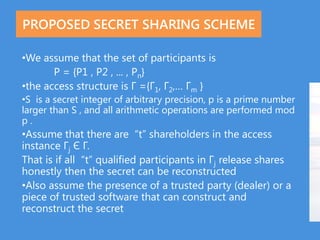
1) Secret sharing schemes involve dividing a secret into multiple pieces called shares such that only certain subsets of shares can be combined to reconstruct the secret.
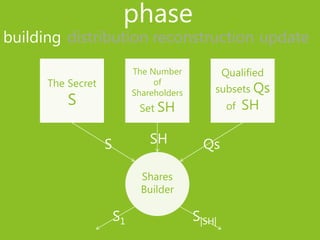
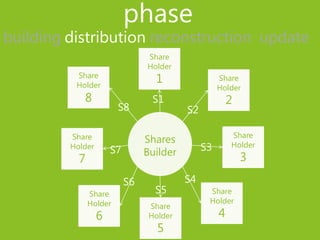
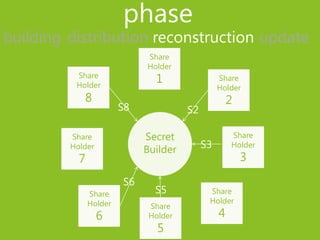
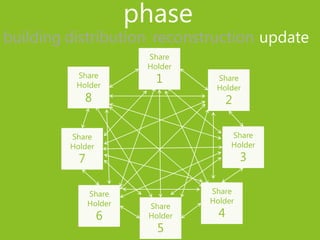
2) The phases of a secret sharing scheme include building shares from the secret, distributing shares to participants, reconstructing the secret from qualified share subsets, and updating shares.
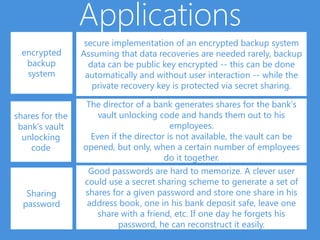
3) Secret sharing schemes have applications including secure encrypted backup systems where the recovery key is protected via secret sharing, distributing bank vault unlocking shares among employees, and generating password shares that are stored in different locations for easy password recovery.