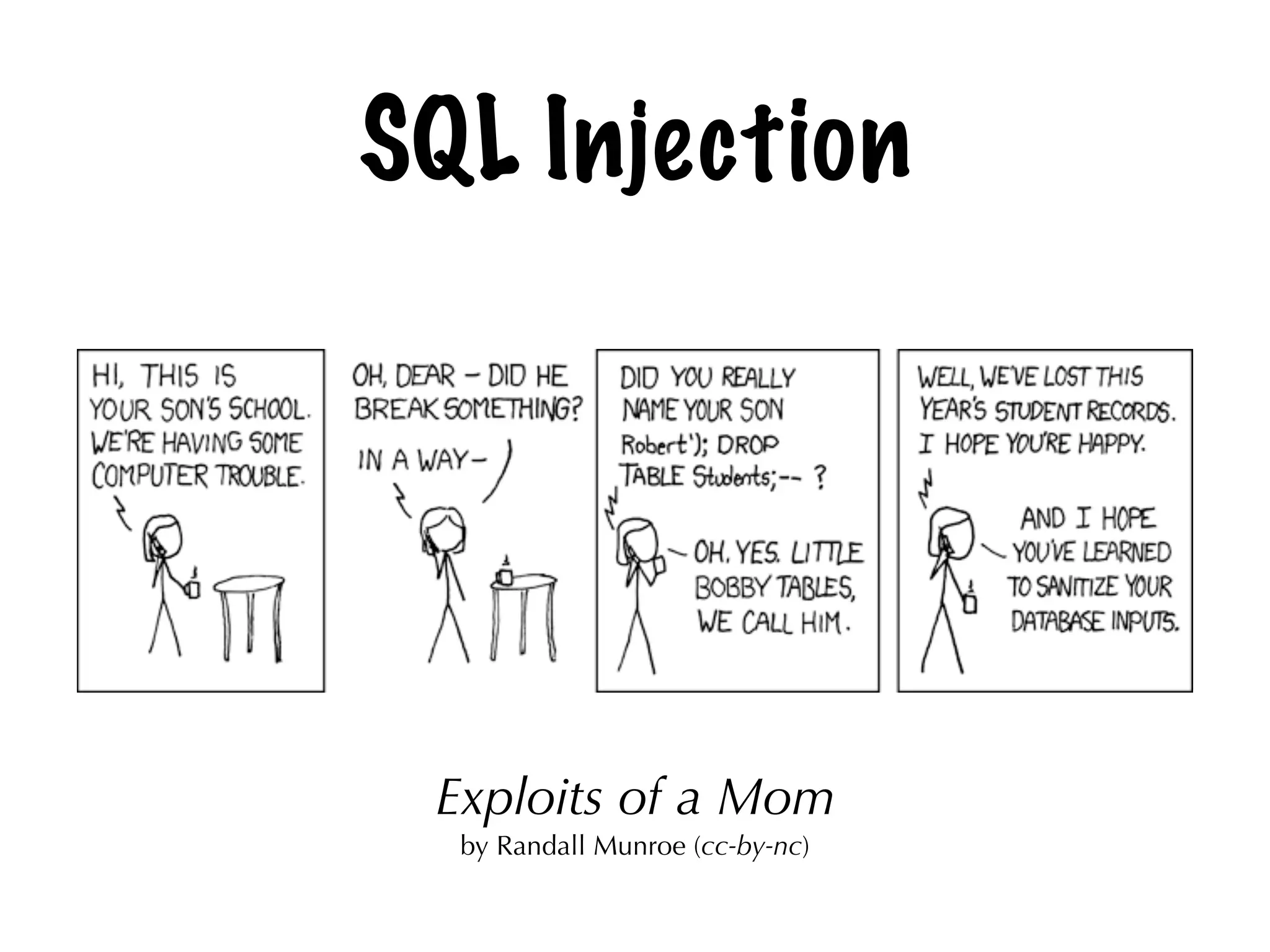
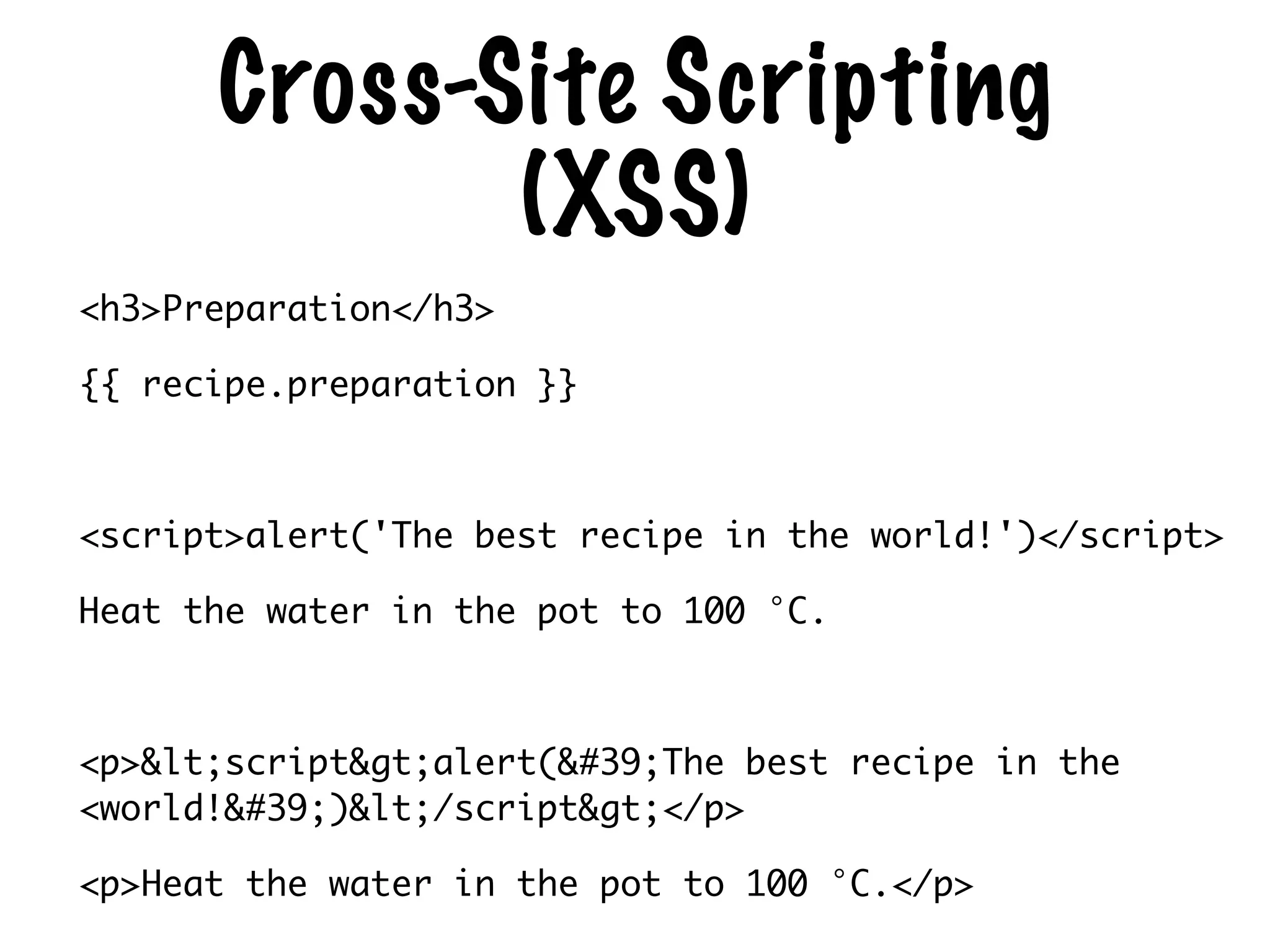
