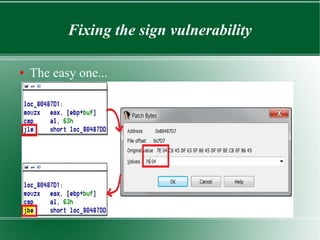
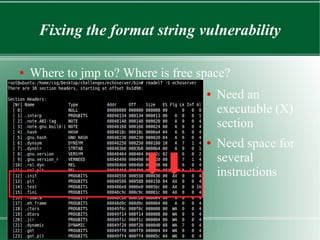
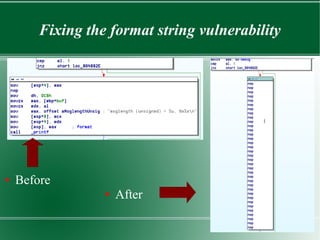
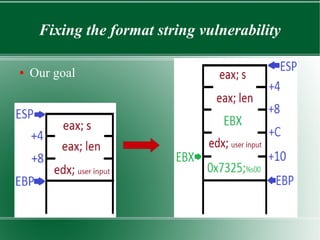
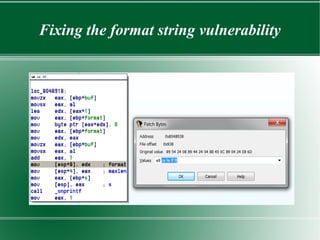
This document discusses binary patching techniques to fix two vulnerabilities in an echoserver program: a signed integer vulnerability and a format string vulnerability. It outlines how to lookup instruction bytes and use IDA to patch binaries by changing individual bytes. It then walks through patching the vulnerabilities, including adding a format string parameter, rearranging the stack, and redirecting control flow to make the proper function call without disrupting registers or the stack. The document provides examples of the binary diffs before and after each patch.



![Background
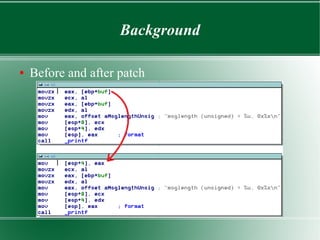
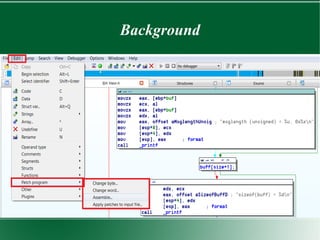
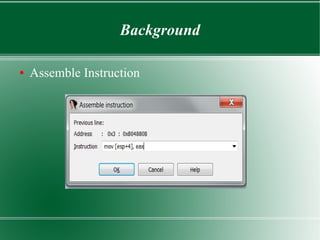
● Change Byte
– Important to notice the size of instructions
– Easy to do with “Change byte”
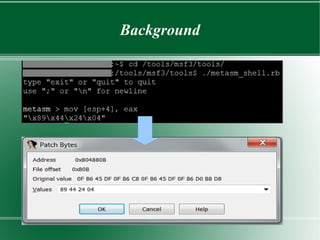
● How do we figure out the bytes that makeup an
instruction? “mov [esp+4], eax”
– Metasploit!
– metasm_shell.rb](https://image.slidesharecdn.com/binarypatching-180129071721/85/Binary-Patching-6-320.jpg)