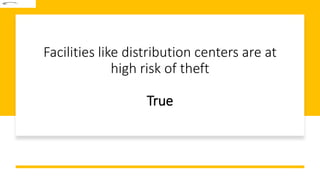
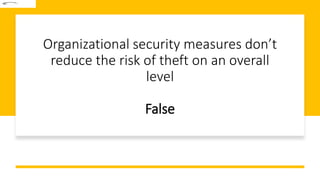
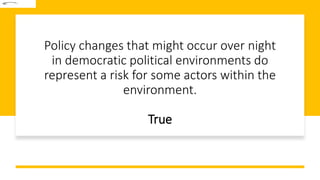
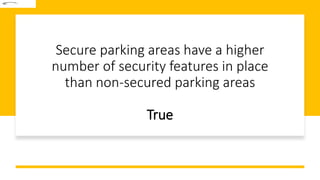
This document discusses challenges in supply chain risk management. It outlines 7 key challenges companies currently face: 1) ongoing market volatility, 2) lack of granular data, 3) outdated inventory strategies, 4) need for exception-based management, 5) cybersecurity concerns, 6) limited visibility, and 7) the constant threat of disruptions. Effective risk management requires addressing these challenges through tools like predictive analytics, greater collaboration, and working with logistics partners.