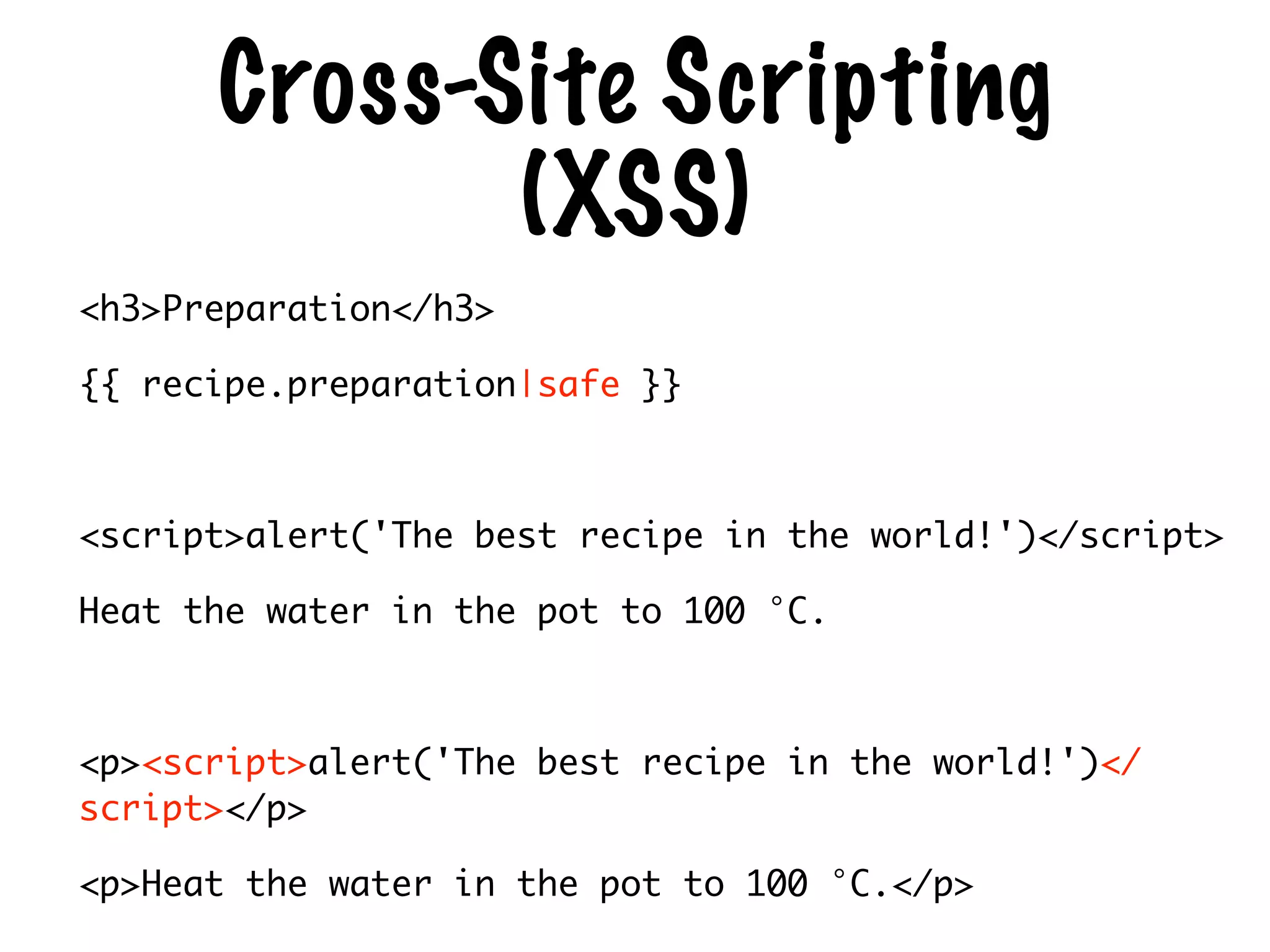
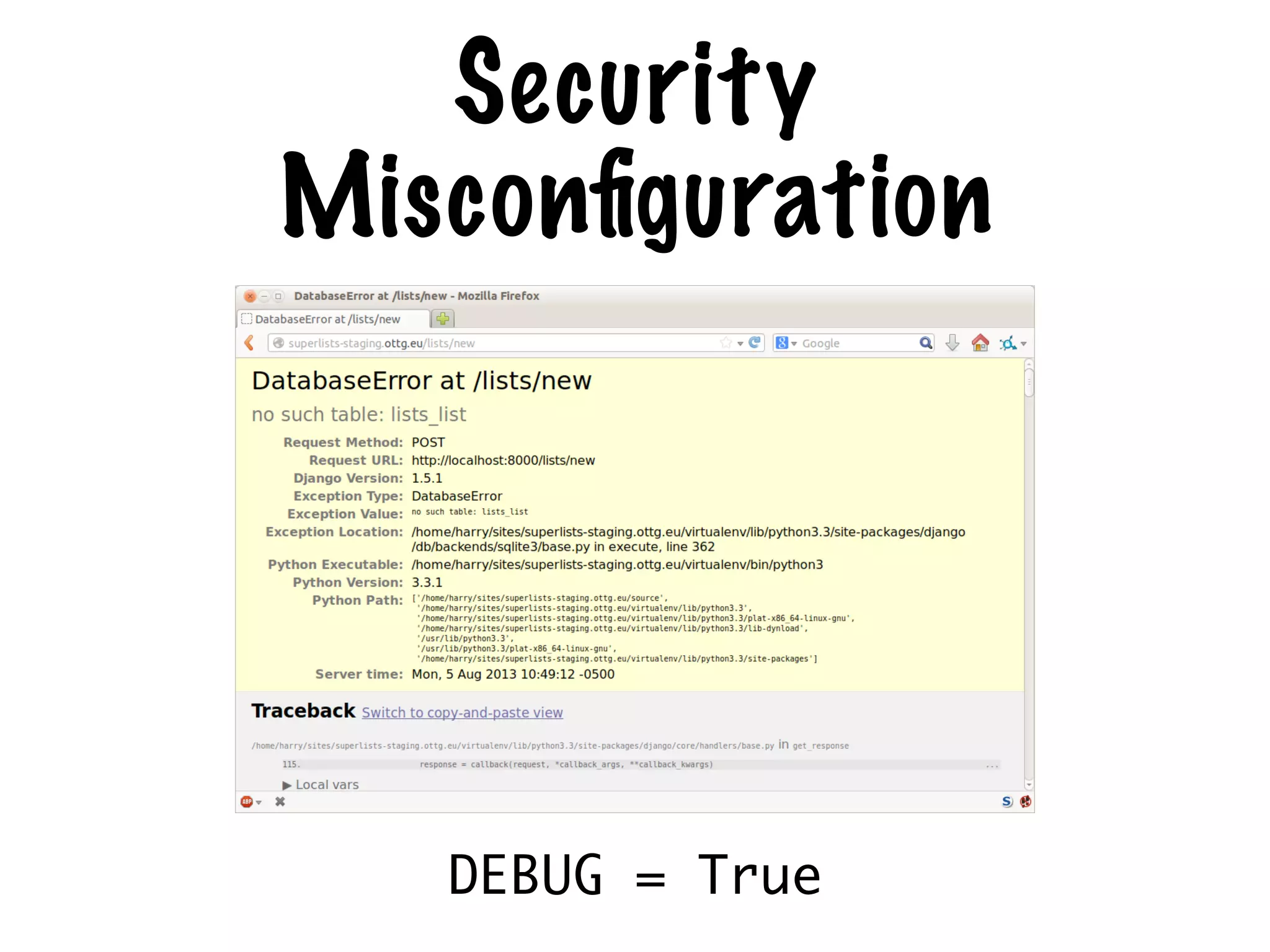
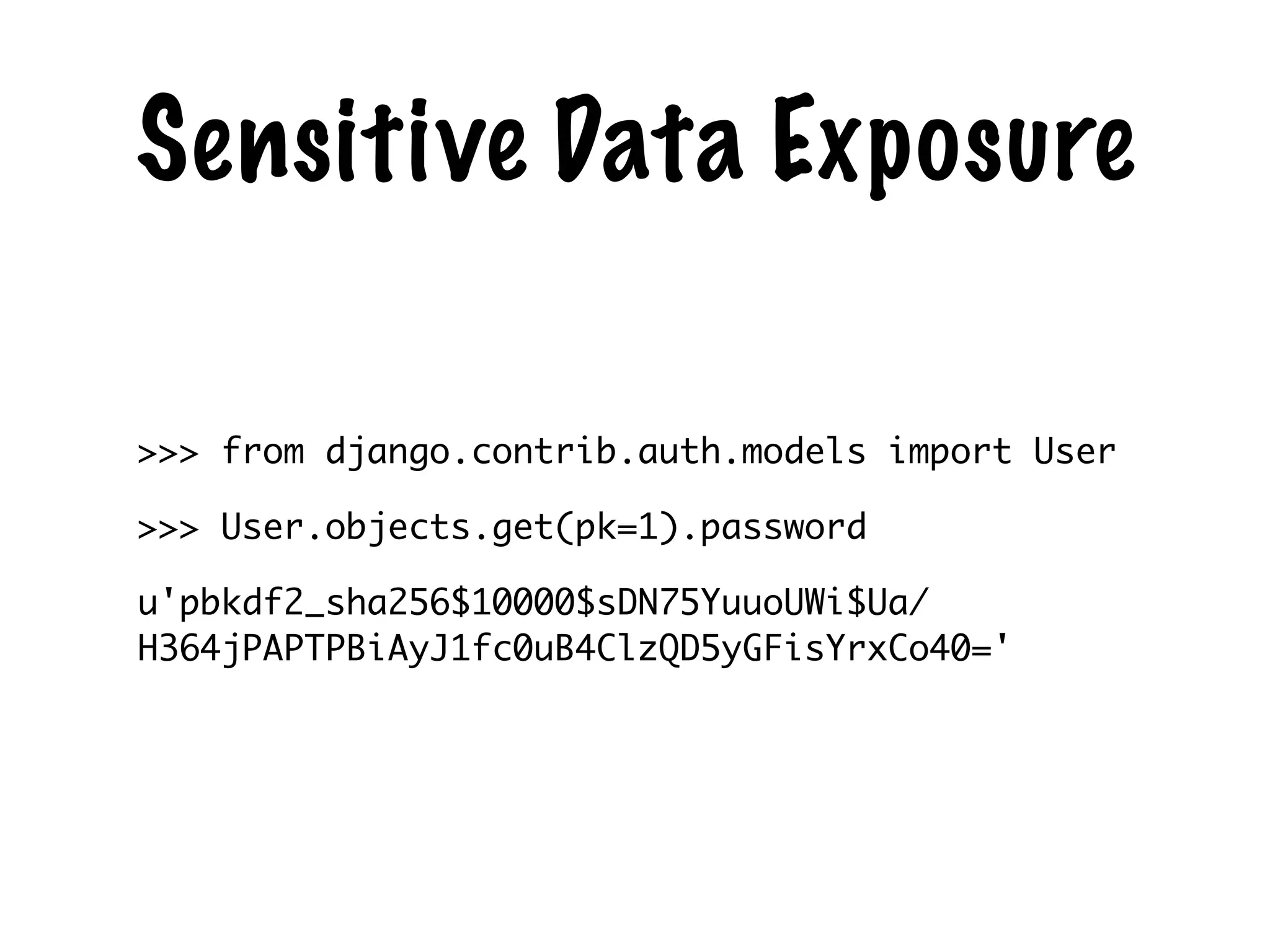
