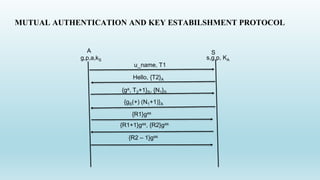
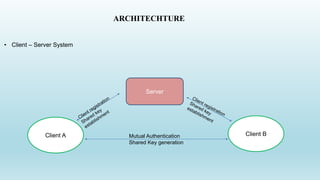
1. The document describes a client-server authentication protocol that uses mutual authentication and key establishment between a client and server.
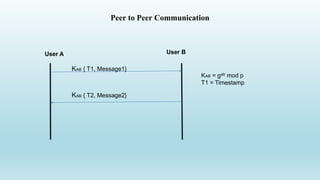
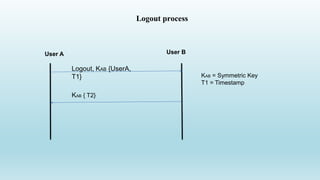
2. It involves the client sending a username and timestamp to the server, which responds with an encrypted challenge. They then perform Diffie-Hellman key exchange to establish a shared key.
3. The protocol specifications include using asymmetric encryption for challenges, SHA-256 for integrity, and restricting usernames and passwords to 8 bytes.


![USER REGISTRATION AND CLIENT-SERVER AUTHENTICATION
PROTOCOL
1. Sending timestamps along with user name and
passwords.
2. Server replies with a ‘Hello’ along with a T2
encrypted with public key of the client.
3. Key Establishment and Authentication happens in
a Diffie Hellman Exchange.
4. Password Hashes and User list is forwarded from
the server to the client along with message
integrity and authentication.
(u_name, pwd) : T1
{ga, T2+1}S, {N1}S
{gs(+) (N1+1)}A
Hello, {T2}A
{R1}gas
{R1+1}gas, {R2}gas
{R2 – 1}gas
A S
g,p,a,kS s,g,p, KA
[Pwd, N] gas, [H(pwd)] gas
[H(u_list)] gas, [u_list] gas](https://image.slidesharecdn.com/finalprojectslides-170702194659/85/Secure-messaging-using-PKI-4-320.jpg)