The document outlines a comprehensive guide on reverse engineering and pwnable techniques for capture the flag (CTF) competitions, detailing essential tools, common vulnerabilities, and strategies to analyze programs. It covers basic knowledge necessary for CTF, binary file types, and debugging tools, along with examples of memory vulnerabilities like buffer overflow. Resources for further learning and practical challenges are also provided to enhance the reader's skills in cybersecurity.






![● Disassembly
○ Ghidra [Free]
○ IDA [Free/Paid]
○ Hopper [Paid]
○ Radare2 [Free]
● Decompiler (like JAVA and .NET)
○ JADX
○ JD-GUI
○ dnSpy
○ ILSpy
○ decompiler.com
Reverse Engineering Tools](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-16-320.jpg)
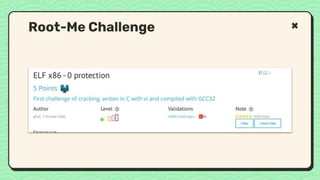
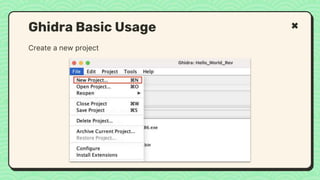
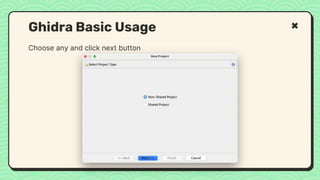
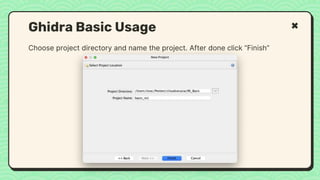
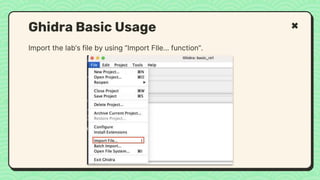
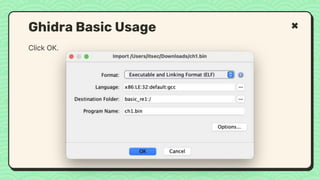
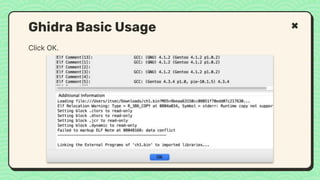
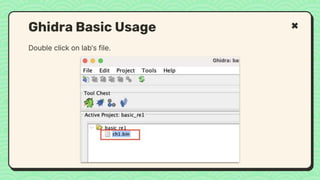
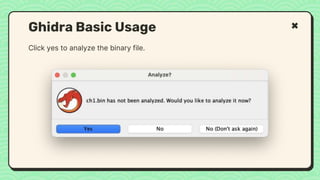
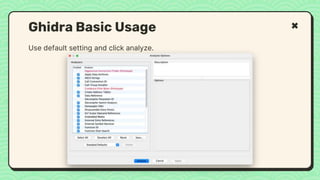
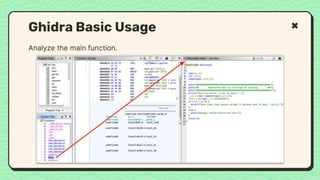
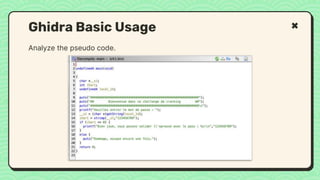
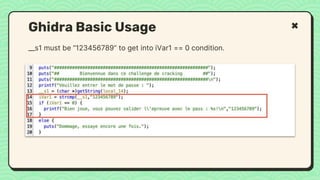





![What happened?
Stack Frame for
call_echo
Return Address (8
bytes)
Unused
[9] [8] [7] [6]
[5] [4] [3] [2]
[1] [0]
buf[10]](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-46-320.jpg)
![Buffer Stack
Stack Frame for
call_echo
Return Address (8
bytes)
Unused
[9] [8] [7] [6]
[5] [4] [3] [2]
[1] [0]
buf[10]](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-47-320.jpg)
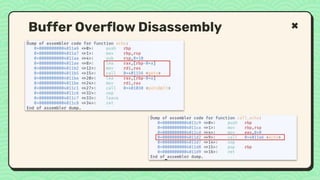
![Buffer Overflow Stack
Stack Frame for
call_echo
Return Address (8
bytes)
Unused
[9] [8] [7] [6]
[5] [4] [3] [2]
[1] [0]
buf[10]](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-48-320.jpg)
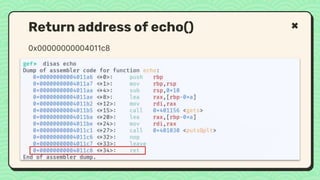
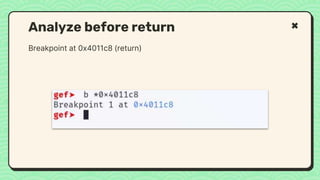