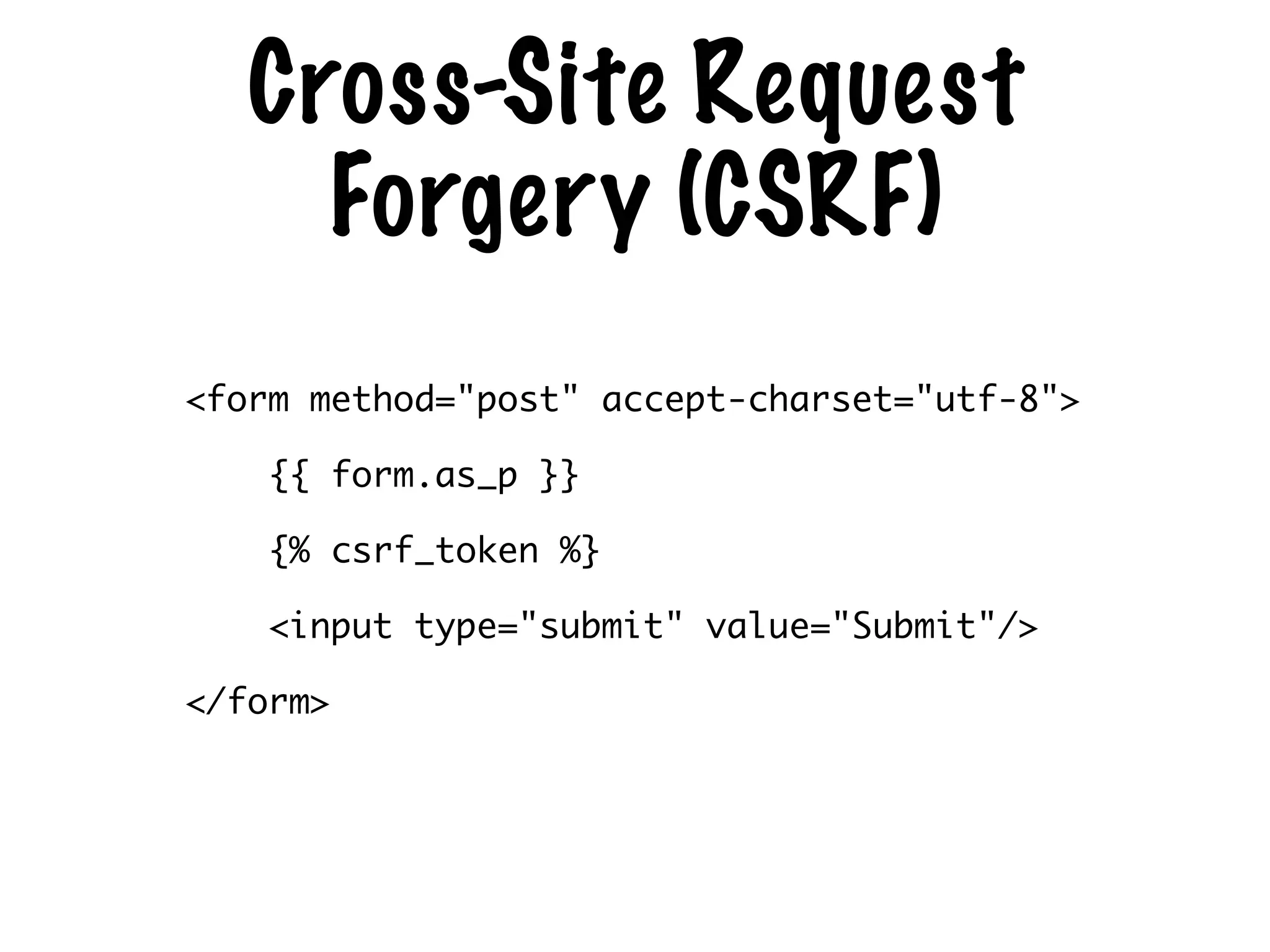
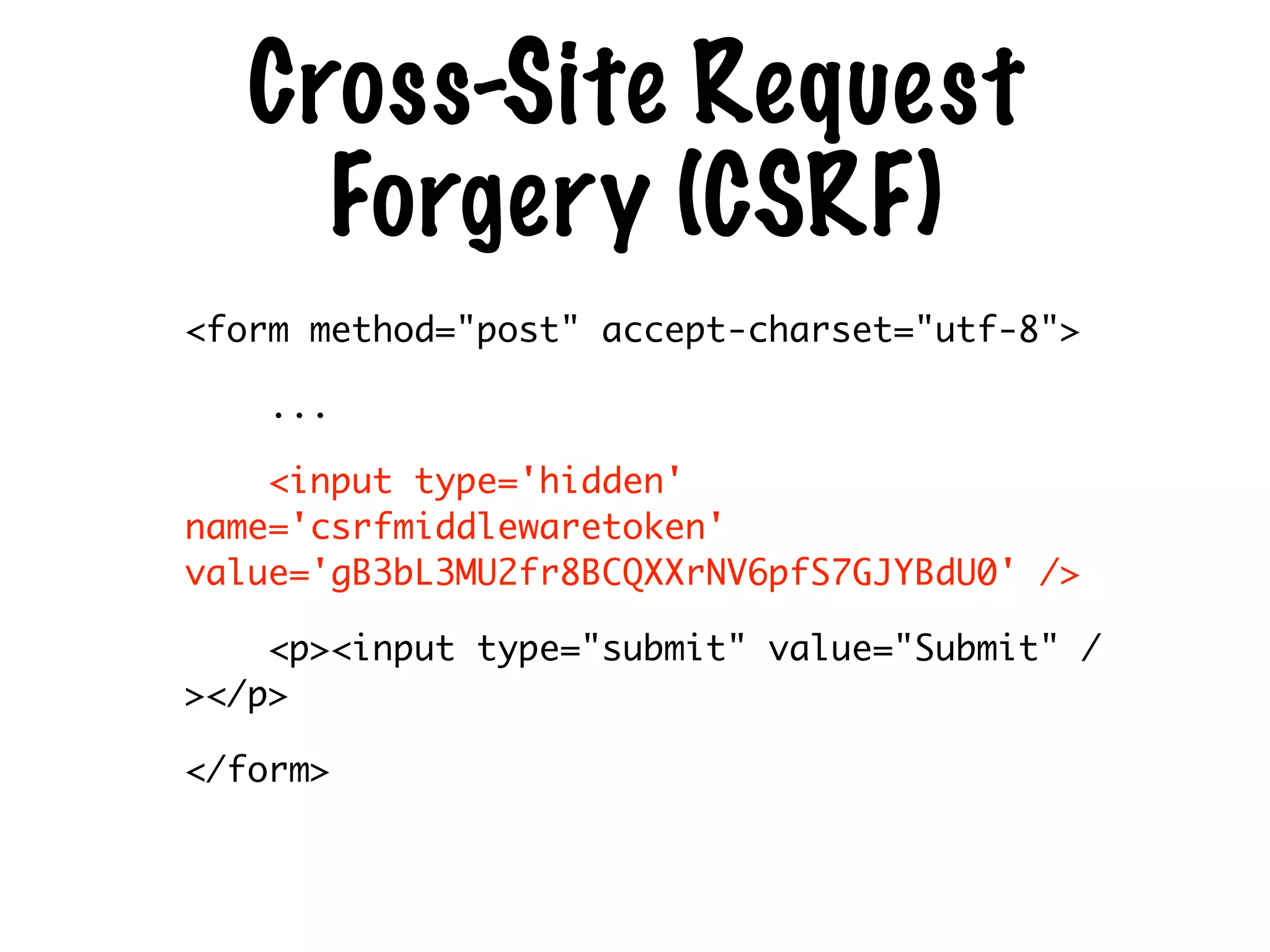
