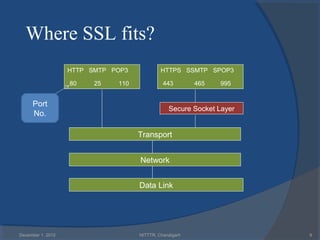
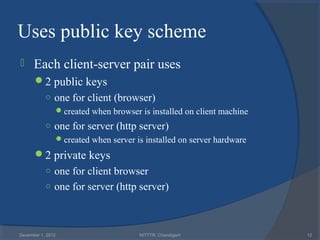
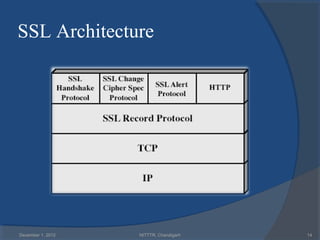
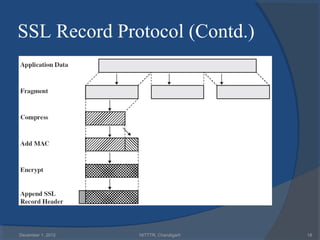
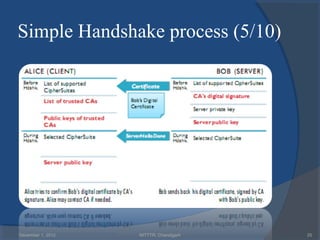
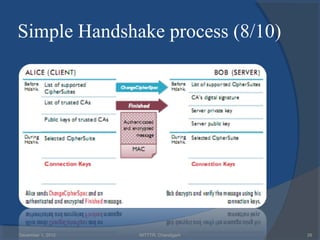
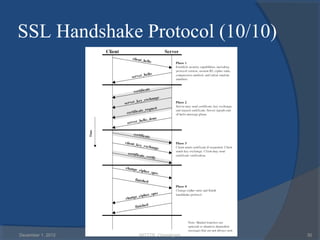
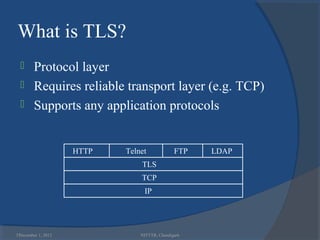
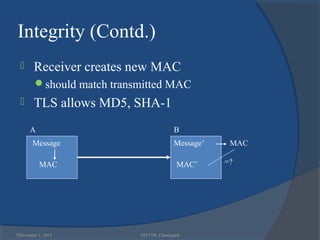
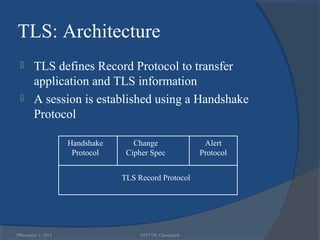
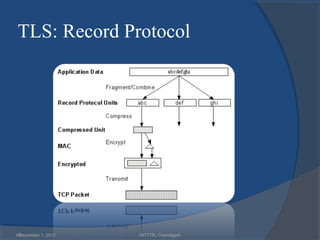
The document provides a comprehensive overview of web security with a focus on Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, detailing their architectures, functions, and cryptographic mechanisms for ensuring secure communications over networks. It outlines the importance of these protocols in safeguarding integrity, confidentiality, and authentication in Internet communications. Additionally, it discusses the implementation and applications of SSL/TLS in various systems and their role in modern web browsing security.