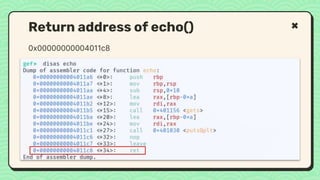


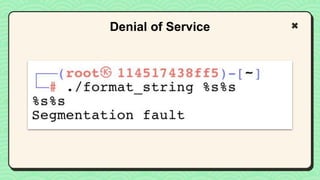
![● We do buffer overflow to RBP.
● Next step
○ How to replace RIP?
○ What address that we want to return?
What happened right now?
RIP Address (8 bytes)
RBP Address (8 bytes)
Buf [10]](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-56-320.jpg)

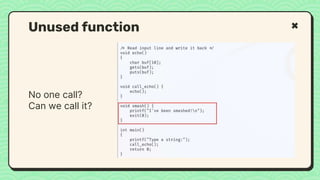
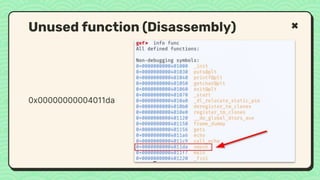


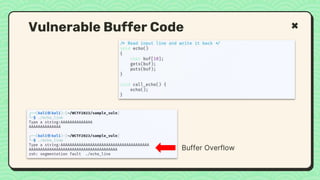
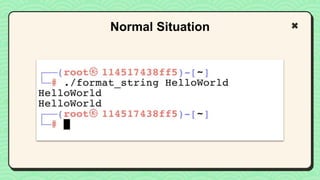
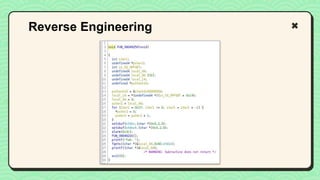
![#include <stdio.h>
void main(int argc, char **argv)
{
// This line is safe
printf("%sn", argv[1]);
// This line is vulnerable
printf(argv[1]);
}
Vulnerable Code
No input validation](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-68-320.jpg)


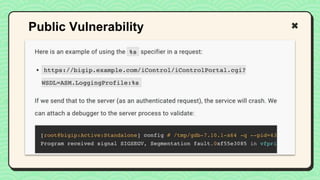
![Payload:
https://bigip.example.com/iControl/iControlPortal.cgi?WSDL=ASM.LoggingPro
file:%08x:%08x:%08x:%08x:%08x:%08x:%08x:%08x
Log Result:
Nov 29 08:41:47 bigip.example.org soap[4335]: query:
WSDL=ASM.LoggingProfile:0000004c:0000004c:08cb31bc:08cba210:08c
c4954:01000000:ffeaa378:f5aa8000
Public Vulnerability](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-76-320.jpg)

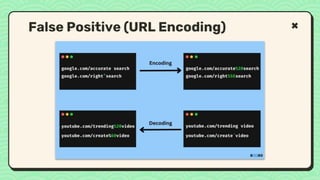
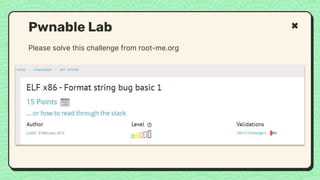
![● https://ctf101.org [Basic to intermediate]
● http://pwnable.kr/ [Basic to advance]
● https://www.youtube.com/@LiveOverflow [Basic to expert]
● https://guyinatuxedo.github.io/ [Basic to expert]
● https://exploit.education/ [Basic to expert]
Learning Resources](https://image.slidesharecdn.com/reverseengineeringpwnabletoolsforctf-240601093330-5d17fcfc/85/Secstrike-Reverse-Engineering-Pwnable-tools-for-CTF-pptx-82-320.jpg)