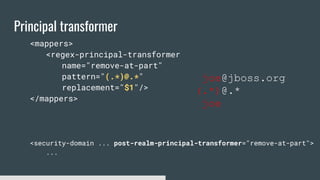
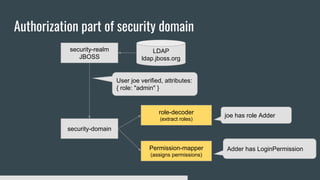
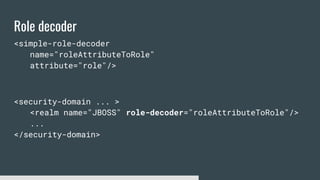
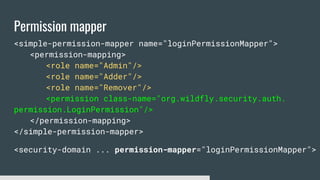
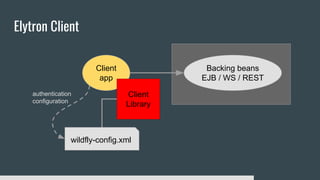
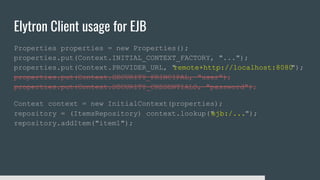
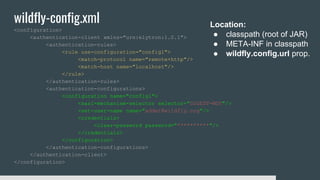
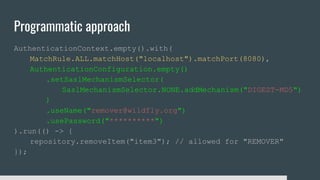
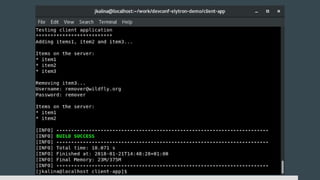
1) Elytron is WildFly's new security subsystem that replaces legacy security configurations.
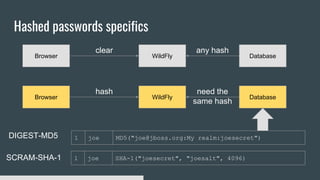
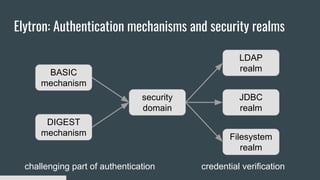
2) Elytron provides authentication mechanisms like BASIC and DIGEST and security realms like LDAP and JDBC to verify credentials.
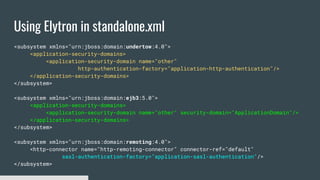
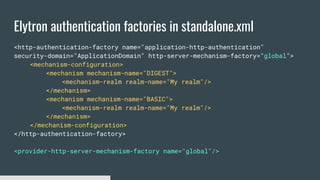
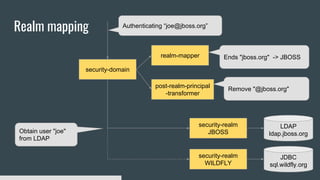
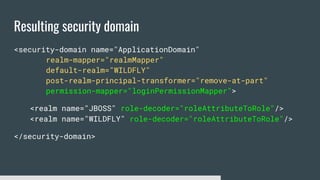
3) Security domains in Elytron integrate authentication, authorization, and principal transformation using concepts like authentication factories, permission mappers, and realm mappers.


![Legacy security
security domain
[web]
security domain
[EJB]
security-domain
[security subsystem]
authentication
login-module Users
authorization
policy-module
accessing user is Joe
and has admin role
admin is permitted
to remove items](https://image.slidesharecdn.com/securingjavaeeappsusingwildflyelytron-180205092743/85/Securing-Java-EE-apps-using-WildFly-Elytron-6-320.jpg)
![Using Elytron
security domain
[web]
security domain
[EJB]
application-security-domain
[undertow subsystem]
http-authentication-factory
application-security-domain
[ejb3 subsystem]
sasl-authentication-factory
security-domain
Http-connector
[remoting subsystem]](https://image.slidesharecdn.com/securingjavaeeappsusingwildflyelytron-180205092743/85/Securing-Java-EE-apps-using-WildFly-Elytron-8-320.jpg)