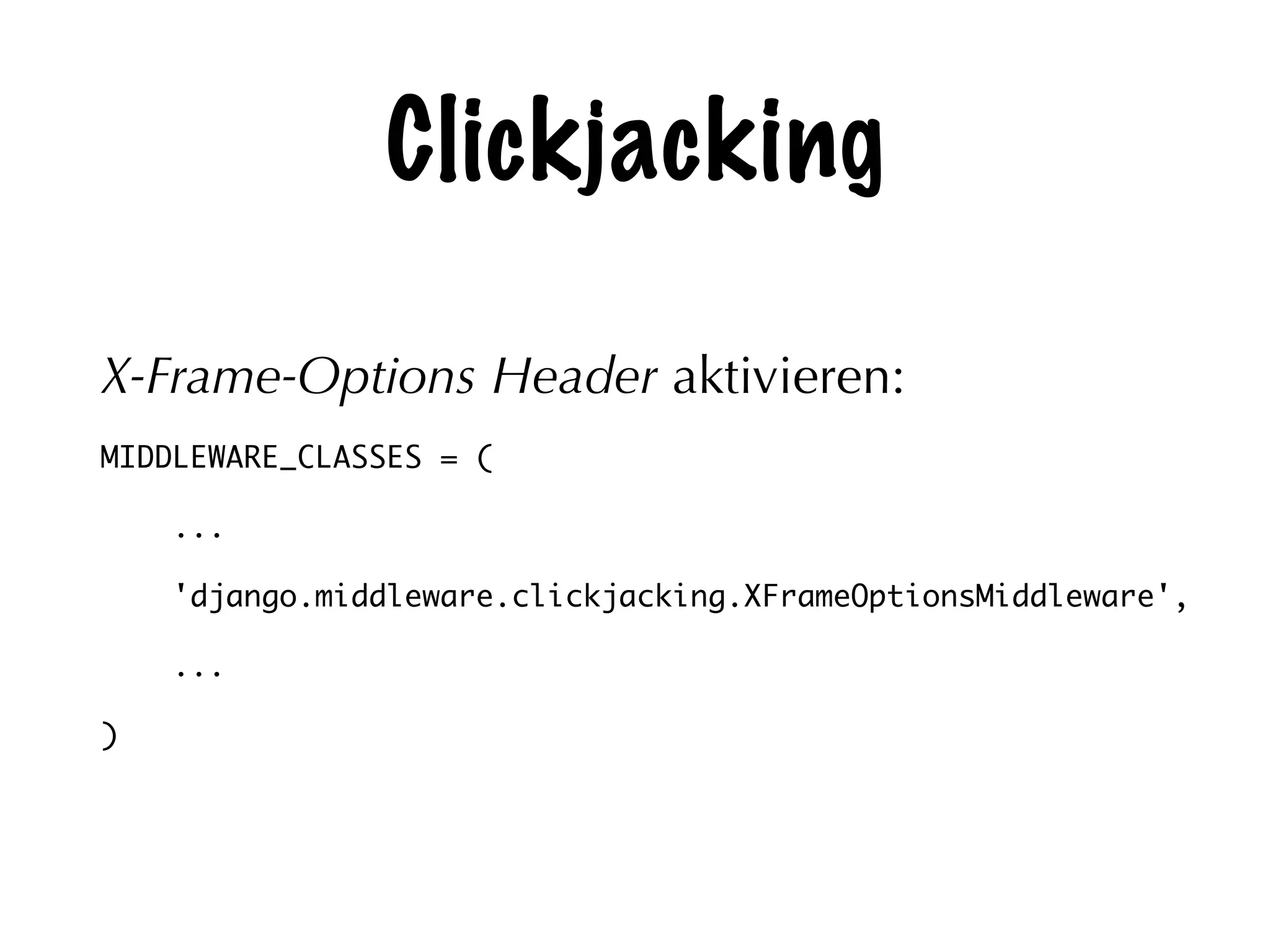
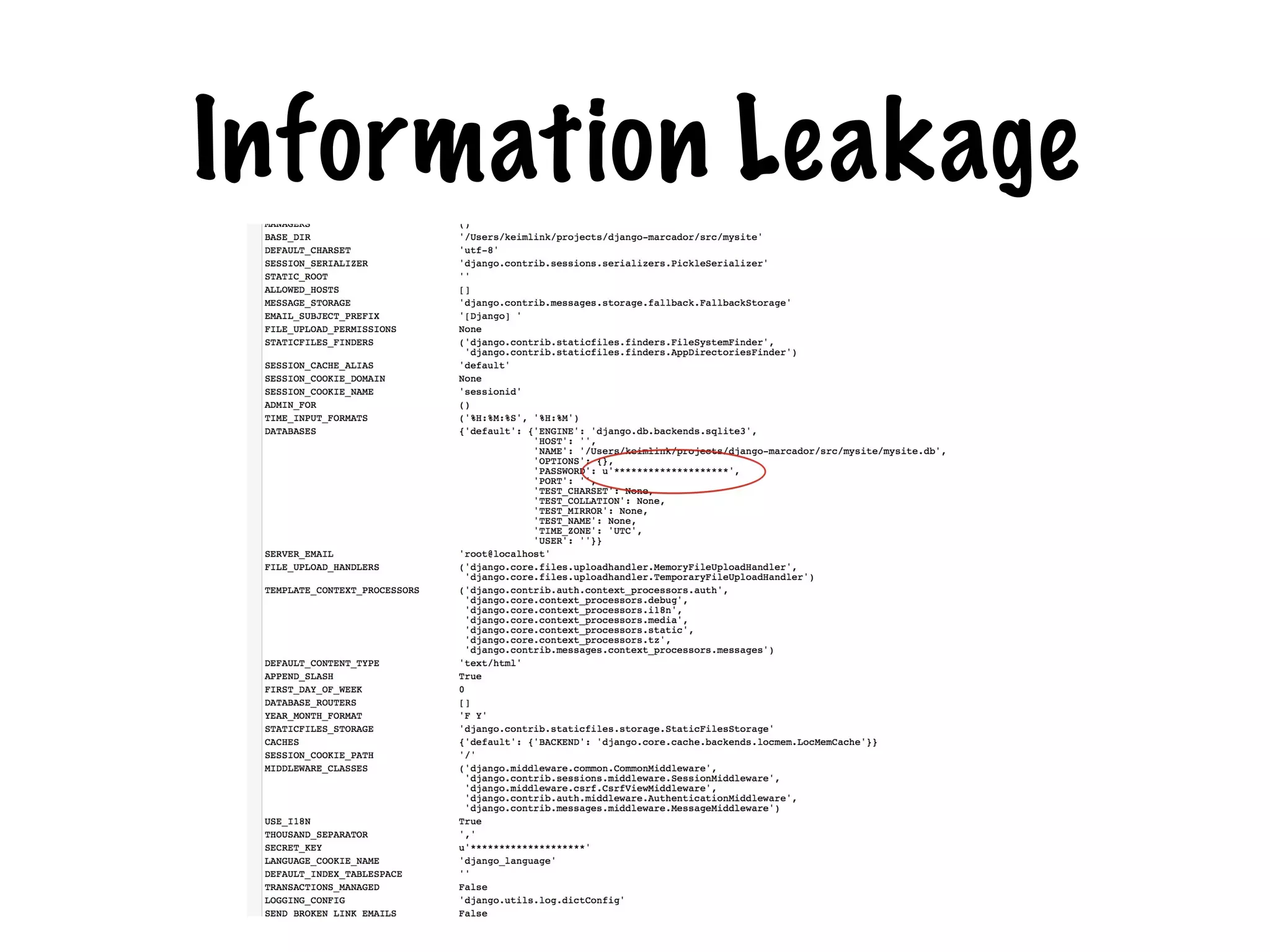
The document discusses the security of web applications using Django as a case study, highlighting key vulnerabilities listed in the OWASP Top 10, such as SQL Injection, Cross-Site Scripting (XSS), and Broken Authentication. It provides examples of code that illustrate these vulnerabilities and suggests best practices for securing Django applications. Additionally, it mentions tools and libraries for enhancing security in web development.