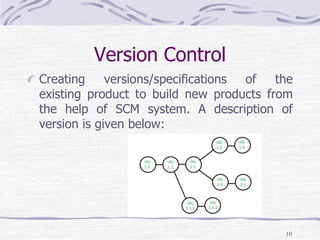
Configuration management is a technique for identifying, organizing, and controlling modifications to software being built by a programming team. It involves identifying changes, monitoring and controlling changes, ensuring proper implementation of changes, auditing changes made, and reporting on changes. The key aspects of configuration management include identification and establishment of configuration items, version control, change control, configuration auditing, and reporting. Configuration management helps improve productivity, reduce errors, and ensure quality and stability by properly controlling and managing all software changes.