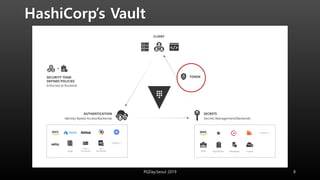
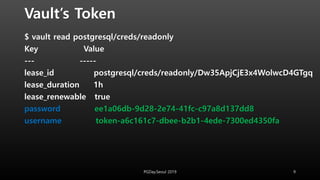
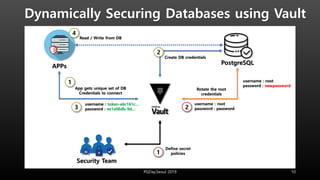
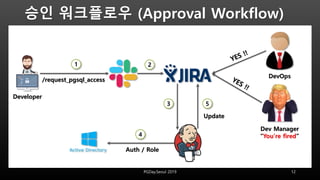
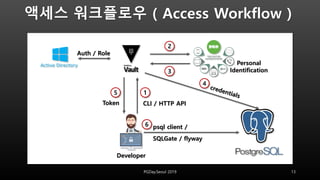
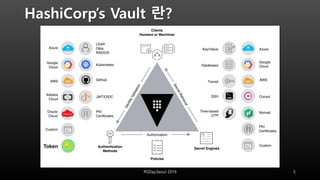
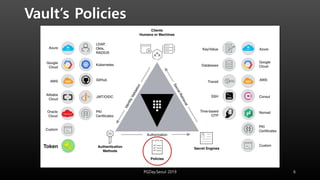
This document discusses using HashiCorp Vault to dynamically generate and revoke database credentials. Vault allows defining policies that control which database operations different credentials can perform. It generates unique credentials with limited lifetimes, reducing the risk of compromised long-term credentials. Applications can authenticate to Vault and retrieve temporary credentials to access databases, without embedding permanent credentials. This improves security by preventing static credentials from being hard-coded or exposed.


![Vault’s Polcies
path “postgresql/creds/readonly” {
capabilities = ["create", "read", "update", "delete", "list"]
}
root@pgsql12:/# ls -la /var/lib/postgresql/data/
drwx------ 19 postgres postgres 4096 Dec 2 02:45 .
drwxr-xr-x 1 postgres postgres 4096 Nov 23 08:10 ..
drwx------ 6 postgres postgres 4096 Dec 2 05:19 base
drwx------ 2 postgres postgres 4096 Dec 2 06:58 global
-rw------- 1 postgres postgres 4535 Dec 2 02:45 pg_hba.conf
PGDay.Seoul 2019 7](https://image.slidesharecdn.com/20191207pgday2019-191209004502/85/Securing-Databases-with-Dynamic-Credentials-and-HashiCorp-s-Vault-7-320.jpg)