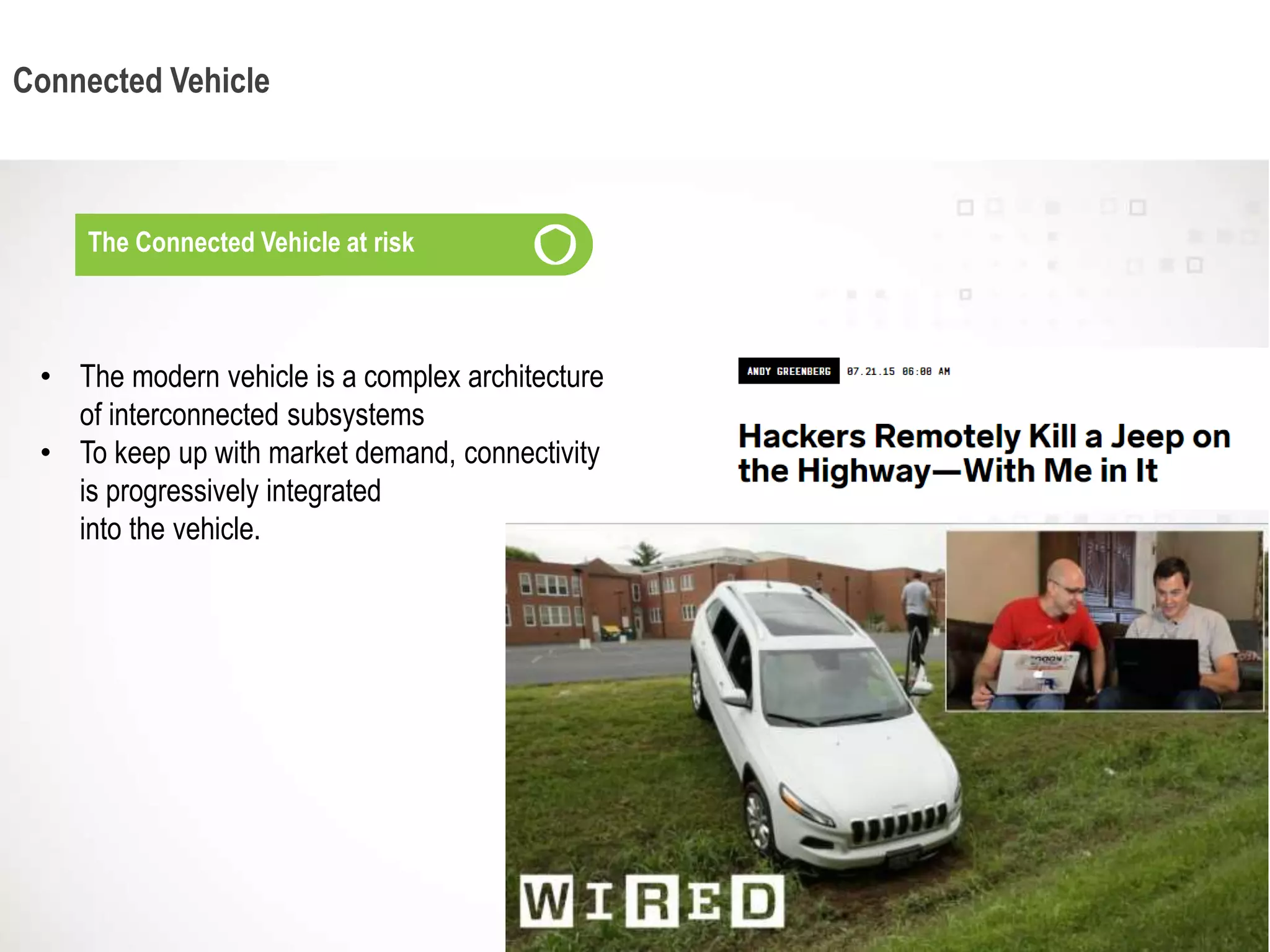
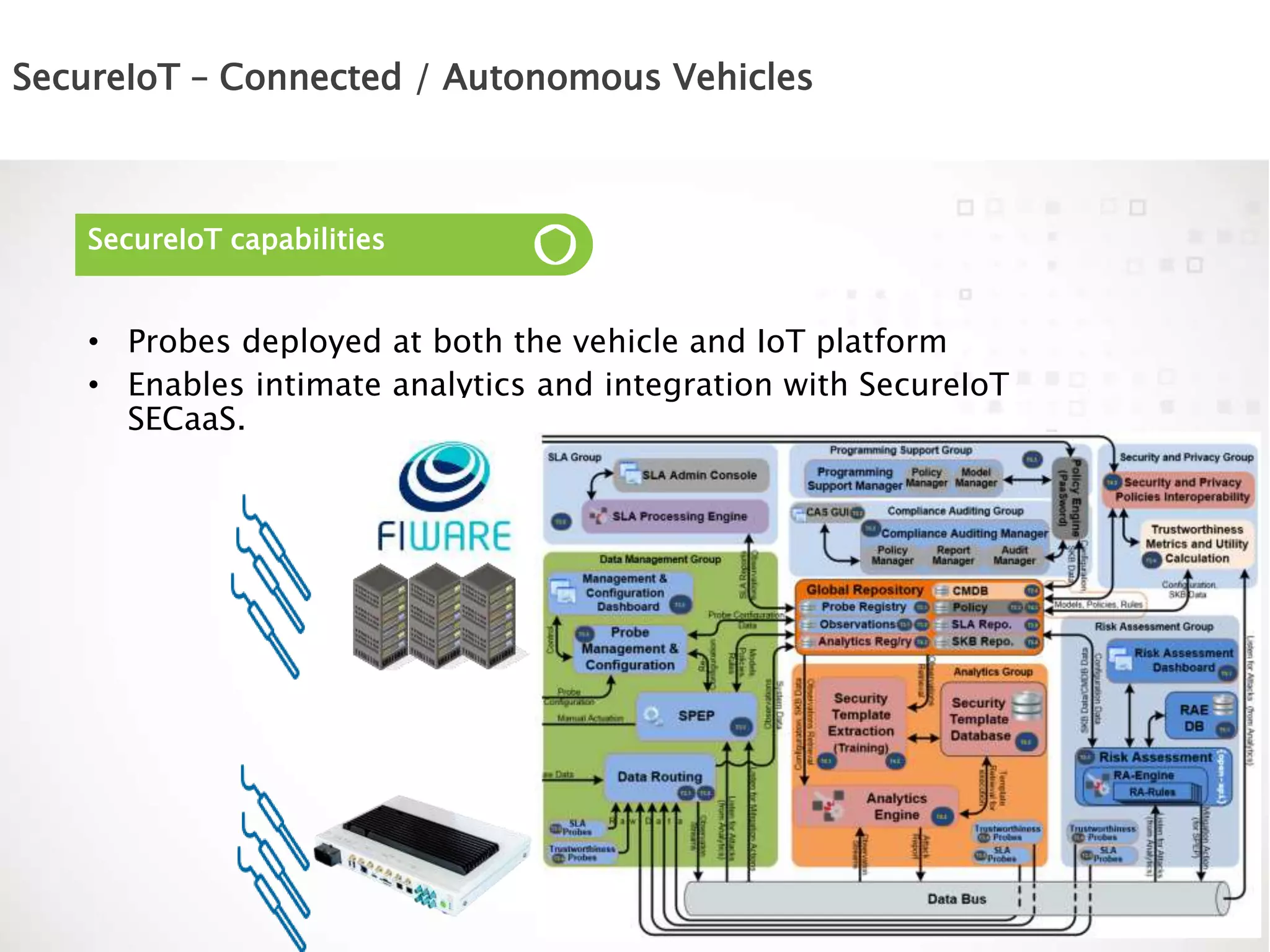
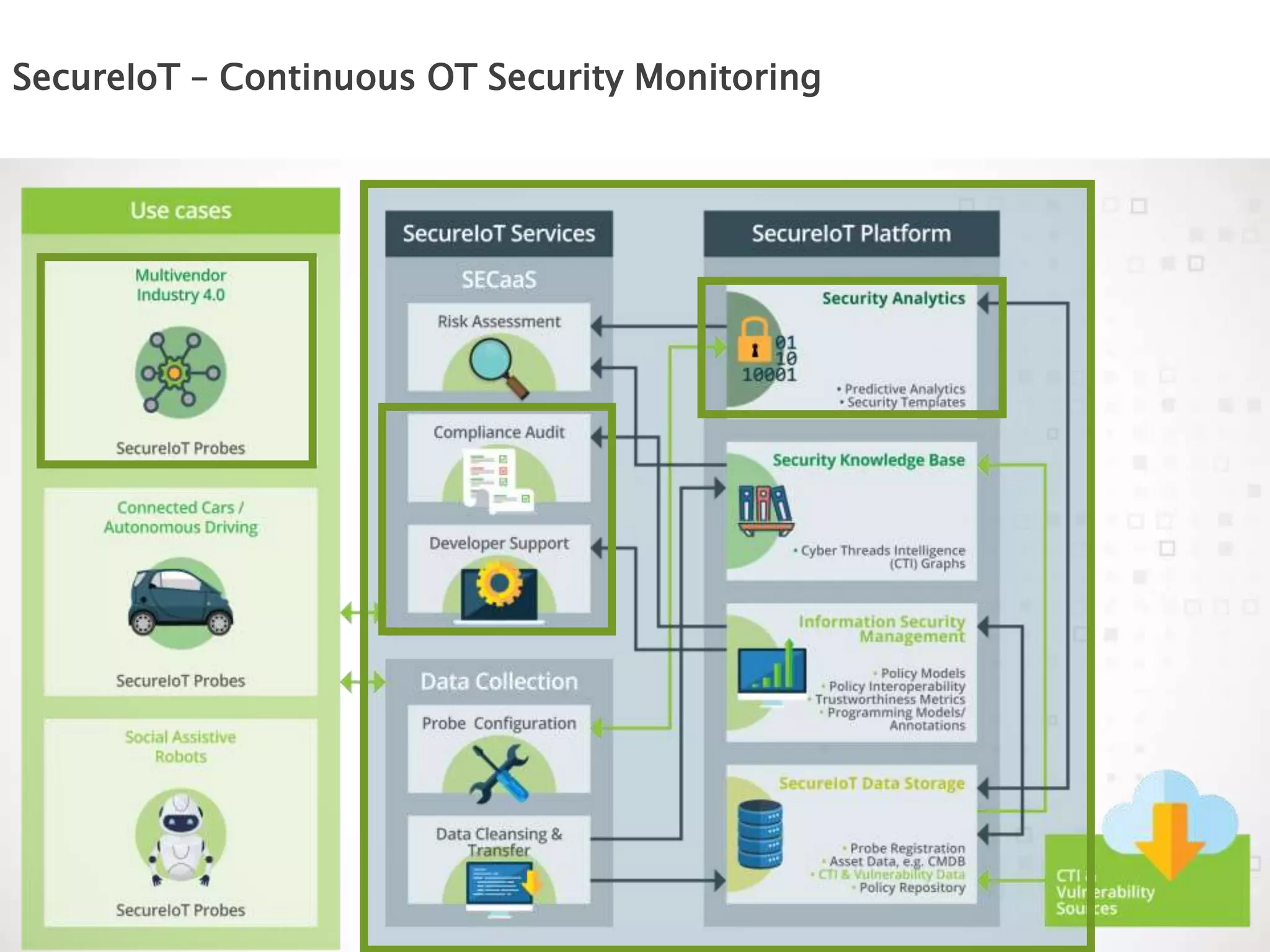
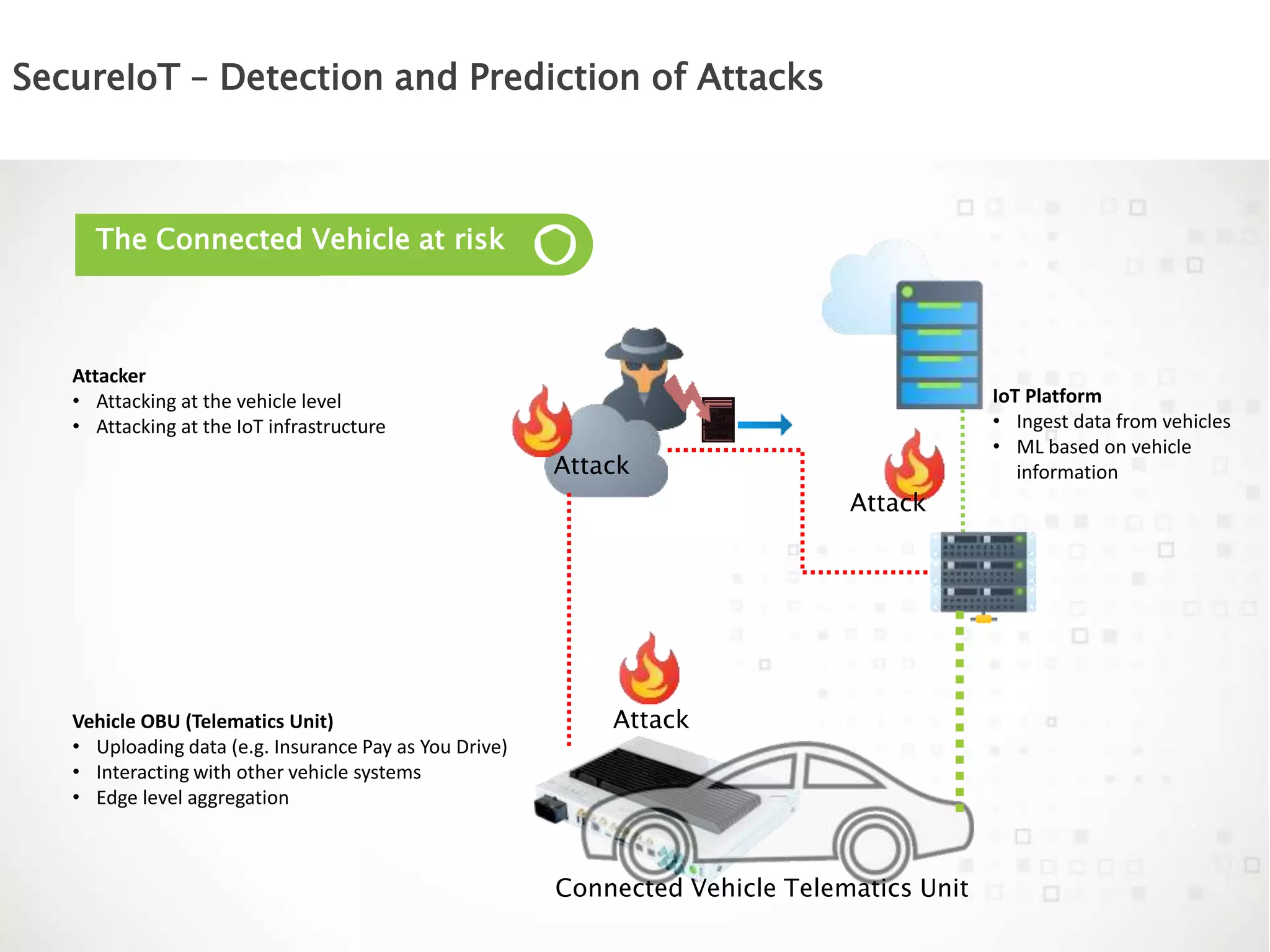
The document discusses the vulnerabilities of connected vehicles, particularly regarding their telematics units which can be accessed remotely by malicious actors, allowing control over critical vehicle functions. To address these security concerns, the SecureIoT project provides independent monitoring and analytics capabilities to detect and predict attacks, ensuring vehicle safety and compliance. The integration of SecureIoT aims to enhance vehicle security by continuously analyzing data and identifying anomalous behaviors at multiple operational layers.