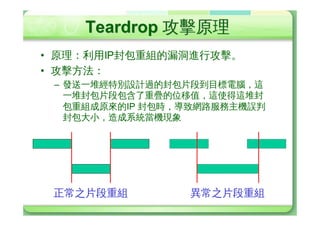
The document discusses various types of cyber attacks including denial of service attacks, man-in-the-middle attacks, password cracking attacks, and social engineering attacks. Specific attack methods covered include TCP SYN floods, Smurf attacks, password brute force, and dictionary attacks. Defense strategies proposed include ingress filtering, disk quotas, firewalls, and intrusion detection systems.




![c)¸Øóè-ô̸Ø
• ô̸Ø8]§kæÁæéз뙆
ý¿ÐL·
• lYô̸Ø,
– ý (Masquerade)
– g(Replay)
– ù·(Message Modification)
– œ(Denial of Service)](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-7-320.jpg)
![c)¸Øóè-—̸Ø
• —̸Ø8]§k(¢,)_{Ã*Y
À_Æd (J(JÁI«™†·f
• lY—̸Ø,
– ÿÓ(Eavesdropping)
– ·Ã±(Traffic Analysis)](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-8-320.jpg)





![±s̜ٸØ
• ±s̜ٸØH‰DDoS
– ®±sY¸ØÙÌdL¥c)jDï
DoS¸ØYôÚÛï¸Ød¯õÛœ«
*[}Ž
t]ç¸ØYfzd¿ÓÁÙ
ûU#7d ¬çÌ,Mld6f](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-17-320.jpg)
![DDoS ¸Øj¡
]§(1Ç
DaemonûÌ client
daemon
¸Øk
client daemon
daemon
a”ôÚ
daemon
client ICMP
Echoreply
Packets
daemon
Internet ôÚ](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-18-320.jpg)





![døÜ8U”¥#ÐJfzJ
broadcastY
• Ä Ä#æ
e]§»Ð]§k#ûU
• ¼?ãX(Disk Quota)](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-27-320.jpg)




![Ýõû̱
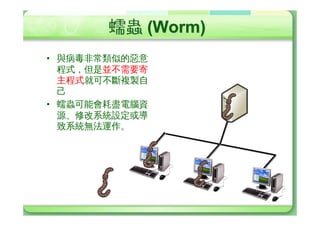
• ÝõûÌ8U
– ûU—]§J¡”]
– F4k£YØ%
– B8)”üYûÌeÄ —·@YûÌ
– —c)@%
Q
• Ýõóè
– ÃLÇ›è/Nxè/ŸµÏ}è/WÁÂÔè/FTPè
• ôÂgÙÌ
– e‰qæéh1/À@*8ûUÐÐûÌ
®Ã—G”
• ôfY
– ›SôÚeØÿ_e*¸Øe#7c)](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-33-320.jpg)





![¹ÞÚ®Ya#
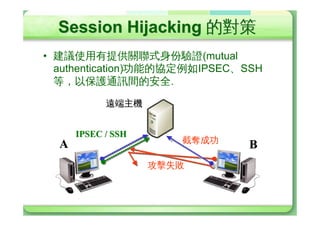
• Session Hijacking•ÖH‰˜¹ÞÚ® ™
• ¸Øa#j
– …]§k¯4kî]ôÚ(Ó…½©dC
†¹ÞÚ®d+¥,4k'ôÚœY¹Þ•Ùd
]§kYeØ_þ¥,4k~ÃLôÚ†¹d
]§kÀ_4a¥,4kÔÞÞÆÀ_Y
‚Uf
• Kra”õ1998Ë11ÜÜ3YHuntd ”Þ
“daemon9”Ü3Yjuggernautdid6Session
Hijacking](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-42-320.jpg)





![Ô¸Ø (Replay Attack)
• a#j
– ¸ØkõÿÓc)d_(¾}Y·ÃPÙÂÔ
Y¯ÇÃd˜© Ôµ…¯ÇÃøÿ½TH
$Þ–LY4kdø:QÀ_ûUY]§f
Yf
• Áj
– –L£›®0õÞÖÛœS
– ®ÆP£ÇYÄŒÌX›](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-48-320.jpg)

![àP (Buffer Overflow)
• £¯ûÌ•Ô
SY¾³ï
Í7:
#include stdio.h
ìt@4Ô
#include string.h
ˆ#YØŽÛd void func(char *p)
func(char
16¿ÓÔWY {
char buffer1[10];
buffer1[10];
àPYK strcpy(buffer1,
strcpy(buffer1, p);
1f printf(buffer1);
printf(buffer1); }
Int main (int argc, char *argv[])
main(int argc, *argv [])
{
func(
func(“I am the law in the network”);
network”
return 0; }](https://image.slidesharecdn.com/random-110331094020-phpapp01/85/slide-50-320.jpg)


